Introduction
In this post, you will learn what is wpscan and how does it work and also we will see some examples of wpscan and I am sure by end of the post, you will be familiar with the tool and also below is the video format of the post, check it out.
Video
What is wpscan ❓
WPscan stands for “wordpress scanner“, This tool specifically made to scan vulnerabilities in the WordPress site.
We knew almost 50% of the sites on the internet are hosted by WordPress. So, If there is a vulnerability scanner specifically for WordPress is great.
This tool can be used in a good way and also it can be used in an “Evil” way.
This wpscan tool is sponsored by one of the biggest security companies called sucuri.
Advertisement
To download the tool just enter the command apt-get install wpscan
Below is the source code for the tool
What all can the wpscan do
- The version of WordPress installed and any associated vulnerabilities
- What plugins are installed and any associated vulnerabilities
- What themes are installed and any associated vulnerabilities
- Username enumeration
- Users with weak passwords via password brute forcing
- Backed up and publicly accessible wp-config.php files
- Database dumps that may be publicly accessible
- If error logs are exposed by plugins
- Media file enumeration
- Vulnerable Timthumb files
- Full Path Disclose
- Upload directory listing
Advertisement
How to use the wpscan
Just follow the below examples and I am sure by end of the last example you will be familiar with the tool and have any doubts comment down below or check the youtube video I made about the tool.
Example1, Default scan
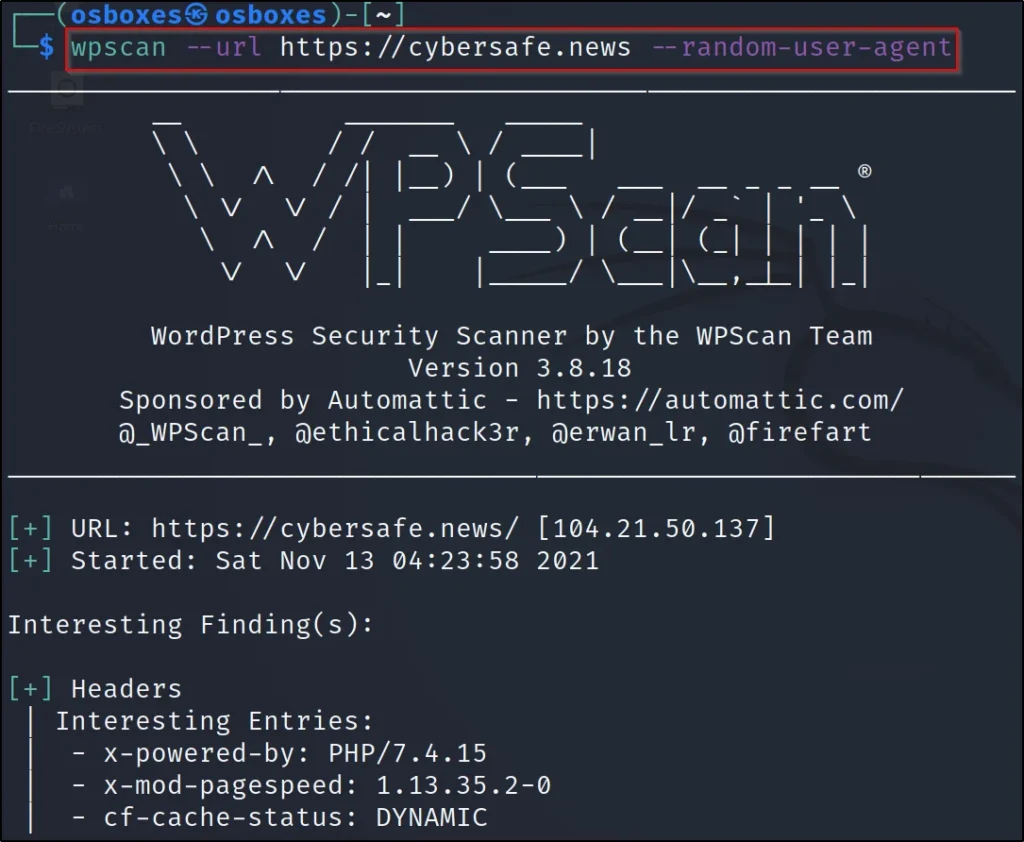
Let’s do a default scan in the tool, To do a default scan we are using the –url command and enter the target URL
wpscan –url https://cybersafe.news –random-user-agent
–url: Target url
–random-user-agent: Facing an error enter this command.
Example2, Enumerating themes
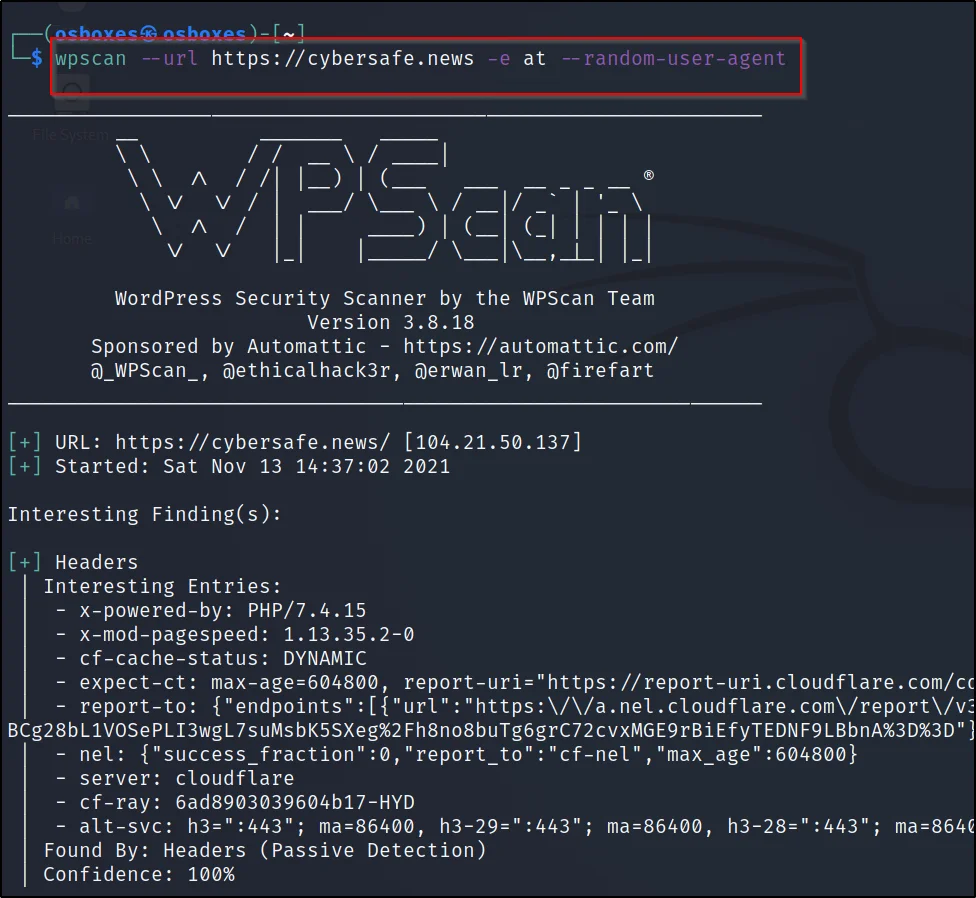
The WPScan uses its database which contains about 2600 themes to check the vulnerable installed one over the targets.
To check the themes, We just enter this command ????????
wpscan –url https://cybersafe.news -e at –random-user-agent
–url: Target
-e: enumerating
at: themes
–random-user-agent: Facing any error enter this command
Advertisement

