Introduction
In this post, You will learn what is naabu and how does it work and I have give all the important commands for naabu.
Below is the video format of the post, Check that also
Video
What is Naabu ❓
Naabu is an open-source CLI recon tool for network mapping and security auditing. Using naabu we can find open ports, services, possible vulnerability with a script and much more can be done.
With Naabu, thousands of IP addresses can be scanned simultaneously using asynchronous scanning techniques.
To determine which ports are open and which services are running, the tool sends out TCP and UDP probes to target hosts.
In order to extract information from open services, such as the software version and configuration details, banner grabbing can be performed.
Advertisement
Who Developed Naabu
I can find that the first commit was done by Ice3man543 so, a big salute to him who started it and also I thank other developers who developed the naabu tool.
Now, The tool is maintained and devloped by projectdiscovery.io and also I thank sandeep singh.
How to Install Naabu
Make sure you install go lang
Win: go get -u github.com/projectdiscovery/naabu/cmd/naabu Linux: sudo apt-get install naabu
Naabu Features
- Fast And Simple SYN/CONNECT/UDP probe based scanning
- Optimized for ease of use and lightweight on resources
- DNS Port scan
- Automatic IP Deduplication for DNS port scan
- IPv4/IPv6 Port scan (experimental)
- Passive Port enumeration using Shodan Internetdb
- Host Discovery scan (experimental)
- NMAP integration for service discovery
- Multiple input support – STDIN/HOST/IP/CIDR/ASN
- Multiple output format support – JSON/TXT/STDOUT
How to Use Naabu
Follow every example carefully by end of thispost you will be very familiar with the tool and if you continuously work for 2 -4 hrs you will become a pro.
Work hard until you reach your goal let’s make hand’s wet
BY STUPID ME ????
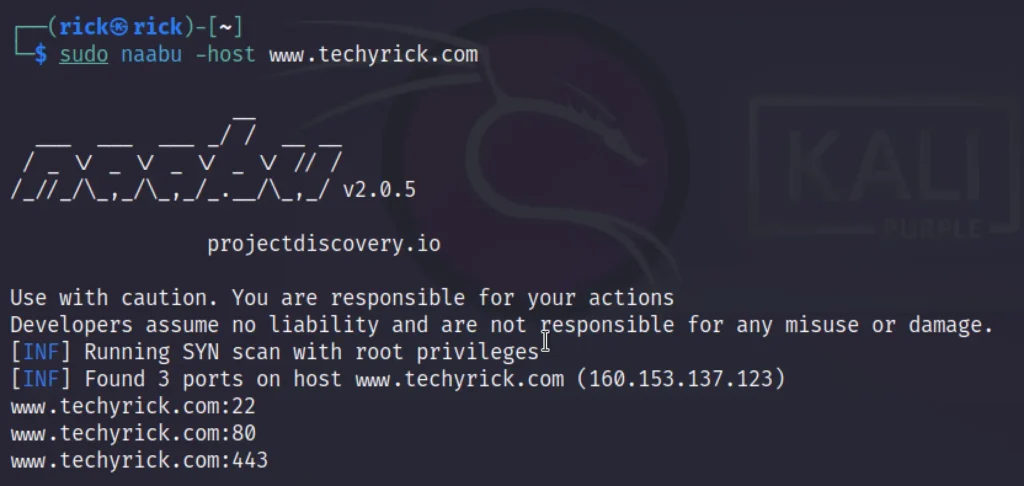
Example 1, Standard Scan
Whatever you call it, Standard scan or Default scan. By doing this you get very little information about the target site.
It’s because by default the naabu scans for Top 1000 ports.
naabu -host www.techyrick.com
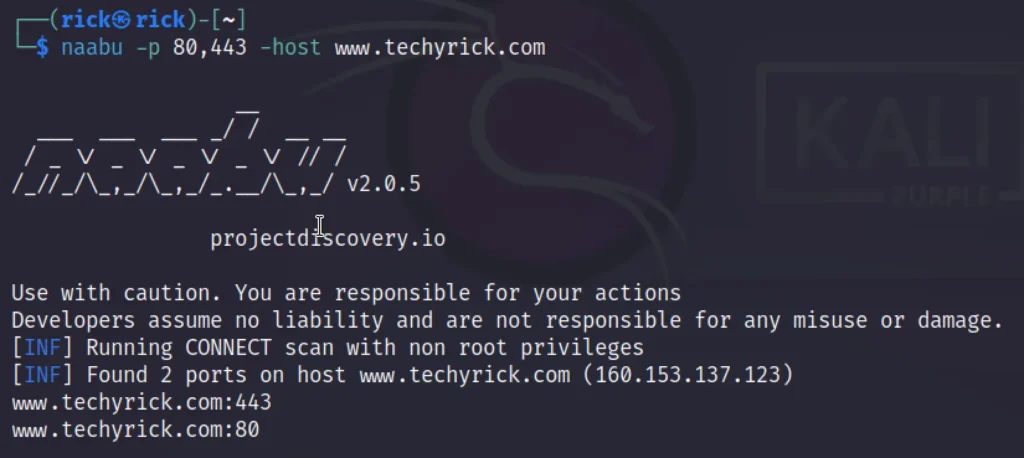
Example 2, Specific Port Scan
To do a specific port scan you can use the command between the ports and mention -p syntax at front.
