Introduction
In this post, you will learn what is theHarvester and how does the tool works and also in addition you will learn who developed the tool and let’s see some examples on theHarvester and also I will give an alternative for this tool. Check the below video, it is all about the tool.
Video
What is theHarvester
theHarvester is an Information-gathering tool. This tool is the same as the other passive information-gathering tool, but what makes this tool specific is the number of contributions for this tool in Github and I wondered.
There are more than 300 contributions. Mostly the tool was written in python and docker files and it was very easy to work with the tool.
Advertisement
Who developed the theHarvester tool
The tool was developed by the author and co, here when I say co they are the public people. Yes, this tool has got GPLV2, so, the public can contribute to GitHub.

The tool author is Christian Martorella and this guy seems to be intelligent, ha Whatever. Let’s talk about the tool ????. I have given theHarvester download link and just go and download from the official page and I have also given the Author’s page go and check.
Well, I have to talk about this the author got a domain name called https://edge-security /blog. And I have noticed he have quite a good number of posts, go and check it!!!
Advertisement
What can the tool do
- Gather emails
- Subdomains searchs
- Hosts seraches
- employee names from twitter only
- Checks for open ports
- Banners from different public sources like search engines,
- PGP key servers and SHODAN computer database.
Advertisement
theHarvester Commands
- -d: Target domain
- -b: data source: Gatherers information from all possible sources
- -v: verify hostname via DNS resolution and search for virtual hosts
- -f: save the results in both XML and HTML format
- -n: perform a DNS reverse on all possible ranges discovered
- -c: perform a DNS brute force for the target domain name
- -l: limits the number of results
- -h: using SHODAN database
Advertisement
How to use theHarvester tool? ????
Example1:
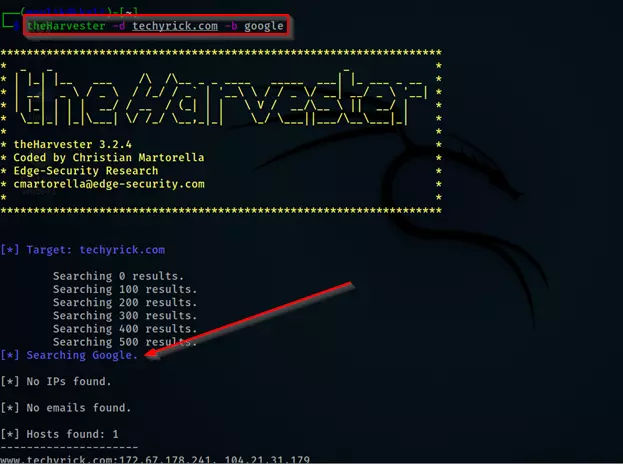
In the first example, we are doing the most common command,
theHarvester -d techyrick.com -b google
This command scans for google information on all the platforms, just try with a kali machine. You may enter bing or Twitter etc.,
Example2:
Let’s do a limit in the search
theHarvester -d techyrick.com -b linkedin -l 1000
-d for the target domain
-b for where you want to search
-l is limit only 1000 could be searched in this command

Don’t mind the handwriting ????
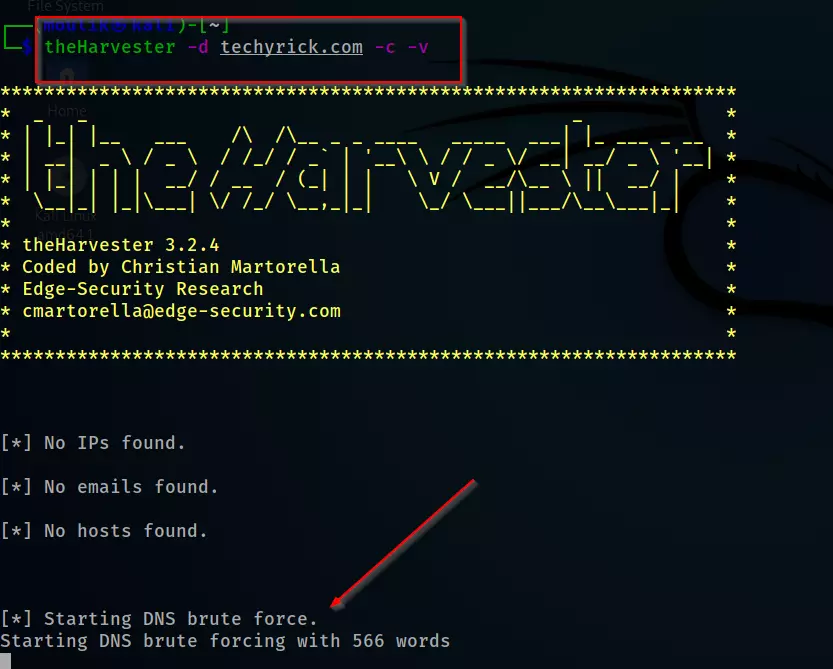
Example3:
Doing a brute force on the target
theHarvester -d techyrick.com -c
Example4:
Doing a scan and saving either in HTML or XML format
theHarvester -d techyrick.com -b google -l 100 -f text
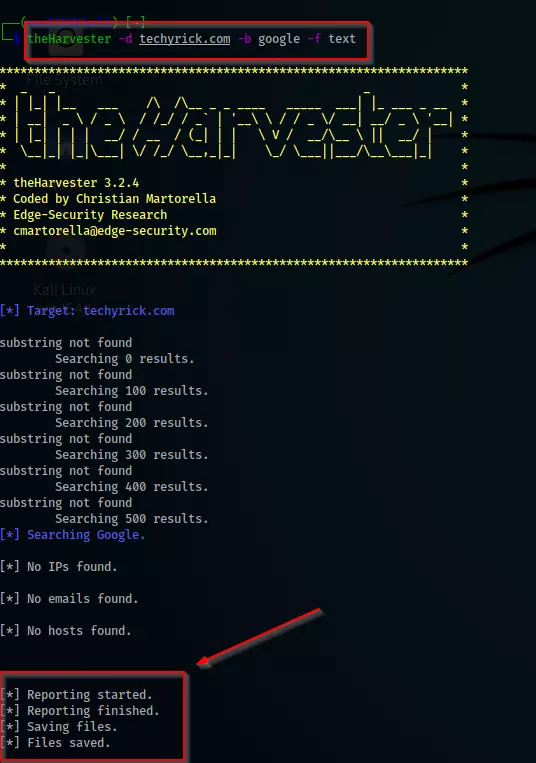
The file will be automatically saved in HTML and XML format
Conculusion
According to my knowledge, this tool is best for scanning the subdomains and also this tool can perform another scan such as port scan but I mostly don’t use this tool because it is not giving a deep information gathering.
Advertisement
The alternative for this tool can be sublist3r and DMitry.




Aw, this was a very nice post. In thought I would like to put in writing like this additionally ?taking time and actual effort to make a very good article?but what can I say?I procrastinate alot and under no circumstances seem to get one thing done.
Thank you, man and Mr. 172.255.125.175 here is your IP