Introduction
Reverse engineering is a crucial skill for cybersecurity professionals, software developers, and security enthusiasts. It involves dissecting and understanding the inner workings of software and hardware to uncover vulnerabilities, optimize performance, or simply gain insights into how something functions. One of the most powerful and versatile tools for reverse engineering is Ghidra.
Video
What is Ghidra ❓
Ghidra is an open-source software reverse engineering (SRE) framework developed by the National Security Agency (NSA). Released to the public in 2019, Ghidra quickly gained popularity due to its extensive feature set and user-friendly interface. It is designed to assist analysts in understanding compiled code across various platforms, enabling them to analyze malicious software, perform vulnerability research, and more.

The History of Ghidra
The roots of Ghidra can be traced back to the 1990s when the NSA started developing an internal SRE tool. Over the years, it evolved into a sophisticated suite of reverse engineering capabilities. In 2019, the NSA surprised the cybersecurity community by open-sourcing Ghidra, making it freely available to the public.
Key Features of Ghidra
Decompilation
One of Ghidra’s standout features is its decompilation capability. It can transform machine code into human-readable C code, making it easier for analysts to understand the functionality of a program.
Disassembly
Ghidra provides robust disassembly features, allowing users to view the assembly instructions of a binary file. This level of insight into the low-level code is essential for reverse engineering tasks.
Scripting Support
Ghidra supports scripting in various languages, such as Python, enabling analysts to automate repetitive tasks and create custom tools.
Collaborative Analysis
With Ghidra Server, multiple analysts can collaborate on the same project simultaneously, sharing findings and insights in real-time.
Advertisement
Getting Started with Ghidra ⬇️
Installation and Setup
To begin using Ghidra, download the latest version from the official website and follow the installation instructions. Once installed, users can customize preferences to suit their workflow.
$ sudo apt-cache search java18$ sudo apt install openjdk-17-jdk
Installation steps:
Extract the zip file using the command –
$ unzip ghidra_10.2.3_PUBLIC_20230208.zip
Navigate to the directory and run this executable file –
$ ./ghidraRun
User Interface Overview
Ghidra’s user interface may seem overwhelming at first, but a basic understanding of its core components simplifies the learning curve.
Loading a Binary
Learn how to load a binary executable into Ghidra for analysis, and explore various loading options and configurations.
Step 1: Download and Install Ghidra
To get started, you’ll need to download the Ghidra application from its official website. If you haven’t installed Ghidra yet, don’t worry; it’s a simple process that takes just a few minutes. Follow the installation instructions, and soon Ghidra will be up and running on your computer.
