Introduction
Microsoft has confirmed a new problem on Windows 10. This issue lets regular users get access to local user passwords without needing administrator privileges.
It’s another vulnerability coming just after the PrintNightmare problem that was reported recently.
As the world figures out how to defend against this vulnerability, it raises the question: Is it fair to expect software to be both convenient and secure? After all, humans make mistakes when writing code.
This blog will talk about the vulnerability, discuss the risks it brings, and explore what kinds of security measures could help detect or stop attackers who exploit it. It will end with a description of an innovative way to protect Windows 10 users.
What is the SeriousSAM vulnerability?
The vulnerability came to light when Jonas Lyk mentioned on Twitter that non-admin users using Windows 11 Preview builds could access the SAM file if shadow volumes were enabled.
Soon after, other researchers confirmed that the issue also affected Windows 10 versions starting with build 1809. The security researcher community quickly dubbed the bug as SeriousSAM and HiveNightmare.
They even developed a couple of proof-of-concept exploits for others to test and confirm. Shortly afterward, a CERT announcement followed, along with official acknowledgment from Microsoft.
This bug allows any user in the “BUILTIN\Users” group to access VSS shadow copies of important on-disk registry hives, including SAM, SECURITY, and SYSTEM. Normally, these files are protected, and only users with admin privileges can access them. This exposure of three critical files poses significant security concerns.
C:\Windows\System32\config\SAM C:\Windows\System32\config\system C:\Windows\System32\config\security
What can an attacker do with this vulnerability?
Once a hacker gains access to a system through this vulnerability, they could do several harmful things:
- Upgrade their privileges to become a local administrator.
