Introduction
In this post, you will learn what is social engineering meaning. And how social engineering works and the 9 most common types of social engineering attacks. I have written a post on DDoS and DoS which is really great content to read more about DDoS and DoS attacks visit http://techyrick.com/difference-between-dos-and-ddos/
What is social engineering
Social engineering is an “Art of manipulation”. In simple words, social engineering is an External reconnaissance attack, which tricks humans and gathers sensitive information for future cyber attacks.
You may ask me why the hackers can’t do internal reconnaissance attacks, which means cyberattacks through hacking tools.
Well, internal reconnaissance is just a passive attack. The main attack is external reconnaissance. Cyberattacks using hacking tools will not last long. The user may change the user credential after an attack. But social engineering attacks last longer, the hacker knows about the user inch by inch.
The 9 types of social engineering methods;
- Pretexting
- Diversion theft
- Phishing
- Phone phishing (vishing)
- Spear phishing
- Water holing
- Baiting
- Quid pro quo
- Tailgating
Pretexting social engineering attack
Pretexting means putting pressure on the user. In simple words, the hacker would do some research about the company, write a lie in the mail and send it to the company and ask for money as their own company manager. At this stage, the company staff will deposit the money in the account. As the mail came from the company managers account.
But in reality that isn’t company managers mail. Take a look at the below example even you would get confused. And this is called pretexting.
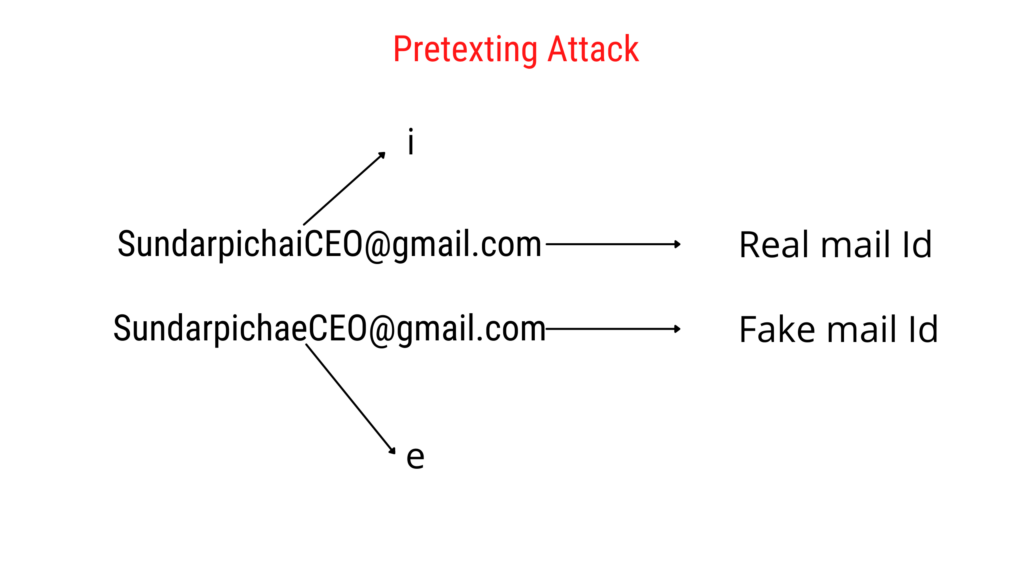
If staff working didn’t read the mail properly I am sure the staff would send the money.
Also Read: What is DDoS in detail
Diversion theft
Diversion theft means just diverting the user. The hacker may found information about what you ordered on the internet and he/she may deliver the fake parcel to the user. And wait there until the real parcel arrives and sign and get the real parcel which comes for the user.
At last, the delivery man is a fake guy. Suppose the user is ordered a laptop and this fake delivery man can deliver a damaged or malware-infected laptop to the original order users and get the real package and this is a double profit for the hacker. The hacker can spy and also he/she got a brand new laptop.
