Introduction
In this post, Let’s learn about Logs ????, Hope you have learnt about the mounting and the un mounting. Below is the video format of the check it out ????????
Video ????
Let’s start ????
If you have any doubts you can watch the video above or you can ask questions in Discord I have given my Twitter profile link so you can ask there. ????????
https://odysee.com/@techyrick:d
https://twitter.com/HacklikeHacker
Rsyslog Locate and Configure
To locate the rsyslog we can use the locate utility and configure. In kali the rsyslog is locate in the below directory…
/etc/rsyslog.conf
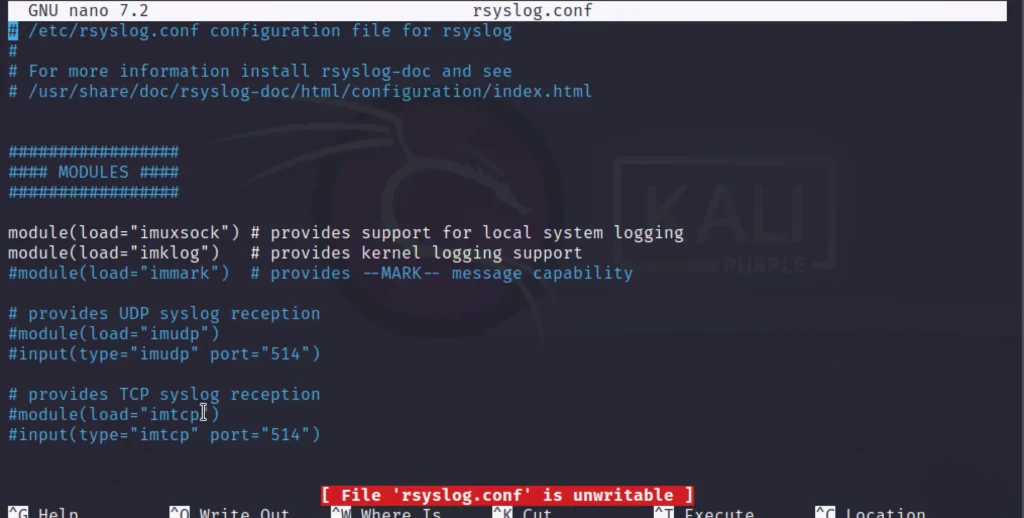
There are thre category in rsyslog they are;
- Modules
- Global Directives
- Rules
Just read the comments you can do the configurations by yourself…
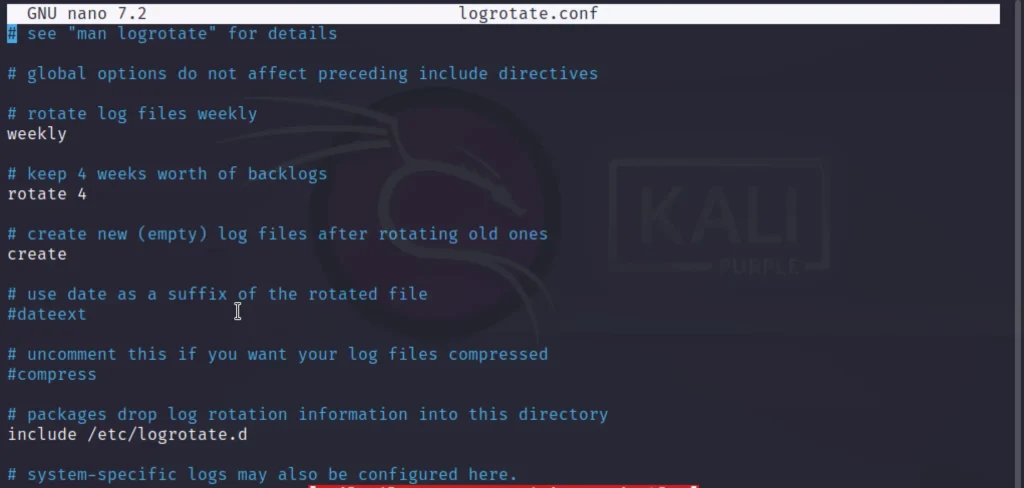
Automatically cleaning up logs
We can clean the logs automatically by configuring the logrotate.conf You can go to the below directory to see how to configure.
/etc/logrotate.conf
Deleting files without getting caught
The shred command is a utility available in Linux and Unix-like operating systems that securely deletes files by overwriting their contents before removing them. It is commonly used when you want to ensure that the deleted files cannot be easily recovered.
shred <file> shred here.txt

Disabling logging
To disable logs we can just use the below command that is ????????
service rsyslog stop

Conclusion
In this post, You have learned about the basic use of logs hope it helped you see you in the next post ????????❤️
THE END