Introduction
Email spoofing is a way of sending fake emails to people.
Criminals use these methods for attacks like phishing or spam, which can create hidden access points that look legitimate.
Public email servers can be exploited for spoofing attacks. If your mail server is set up with an OPEN RELAY, attackers can perform these dangerous spoofing attacks.
An open relay is an SMTP server that lets a third party send or receive emails that are not from or for local users.
Spam senders often target such servers to send fake emails to victims’ inboxes.
Finding a vulnerable mail server on a public network with an open relay might be how these email spoofing attacks are done.
Discovery of Vulnerable Mailserver — Email spoofing
The attacker will try to find a mail server by using tools like Dig or Nslookup, or by simply using a legitimate website like VirusTotal to find the subdomains of the target.
Telnet or Netcat Client
Many ISPs block or restrict SMTP connections on port 25. Here’s why:
According to the Internet Engineering Task Force (IETF), Request For Comments (RFC) 821 established port 25 as the default channel for transmitting Internet email.
We still use port 25 as the main way to send email between two mail servers.
Later, RFC 2476 suggested adding a new specification for internet email. It proposed separating message submission and message relay, defining that message submission should occur over port 587 to meet new policy and security requirements.
Finally, RFC 2487 introduced the STARTTLS protocol, which encrypts communications over the internet for secure SMTP.
To check if these ports are open, you can use Telnet or Netcat client tools.


The figure above shows that you’re on the external mail server. It should not connect, and you should get an error.
SMTP Commands
Every action you take with email, like composing and sending, uses SMTP commands behind the scenes. Understanding these commands helps you understand open mail relay.
- HELO: The first SMTP command to start the conversation, identifying the sender server by its domain name.
- EHLO: Similar to HELO, but used when the server supports Extended SMTP protocol.
- MAIL FROM: The sender specifies the source email address in the “From” field, beginning the email transfer.
- RCPT TO: Identifies the recipient of the email.
- DATA: Starts the transfer of the email’s content.
- VRFY: Asks the server to verify if a particular email address or username exists.
- AUTH: Authenticates the client to the server using a username and password.
- HELP: Requests information useful for the successful transfer of the email.
- EXPN: Confirms the identification of a mailing list.
- RSET: Stops the ongoing email transmission or terminates continuous mail from the server.
- ETRN or TURN: Changes roles between the client and the server, with the client acting as the SMTP server.
- QUIT: Terminates the SMTP conversation.
Mailserver User Enumeration
The attacker uses the VRFY SMTP command to find out the existing email addresses on the server.

The figure above shows the mail server replying with a 250 code, indicating that the usernames are found on the mail server.
Composing the spoofing mail
Here, we have identified two usernames on the mail server.

The figure above shows the SMTP commands MAIL FROM and RCPT TO being used to send a forged email to the receiver.
- Syntax for the sender:
MAIL FROM: balaji@123.com - Syntax for the receiver:
RCPT TO: gurubaran@123.com
The mail server will reply with a 250 code, indicating that both the sender and receiver are accepted.
Sending Forge mail
The last step is to send fake emails to recipients using this open relay. Use the SMTP command DATA to write the email in the command line.
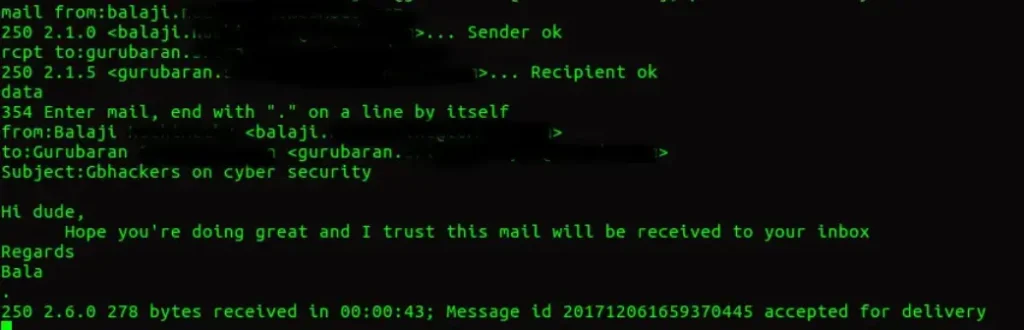
Executing the DATA command will prompt a 354 code, allowing us to compose our email to the target.
In the example above, the email is forged with sender, recipient, subject, and body content. After composing the email and pressing Enter, the spoofed mail is sent to the receiver.
Remember, never configure your mail server with an open relay. Instead, implement security measures such as authentication with user accounts and encryption with STARTTLS.
Conclusion
In conclusion, conducting an SMTP pentest reveals critical vulnerabilities in mail servers that could be exploited by attackers.
Through various SMTP commands like VRFY and DATA, potential threats such as email spoofing and unauthorized access can be identified.
It underscores the importance of securing mail servers with measures like authentication and encryption to mitigate risks and ensure the integrity of email communications. Organizations should prioritize regular security assessments to safeguard against potential exploits and protect sensitive information.
Also Read: Pentesting Telnet
