Introduction
In this post, You will learn what is driftnet and how does it work and I am sure by end of the post, You will be familiar with using the tool.
Below is the video format of the post, Check it out 👇🏾
Video
What is driftnet ❓
Driftnet is a program that listens to network traffic and picks out images from TCP streams it observes.
It is interesting to run it on a host which sees a lot of web traffic.
In simple driftnet acts as a screen grabber, Which means just captures the images on the target. Whenever the target access any image the image will be printed out in driftnet GUI.
Advertisement
Who developed driftnet tool
The tool was developed by David Suárez and he is very anonymous and If you are reading this blogpost comment down below and leave your Twitter to handle below.
By the way, the tool is Great and EVIL. Will the author be EVIL 😁
[Click here] to view the author GitHub page.
Advertisement
How to use driftnet
It is very much easy to use driftnet. Just follow the below examples. If you have any doubt comment down below or watch the video I made.
Example1, Execute driftnet
There is only one command to execute driftnet that is,
driftnet -i eth0
driftnet -i <Network>
Once you enter this command the tool will start to capture images on the target host.
I will go with driftnet -I eth0 and open my web browser and search for any images.
Now you will be seeing the captured images on the driftnet GUI box.
You will be seeing a black screen and Now, you can hack the target network using aircrack-ng. I recommend you to visit my wireless attack menu.
Example2, Capturing Images
I have gone to this URL and I have captured all images http://www.ex-parrot.com/~chris/
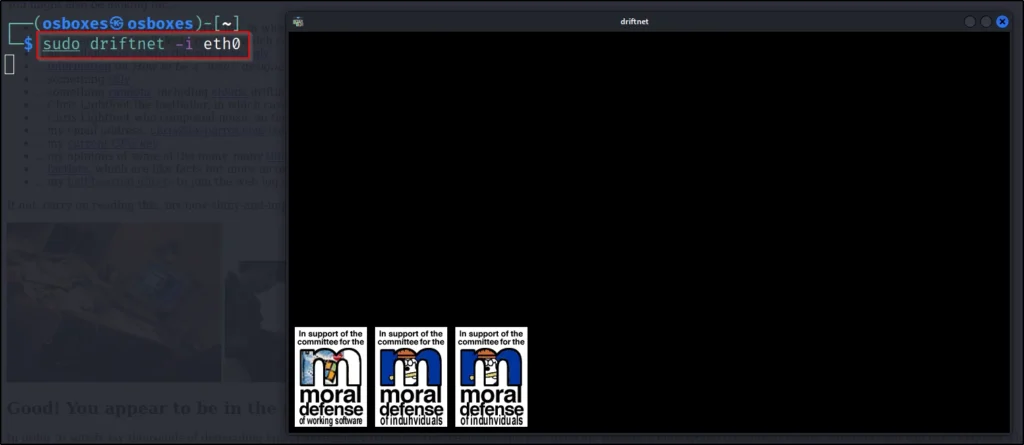
Example3, Verbose
If you add verbosely -v You can literally find what exactly happening what all the connections is made.

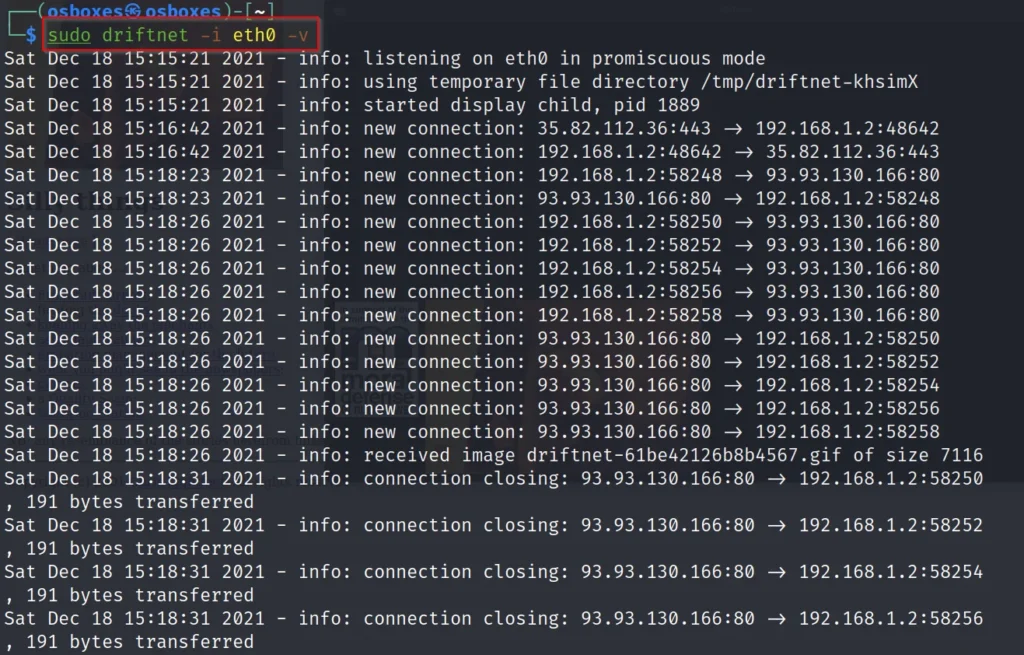
Example4, Adding beep sound whenever you find an image
To add the beep sound you just add the -b option and in some systems, it is not working properly
driftnet -i eth0 -v -b
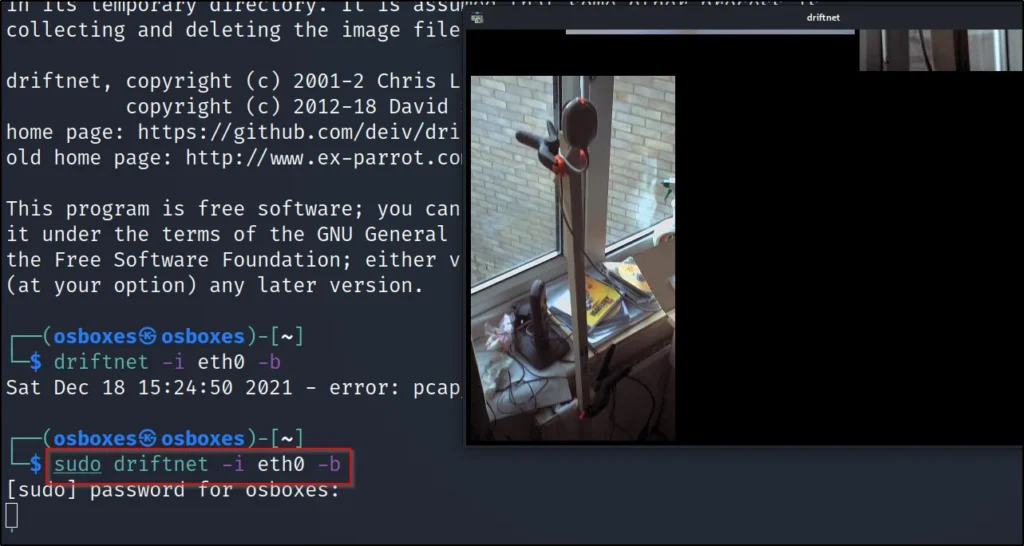
Conclusion
Driftnet is an Old and Great tool to work with this tool is most probably helpful at the post enumeration activity, Like stealing passwords images.
What are you looking at it is a great fuc*ing tool and perform above example and peace out ✌
Also Read: A complete wireless attack using Aircrack-ng Full tutorial