Example3, Enumerating plugins
To enumerate the plugins of the target we just enter this particular command ????????
wpscan –url https://cybersafe.news -e ap –random-user-agent
–url: Target
-e: enumerating
ap: plugin
–random-user-agent: facing any problem enter this command

Example4, Enumerating themes, plugins, and username
Use this command to do themes enumeration, plugin enumerating and also username enumeration.
By default when you enumerate for the username the tool does a brute-forcing.
wpscan –url http://cybersafe.news -e at -e ap -e u –random-user-agent
–url: Target of the site
-e: enumeration
–random-user-agent: Any error then enter this command
at: enumerate all themes of targeted website
ap: enumerate all plugins of targeted website
u: enumerate all usernames of targeted website

Example5, Doing brute forcing
wpscan –url http://techyrick.com -U <username> -P <Password>
-U: After the -u you should either enter the username or enter the username folder
-P: Enter the password or enter the password list file


Conclusion
This is the best tool for brute-forcing WordPress sites and also it is an awesome tool to find the themes and plugins.
Moreover, the tool claims to be a vulnerability finder, but it is not. The tool just enumerates the target and finds the information like the plugins and themes.
Therefore, the tool has got more features that even I didn’t even explore.
Also Read: Full tutorial on webhttrack
Also Read: SQLMAP full tutorial





Pretty! This has been an extremely wonderful post.
Thanks for supplying these details.
Thank you, I hope you like the post 💖