naabu -p 80,443 -host www.techyrick.com
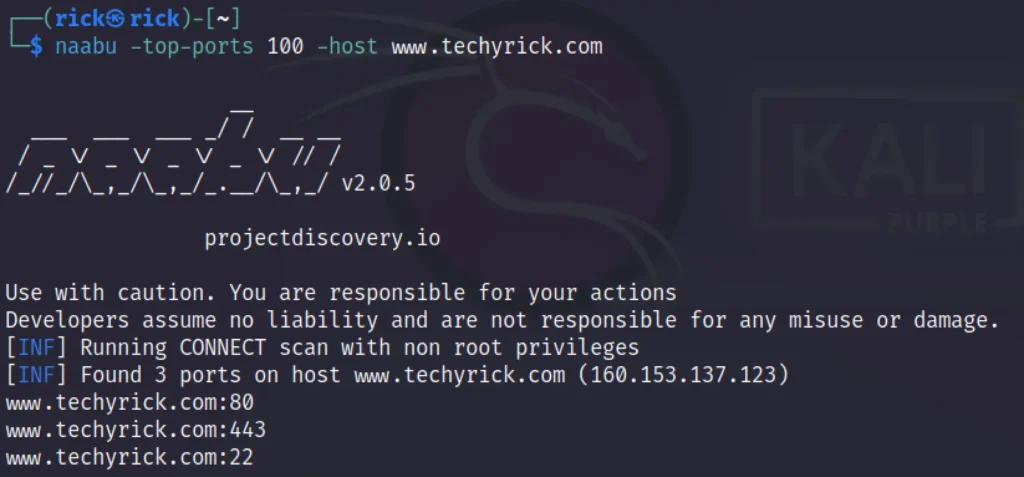
Example 3, Scanning Top 100 Ports
To scan for the top 100 post, You can use the below command
naabu -top-ports 100 -host www.techyrick.com
Found a mistake here, I tried to scan for the top 100 ports but I got the below result, That’s the port 443. But why ❓
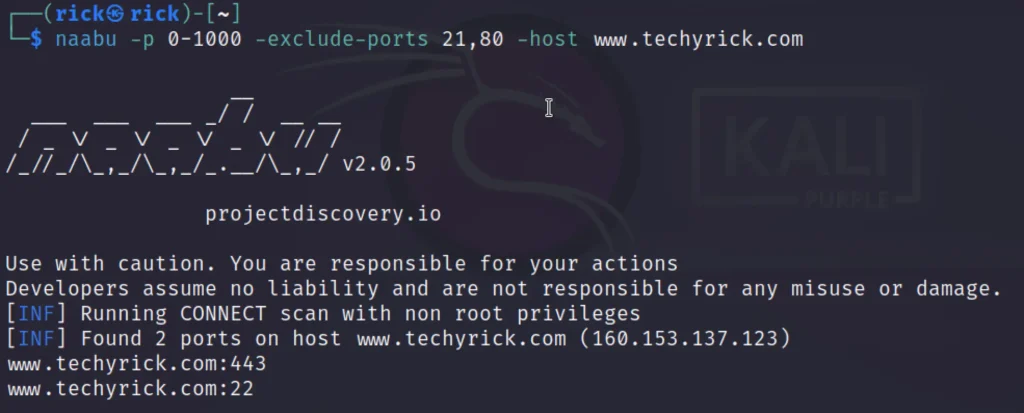
Example 4, Exclude Ports
We can also exclude the ports, We no need to scan for below is the command try it out
naabu -p 0-1000 -exclude-ports 21,80 -host www.techyrick.com
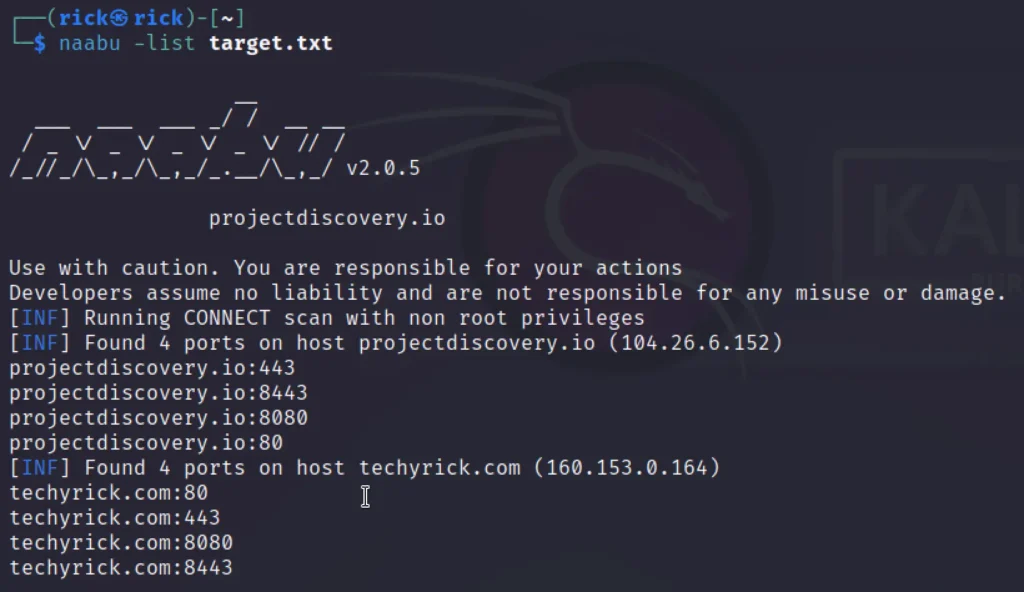
Example 5, Scanning List
To scan for list of domain names, Create a file with target domains and scan the file.
