Introduction
In this post, you will learn what is dnsenum and how to work with the tool and also addition I have given some examples and extra information about the tool. Do check the video format of the post ????, My apologies if you didn’t like my voice!!!
Video:
What is Dnsenum
Firstly, the DNSenum stands for “Domain name server enumeration“, With this tool we can easily gather the target DNS information. I think you know very well what is in DNS. If you don’t know don’t worry I will explain ????
The Domain name server contains information such as the TXT and NS, A and AAAA, MX records and much more information which are related to the target.
I simple words, this tool is used to scan and get all the information related to the DNS servers. If you have any doubt comment down below ???? I will help.
Also Read: Information gathering using crt.sh
Advertisement
Who developed the dnsenum tool
The tool was developed by flip waeytens and he has also given his mail if you have any doubt you can directly ask him and the tool was completely written in Perl language.
To download this tool in Linux distribution just enter Sudo apt-get install dnsenum
What the dnsenum tool can do
- Host’s addresse A and AAAA address.
- Namservers NS information.
- MX record, the mail records.
- Subdomains serach.
- Brute force subdomains from files.
- Whois lookup.
- Reverse lookup.
Advertisement
Dnsenum useful commands
- –dnsserver – Use this DNS server for A, NS and MX queries.
- –enum – Shortcut option equivalent to –threads 5 -s 15 -w.
- -h –help – Print this help message.
- –noreverse – Skip the reverse lookup operations.
- –subfile – Write all valid subdomains to this file.
- –threads – The number of threads that will perform different queries.
- -v, –verbose – Be verbose: show all the progress and all the error messages.
- f, –file – Read subdomains from this file to perform brute force
- -o –output – Output in XML format. Can be imported in MagicTree
Advertisement
How the the dnsenum works
Example1: Default scan
In the first example we are going to see about this command
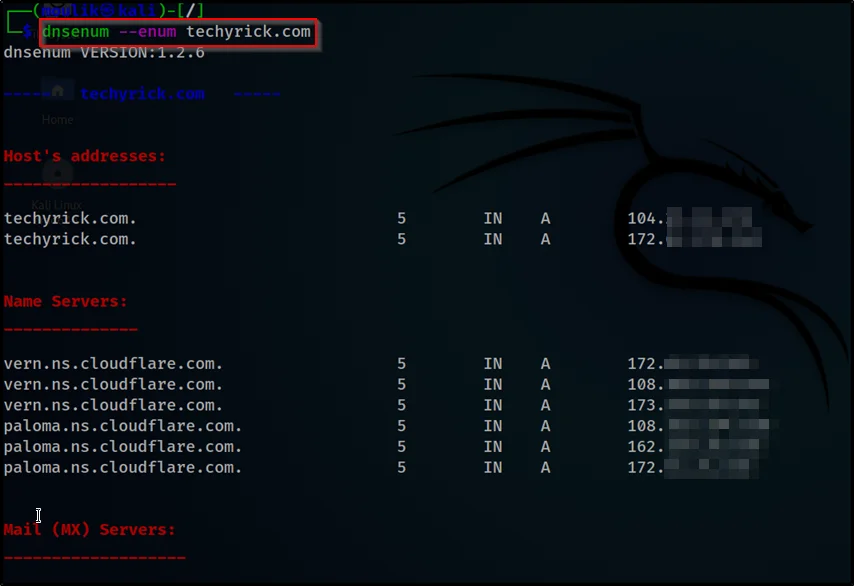
dnsenum --enum techyrick.com
–enum scan for all the dns result in general
Example2: Subdomain scan
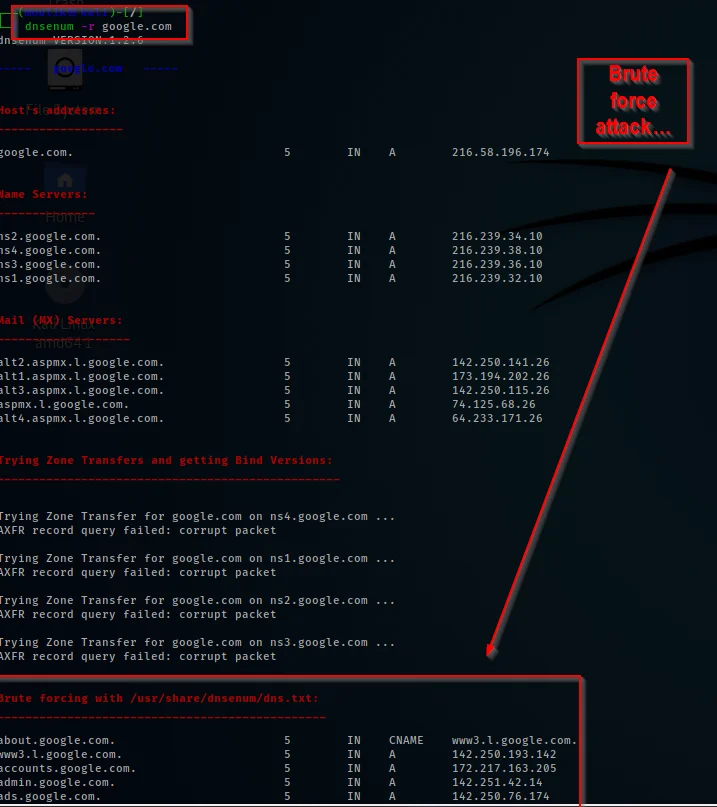
The next command is we are going to do a bute force on the possible subdomains found ????
dnsenum -r techyrick.com
Give a try and the result will be like this
Example3: Verbose, Time
In this example, we are going to include the verbose and the timeout and also no reverse
dnsenum --enum --noreverse -t -V techyrick.com

