
Uncategorized

Automating SQLi with SQLmap and custom code.

Top 5 Indian Hackers | Updated 2024

Enum4Linux Full Tutorial | Noob to Pro | 2024

7 Packet sniffing tools that you should try at least once

DLL Hijacking | How to do it | Explained
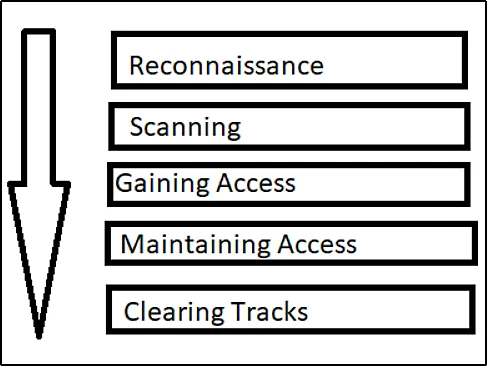
5 Stages of Hacking | Explained by Hacker

What are cyber-attack vectors? 10 Most common vectors – Explained


