Introduction
In this post, you will learn what is Ncrack and how does the tool work and also you will learn lot’s of examples in this tool and I am sure by end of this post You will be familiar with using the tool.
Below is the video format of the post, Check it out ❤
Video
What is Ncrack ❓
The Ncrack is a password cracking tool and it is one of the powerful password cracking tools.
The tool was developed to help companies secure their networks by proactively testing all their hosts and networking devices for poor passwords.
Even I and many security professionals rely on the Ncrack tool.
This tool is a command-line interface, So this is going to be a disadvantage. But anyway, this tool has positive reviews constantly every year. It allows for rapid, yet reliable large-scale auditing of multiple hosts.
Advertisement
Who developed the Ncrack tool
The Ncrack tool is developed by the guys who developed the Nmap and Zenmap tools. And below is the link to the creator’s homepage and also the download links.
The tool is available for windows, mac and of course for Linux.
For Linux users just enter apt-get install ncrack
Features in Ncrack tool
- Allowing for very sophisticated brute-forcing attacks
- Timing templates for ease of use
- Protocols supported include SSH, RDP, FTP, Telnet, HTTP(S), WordPress, POP3(S), IMAP, CVS, SMB, VNC, SIP, Redis, PostgreSQL, MQTT, MySQL, MSSQL, MongoDB, Cassandra, WinRM, OWA, and DICOM
- Runtime interaction similar to Nmap
Advertisement
Usefull commands in Ncrack
Target specification:
-iX: Input from Nmap’s -oX XML output format
-iN: Input from Nmap’s -oN Normal output format
-iL: Input from list of hosts/networks
–exclude: Exclude hosts/networks
–excludefile: Exclude list from file
Service specification:
-p: services will be applied to all non-standard notation hosts
-m: options will be applied to all services of this type
-g: options will be applied to every service globally
Authentication:
-U: username file
-P: password file
–user: comma-separated username list
–pass: comma-separated password list
–passwords-first: Iterate password list for each username. Default is the opposite.
–pairwise: Choose usernames and passwords in pairs.
Output:
-oN/-oX: Output scan in normal and XML format, respectively, to the given filename.
-oA: Output in the two major formats at once
-v: Increase verbosity level (use twice or more for greater effect)
Module:
SSH, RDP, FTP, Telnet, HTTP(S), WordPress, POP3(S), IMAP, CVS, SMB, VNC, SIP, Redis, PostgreSQL, MQTT, MySQL, MSSQL, MongoDB, Cassandra, WinRM, OWA, DICOM
Advertisement
How to use the Ncrack tool
Finally, let’s get into the practical part and I am damn sure by end of the post, You will be familiar with using the tool.
Just follow the below examples and commands and try it and if you have any doubt comment down below or watch the video I made on Ncrack.
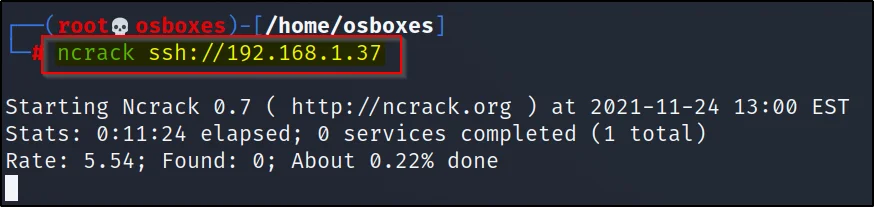
Example1, Default scan
To do a default scan just enter the service you are attacking and then mention the target like this
ncarck ssh://192.168.1.37
Example2, Using specific username & Password
Now, let’s use a specific username and password to crack the target. For this we are using the -user and -pass command.
ncrack ssh://192.168.1.37 -user msfadmin -pass msfadmin

Example3, Dictionary attack
To do a dictionary attack you should have a list of usernames and passwords in a file and then you are ready to do a dictionary attack.
Advertisement
ncrack ssh://192.168.1.37 -U user1.txt -P pass1.txt

Example 4, Pairwise attack
Suppose you don’t know the username and password and also you are really tired to create a list of dictionary files then leaving it to ncarck is great.
Ncrack creates the user and password and also does a successful login. So you have to sit back and do a waiting game.
ncrack -v –pairwise 192.168.1.37:21

Example5, Brute forcing
If you have a custom username list and password just do brute-forcing by just entering this command
ncrack -user msfadmin,ignite -pass msfadmin,123 ftp://192.168.1.37

Example6, Resume an attack
To resume an attack we just use the –resume command and mention the previous log file like this
Advertisement
ncrack –resume /root/.ncrack/restore.2021-11-24_14-30

Example7, Timing
The ncrack timing is very similar to the nmap. So, I think you have guessed it the timing are from T0 to T5
T5: Insane Scan
T4: Aggressive Scan
T3: Normal Scan
T2: Polite Scan
T1: Sneaky Scan
Let’s do an aggressive scan
ncrack -user msfadmin,ignite -pass msfadmin,123 ftp://192.168.1.37 -T4

Example 8, Multiple host attack
To attack multiple hosts just add the list of targets in a file and enter the file in the command
ncrack -user user1.txt -pass pass1.txt -iL host1.txt -p21 -v
-iL: Specify the target host
-p21: Mentioning the port to attack

Example9, Output
There are different commands to save the output and let’s see how to save in text format and also in xml format.
To save the output in text format you can use ????????
Advertisement
ncrack -U user1.txt -P pass1.txt 192.168.1.37:21 -oN normal.txt
or
ncrack -U user1.txt -P pass1.txt 192.168.1.37:21 > normal.txt

For xml format just enter this command
ncrack -U user1.txt -P pass1.txt 192.168.1.37 -oX save.xml
Good old conclusion
In Conclusion, n-crack is a great and fast tool and it has a feature called pairwise and I haven’t seen this feature in any other password cracking tool.
Some alternatives for ncrack is medusa and john the ripper and thc hydra.
I personally like this tool and just give it a try this tool then you will love it see ya ????
Advertisement
Also Read: My favourite password cracking tool is????