- Find out the default installation password for Windows.
- Get hold of DPAPI computer keys, which could be used to decrypt all other private keys stored within the computer.
- Obtain a Silver Ticket, which could serve as a pathway to gaining Domain Admin privileges.
How can one protect or mitigate this vulnerability?
The security community has suggested various ways to tackle the vulnerability, from adjusting file permissions to implementing rules in Endpoint products to block access to affected files.
However, it’s worth considering how an Active Defense strategy could offer protection against such attacks. Attivo’s EDN solution provides features that guard against unauthorized access to critical system information.
This could include important files like shadow copies of registry hives or stores of credentials. This capability helps restrict access to all vital information. The EDN suite already covers this specific vulnerability right from the start.
Here’s what happens when Kevin Beaumont’s proof-of-concept exploit runs on a vulnerable Windows 10 system without using the Attivo EDN solution:
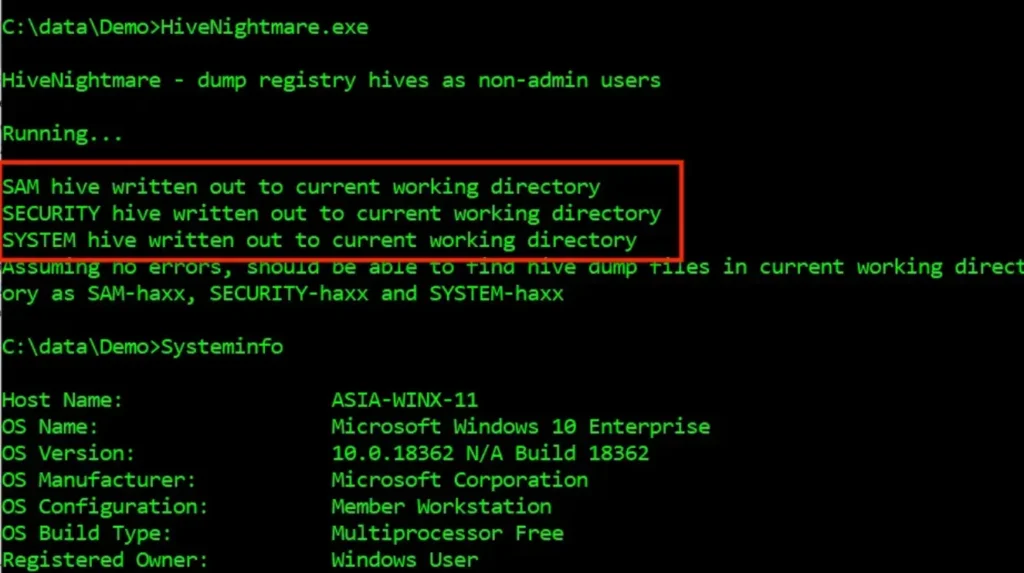
After installing the Attivo EDN solution on the same system, here’s how it appears when Kevin Beaumont’s proof-of-concept exploit runs:
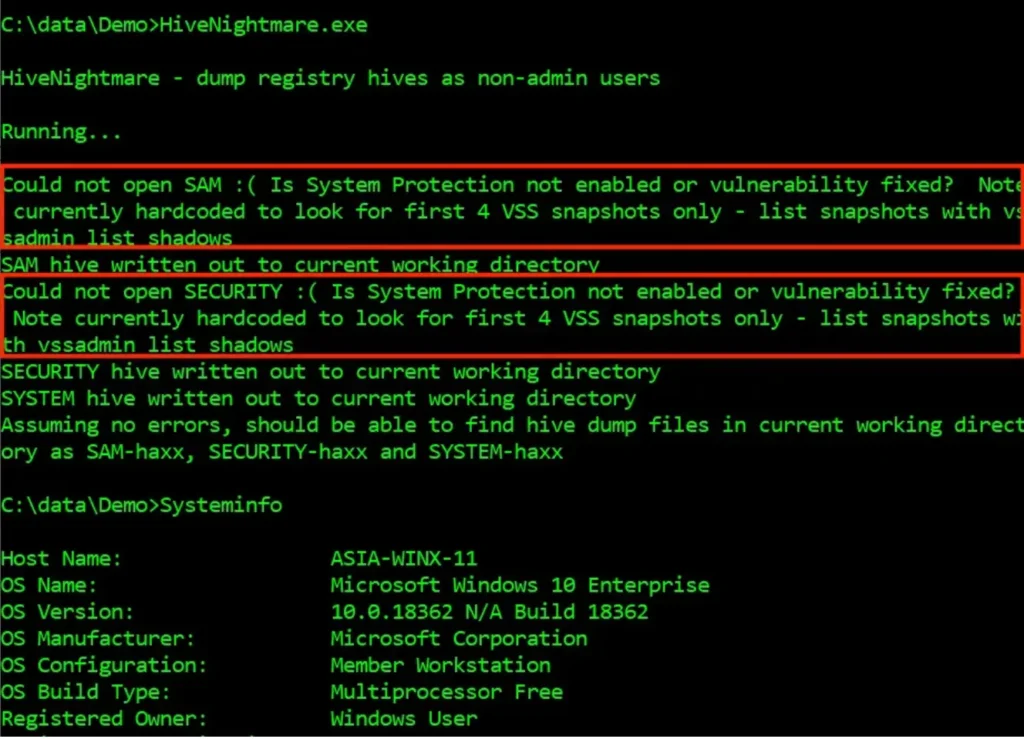
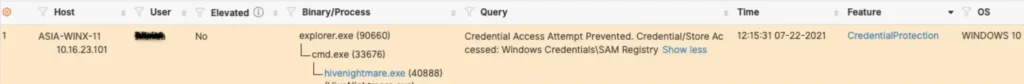
Meanwhile, the Attivo ThreatDefend platform records the attempt and its prevention in the console like this:
Conclusion
An effective way to defend against such attacks is by embracing a zero-trust model and tightly controlling access within the system.
While achieving a completely vulnerability-free world might not be feasible, implementing a strategy that assumes breaches and restricts access to resources (such as devices, files, registry, credential stores, password vaults, etc.) based on defined policies can greatly enhance protection against future attacks.
Also Read: SeImpersonatePrivilege – Windows Privilege Escalation