naabu -list target.txt
Example 6, Integration with Nmap
The naabu tool has integrated the nmap features too, So let’s give a try on how that works.
echo techyrick.com | naabu -nmap-cli 'nmap -sV -oX nmap-output'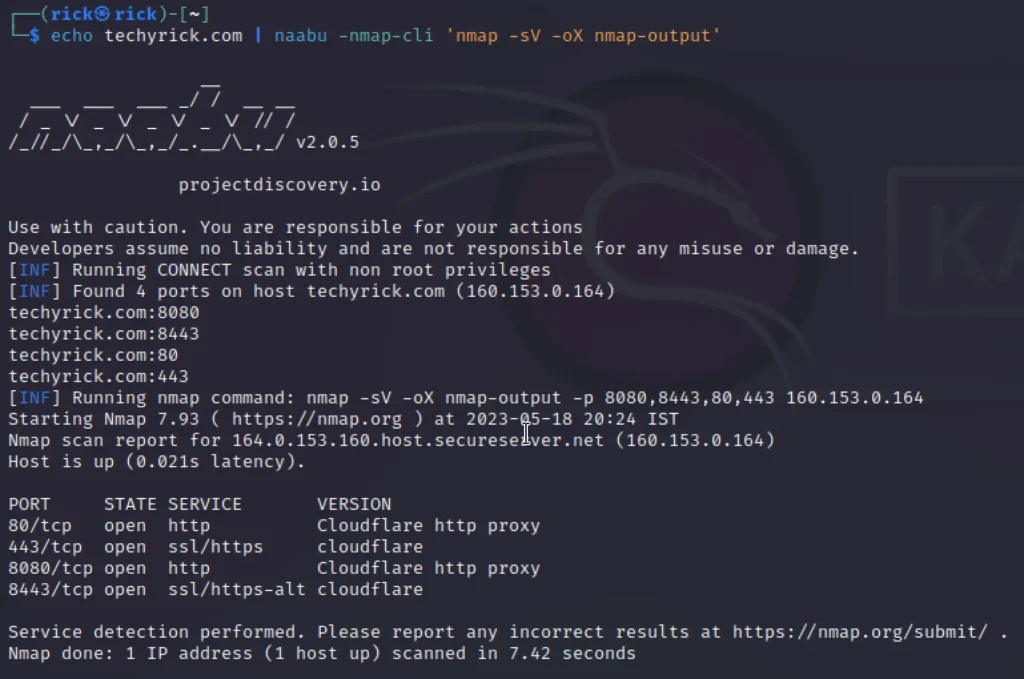
Conclusion
In this post, You have learnt about the Naabu tool, Hope you like it. In my opinion the naabu tool is just an another network mapping tool.
But still I appreciate their work, So I would rate a solid 6 out of 10 for this tool. There is no script for scanning that’s a major disadvantage.
See you in the next post ❤️
Advertisement
Also Read: Unicornscan Full Tutorial
Also Read: Nmap Scripting Engine




