Introduction
This blog talks about how to solve the GET aHEAD challenge, which is one of the tasks in the picoCTF Web Exploitation section.
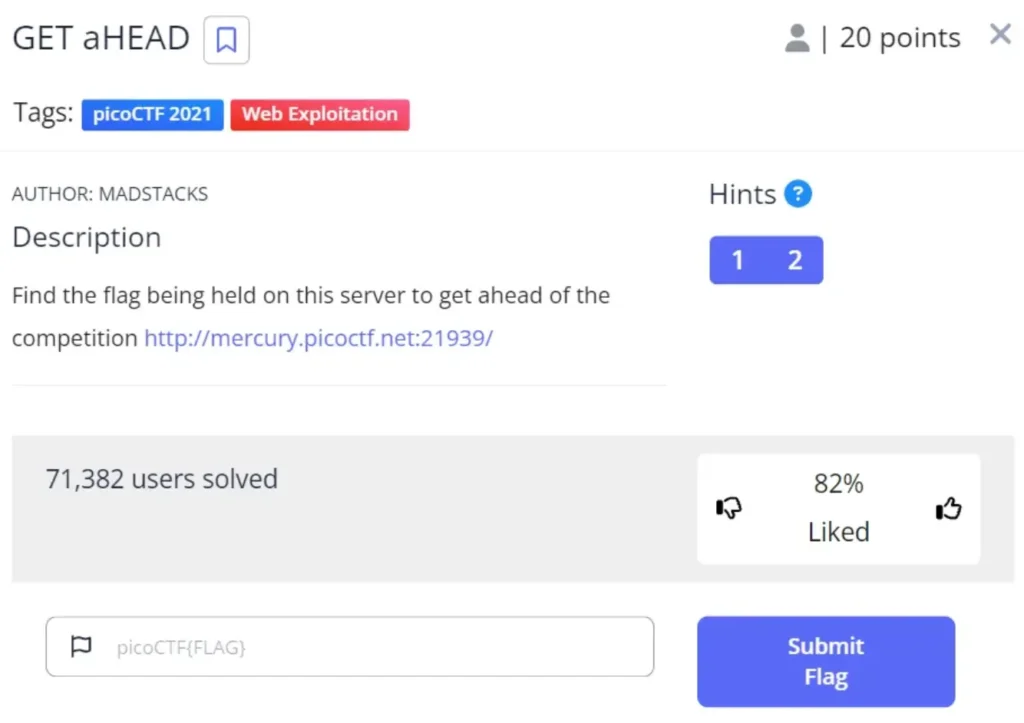
Solution
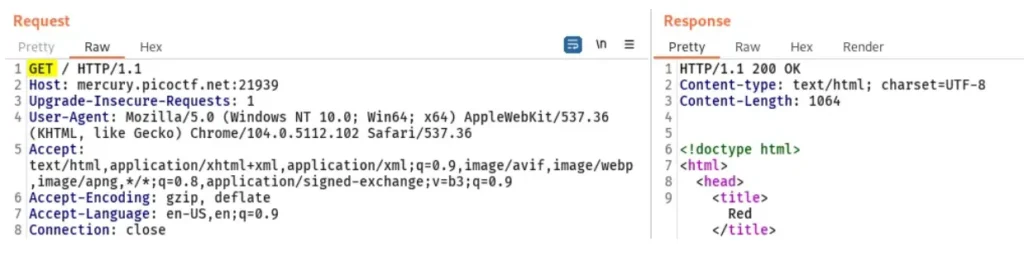
Here’s what you need to do: There’s a flag hidden on a server. You can access it through this link: http://mercury.picoctf.net:21939/ Just open the link in your web browser and use a Burp Suite tool to capture the requests and responses. That’s all!

Here’s what we’ve got: There are only 2 buttons on the app, and they change the page’s color when clicked. We’ve clicked both buttons and checked all the traffic captured so far in the tool, but nothing seems important.
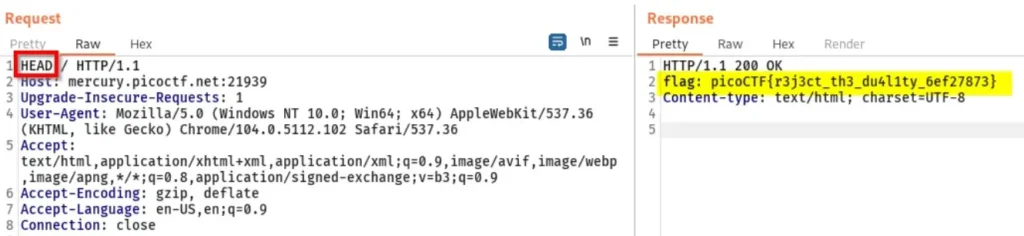
The challenge name, “Get aHEAD,” seems like a clue. “HEAD” is a known HTTP method, so let’s try changing the method from “GET” to “HEAD” in one of the captured requests and see what response we get.
Here’s something interesting: The flag value is shown in the response.
Challenge completed. Thank you.
Conclusion
In conclusion, by carefully analyzing the application, experimenting with different HTTP methods, and inspecting the responses, we successfully solved the challenge. This experience underscores the importance of thorough investigation and creative problem-solving in cybersecurity tasks.


