What is proxychains ❓
In computer networking, A proxy server is a server application that acts as an intermediary between a client requesting a resource and the server providing that resource.
Where’s proxy chains are series of intermediate between a client and the resource.
In simple the proxychains gives anonymity while attacking the target machine.
Video ????
Difference between proxy vs proxychains ????
Proxy
Proxy are usually found on the browser. And anonymize HTTP protocols and web connection and the things you are doing on the internet.
Proxy-chains
Proxy-chains is a tool that anonymize whatever you are doing on the computer, We could add multiple IP address as bridge to get the resources.
How to configure proxy-chains ????
To configure proxychains enter this command nano /etc/proxychains4.conf
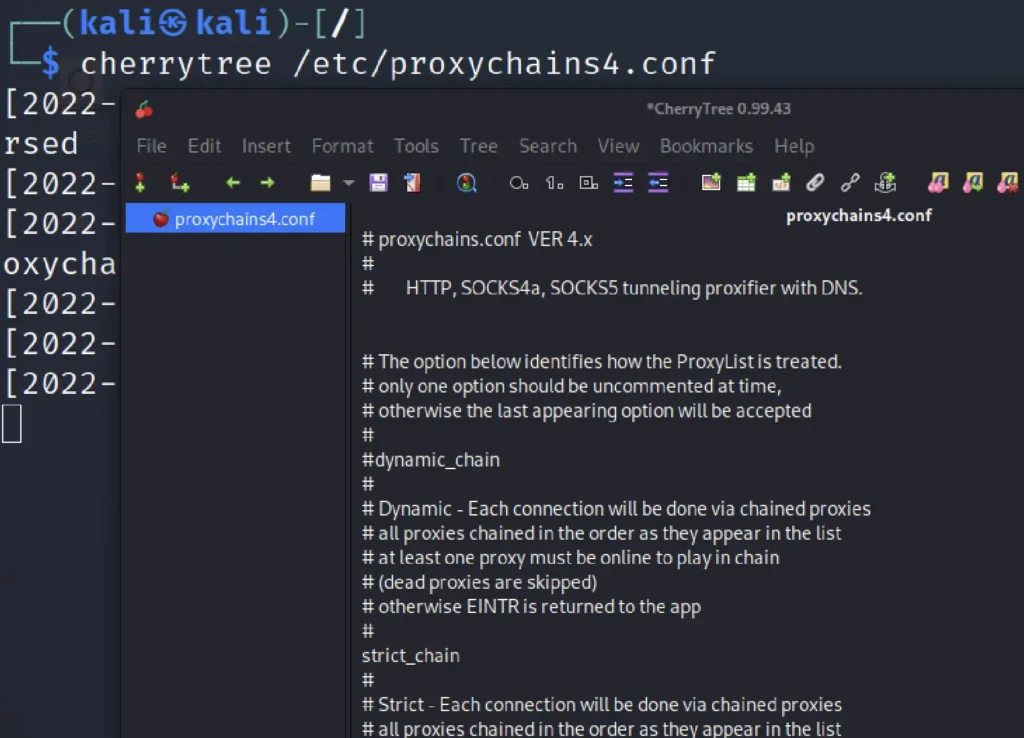
proxychains formats are in HTTP, SOCKS4a, SOCKS5. HTTP format are very old and hope you are very familiar with it.
Also we use the HTTP format to access the TOR browser etc.,
SOCKS4a is pretty old but it is good at anonymising and I recommend you to use the SOCKS5 which anonymise pretty much everything on your system.
You can uncheck the # tags to configure
Advertisement
Types of proxy
Currently there are four types of proxychains they are ????
- Dynamic chain
- Strict chain
- Round robin chain
- Random chain
Dynamic chain
The Dynamic chain has series of IP address and the connection goes through it, In dynamic proxy at least one proxy must be online to play in the chain.
Strict chain
All the IP address will be in a list, Each connection will be going through the order of IP address.
Round robin chain
The round robin chain has also series of IP address and at least one proxy must be online to play in the chain. If there are any dead proxy they are skipped.
If the request doesn’t work then the connection starts from the beginning.
Random chain
Using random proxy to connect to the network and gather the information requested.
How to use proxychains with tools
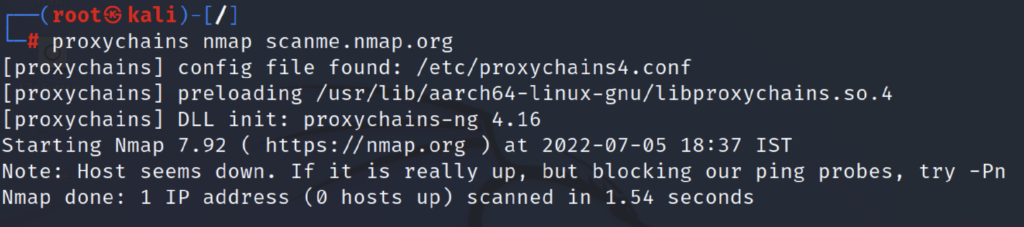
You can use proxy-chains with almost all scanning tools, To use this tool just add proxy-chains in front of the command.
proxychains Nmap scan.nmap.org
Conclusion
According to me proxychains is one of the best tool for obfuscation, But remember using public IP’s in proxychains is like you are getting caught. So, try to use a well known paid service.
Also Read: Gobuster full tutorial from noob to pro