Step 2: Create or Open a Project
When you launch Ghidra, you’ll encounter the option to create a new project or open an existing one. A project acts as a container for your reverse engineering work, housing all the data and configurations related to your analysis.
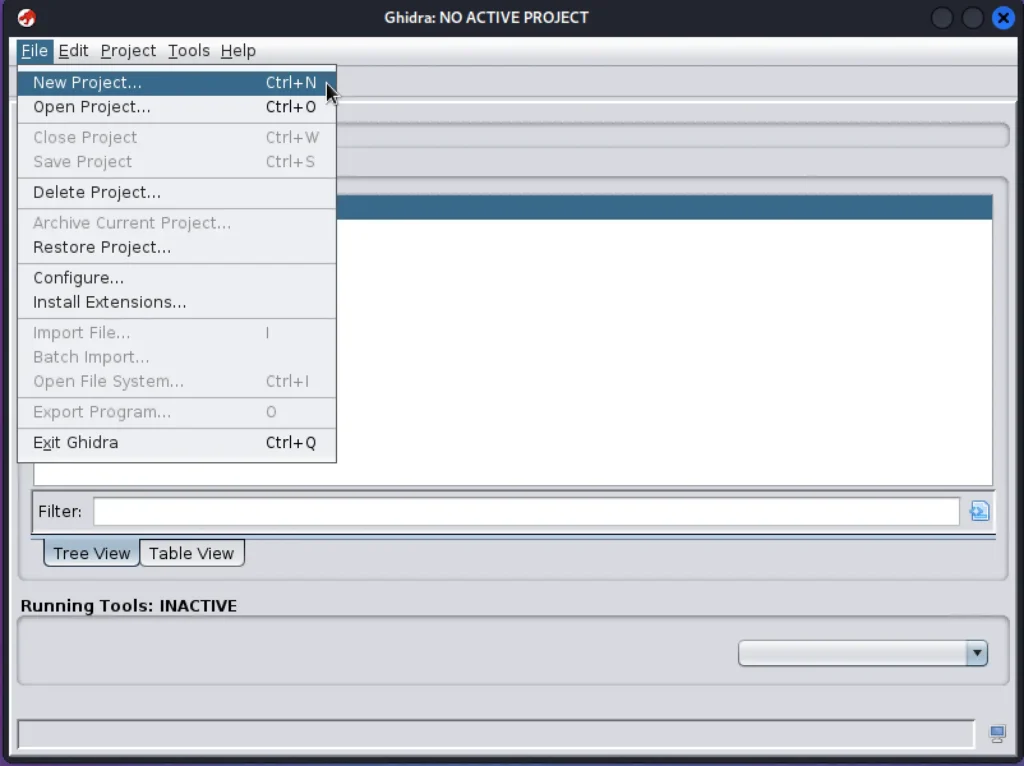
To start a new project, click on “File” in the Menu Bar, then select “New Project.” Follow the on-screen instructions to specify a name and location for your project. If you have an existing project, click on “File” in the Menu Bar, then select “Open Project,” and navigate to the project’s location on your computer.
Step 3: Import the Binary
With your project ready, you can now import the binary file that you wish to analyze. This is the key step where Ghidra’s magic begins.
Click on “File” in the Menu Bar, then select “Import File.” In the “Import File” window, browse to the location of the binary file on your computer. Once you’ve found the binary, select it and click “OK” to proceed.
Step 4: Choose the Processor
After importing the binary, Ghidra will request you to select the appropriate processor type that matches the binary’s architecture. If you’re unsure about the architecture, you can refer to the binary’s documentation or specifications to determine the correct processor type.

Step 5: Load the Binary
Ghidra will now analyze the binary file, a process that might take some time depending on the binary’s size and complexity. Don’t worry; Ghidra will keep you informed with a progress bar during the analysis. Once completed, the binary’s disassembled code will be at your disposal in Ghidra’s powerful CodeBrowser.
Step 6: Start Reverse Engineering
Congratulations! You’ve successfully loaded the binary into Ghidra. Now, the real adventure begins. Dive into the CodeBrowser, explore the disassembled code, and start identifying functions and analyzing the binary’s behavior.

With Ghidra as your guide, you have a robust toolset to unravel the mysteries of any binary file. Happy reverse engineering!
Understanding the Core Components
CodeBrowser: Your Window into Disassembled Code
The CodeBrowser is at the heart of Ghidra’s powerful features. Acting as a central hub, it grants analysts an intuitive interface to explore the logic flow of the program.
This indispensable tool allows you to dive into the binary’s intricacies, comprehend its assembly instructions, and uncover the underlying program structure. With CodeBrowser, you can navigate through the code effortlessly, empowering you to conduct a thorough analysis.
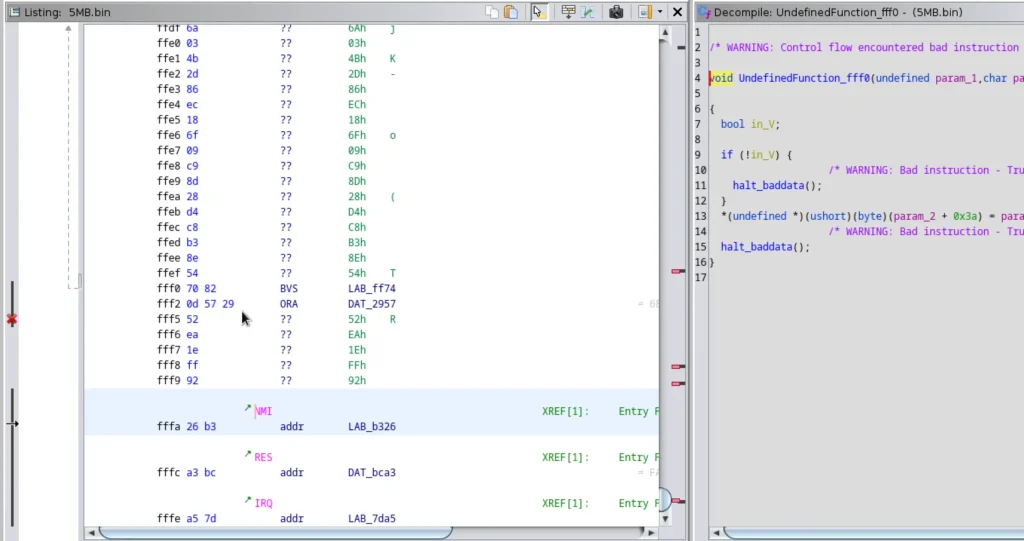
Listing Panel: Deep Dive into Disassembled Code
This tool offers the Listing Panel for a detailed view of the disassembled code. This feature provides analysts with deeper insights into the binary’s instructions, memory addresses, and mnemonics.
