Introduction
In this post, you will learn what is Nikto and how the tool works. The post is just an overview or summary of the tool. If you already knew something about this tool, comment down below.
What is Nikto?
Nikto is a web-based vulnerability scanner, It is open-source software written in Perl language. The primary target of the tools is to do vulnerability scanning.
There are some alternative tools such as Metasploit, comparing to Metasploit, Nikto is the best tool. Bug bounty hunters use this tool a lot and even hackers use this tool.
This tool scans 6,800 vulnerabilities that are commonly available on the sites. The tool also scans 250 platforms from an unpatched site. Also finds some vulnerability in the webserver files. I will use this tool very often, Mostly this tool will be caught in IDS (Intrusion detection sensor) or IPS (Intrusion Prevention sensor).
Also Read: What is Kismet tool – An overview
Who can use Nikto?
Nikto is a Linux-based tool so, only Linux OS users can use this tool.
How Nikto exactly works?
Firstly, the user opens Nikto, the tool will be in a terminal format and once the user enters the tool he/she can enter the targeted IP address that wanted to be scanned and just run the program using few commands.
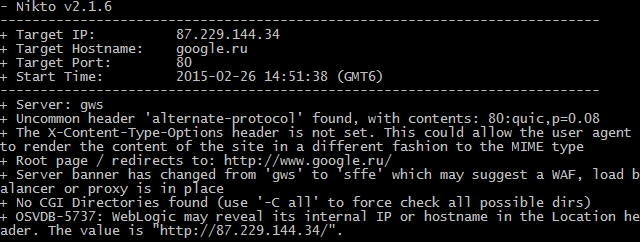
Once the scan is successful the tool will display the vulnerabilities in the Network by sniffing the packets. Remember this tool is not a packet sniffer, Only finds the vulnerabilities in a network.
This tool can import files from packet sniffing tools such as Nmap and Kismet, which is a good feature.
Also Read: What is Aircrack-ng?
Conclusion
According to me Nikto is mostly used by Red team, cybercriminals and those who wants to do vulnerability test or vulnerability attack they go with this tool. But remember this tool is still dependent on others.
Also Read: What is Wireshark?
Also Read: What is THC hydra?
Read: What is john the ripper?
Read: What is Metasploit?

Super-Duper website! I am loving it!! Thanks for the full tutorial on Nikto