Introduction
Hi Everyone!! This post is on some of the introductory topics in CEH v10 which can make a solid foundation for anyone who wants to start their journey in ethical hacking and there will be a series of blogposts after this which will definitely help you further in your journey. I hope this helps you. Happy Learning!😊
Key Terms and Definitions
Vulnerability:
A weakness in a system that has the possibility of being exploited for unethical means.
Threat:
An event or an action that could cause harm to a system.
Exploit:
To engage in threatening of a vulnerability. Or taking advantage of a vulnerability.
Zero-Day exploit:
It is a malicious technique which takes advantage of unknown or unpatched vulnerabilities in a software or a system. Since this is a kind of surprise attack there is no defences to counter this attack.
Payload:
A chunk of malware or code used to exploit to gain access to a system.
Attack Vector:
Various paths attackers can use to infiltrate a system such as vulnerabilities in a software or a weakness in a system.
Threat Actor:
Individuals behind an attack and their motivations and techniques can be considered as a threat actor.
CIA Triad
The CIA triad represents the three pillars of information security:
Confidentiality:
Ensures that only the authorised individual should be able to access the sensitive data.
Integrity:
Ensures that the sensitive information remains original and is not altered by unauthorised means.
Availability:
Keeping the important information readily accessible to the authorised users whenever necessary.
Advertisement
Security Triangle
Its a concept of security, functionality and usability which according to CEH v10 exists in a trade-off relationship where something is gained when something else is given up. That is we can’t prioritise security, functionality and usability together but there must be a balance among them.
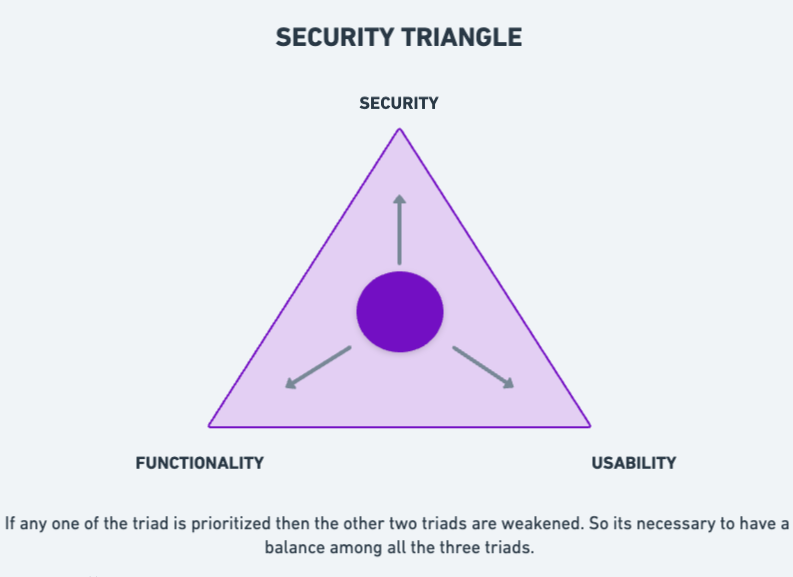
Security: Implementing strict security measures can sometimes lead to limited functionality and usability. Such stringent security can block legitimate users from accessing the system.
Functionality: When features and functionality are heavily focused on then there will be high possibilities of vulnerabilities in the system. So such special functions can only come at the expense of security. And also such high features might be confusing for the users to work with.
Usability: When systems are made over user-friendly it might weaken the security and might cause unauthorised use. Also some functionalities which are important might not be available for the users.
As seen above its impossible to focus on one specific aspect alone so its important to maintain an optimal balance among the three.
Threat Categories
The categories are shown below:
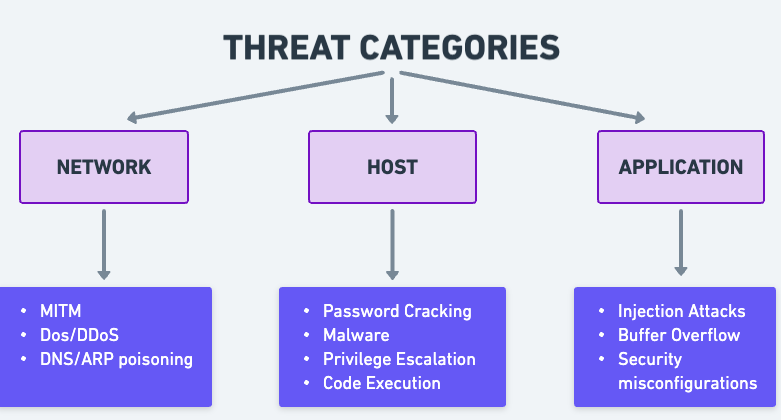
Network Threats: These are the threats which comes via networks.
MITM: Man in the Middle
- Intercepting communication between two parties by a third party outsider.
- Stealing or modifying sensitive data shared between the parties.
DoS/DDoS: Denial of Service/ Distributed Denial of Service
- Overwhelming a target system by excessive traffic and making the system inaccessible to the users i.e denying the service to user.
- DDoS is the use of many compromised systems such as botnets to launch the attack making it impossible to trace.
DNS/ARP Poisoning
- Exploits vulnerabilities in Domain Name System to redirect internet traffic to malicious websites instead of valid ones.
- Targets Address Resolution Protocol to map IP addresses to incorrect MAC address for manipulation of network traffic.
Host Threats: Malicious activities targets specifically on mobiles, desktops and tablets.
Password Cracking
- Attempting malicious methods to discover a password to gain access to a device.
- Methods like brute force, dictionary attack are used. This will be explained in further posts.
Malware
- Malicious programs used to gain unauthorised access or damage systems.
- Malwares can include worms, viruses, trojans etc.
Privilege Escalation
- Exploiting vulnerabilities or misconfigurations to gain higher privileges within a system.
- This will enable the attacker to gain greater control of the system.
Code Execution
- Running code on a system without authorization.
- This is done using social engineering and cross-site scripting (XSS).
Application Threats: These kind of threats lurk within the applications in a system waiting to exploit.
Injection Attacks
- Injecting malicious code into databases or webpages for manipulation.
- Gaining unauthorised access or installing malware.
Buffer Overflow
- It occurs when memory buffer exceeds its allocated size and overwriting occurs which may also modify programs.
Security Misconfigurations
- Unpatched vulnerabilities can be exploited by attackers.
- Improper security configurations might enable unauthorised access.
Conclusion
I hope this introduction was useful. I will post more in series. Sayonara!💜




