Introduction
In this post, you will learn what is Prismdump and how the tool works, Just an overview. Other than that I have written a separate post on how to work with Prismdump and the post is available in the hacking tools menu.
What is Prismdump?
Prismdump is a sniffing tool, used to capture packets in a network. The tool can just sniff the packets and cannot analyse the packets in the tool and the user can’t bring an external tool to analyse along with the Prismdump.
So, the user gathers information from the tool and place the gathered information in another tool such as Wireshark and Nessus will give more details about the targeted network. More details mean the vulnerabilities also.
The tool is chipset base, remember the prism2 is chipset based. Prism2 is an upgraded version of the Prismdump.
Also Read: An Overview of TCPdump
Who can use Prismdump?
The prism dump tool can only be used by Linux users. Because the tool is specifically made for Linux users.
How Prismdup works?
Prismdump is a kind of GUI format because the packets displayed will be in an organized manner but the user should command on the Prismdump terminal. The tool captures packets and dumps them and that’s why the name dump came after prism.
The tool stores the packets in the pcap format, as the other sniffing tools do. As most of the sniffing tools use pcap format even this tool uses because of the long reconnaissance mission.
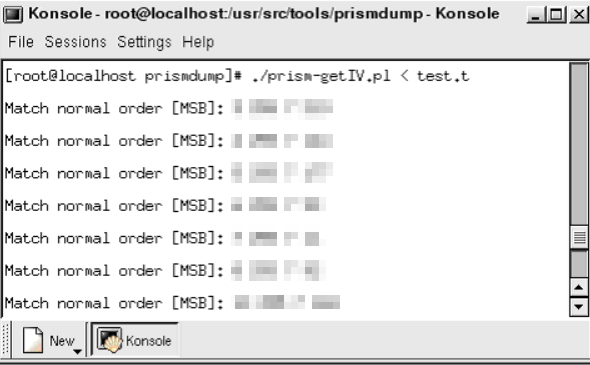
Once the user opens the tool he just needs to enter prism-getIV.pl and enter the targeted network the tool starts to scan and gives the captured packets.
Also Read: Nessus overview for beginners
Conclusion
According to my knowledge, this tool is very old and I personally don’t use the tool and some alternative tools are Wireshark, Nmap, Zmap, Kismet.
Also Read: What are Cain and Abel
Also Read: Nikto a vulnerability scanner