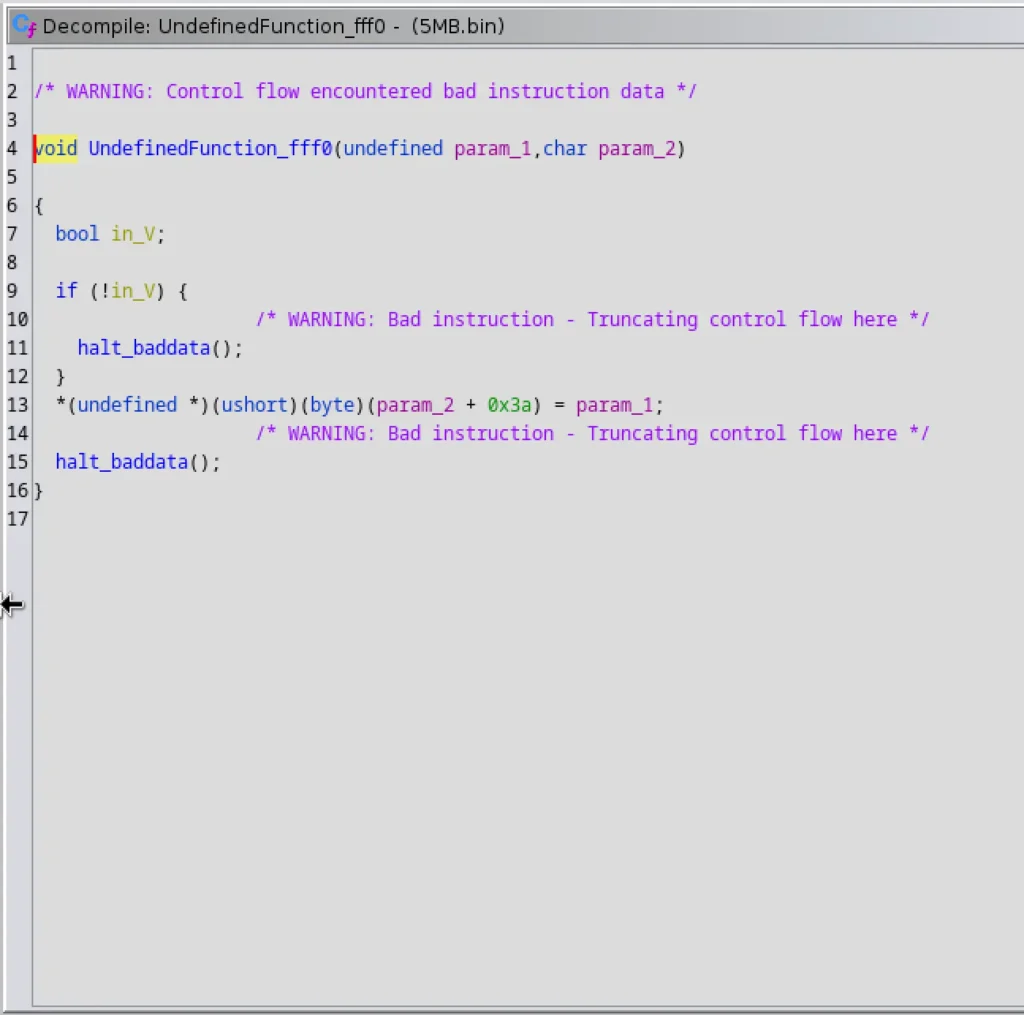
With the Listing Panel, you get a comprehensive overview of the code, enabling a more profound understanding of the binary’s inner workings. It’s the perfect tool to gain valuable insights into the code’s complexities.
