Introduction
In the ever-evolving digital landscape, staying ahead of the curve is paramount. In this age of information, mastering the art of cracking ZIP passwords can be a game-changer.
Today, we delve into the world of fcrackzip, a versatile tool that has gained recognition in the cybersecurity realm.
Buckle up as we explore the intricacies of fcrackzip, from its functionality to its applications, best practices, and even how to get started with it.
To Download Fcrackzip [Click Here]
Advertisement
Video
Understanding Fcrackzip
Fcrackzip is a powerful command-line utility designed primarily for cracking password-protected zip files.
This open-source tool is highly valuable, especially for cybersecurity experts, ethical hackers, and digital forensics specialists.
Fcrackzip excels in one essential task – recovering lost or forgotten passwords for encrypted zip archives, making it an indispensable asset for individuals and professionals alike.
Who Developed Fcrackzip
Fcrackzip, the password cracking tool for zip files, was developed by Marc Lehmann. It is an open-source software project, and Marc Lehmann has contributed significantly to its development and maintenance.
Fcrackzip has been a valuable tool in the field of data security and password recovery, helping users regain access to password-protected zip archives.
Why, the hell, another zip cracker ❓
As is often the case, software programs are developed in response to real-world needs.
The story behind Fcrackzip is no exception. Although I didn’t frequently use zip files, a recent situation required me to find a reliable password cracker.
My initial thought was, “There must be plenty of options available online. I’ll simply choose one.”
However, this quest proved to be more challenging than I anticipated. None of the zip crackers I came across seemed to meet my requirements.
Some couldn’t handle more than one zipfile, while others were exceptionally slow in their operation.
Additionally, none of them supported the brute force attacks I needed for my task. To make matters worse, I couldn’t find the source code for any of these tools.
HOPE YOU KNOW WHY WE NEED ANOTHER ZIP CRACKER ????
Advertisement
Features of Fcrackzip
- Multiple Attack Modes
- Dictionary Attack
- Brute Force Attack
- Support for Zip Encryption Methods
- Customizable Password Length
- Progress Monitoring
- Optimized Performance
- Cross-Platform Compatibility
- Open-Source
- Community Support
- User-Friendly Interface
FCrackzip Commands
Here are some useful commands in Fcrackzip for performing common password cracking tasks:
Perform a Dictionary Attack:
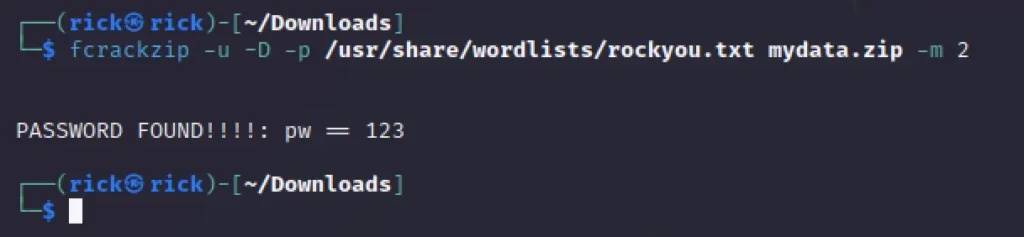
fcrackzip -u -D -p /path/to/dictionary.txt /path/to/lockedfile.zip
-u: Unzip the file if the password is found.-D: Use a dictionary attack.-p: Specify the path to the dictionary file containing potential passwords./path/to/lockedfile.zip: The path to the locked zip file.

Perform a Brute Force Attack (Specify Password Length):
fcrackzip -u -b -c 'charset' -l min:max /path/to/lockedfile.zip
-u: Unzip the file if the password is found.-b: Use a brute force attack.-c 'charset': Define the character set to use for the attack (e.g., ‘a’ for lowercase letters).-l min:max: Specify the minimum and maximum password length./path/to/lockedfile.zip: The path to the locked zip file.

Monitor Progress:
fcrackzip -u -D -p /path/to/dictionary.txt /path/to/lockedfile.zip -V
-V: Enable verbose mode to see progress updates during the cracking process.

Limit the Number of Passwords to Attempt:
fcrackzip -u -D -p /path/to/dictionary.txt /path/to/lockedfile.zip -b -l min:max -c 'charset' -m limit
-m limit: Set a limit on the number of passwords to attempt.
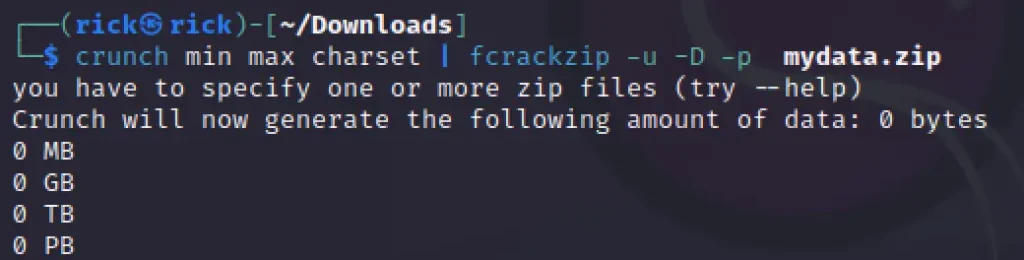
Generate a List of Common Passwords:
crunch min max charset | fcrackzip -u -D -p - /path/to/lockedfile.zip
This combination of commands uses crunch to generate a list of passwords and then pipes it to Fcrackzip for testing.
Conclusion
In conclusion, Fcrackzip is a versatile tool, empowering users to recover lost zip file passwords effectively. Its diverse attack modes and open-source nature make it a valuable asset in data security.
Also Read: Medusa Full Tutorial
