Introduction
In this post, Let’s see what is brute force attack and how to do it and also I will mention some software for brute force.
What is Brute Force Attack explained ????????
A Brute Force is a password cracking method, This password cracking method is widely used by cybersecurity people.
No cybersecurity experts will recommend brute force on the target, But why? Brute force is directly attacking the target network.
You will be easily caught by the IDS/IPS sensors.
Brute force password cracking method is like “Trial and error method“, Try’s all possible usernames and passwords provided by the user.
Though the brute force attack is very old still the method is very effective.
Is Brute Force legal ????
Brute force will be legal if you got permission from the target owner, Though the target owner grants permission, You should get a written agreement that if something goes wrong you will have a get of jail agreement.
On the other hand, Burte force is still illegal if you didn’t get permission from the target owner. Most of the time the brute force attack is used to steal credentials.
So, that’s why brute force is illegal.
How to perform a Brute Force Attack
There are multiple ways to do a Brute Force attack. In order to Brute Force a target you need the following.
- Nmap scan
- What port is open
- If open port send payloads
- Exploit the vulnerabilite sent
- Finally Brute force on the open port
* Let me show a live example of how to do brute force using the metasploitable 2
Firstly, I have found the open port of the metasploitable 2

We can see the ssh is open and let me connect to that port using the medusa tool. Here I am using the medusa to do Brute force.
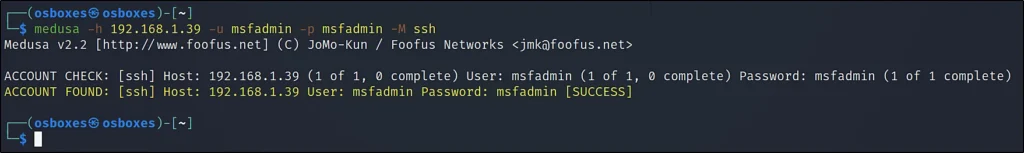
Now, We have found the correct username and password. I have specifically given the username and password. If you wanna load a list of usernames and passwords then you have to specify the path and file.
To learn how to do Brute Force Attack using medusa [Click here]
Softwares for Brute Force Attack
There is much software to do Brute Force, I will be sharing my 3 favourite Brute Force software.
Types of Brute Force Attack
There are many different types of brute force attack but three of them are considered very important they are;
- Simple Brute Force Attacks
- Dictionary Attacks
- Hybrid Brute Force Attacks
Simple Brute Force Attack: These can reveal extremely simple passwords and PINs. For example, a password that is set as “12345”.
Dictionary Attack: Hacker chooses a goal and runs viable passwords in opposition to that username. These are called dictionary attacks.
Hybrid Brute Force Attack: A hybrid attack usually mixes dictionary and brute force attacks. For example “Guest123@#”
How to prevent Brute Force Attack
- Limit login attempts
- Turn of ssh
- Modify the default ports
- Use Captcha
- MFA or 2FA
- Change login URL’s
- Monitor your logs
Conclusion
Brute forcing is a very old method but still, it is very effective. But remember brute force is a bad idea.
Also Read: THC-hydra full tutorial for beginners