Function Graph: Visualizing Program Behavior
The Function Graph, a visual representation in this tool, allows you to understand the control flow of functions within the binary.

By visually mapping how functions interact and influence the program’s behavior, you can quickly grasp the code’s execution flow. The Function Graph streamlines your analysis, helping you identify potential vulnerabilities and patterns efficiently.
Data Type Manager: Streamlining Analysis Efficiency
To boost analysis efficiency, Ghidra’s Data Type Manager lets you define and manage custom data types. This invaluable feature becomes crucial when dealing with complex data structures.
It enables you to organize and manipulate data effectively, smoothing your reverse engineering process. With the Data Type Manager, you gain deeper insights into the binary’s data organization, making your analysis even more comprehensive.

By leveraging these core components of Ghidra, you unlock the true potential of reverse engineering. The CodeBrowser, Listing Panel, Function Graph, and Data Type Manager act as your guiding tools, unveiling the hidden mysteries within the binary. With Ghidra’s assistance, you are equipped to tackle any reverse engineering challenge with confidence and precision.
Advertisement
Analyzing Binaries with Ghidra
Identifying Functions and Control Flow
Welcome to the world of Ghidra, where analyzing binaries becomes a breeze! With Ghidra’s assistance, you’ll effortlessly spot functions and understand how they flow within the program. It’s like having a secret decoder to unlock the program’s logic and behavior.
Cross-References and Data Flow
Ghidra’s magic extends to cross-references and data flow, allowing you to trace specific data throughout the binary. This invaluable insight helps you unravel data dependencies, revealing critical clues during your analysis.
Patching Binaries: Fixing and Enhancing
Need to fix security holes or add some extra features? Ghidra has your back! You’ll learn the art of patching binaries, tweaking them while preserving their core functionality. It’s like wielding a magic wand to bring improvements to your software.
Advanced Ghidra Techniques
Customizing and Extending Ghidra: Tailored to You
Make Ghidra your very own! Customize it to match your unique style and preferences, optimizing your reverse engineering process. And that’s not all! Explore Ghidra’s extensions, unlocking even more powers to suit your specific needs.
Analyzing Obfuscated Code: Crack the Mystery
Obfuscated code might seem like a puzzle, but Ghidra has the answers! With its powerful tools, you’ll decode the secrets of obfuscated code, unraveling its hidden brilliance.
Exploiting Vulnerabilities: Ethical Responsibility
With great power comes great responsibility! Ghidra helps you handle discovered vulnerabilities responsibly, ensuring an ethical approach to your reverse engineering adventures.
Empowered by Ghidra, you’ll become a binary analysis wizard, confidently navigating through functions, understanding data flow, and gracefully patching binaries. Embrace the excitement of advanced techniques while unlocking the secrets hidden within your binaries. Ghidra is your trusted companion on this reverse engineering journey, always ready to lend a helping hand and reveal the magic of binary analysis!
Ghidra vs. Other Reverse Engineering Tools
Compare Ghidra with other popular reverse engineering tools to determine which best suits your needs.
Practical Use Cases
Malware Analysis
Ghidra is a valuable tool in the fight against malware, providing insights that aid in malware identification and eradication.
Software Security Auditing
Perform security audits on software applications to identify vulnerabilities and weaknesses.
Game Hacking
Explore how Ghidra can be used for game hacking and modifying game behavior.
Conclusion
Ghidra has revolutionized the world of reverse engineering, providing a powerful and accessible tool for analyzing binaries and understanding software at a deeper level. Whether you are a cybersecurity professional, a software developer, or a security enthusiast, mastering Ghidra is a valuable asset in your toolkit.
Frequently Asked Questions (FAQs)
- Q: Is Ghidra suitable for beginners in reverse engineering?A: Ghidra’s user-friendly interface and extensive documentation make it an excellent choice for beginners.
- Q: Can I use Ghidra for commercial purposes?A: Yes, Ghidra’s open-source license allows both personal and commercial use.
- Q: What platforms does Ghidra support?A: Ghidra runs on various platforms, including Windows, macOS, and Linux.
Also Read: Amass Full Tutorial
Also Read: Responder Full Tutorial





Khan👿❤👿❤