Also Read: What is Denial of service attack in detail
Phishing attack
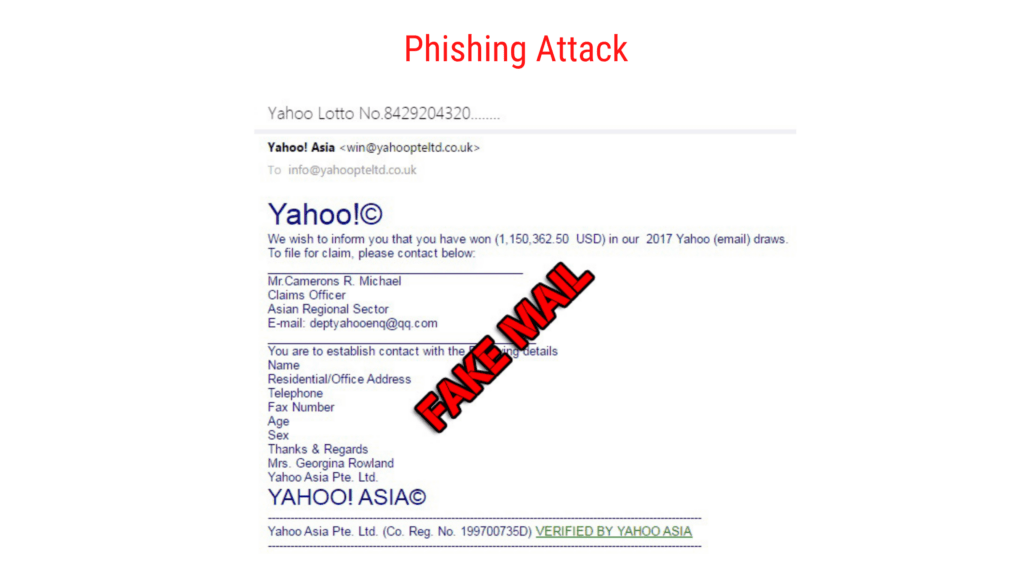
Phishing attack mainly happens through spam mails. Sending tons of spam mail to the users in a particular network or the data the hacker got. When the hacker sends as much as spam emails the success rate of the hacker will increase. At least one in 1000 will get tricked by the mail.
Take a look at the below image, which forces the users to click on the link.
Phone phishing (Vishing)
phone phishing or vishing. Also called a scam call, you must very well know about scam calls. The scammer calls the users and asks for the login credentials. You may ask how the hacker get the ph number? The hacker gets the ph number from the data breach websites.
To learn more about data breach visit: http://techyrick.com/what-is-data-breach/
Once the hacker gets the login credentials, he will definitely take compromise the account. This type of attack can be more professional. There will be no difference between a scam caller and a Bank staff caller.
Spear phishing
Spear phishing is also a type of phishing and also vishing attack. In spear phishing, the hacker does a targeted attack. This means the hacker knows the target and then attacks.
Water Holing
Water holing is a type of social engineering attack. This attack takes users trust. In simple words, you would trust a website like StackOverflow but the hacker would found some vulnerability in the site and takes the user information.
The information took would not be known to the user. But the trusted site would know and they will not say publically or they just say sorry. And finally, the user information is stolen.
Baiting
Baiting or baits for humans. Human beings, when found something new the curiosity in them, will increase and temp them to use the product. The same here takes place the hacker would drop a malicious Pendrive or an IoT device on the floor when the user cross by near. I am damn sure they will take it with them.
The curiosity in the user will temp them to put USB in their device and once they inject there will be a drive via attack.
Quid pro quo
This is a very cheap type of social engineering attack. The attacker will randomly call many users from the data got. And this is not even a targeted attack. The attacker asks users to enter into a competition on a site. The site will be injected with malicious malware.
Once the user enters the malware injected site. The user phone will also be injected by some different types of malware.
Tailgating social engineering attack
Tailgating is the least performed social engineering attack. Entering into a restricted place is called Tailgating. The attacker may enter into a company using an employee id card going behind the staff. The attacker may say that I forgot my Id card can I get in with your card.
Also Read: What is incident response?
Also Read: What is the red and blue team




You made some decent points there. I looked on the internet for the topic and found most guys will agree with your site.
Thanks man 👍💯