Introduction
In this post, you will learn what is internal and external reconnaissance and an example from both the reconnaissance. You will also learn how the process works.
What is Reconnaissance?
Like many words in IT originally come from the military and even the reconnaissance term came from the military. We can call the term reconnaissance or recon, Which means gathering information in the enemy’s Bootcamp. The word recon often used in cybersecurity. In cybersecurity, recon means gathering information of targeted users is called reconnaissance.
There are two types of reconnaissance they are internal and external reconnaissance.
Also Read: What is baiting?
What is Internal Reconnaissance?
Internal reconnaissance means gathering information about the targeted user’s network is called Internal recon. In simple words, internal recon means gathering information of the end-user internally.
When I say Internal recon, you should understand that no humans are involved in it. So, only the targeted internals are involved. This means the target IP address, the vulnerability, the exploits are only involved.
They gather information of the target using a number of the open-source tools or he/she can build their own tool which means (BYOD) Bring your own device.
Most used tools for Internal recon
As I am in the cybersecurity field I know very well about the Information gathering tools, I have mentioned some they are;
- Weleakinfo.to
- sublist3r
- theHarvester
- Nmap
- Metasploit
- Nessus
- Cain and abel
- Nikto
- Kismet
- Aircrack-ng
- Wireshark
- THC-hydra
- John the ripper
I use the above tools on a regular basis and all these tools are really very helpful for information gathering and also for exploiting.
An example of Internal recon?
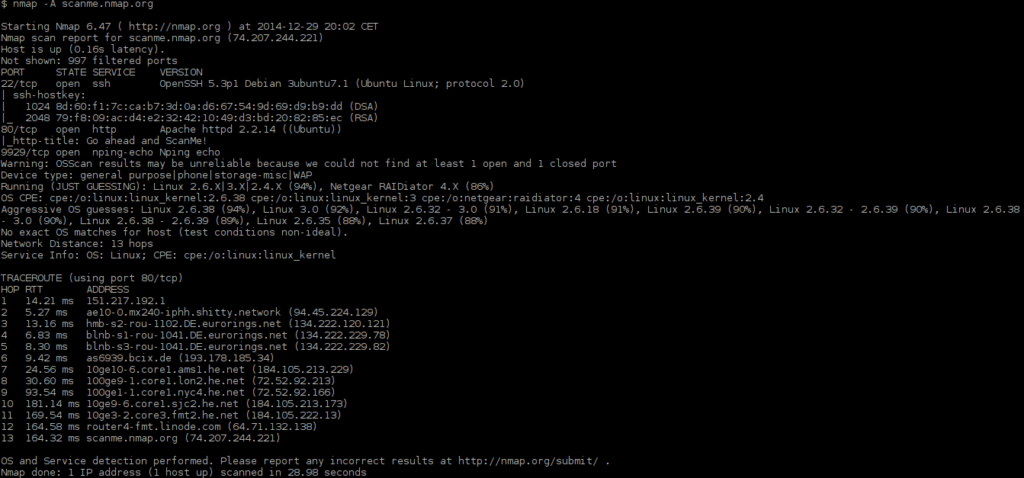
Let me use Nmap as an example, Firstly the hackers open the Linux machine and open Nmap. Once the Nmap open the hacker should know the targets IP address! But how?
It ‘s is very easy to gather the IP address of a domain or a target. Just open a Linux terminal and enter
>dig techyrick.com A
The above is the command to find the IPV4 address of theyrick.com, Suppose if the hacker wants the IPV6 address he/she should type
>dig techyrick.com AAAA
Once the above command is entered the hacker will get the IPV4 or IPV6 address and the hacker should just copy the address and pst in the text files for further enumeration.
Now, on Nmap, the hacker should enter the following command
>nmap -T4 -A -P -Pn -Sv 160.153.137.210
Here -T4 means speed, -A means scan all, -P means all ports, -Pn means to treat all ports as online, -Sv means the service and version info. Therefore, the scan completed the hacker will get information such as ports, firewall info, OS, etc.,
What is External reconnaissance?
External reconnaissance did outside, which means the humans are involved in the external recon and the primary target is the humans only.
How external reconnaissance works?
External recon works only if it is directly or indirectly involved the target human. For example, we can take smishing therefore which is a type of social engineering attack and also it is an External recon. The hacker can perform external reconnaissance if he/she knows the target for example if the hacker knows the target company working on or his house address.
Any sensitive physical information of the users is on the hacker’s side then they can perform external recon. Therefore, let’s see some methods used in the external recon process.
Also Read: What is water holing – Overview
The methods used for external reconnaissance?
I have mentioned some most used external recon methods, they are;
An example of external recon?
Let’s take baiting as an external recon example,
Baiting’s works by tempting the end-user and the cybercriminals will have some malicious codes in the bait(Hardware). And therefore once the user takes and enters into his administrator account the Game is Over!
Also Read: What is diversion theft
Also Read: What is pretexting