Example4: Subdomain bruteforce
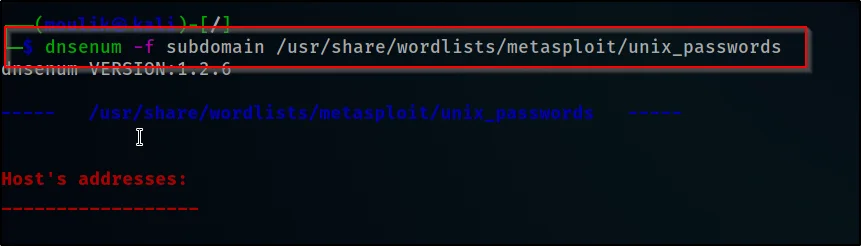
In this example, we are doing brute force from our own list of subdomain
dnsenum -f subdomain /usr/share/wordlists/metasploit/unix_passwords
Example5: Whois
Doing a whois lookup of c class domains
dnsenum -w techyrick.com

Example6: Save output
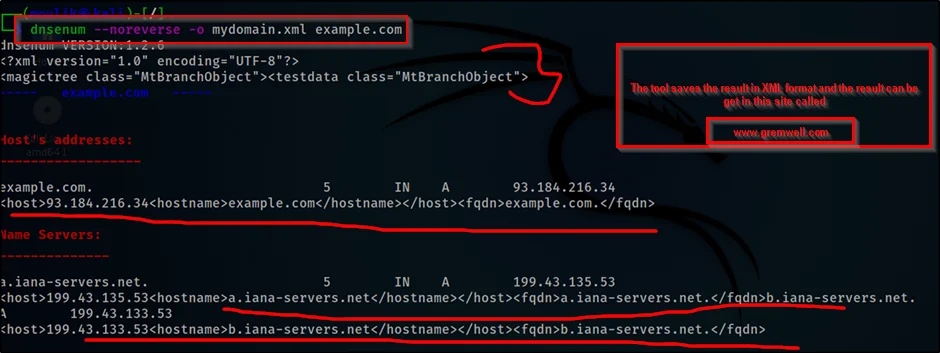
Finally, Iam going to teach you how to save the result, It’s very simple to use this command
dnsenum --noreverse -o mydomain.xml example.com
Conculusion
In conclusion, According to my knowledge, this tool is somewhat good but the tool has lots of unwanted commands which one will not use in their lifetime. The alternative for this tool is Dmitry, easy to use and has few commands.
Advertisement
Also Read: Weleakinfo info gathering
Also Read: theHarvester from noob to pro





I am really enjoying the theme/design of your weblog. Do you ever run into any internet browser compatibility problems? A number of my blog visitors have complained about my website not working correctly in Explorer but looks great in Opera. Do you have any recommendations to help fix this issue?
For different browsers the layouts will change don’t worry abou that