Introduction
In this post, You will learn what is Modules in Metasploit and you will learn the different types of Modules.
If you haven’t read Lesson 1 and Lesson 2 of Metasploit [click here]
Video
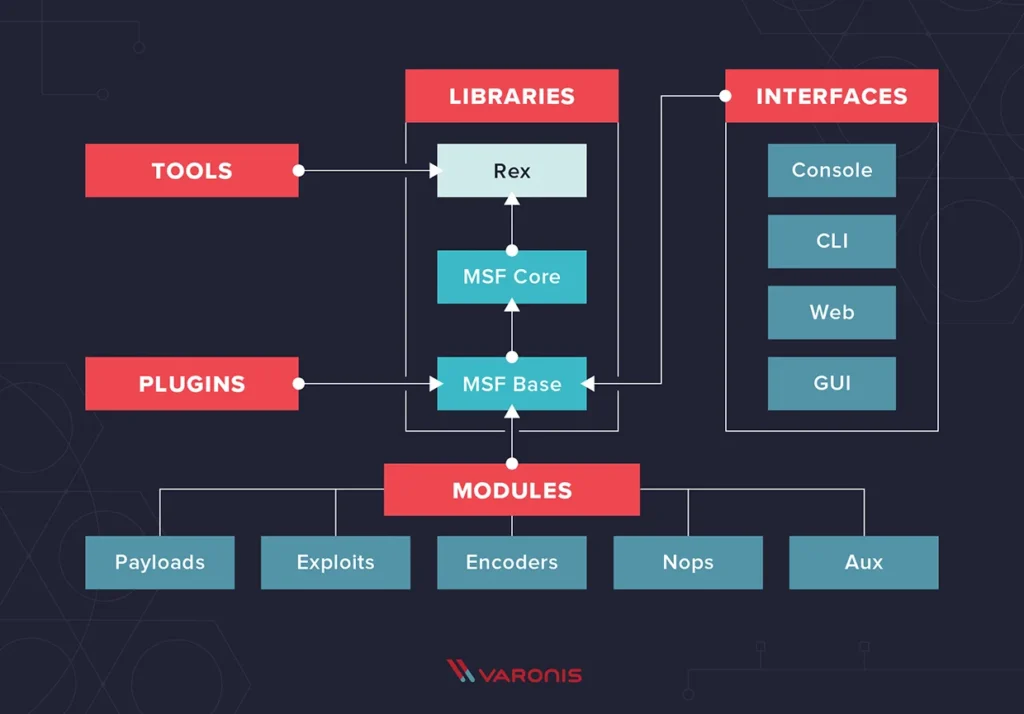
Metasploit Modules
There are 7 Modules in Metasploit they are;
auxiliary
encoders
evasion/windows
exploit
nops
payloads
post
To see the branch of Metasploit Modules [click here]
Modules are the important sections and most of the time you will be spending time in modules only.
You can find the Metasploit Modules in this location /usr/share/metasploit-framework/modules/
root@kali:~# ls /usr/share/metasploit-framework/modules/
auxiliary encoders exploits nops payloads post
Auxilary Module
The Auxiliary modules include port scanners, fuzzers, sniffers, parser, server, admin access and much more.
root@kali:~# ls /usr/share/metasploit-framework/modules/auxiliary/
admin client dos gather scanner spoof vsploit
analyze crawler example.rb parser server sqli
bnat docx fuzzers pdf sniffer voipEncoders
Encoders make sure the payloads make it to their destination. Here we can find the languages and much more.
root@kali:~# ls /usr/share/metasploit-framework/modules/encoders/
cmd generic mipsbe mipsle php ppc ruby sparc x64 x86evasion/windows
The evasion/windows directory is recently added to the Modules, Here we can find the modules to evade the windows system.
┌──(root????osboxes)-[/usr/…/metasploit-framework/modules/evasion/windows]
└─# ls
applocker_evasion_install_util.rb applocker_evasion_regasm_regsvcs.rb windows_defender_exe.rb
applocker_evasion_msbuild.rb applocker_evasion_workflow_compiler.rb windows_defender_js_hta.rb
applocker_evasion_presentationhost.rb process_herpaderping.rb
Exploit
Exploits are nothing but which use the payloads and exploit the target.
root@kali:~# ls /usr/share/metasploit-framework/modules/exploits/
aix bsdi firefox irix multi solaris
android dialup freebsd linux netware unix
apple_ios example.rb hpux mainframe osx windowsNops
The Nops Modules keep the size of the payload at the same size throughout the exploitation.
root@kali:~# ls /usr/share/metasploit-framework/modules/nops/
aarch64 armle mipsbe php ppc sparc tty x64 x86Payloads
The payloads are consist of codes that run remotely.
root@kali:~# ls /usr/share/metasploit-framework/modules/payloads/
singles stagers stagesPost
The Post modules contain Post exploitation modules that can be used on compromised targets.
┌──(root????osboxes)-[/usr/share/metasploit-framework/modules/post]
└─# ls
aix android apple_ios bsd firefox hardware linux multi networking osx solaris windows
Conclusion
In the next lesson let’s learn about the Metasploit fundamentals. This is just the basics of Metasploit Modules. Let’s dive deeper into Metasploit modules in later Lessons.




